Think about you might be launching a brand new digital service: it’s essential to shortly confirm the authenticity of buyer paperwork, securely retailer knowledge, and automate settlements with companions in numerous nations. An error in these processes can price an organization tens of millions, and a sluggish system will drive clients away.
That’s the reason enterprise house owners are more and more turning their consideration to Distributed Ledger Applied sciences (DLT).
In line with Statista, the worldwide DLT market will exceed $127 billion by 2030 — a rise of greater than $100 billion in comparison with 2020. The primary driver is provide chain audits, which is able to attain $103 billion by the top of the last decade, however different areas are additionally actively growing: digital id, good contracts, and immutable data.
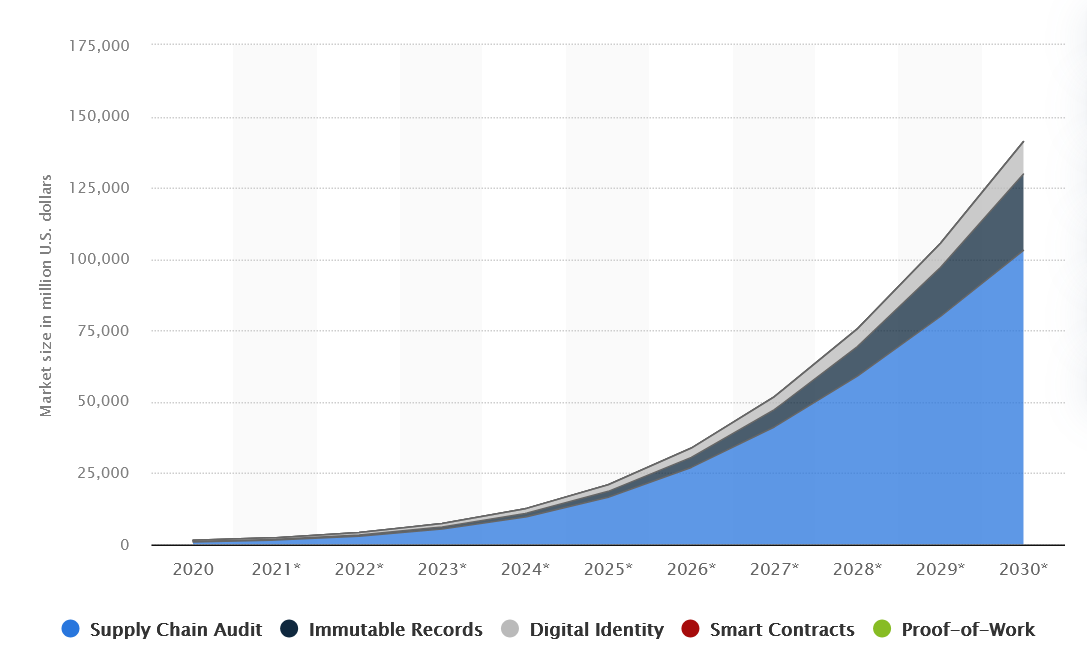
Distributed ledger market dimension worldwide from 2020 to 2030
Amid this speedy growth, the query of “hashgraph vs blockchain” has grow to be a key consideration for companies and builders exploring distributed ledger applied sciences.
On the one hand, blockchain has grow to be the inspiration for initiatives similar to Bitcoin and Ethereum, proving that decentralization can efficiently work in actual enterprise.
Then again, hashgraph presents a distinct path: larger transaction pace, energy-efficient consensus, and new alternatives for enterprise options.
For firms, that is now not a query of “know-how for know-how’s sake.” It’s a strategic selection: on which platform to construct digital merchandise and enterprise providers as a way to stay aggressive tomorrow.
Fundamentals of Distributed Ledger Applied sciences (DLT)
At the moment, many firms are contemplating implementing digital options the place belief in knowledge performs a key position.

Think about a scenario: a number of companions from totally different nations are engaged on one venture, and every of them must make sure that the data of transactions or paperwork are correct and can’t be tampered with.
In conventional programs, this belief is supplied by a single central authority — a financial institution, a authorities company, or a service supplier. However what if there isn’t a middle?
Distributed ledger applied sciences step in right here, serving because the spine for improvements like blockchain and hashgraph, and more and more turning into a subject of lively dialogue within the enterprise world.
What Is DLT?
Distributed Ledger Applied sciences (DLT) are a means of concurrently storing and synchronizing knowledge throughout all individuals in a community. As an alternative of counting on a single server, data is copied and up to date throughout a number of nodes on the identical time.
The important thing distinction is straightforward. A centralized system relies on one operator. If that operator goes down, everybody feels the impression. With DLT, the information is unfold out, so each participant sees the identical model of occasions. This makes the system extra clear and far tougher to interrupt.
Due to this, firms can construct providers the place individuals belief the information with out having to belief one another instantly.
The primary real-world purposes of distributed ledgers had been made attainable by the appearance of blockchain, which first gained consideration via cryptocurrencies. In 2009, Bitcoin confirmed that worth could possibly be exchanged instantly between people with out counting on banks or intermediaries.
A couple of years later, Ethereum expanded the idea of blockchain by introducing good contracts — self-executing applications that mechanically perform agreements. These improvements pushed blockchain far past the crypto group and paved the way in which for a variety of enterprise purposes.

Hashgraph as a New Sort of DLT
If blockchain was the primary mass type of DLT, then hashgraph know-how is positioned as its improvement.
Not like a linear chain of blocks, hashgraph makes use of the construction of a directed acyclic graph (DAG), the place transactions are recorded not one after the other, however in parallel. This enables processing hundreds of transactions per second with minimal prices.
The primary variations from conventional blockchain are:
- Velocity — hashgraph can deal with as much as 10,000 transactions per second, whereas Bitcoin is proscribed to about 7 and Ethereum to round 30 (these numbers are for public blockchains; personal ones can course of as much as 2,000 transactions per second).
- Power effectivity — due to the digital voting mechanism and gossip protocol, the community doesn’t require resource-intensive computations like PoW.
- Transaction finality — confirmations happen immediately, with out the necessity to look ahead to a number of blocks.
Variations Between Hashgraph and Blockchain
To grasp the variations between blockchain and hashgraph, you will need to analyze how they work. At first look, each applied sciences fall beneath DLT and clear up an analogous drawback — storing and verifying knowledge in a decentralized community. Nonetheless, their mechanisms and structure differ considerably.
How Does Blockchain Work?
In blockchain, knowledge is grouped into blocks which are linked into a series. Every new block is linked to the earlier one, and altering an outdated file with out altering all the chain is virtually not possible.
The community is maintained by nodes (computer systems) that validate transactions and retailer similar copies of the database. Blockchain additionally helps good contracts — small applications that mechanically execute the phrases of an settlement.
To resolve which transactions are legitimate, the community makes use of a consensus mechanism. The preferred choices are:
- Proof-of-Work (PoW) — utilized in Bitcoin, the place miners clear up puzzles so as to add a block (dependable, however very energy-intensive).
- Proof-of-Stake (PoS) — for instance, in Ethereum: new blocks are validated by individuals who’ve staked their cryptocurrency. This technique is quicker and extra resource-efficient.
How Does Hashgraph Work?
Hashgraph works otherwise. There isn’t a chain of blocks. As we said above, it makes use of a construction referred to as a DAG (Directed Acyclic Graph), the place transactions are recorded in parallel fairly than one after the other, which supplies the community higher pace.
Data in hashgraph spreads via the gossip-about-gossip technique: every node shares what it is aware of with others, and on this means, knowledge shortly propagates throughout all the community.
On this foundation, digital voting is used: nodes don’t must vote; they’ll merely calculate the consequence, since all of them have the identical data. That is the hashgraph consensus — a quick, honest, and safe option to agree on the validity of transactions.
Hashgraph vs Blockchain: Detailed Comparability
For companies, selecting the best blockchain community or various DLT like Hedera Hashgraph is a strategic determination.
We have now already checked out how blockchain and hashgraph work, however for companies, you will need to see the clear variations in figures and traits. The desk beneath supplies a side-by-side comparability of each applied sciences throughout key parameters — from structure to efficiency.
| Criterion |
Blockchain |
Hashgraph (Hedera) |
| Structure |
Linear chain of blocks. Every transaction is added sequentially. |
Directed Acyclic Graph (DAG). Transactions are recorded in parallel. |
| Throughput |
Restricted: Bitcoin ~7 TPS, Ethereum ~30 TPS (for public blockchains). |
Excessive: as much as 10,000+ TPS within the Hedera Hashgraph community. |
| Transaction price |
May be excessive beneath load: from just a few cents to tens of {dollars} (for public blockchains). |
Very low: fractions of a cent per transaction. |
| Consensus algorithm |
Proof-of-Work (energy-intensive) or Proof-of-Stake (less expensive however complicated to handle). |
Hashgraph consensus primarily based on gossip-about-gossip and digital voting. |
| Power effectivity |
Low in PoW (enormous mining prices), larger in PoS. |
Very excessive: no heavy computations, solely data trade. |
| Safety |
Weak to 51% assault: an attacker with majority energy can rewrite historical past. |
Asynchronous Byzantine Fault Tolerance (ABFT). The community stays trustworthy even when some nodes fail. |
| Finality |
Requires ready for a number of blocks (in public blockchains): in Bitcoin — as much as 60 minutes. |
Immediate finality — transactions are confirmed straight away. |
| Scalability |
Restricted: larger load = larger charges and slower confirmations. |
Excessive: designed for enterprise-level efficiency. |
| Use circumstances |
Bitcoin, Ethereum, DeFi, NFT, provide chain (business-specific options for personal blockchains can be found). |
Hedera Hashgraph: micropayments, digital id, enterprise purposes. |
Hashgraph vs Blockchain
Overview of Hedera Hashgraph
When individuals discuss hashgraph, they often imply its most well-known implementation — the Hedera Hashgraph platform. This community grew to become one of many first sensible makes an attempt to show DAG know-how and hashgraph consensus right into a working ecosystem out there to firms and customers worldwide.
What Is the Hedera Hashgraph Platform?
Hedera Hashgraph is a public community designed to provide companies and builders a quick, safe, and scalable means to make use of distributed ledgers. Not like many blockchains, Hedera shouldn’t be constructed round cryptocurrency as its core worth. As an alternative, it supplies a platform for creating purposes — from micropayments to digital id programs.
Key options:
- Excessive efficiency: hundreds of transactions per second with low charges.
- Transparency and belief: all individuals have equal entry to knowledge.
- Power effectivity: no pricey mining, not like blockchain.
The community is ruled by the Hedera Governing Council — a board that features main international firms (Google, IBM, Boeing, and others). This strategy builds belief with companies, since choices are made not by a single operator however by a gaggle of unbiased individuals.
Hedera Hashgraph and Blockchain: Competitors or Coexistence?
Many firms wonder if Hedera Hashgraph can substitute present blockchain options or no less than combine with them. In observe, it’s extra about coexistence than competitors.
Hedera doesn’t set itself in opposition to blockchain however fairly enhances the DLT ecosystem. It may be used as a standalone platform or alongside different applied sciences. For instance, hashgraph is right for micropayments, high-throughput purposes, or IoT, whereas blockchain retains its sturdy place in cryptocurrencies, DeFi, and NFTs due to its mature infrastructure and broad ecosystem.
By way of strengths:
- Hashgraph wins the place pace, scalability, low transaction price, and on the spot finality are important.
- Blockchain stays indispensable the place market belief and ecosystem maturity matter most — cryptocurrencies, DeFi, NFTs, and large-scale public initiatives.
Thus, within the coming years, companies ought to focus not on selecting “either-or” however on hybrid architectures the place blockchain and hashgraph are utilized collectively, relying on the duty.
Way forward for DLT: Can Hashgraph Exchange Blockchain?
At the moment, it’s tough to call a transparent winner within the debate between blockchain and hashgraph. On the one hand, blockchain has already confirmed its worth: it has grow to be the inspiration for the most important cryptocurrencies, hundreds of initiatives are constructed on it, and buyers proceed to pour billions into its ecosystem.
Then again, hashgraph is step by step attracting market consideration, particularly via the Hedera Hashgraph community, which is supported by main international companies. Its pace, vitality effectivity, and dependable consensus make the know-how interesting for enterprise options.
In line with analysts, the DLT market will develop to a whole lot of billions of {dollars} by 2030, and each blockchain and hashgraph will share on this development. It’s unlikely that one know-how will utterly substitute the opposite.

SCAND and Distributed Ledger Applied sciences Improvement
At SCAND, we’ve intensive expertise in growing options primarily based on blockchain applied sciences — from good contracts and crypto wallets to decentralized purposes (DAO, DeFi, NFT, and Web3). We assist firms leverage distributed ledgers to enhance transparency, safety, and automation of enterprise processes.
These days, we’ve been actively exploring the potential of the Hedera Hashgraph community. This know-how opens new alternatives for enterprise options due to its excessive transaction pace, vitality effectivity, and on the spot finality.
Why select us:
- We have now deep experience in good contract improvement, blockchain improvement, and work with numerous DLT platforms.
- We ship customized options tailor-made to particular enterprise wants — whether or not it’s fee programs, digital id, provide chain administration, or micropayments.
We see ourselves not simply as builders however as a companion who helps combine trendy DLT options and unlock their potential for enterprise development and competitiveness.

















