ESET researchers present particulars on a beforehand undisclosed China-aligned APT group that we observe as PlushDaemon and one among its cyberespionage operations: the supply-chain compromise in 2023 of VPN software program developed by a South Korean firm, the place the attackers changed the respectable installer with one which additionally deployed the group’s signature implant that we’ve got named SlowStepper – a feature-rich backdoor with a toolkit of greater than 30 parts.
Key factors of this blogpost:
- PlushDaemon is a China-aligned risk group, engaged in cyberespionage operations.
- PlushDaemon’s major preliminary entry vector is hijacking respectable updates of Chinese language functions, however we’ve got additionally uncovered a supply-chain assault in opposition to a South Korean VPN developer.
- We consider PlushDaemon is the unique person of a number of implants, together with SlowStepper for Home windows.
- SlowStepper has a big toolkit composed of round 30 modules, programmed in C++, Python, and Go.
Overview
In Could 2024, we observed detections of malicious code in an NSIS installer for Home windows that customers from South Korea had downloaded from the web site of the respectable VPN software program IPany (https://ipany.kr/; see Determine 1), which is developed by a South Korean firm. Upon additional evaluation, we found that the installer was deploying each the respectable software program and the backdoor that we’ve named SlowStepper. We contacted the VPN software program developer to tell them of the compromise, and the malicious installer was faraway from their web site.
We attribute this operation to PlushDaemon – a China-aligned risk actor energetic since at the least 2019, participating in espionage operations in opposition to people and entities in China, Taiwan, Hong Kong, South Korea, the USA, and New Zealand. PlushDaemon makes use of a customized backdoor that we observe as SlowStepper, and its major preliminary entry approach is to hijack respectable updates by redirecting site visitors to attacker-controlled servers. Moreover, we’ve got noticed the group gaining entry by way of vulnerabilities in respectable net servers.
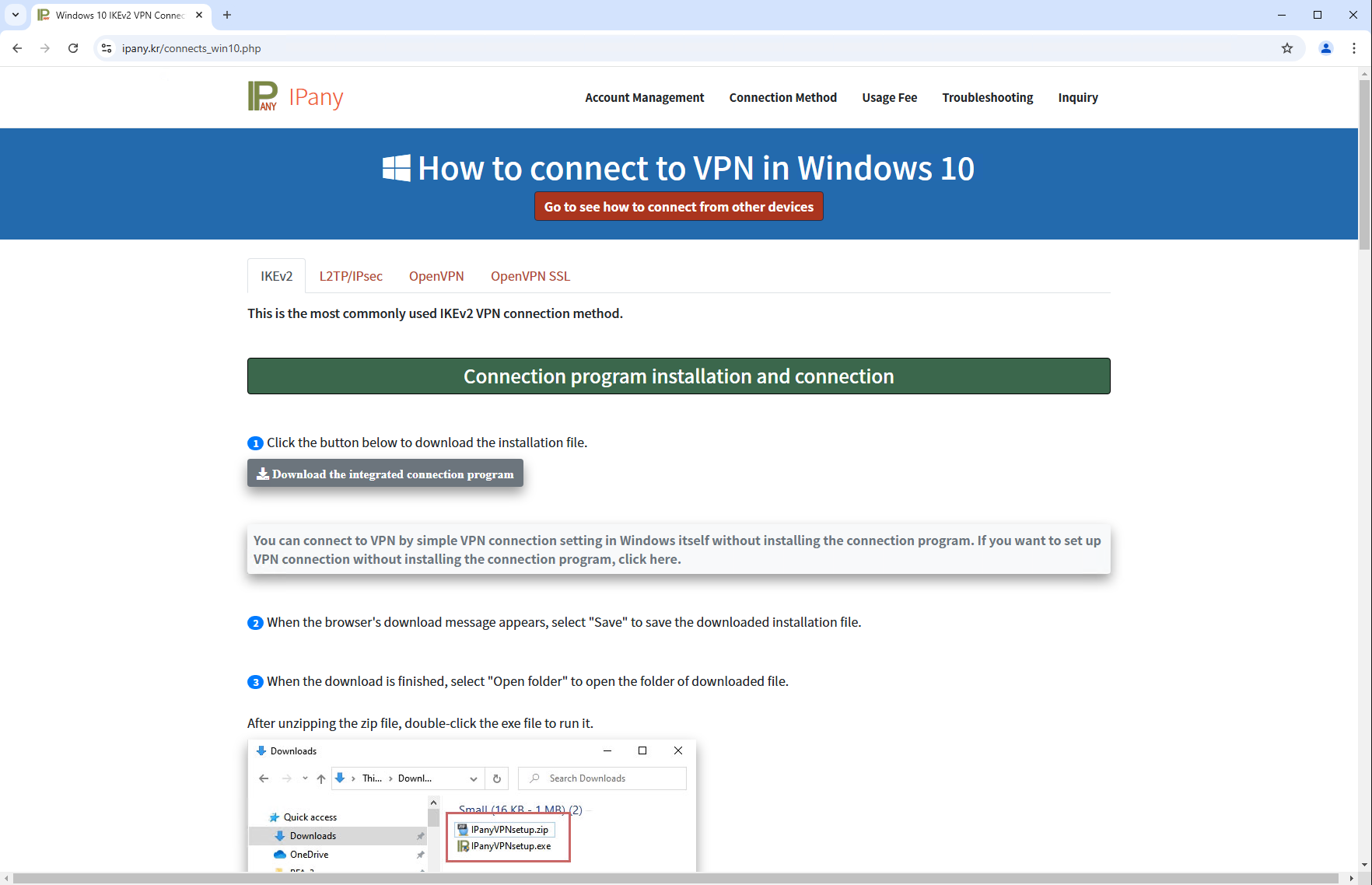
The victims seem to have manually downloaded a ZIP archive containing a malicious NSIS installer from the URL https://ipany[.]kr/obtain/IPanyVPNsetup.zip. We discovered no suspicious code on the obtain web page (proven in Determine 1) to supply focused downloads, for instance by geofencing to particular focused areas or IP ranges; due to this fact, we consider that anybody utilizing the IPany VPN may need been a legitimate goal.
Through ESET telemetry, we discovered that a number of customers tried to put in the trojanized software program within the community of a semiconductor firm and an unidentified software program improvement firm in South Korea. The 2 oldest instances registered in our telemetry had been a sufferer from Japan in November 2023, and a sufferer from China in December 2023.
Technical evaluation
As illustrated in Determine 2, when the malicious IPanyVPNsetup.exe installer is executed, it creates a number of directories and deploys each respectable and malicious recordsdata.
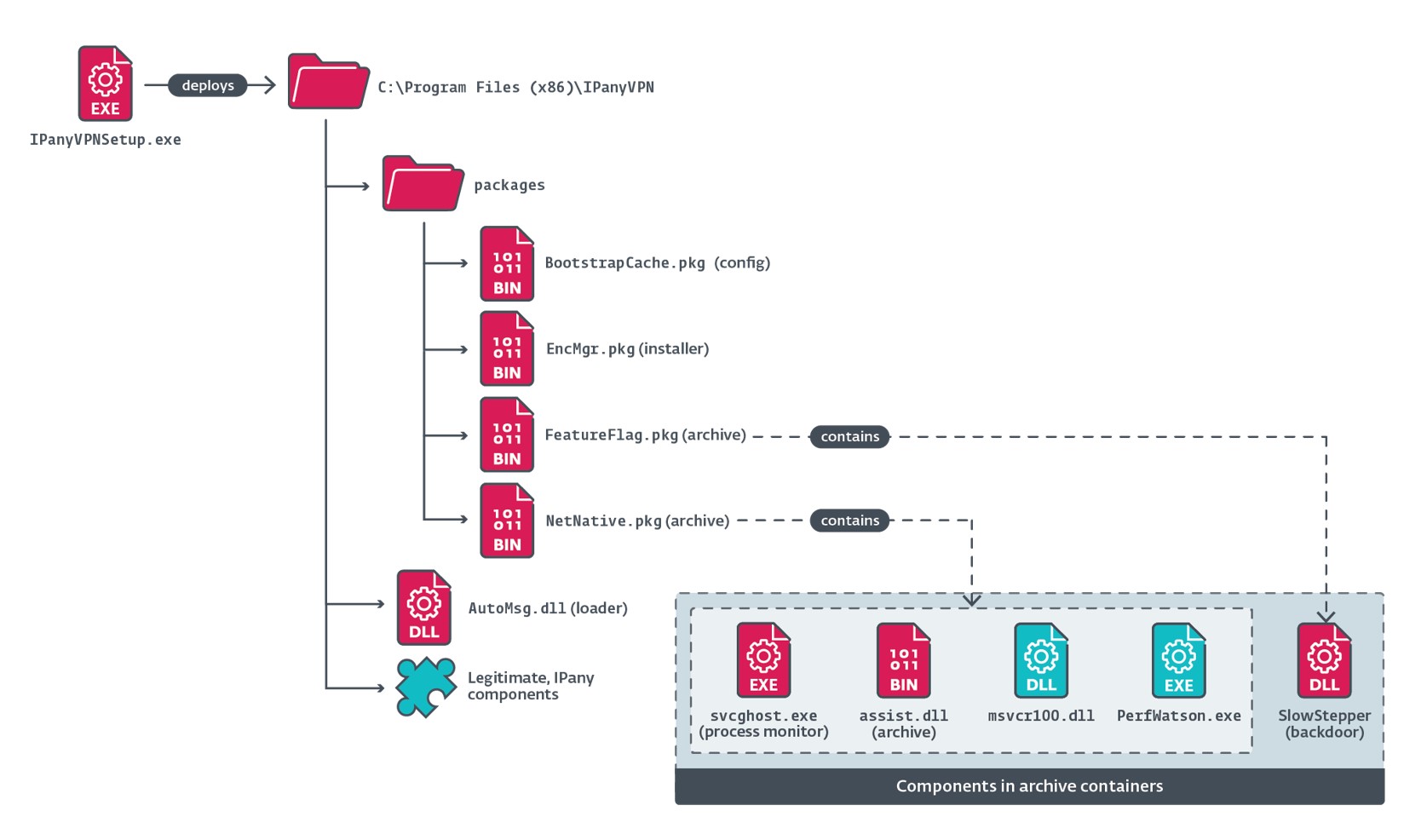
Moreover, the installer establishes persistence for SlowStepper by including an entry named IPanyVPN to a Run key, with the worth %PUBLICpercentDocumentsWPSDocumentsWPSManagersvcghost.exe, in order that the malicious element svcghost.exe (later extracted and deployed by the loader in EncMgr.pkg) is launched when the working system begins.
The primary malicious element that’s loaded by the installer is the AutoMsg.dll loader. Determine 3 illustrates the key steps taken throughout the execution of this element.
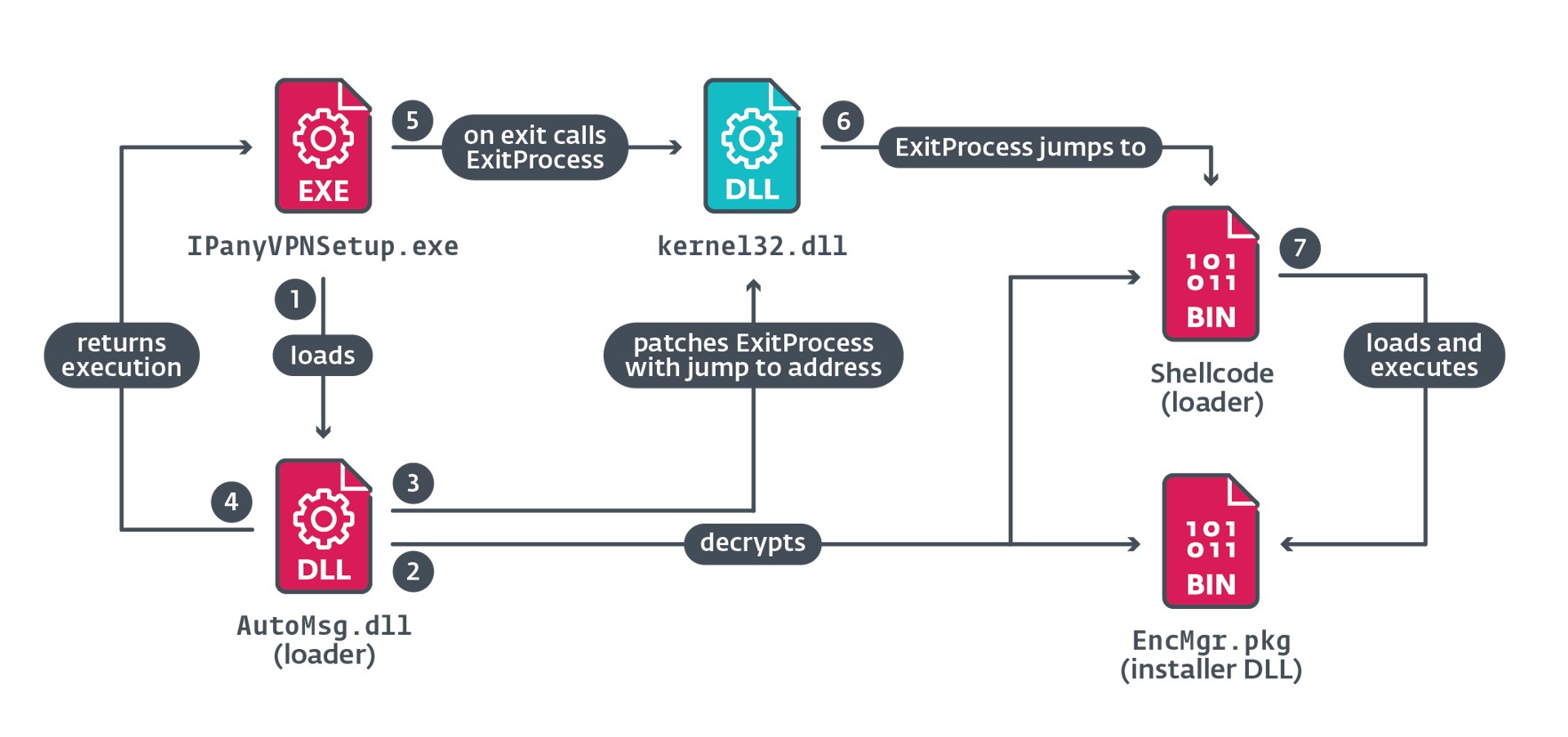
When IPanyVPNSetup.exe calls ExitProcess, the patched bytes redirect execution to the shellcode that hundreds EncMgr.pkg into reminiscence and executes it.
EncMgr.pkg creates two directories – WPSDocuments and WPSManager – in %PUBLICpercentDocuments and the deployment begins by extracting parts from the customized archives NetNative.pkg and FeatureFlag.pkg. The parts are dropped to disk and moved to different areas with new filenames. The sequence and actions taken are as follows:
1. Extracts the recordsdata from NetNative.pkg to:
a. %PUBLICpercentDocumentsWPSDocumentsWPSManagerassist.dll,
b. %PUBLICpercentDocumentsWPSDocumentsWPSManagermsvcr100.dll,
c. %PUBLICpercentDocumentsWPSDocumentsWPSManagerPerfWatson.exe, and
d. %PUBLICpercentDocumentsWPSDocumentsWPSManagersvcghost.exe.
2. Deletes NetNative.pkg.
3. Strikes FeatureFlag.pkg to C:ProgramDataMicrosoft SharedFiltersSystemInfowinlogin.gif.
4. Strikes help.dll to C:ProgramDataMicrosoft SharedFiltersSystemInfoWinse.gif.
5. Extracts file from Winse.gif to %PUBLICpercentDocumentsWPSDocumentsWPSManagerlregdll.dll.
6. Copies knowledge from BootstrapCache.pkg to %PUBLICpercentDocumentsWPSDocumentsWPSManagerQmea.dat.
Its final actions are to execute svcghost.exe utilizing the ShellExecute API after which exit.
The svcghost.exe element performs monitoring of the PerfWatson.exe course of, the place the backdoor is loaded, guaranteeing that it’s all the time operating. If the processes should not operating, it executes PerfWatson.exe (initially a respectable command line utility named regcap.exe, included in Visible Studio), which the attackers abuse to side-load lregdll.dll. The DLL’s purpose is to load the SlowStepper backdoor from the winlogin.gif file.
On a brand new thread, it creates a anonymous window that ignores all messages besides WM_CLOSE, WM_QUERYENDSESSION, and WM_ENDSESSION. When any of those three messages is acquired, the thread makes an attempt to determine persistence within the Home windows registry, relying on the permissions of the present course of; see Desk 1.
Desk 1. Registry keys focused for persistence
| Requires | Registry key | Entry | Worth |
| Administrator | HKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogon | Userinit | Present path of svcghost.exe. |
| Consumer | HKCUSoftwareMicrosoftWindows NTCurrentVersionWindows | load |
The SlowStepper backdoor
SlowStepper is a backdoor developed in C++ with in depth use of object-oriented programming within the C&C communications code. Though the code incorporates a whole bunch of capabilities, the actual variant used within the supply-chain compromise of the IPany VPN software program seems to be model 0.2.10 Lite, in accordance with the backdoor’s code. The so-called “Lite” model certainly incorporates fewer options than different earlier and newer variations.
The oldest model of the SlowStepper backdoor that we all know of is 0.1.7, compiled on 2019-01-31 in accordance with its PE timestamps; the most recent one is 0.2.12, compiled on 2024-06-13, and is the total model of the backdoor.
Each the total and Lite variations make use of an array of instruments programmed in Python and Go, which embrace capabilities for in depth assortment of information, and spying by recording of audio and movies. The instruments had been saved in a distant code repository hosted on the Chinese language platform GitCode, beneath the LetMeGo22 account; on the time of writing, the profile was personal (Determine 4).
C&C communications
SlowStepper doesn’t carry the C&C IP tackle in its configuration; as a substitute, it crafts a DNS question to acquire a TXT report for the area 7051.gsm.360safe[.]firm. The question is distributed to one among three respectable, public DNS servers:
- 8.8.8.8 – Google Public DNS,
- 114.114.114.114 – 114dns.com, or
- 223.5.5.5 – Alibaba Public DNS.
We obtained 4 such data related to that area:
- &%QT%#/zZDmb4ATTVIxwHXPLGrj0FAOV7q+P/sMG109ooj5YLnVZBs3R/eZcuQximtgLkf
- &%QT%#/zZDmb4ATTVIxwHXPLGrj0FAOV7q+P/sMG109ooj5YKQs3XiHSjM3f+h9ok9XfQ1AjoX+C4UXZsDLVqCDhvxyw==
- &%QT%#aT1sAjOFTcwzQ7hwc0iyfygP/ooo8pkIRyaNKWcqBz+QRGYBV/2v8HrVg28+aZXhfXvgDxS1vXAuhdcN2dEKxw==
- &%QT%#aT1sAjOFTcwzQ7hwc0iyfySJBEDM0z6na7BiogG0hDJqdKlUqkrb9ppOjg8epeQ6I6cUXWLKyZGZCkJwFyKD4Q==
The format of the information within the question is proven in Determine 5. The code checks whether or not the primary six bytes of the TXT report match &%QT%# and in that case, it extracts the remainder of the string, which is a base64-encoded AES-encrypted blob containing an array of 10 IP addresses for use as C&C servers. The important thing used for decryption is sQi9&*2Uhy3Fg7se and the IV is Qhsy&7y@bsG9st#g.
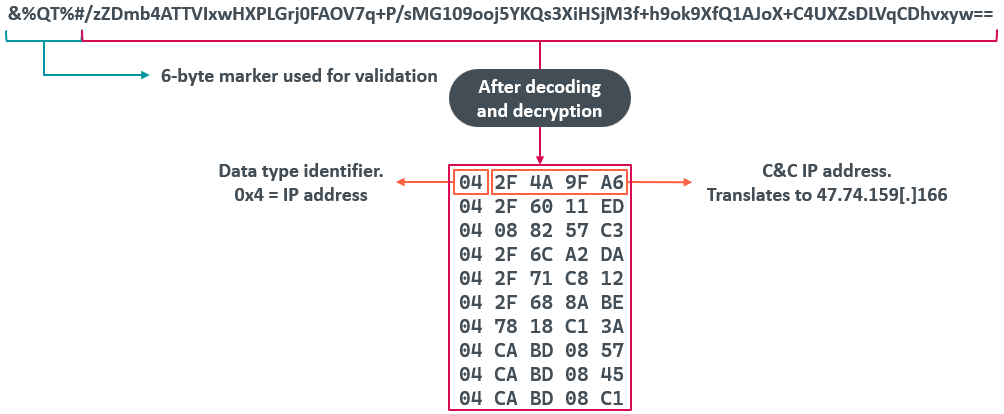
When parsing the decrypted knowledge, the code can extract at the least 4 knowledge identifiers, described in Desk 2.
Desk 2. Knowledge sorts processed by the backdoor’s code
| Knowledge identifier | Dimension of information | Description |
| 0x04 | 4 | Knowledge is an IP tackle. |
| 0x05 | 6 | Knowledge is an IP tackle and port quantity. |
| 0x06 | 16 | Skips the following 16 bytes of information. We suspect that, given the dimensions of the information, it’s attainable that it’s an IPv6 tackle. |
| 0x00–0x03 0x07–0xFF |
Knowledge identifier worth is the worth of the information measurement. | Skips the following (unknown) bytes of information. |
One of many IP addresses is chosen and SlowStepper connects to the C&C server by way of TCP to start its communication protocol. If, after plenty of makes an attempt, it fails to determine a connection to the server, it makes use of the gethostbyname API on the area st.360safe[.]firm to acquire the IP tackle mapped to that area and makes use of the obtained IP as its fallback C&C server.
As soon as communication is established, SlowStepper can course of the instructions listed in Desk 3.
Desk 3. Primary instructions supported by SlowStepper
| Command ID | Motion carried out |
| 0x32 | Collects the next data from the compromised machine and sends it to the server: · model of the CPU, utilizing the CPUID instruction, · HDDs linked to the pc and their serial numbers, · laptop title, · native host title, · public IP tackle, by querying a number of providers, · record of operating processes, · record of put in functions, · community interface data, · extra details about the pc’s drives, akin to quantity title and free area, · system reminiscence, · present username, · persistence sort used, · whether or not cameras are linked, · whether or not microphones are linked, · whether or not the working system is operating as a digital machine, · system uptime, · HTTP proxy configuration, and · whether or not queries to the DNS server at 114.114.114.114:53 to resolve the addresses of two respectable domains, cf.duba.internet (Kingston) and f.360.cn (360 Qihoo), failed or succeeded. It’s unclear to us what the aim of this data is. |
| 0x38 | Executes a Python module from its toolkit; the output and any recordsdata created by the module are despatched to the server. The process is similar to what’s used within the shell mode. |
| 0x39 | Deletes the desired file. |
| 0x3A | This command can course of different instructions despatched by the operator in SlowStepper’s shell mode, which we clarify in additional element beneath. Alternatively, it could actually additionally: · Run a command by way of cmd.exe and ship the output again to the server. · Run a command by way of cmd.exe with out sending the output to the server. |
| 0x3C | Uninstalls SlowStepper by eradicating its persistence mechanism and eradicating its recordsdata. |
| 0x3F | Lists recordsdata within the specified listing, and lists drives. |
| 0x5A | Downloads and executes the desired file. |
SlowStepper has a slightly uncommon function: the builders carried out a customized shell, or command line interface, on prime of its communication protocol. Whereas the backdoor accepts and handles instructions within the conventional method, the 0x3A command prompts the interpretation of operator-written instructions (Desk 4).
Desk 4. Instructions supported in shell mode
| Command | Parameters | Description |
| cd | Path to a listing. | Checks whether or not a listing exists. |
| gcall | Module title and different unknown parameter(s). | This perform can carry out two duties: · Obtain a module from the distant code repository and execute it. The module is meant to be a console utility. · Ship a file from the compromised machine to the operator. |
| pycall | Device title to be executed. | This command is defined intimately within the Execution of instruments by way of SlowStepper’s pycall shell command part. |
| restart | self | Restarts SlowStepper by rerunning the host course of and calling the ExitProcess API. Returns the message The mode of NSP would not assist restart self. when SlowStepper is operating in a course of by way of a persistence approach that abuses Winsock namespace suppliers; nevertheless, it’s not included on this variant of SlowStepper. |
| replace | N/A | Downloads a module from the distant code repository, changing a earlier current model. |
| gconfig | present | Shows the worth of ServerIP (the C&C IP tackle). |
| set | Modifications the worth of ServerIP. The console suggests the next to the operator: In order for you make the Configuration efficient instantly, please command “gconfig reload”. |
|
| reload | Reloads the configuration. | |
| getname | Returns the title of the present course of through which SlowStepper is operating. | |
| getdll | Returns the title of the SlowStepper DLL within the present course of. | |
| getpid | Returns the method ID of the present course of through which SlowStepper is operating. | |
| getsid | Returns the Distant Desktop Providers session ID of the present course of. This implies that SlowStepper may additionally be supposed to compromise machines operating Home windows Server. | |
| getpwd | Downloads getcode.mod from the distant code repository and executes it utilizing rundll32.exe. The module generates a file, named psf.bin, that incorporates the collected knowledge. | |
| gcmd | question | Creates a whole report of details about the desired file or listing. |
| delete | Deletes the desired file, listing, or all recordsdata in a listing. | |
| set | Units configuration parameters. | |
| terminate | Terminates the desired course of. | |
| cancel | Creates a file with the .delete extension. |
Execution of instruments by way of SlowStepper’s pycall shell command
Determine 6 illustrates the execution chain, beginning when the operator points a pycall command to request the execution of a Python module on the compromised machine; right here, for example, the module CollectInfo.
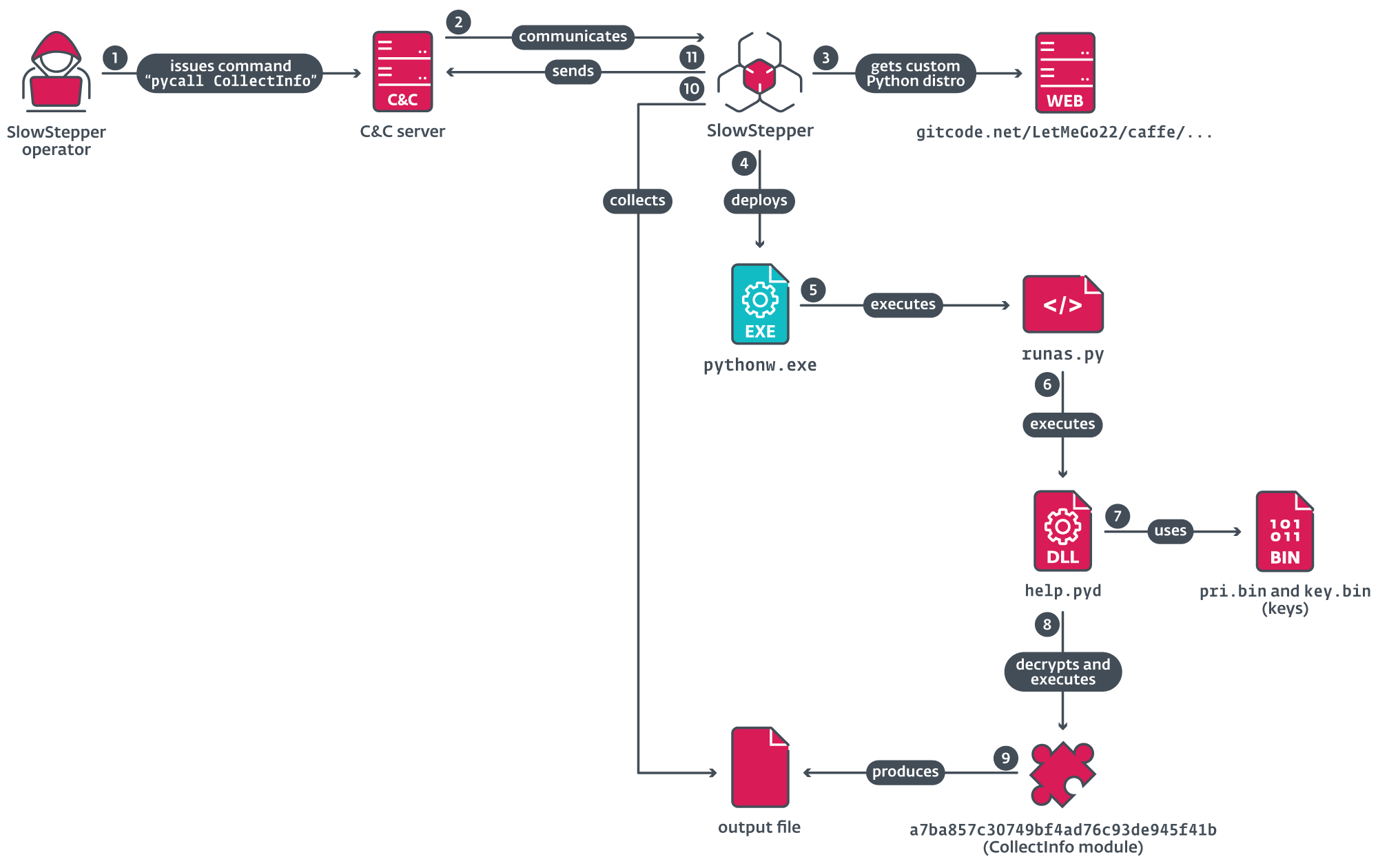
From the distant repository, the pycall command downloads a ZIP archive that incorporates the Python interpreter and its supporting libraries. One in every of three attainable custom-made distributions is downloaded, as outlined in Desk 5.
Desk 5. Record of custom-made Python distributions and the situations beneath which they’re downloaded
| Situation | Archive title | Description |
| Home windows working system is XP. | winxppy.org | Python 3.4 |
| All required Home windows API set (stub) DLLs and the Microsoft C runtime are current. | winpy_no_rundll.org | Python 3.7 |
| Neither of the previous situations are met. | win7py.org | Python 3.7; consists of Home windows API set (stub) DLLs and the Microsoft C runtime library. |
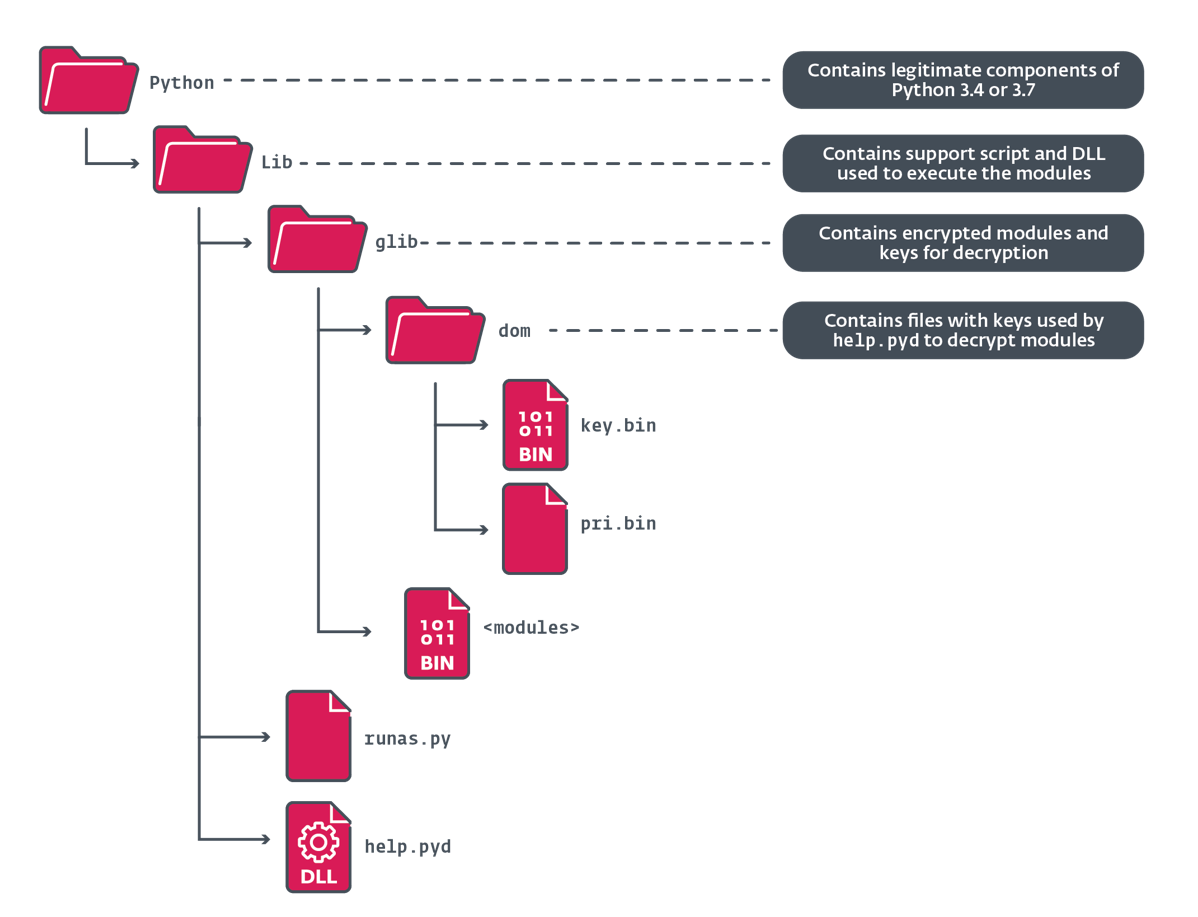
Determine 7 exhibits the listing construction of the decompressed archive containing the Python distribution, itemizing solely the malicious recordsdata which might be included inside.
SlowStepper runs the Python interpreter utilizing the next command line:
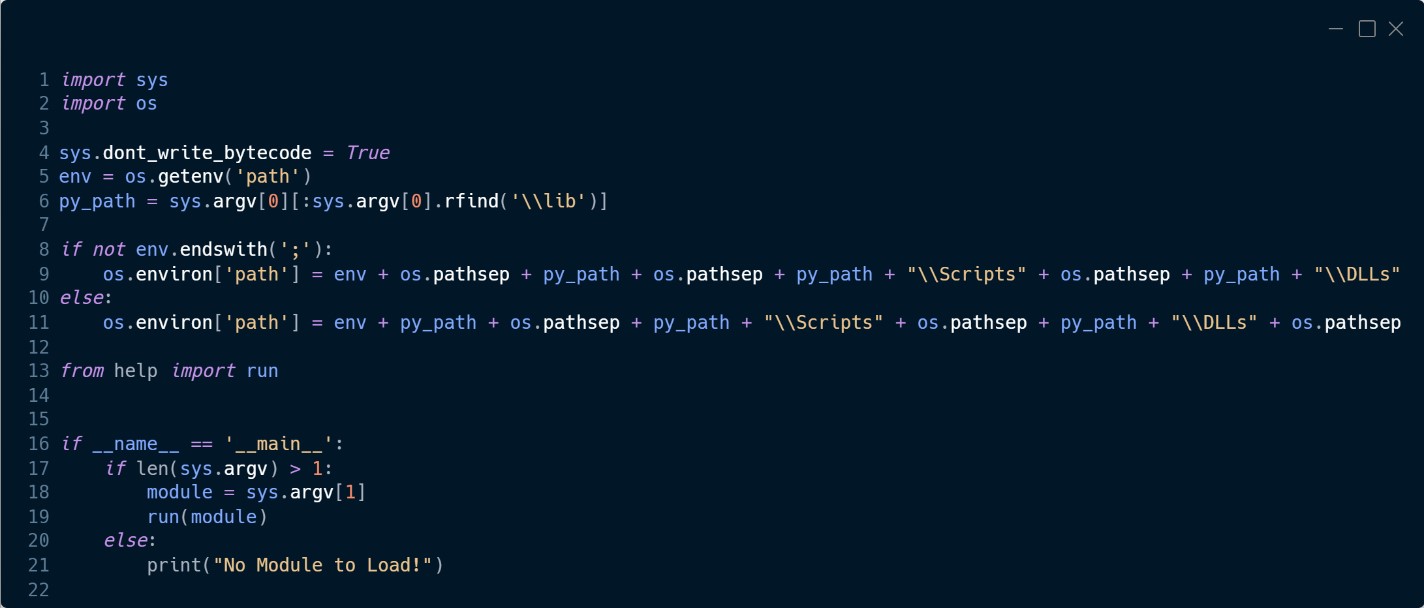
%PUBLICpercentDocumentsWPSDocumentsWPSManagerPythonPythonw.exe -m runas
The module named runas is a customized Python script (Determine 8) that hundreds one other customized Python module named assist from which it makes use of the perform named run to decrypt the module and execute it.
Desk 6 lists the modules that we recovered from the distant repository throughout the time it was obtainable.
Desk 6. Record of Python modules and their goal
| Filename on disk | Authentic module title | Objective |
| 900150983cd24fb0 |
abc | Check module that prints hiya world. |
| ef15fd2f45e6bb5c |
Browser | Collects a variety of information from net browsers: Google Chrome, Microsoft Edge, Opera, Courageous, Vivaldi, Cốc Cốc browser, UC Browser, 360 Browser, and Mozilla Firefox. |
| 967d35e40f3f95b1 |
Digital camera | If the pc has a digital camera linked, it takes photographs. |
| a7ba857c30749bf4 |
CollectInfo | Scans the disk for recordsdata with extensions .txt, .doc, .docx, .xls, .xlsx, .ppt, and .pptx. Collects data from a number of software program titles, together with: LetsVPN, Tencent QQ, WeChat, Kingsoft WPS, e2eSoft VCam, KuGou, Oray Sunlogin, and ToDesk. |
| 6002396e8a3e3aa7 |
Decode | Downloads a module from the distant repository and decrypts it. |
| 9348a97af6e8a2f4 |
DingTalk | Collects a variety of information from DingTalk (a company administration device developed in China), together with chat messages, audio, video, contact data, and teams the person has joined. |
| 801ab24683a4a8c4 |
Obtain | Downloads (non-malicious) Python packages. |
| 16654b501ac48e46 |
FileScanner | Scans the disk for recordsdata, utilizing the identical code as CollectInfo. |
| 7d3b40764db47a45 |
FileScannerAllDisk | |
| 3582f6ebaf9b6129 |
getOperaCookie | Will get cookies from the Opera browser. |
| 10ae9fc7d453b0dd |
record | Lists modules with a .py extension. |
| ce5bf551379459c1 |
Location | Obtains the IP tackle of the pc and the GPS coordinates, utilizing on-line providers. |
| 68e36962b09c99d6 |
Location1 | |
| 5e0a529f8acc19b4 |
LocationByIP | |
| c84fcb037b480bd2 |
PackDir | Creates a ZIP archive of the desired file. |
| 4518dc0ae0ff517b |
qpass | This script seems to be unfinished. It obtains and decrypts passwords from Tencent QQ Browser. Most likely changed by the qqpass module. |
| 5fbf04644f45bb2b |
qqpass | Obtains and decrypts passwords from Google Chrome, Mozilla Firefox, Tencent QQ Browser, 360 Chrome, and UC Browser. |
| 874f5aaef6ec4af8 |
ScreenRecord | Data the display, saving the consequence as an AVI file inside a ZIP archive. |
| c915683f3ec888b8 |
Telegram | Collects account data from the Telegram desktop utility. |
| 104be797a980bcbd |
Webpass | Just like the qqpass module. |
| e5b152ed6b4609e9 |
One of many largest modules, it collects a variety of information from WeChat. | |
| 6d07a4ebf4dff8e5 |
Wechat_all_file | Collects knowledge from WeChat. |
| 17cf4a6dd339a131 |
Wechat_src | |
| 8326cef49f458c94 |
Wechat1 | Just like WeChat. |
| 427f01be70f46f02 |
WechatFile | |
| 72704d83b916fa1f |
WirelessKey | Collects wi-fi community data and passwords, and output from the ipconfig /all command. |
Along with the Python toolkit, we discovered, saved within the distant code repository different instruments (Desk 7) that aren’t encrypted; a few of these had been programmed in C/C++ and others in Go, as famous beneath.
Desk 7. Instruments and their perform
| Device filename | Description |
| agent.mod | Reverse proxy programmed in Go. |
|
getcode.mod getcode64.mod |
Mimikatz. This device is a DLL downloaded by the getpwd command. |
| InitPython.mod | Previous downloader to put in the custom-made Python distribution on the compromised machine. This device is a DLL. |
| Distant.mod | RealVNC server that enables the attackers to remotely management the compromised machine. This device is a DLL. |
| soc.mod |
Reverse proxy programmed in Go. Signed with a certificates from a Chinese language firm referred to as Hangzhou Fuyang Qisheng Info Expertise Service Division. We had been unable to seek out any details about the corporate. |
| stoll.mod |
Device used to carry out downloads, written in Go. Signed with a certificates from the Chinese language firm Zhoushan Xiaowen Software program Improvement Studio. We had been unable to seek out any details about the corporate. |
Conclusion
On this blogpost, we’ve got analyzed a supply-chain assault in opposition to a Korean VPN supplier, concentrating on customers in East Asia, as evident by the particular software program focused for data assortment and confirmed by way of ESET telemetry. We additionally documented the SlowStepper backdoor, used completely by PlushDaemon. This backdoor is notable for its multistage C&C protocol utilizing DNS, and its potential to obtain and execute dozens of extra Python modules with espionage capabilities.
The quite a few parts within the PlushDaemon toolset, and its wealthy model historical past, present that, whereas beforehand unknown, this China-aligned APT group has been working diligently to develop a wide selection of instruments, making it a big risk to look at for.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis provides personal APT intelligence experiences and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete record of indicators of compromise and samples will be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | Detection | Description |
| A8AE42884A8EDFA17E9D |
AutoMsg.dll | Win32/ShellcodeRunner.GZ | Preliminary loader DLL. |
| 2DB60F0ADEF14F4AB357 |
lregdll.dll | Win32/Agent.AGUU | Loader DLL for the SlowStepper backdoor. |
| 846C025F696DA1F6808B |
OldLJM.dll | Win32/Agent.AGXL | Installer DLL, internally named OldLJM.dll. It’s extracted from EncMgr.pkg and executed in reminiscence. |
| AD4F0428FC9290791D55 |
svcghost.exe | Win32/Agent.AGUU | Course of monitor element that launches PerfWatson.exe or RuntimeSvc.exe to side-load lregdll.dll. |
| 401571851A7CF71783A4 |
major.dll | Win32/Agent.AEIJ | Decrypted SlowStepper backdoor element. |
| 068FD2D209C0BBB0C6FC |
IPanyVPNsetup |
Win32/ShellcodeRunner.GZ | Malicious IPany installer. Comprises the SlowStepper implant and the respectable IPany VPN software program. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 202.189.8[.]72 | reverse.wcsset |
Shandong eshinton Community Expertise Co., Ltd. | 2024‑10‑14 | Server utilized by the (reverse proxy) soc.mod device. |
| 47.96.17[.]237 | agt.wcsset[.]com | Hangzhou Alibaba Promoting Co.,Ltd. | 2024‑10‑14 | Server utilized by agent.mod device. |
| N/A | 7051.gsm.360safe |
N/A | 2020‑09‑29 | SlowStepper queries this area to acquire its related DNS TXT report. |
| 202.105.1[.]187 | st.360safe |
IRT-CHINANET-CN | 2021‑03‑11 | Fallback C&C server contacted by SlowStepper. |
| 47.74.159[.]166 | N/A | Alibaba (US) Expertise Co., Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 8.130.87[.]195 | N/A | Hangzhou Alibaba Promoting Co.,Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 47.108.162[.]218 | N/A | Hangzhou Alibaba Promoting Co.,Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 47.113.200[.]18 | N/A | Hangzhou Alibaba Promoting Co.,Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 47.104.138[.]190 | N/A | Guowei Pan | 2020‑09‑29 | SlowStepper C&C server. |
| 120.24.193[.]58 | N/A | Hangzhou Alibaba Promoting Co.,Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 202.189.8[.]87 | N/A | Shandong eshinton Community Expertise Co., Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 202.189.8[.]69 | N/A | Shandong eshinton Community Expertise Co., Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 202.189.8[.]193 | N/A | Shandong eshinton Community Expertise Co., Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
| 47.92.6[.]64 | N/A | Hangzhou Alibaba Promoting Co.,Ltd. | 2020‑09‑29 | SlowStepper C&C server. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 16 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Useful resource Improvement | T1583.001 | Purchase Infrastructure: Domains | PlushDaemon has acquired domains for its C&C infrastructure. |
| T1583.004 | Purchase Infrastructure: Server | PlushDaemon has acquired servers for use as C&C servers. | |
| T1608.001 | Stage Capabilities: Add Malware | PlushDaemon has staged its toolkit within the code repository web site GitCode. | |
| T1608.002 | Stage Capabilities: Add Device | PlushDaemon has staged its toolkit within the code repository web site GitCode. | |
| T1588.001 | Receive Capabilities: Malware | PlushDaemon has entry to SlowStepper. | |
| T1588.002 | Receive Capabilities: Device | PlushDaemon instruments getcode.mod and getcode64.mod use Mimikatz. | |
| T1588.003 | Receive Capabilities: Code Signing Certificates | PlushDaemon instruments soc.mod and stoll.mod are signed. | |
| T1588.005 | Receive Capabilities: Exploits | PlushDaemon has used an unidentified exploit for Apache HTTP server. | |
| Preliminary Entry | T1659 | Content material Injection | PlushDaemon can intercept community site visitors to hijack replace protocols and ship its SlowStepper implant. |
| T1190 | Exploit Public-Going through Utility | PlushDaemon exploited an unidentified vulnerability in Apache HTTP Server. | |
| T1195.002 | Provide Chain Compromise: Compromise Software program Provide Chain | PlushDaemon has compromised the availability chain of a VPN developer and changed the unique installer with a trojanized one containing the SlowStepper implant. | |
| Execution | T1059.003 | Command-Line Interface: Home windows Command Shell | SlowStepper makes use of cmd.exe to execute instructions on a compromised machine. |
| T1059.006 | Command-Line Interface: Python | SlowStepper for Home windows can use the Python console to execute the Python parts of its toolkit. | |
| Persistence | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | The SlowStepper installer establishes persistence by including an entry in HKLMSOFTWAREMicrosoftWindows |
| T1547.004 | Boot or Logon Autostart Execution: Winlogon Helper DLL | The SlowStepper course of monitor element can set up persistence by including an entry in HKLMSoftwareMicrosoftWindows NTCurrentVersionWinlogonUserinit or HKCUSoftwareMicrosoftWindows NTCurrentVersionWinlogonload. | |
| T1574.002 | Hijack Execution Stream: DLL Aspect-Loading | PlushDaemon has abused a respectable command line utility included in Visible Studio referred to as regcap.exe to side-load a malicious DLL named lregdll.dll. | |
| Protection Evasion | T1222.001 | File Permissions Modification: Home windows File and Listing Permissions Modification | SlowStepper modifies the entry rights of the listing the place its parts are saved on disk. |
| T1070.004 | Indicator Removing: File Deletion | SlowStepper can take away its personal recordsdata. | |
| T1036.005 | Masquerading: Match Legit Identify or Location | SlowStepper makes use of folder names and filenames from respectable software program. | |
| T1112 | Modify Registry | SlowStepper can modify the registry. | |
| T1027.007 | Obfuscated Recordsdata or Info: Dynamic API Decision | SlowStepper dynamically resolves Home windows API capabilities. | |
| T1027.009 | Obfuscated Recordsdata or Info: Embedded Payloads | SlowStepper loader DLLs comprise embedded, position-independent code, executed in reminiscence, to load parts. | |
| T1027.013 | Obfuscated Recordsdata or Info: Encrypted/Encoded File | SlowStepper parts are saved encrypted on disk. | |
| T1553.002 | Subvert Belief Controls: Code Signing | PlushDaemon instruments soc.mod and stoll.mod are signed. | |
| Discovery | T1217 | Browser Bookmark Discovery | SlowStepper’s Browser device collects data from browsers. |
| T1083 | File and Listing Discovery | SlowStepper and its instruments can seek for recordsdata with particular extensions, or enumerate recordsdata in directories. | |
| T1120 | Peripheral Machine Discovery | SlowStepper and its toolkit can uncover units linked to the compromised machine. | |
| T1057 | Course of Discovery | SlowStepper can create an inventory of operating processes. | |
| T1012 | Question Registry | SlowStepper can question the registry. | |
| T1518 | Software program Discovery | SlowStepper can create an inventory of software program put in on the compromised machine. | |
| T1082 | System Info Discovery | SlowStepper can accumulate system data. | |
| T1614 | System Location Discovery | SlowStepper’s Location device makes an attempt to find the attainable geolocation of the compromised machine by querying a number of on-line providers. | |
| T1016 | System Community Configuration Discovery | SlowStepper collects data from the community adapters. | |
| T1016.002 | System Community Configuration Discovery: Wi-Fi Discovery | SlowStepper’s Wi-fi device and its variants collects a variety of knowledge from the Wi-Fi community. | |
| T1033 | System Proprietor/Consumer Discovery | SlowStepper obtains the username. | |
| Assortment | T1560.002 | Archive Collected Knowledge: Archive by way of Library | SlowStepper instruments can compress the collected knowledge in ZIP archives. |
| T1123 | Audio Seize | SlowStepper can seize audio if the compromised machine has a microphone. | |
| T1005 | Knowledge from Native System | SlowStepper and its instruments accumulate a variety of information from the compromised system. | |
| T1074.001 | Knowledge Staged: Native Knowledge Staging | SlowStepper and its instruments stage knowledge domestically earlier than exfiltrating it to the C&C server. | |
| T1113 | Display Seize | SlowStepper’s ScreenRecord device can take screenshots. | |
| T1125 | Video Seize | SlowStepper’s Digital camera device can report movies if the compromised machine has a digital camera. | |
| Command and Management | T1071.004 | Normal Utility Layer Protocol: DNS | SlowStepper retrieves a DNS TXT report that incorporates an AES-encrypted record of C&C servers. |
| T1132.001 | Knowledge Encoding: Normal Encoding | SlowStepper retrieves a DNS TXT report that incorporates an AES-encrypted record of C&C servers. The report is base64 encoded. | |
| T1573.001 | Encrypted Channel: Symmetric Cryptography | SlowStepper’s communication protocol with its C&C is encrypted with AES. | |
| T1008 | Fallback Channels | SlowStepper will get a fallback C&C server IP tackle by resolving another area managed by the attackers. | |
| T1105 | Distant File Copy | SlowStepper downloads extra instruments from a distant code repository at GitCode. | |
| T1104 | Multi-Stage Channels | SlowStepper obtains an inventory of C&C servers by querying the DNS TXT report from a site managed by the attackers; if no communication will be established with the servers, it resolves the IP tackle of one other area managed by the attackers to acquire a backup server. SlowStepper instruments use totally different servers from PlushDaemon infrastructure. |
|
| T1095 | Normal Non-Utility Layer Protocol | SlowStepper communicates with its C&C by way of TCP. | |
| T1090 | Connection Proxy | SlowStepper instruments agent.mod and soc.mod are reverse proxies. | |
| T1219 | Distant Entry Instruments | SlowStepper device Distant.mod permits its operator to remotely management the compromised machine by way of VNC. | |
| Exfiltration | T1020 | Automated Exfiltration | SlowStepper can exfiltrate staged knowledge. |
| T1041 | Exfiltration Over C2 Channel | SlowStepper exfiltrates collected knowledge when linked to one among its C&C servers. |

