Uncover how prime modifying is redefining the way forward for medication by providing extremely exact, secure, and versatile DNA corrections, bringing hope for simpler therapies for genetic ailments whereas elevating essential scientific and moral questions.
Introduction
What if we may rewrite the genetic code of a single cell with surgical precision? Prime modifying, the following leap in genome engineering, allows extremely correct DNA corrections with out damaging the genetic code, paving the way in which for safer and simpler therapies for genetic issues.
As know-how evolves, prime modifying exhibits promise in changing into a cornerstone of personalised medication. This text explores the basics of prime modifying, its variations from different gene modifying applied sciences, the underlying mechanisms, potential medical functions, in addition to the scientific and moral challenges that lie forward.
What’s Prime Modifying?
Launched in 2019 by a group of researchers from the Broad Institute on the Massachusetts Institute of Expertise and Harvard College, prime modifying builds upon clustered commonly interspaced quick palindromic repeats (CRISPR), redefining therapeutic approaches to numerous genetic issues.1
Prime modifying is a next-generation gene-editing method designed to right, insert, or delete particular DNA sequences with out inflicting double-stranded breaks or counting on donor DNA templates. As in comparison with earlier genome modifying strategies comparable to zinc finger nucleases (ZFNs), transcription activator-like effector nucleases (TALENs), and CRISPR-CRISPR-associated protein 9 (Cas9), prime modifying affords a extra exact and versatile various with fewer off-target results.3,4
Typical CRISPR-Cas9 techniques edit DNA by creating double-stranded breaks at focused genomic areas, adopted by mobile restore by way of both non-homologous finish becoming a member of or homology-directed restore. Whereas efficient, this course of can lead to unintended DNA insertions or deletions, also called indels, and is primarily restricted to dividing cells.5
Comparatively, prime modifying depends on Cas9 nickase, a modified CRISPR-Cas9 system, fused to a reverse transcriptase enzyme able to figuring out and subsequently changing particular DNA sequences with greater precision and decrease danger.5 Since its introduction in 2019 by David Liu and colleagues, prime modifying has quickly change into a spotlight of intensive analysis, with a number of enhancements which have enhanced its effectivity and applicability in therapeutic settings.6
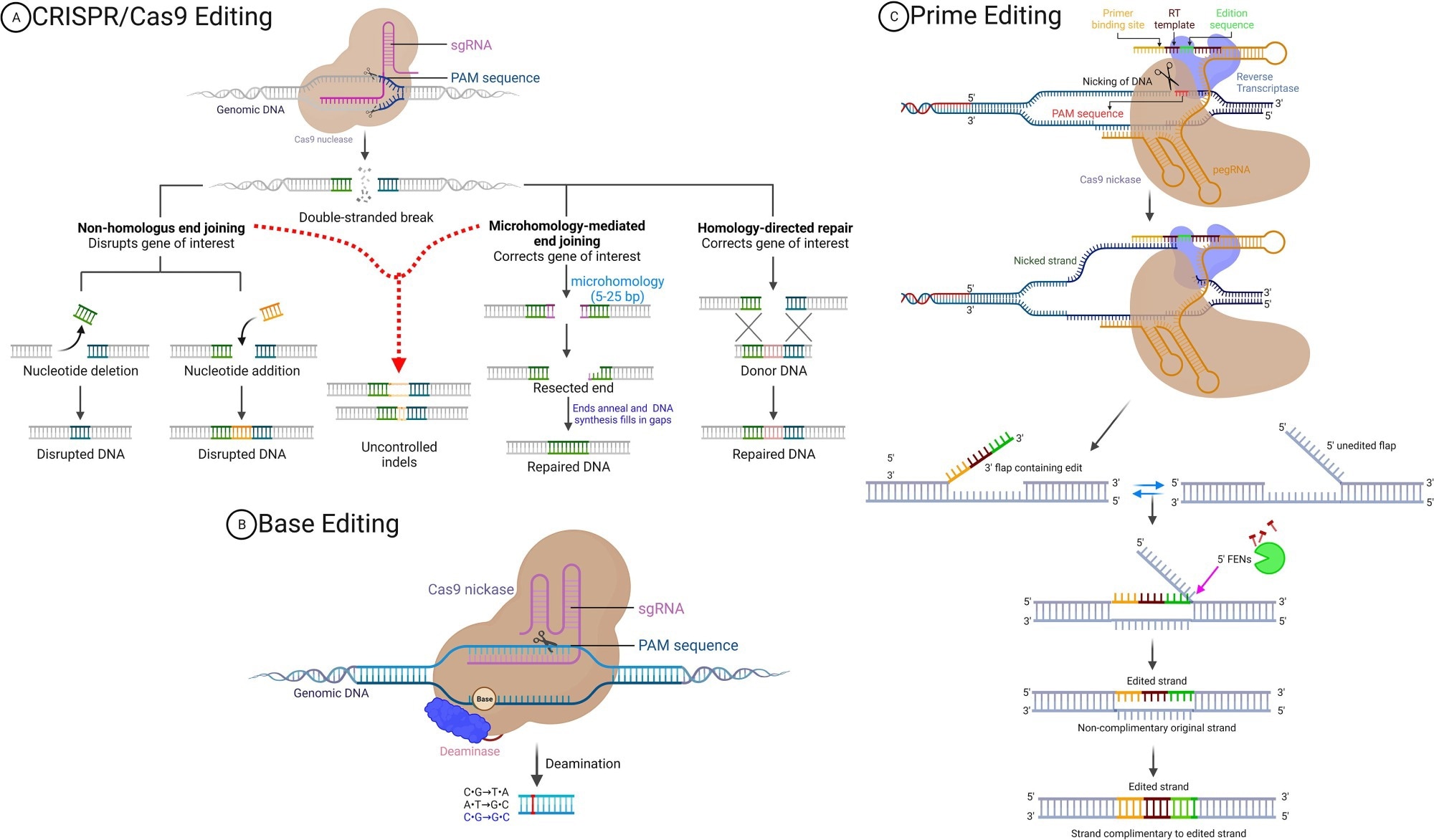
How Does Prime Modifying Work?
Prime editors (PEs) include a three-component system together with a Cas9 nickase, which is conjugated to an engineered reverse transcriptase paired with a primary modifying information ribonucleic acid (pegRNA). Initially, pegRNA will bind to the goal DNA sequence by way of complementary base pairing, following which the Cas9 nickase nicks the non-target strand.
pegRNA serves the twin goal of guiding the PE protein to the focused locus and encoding the specified edit.”
The pegRNA subsequently makes use of the reverse transcription template to synthesize the specified DNA sequence on the break website. Ligation and DNA mismatch restore (MMR) are then initiated to repeat data from the modifying strand to the unedited strand, which leads to the specified modification to the genome.3,6
“Prime Modifying” Revolutionizing Genetic Engineering
Benefits of Prime Modifying
Prime modifying affords quite a few benefits as in comparison with earlier genome modifying instruments.
The flexibility of prime modifying, for instance, allows all 12 attainable base-to-base conversions and helps small insertions and deletions, thus providing immense flexibility for exact genomic modifications. Prime modifying can be extremely exact, which considerably reduces the chance of unintended mutations and off-target results as in comparison with CRISPR-Cas9, thereby making it a safer various for therapeutic functions.7
Prime modifying can perform in each dividing and non-dividing cells, thereby broadening its utility in tissues comparable to neurons and muscle cells that had been beforehand difficult to edit. This know-how additionally eliminates the necessity for double-strand breaks or donor templates, thereby minimizing mobile stress and enhancing modifying outcomes.5
Potential Purposes in Well being and Medication
Prime modifying is presently being explored as a novel method for the remedy of genetic ailments, most cancers, and infectious ailments.
This environment friendly device can right as much as 89% of beforehand found genetic variants which might be related to human ailments.”
Monogenic Illnesses
Prime modifying has been broadly studied in each in vitro and in vivo preclinical fashions to right genetic mutations accountable for Duchenne muscular dystrophy, Leber congenital amaurosis, tyrosinemia, α1-Antitrypsin deficiency (AATD), and phenylketonuria. Though quite a few prime editors (PEs) have been investigated and offered promising outcomes, further research utilizing greater animal fashions are warranted earlier than this know-how will be evaluated in human topics.3
Most cancers analysis
Chemotherapy, radiation, and surgical procedure are the first therapies used for the remedy of most cancers, along with hormonal and focused immunotherapies when relevant. Nonetheless, these approaches are related to quite a few undesirable and significant unwanted effects, which warrant the event of secure and extra focused methods.
Numerous genetic mutations have been implicated in most cancers because the driving reason behind non-cancerous cells reworking into most cancers cells attributable to altered protein expression. Gene modifying applied sciences like CRISPR Cas9 and prime modifying have been broadly studied for his or her potential to right these malignant mutations, in addition to induce cancer-related mutations in preclinical fashions used to research novel therapeutics.
Infectious ailments
There may be rising curiosity in utilizing prime modifying to supply resistance to viral infections or take away built-in viral genomes from host DNA, thereby stopping the virus from being reactivated. This might present everlasting immunity or viral elimination.4
Preventive genomics
Making exact adjustments within the genome raises the potential of utilizing prime modifying in germ cells or embryos to create adjustments that may very well be inherited. Nonetheless, these functions stay ethically contentious and tightly regulated.10
Present Standing of Medical Analysis
Most prime modifying functions are preclinical and, consequently, have been restricted to in vitro and in vivo fashions. Nonetheless, ex vivo modifying of affected person cells adopted by transplantation has offered substantial hope for profitable future scientific translation.8
Challenges and Moral Concerns
A number of scientific, technical, and moral considerations should be addressed earlier than prime modifying turns into normal follow. The big dimension of PEs makes supply by way of viral vectors tough, which has led researchers to research the potential utility of non-viral platforms and optimized vectors for prime modifying functions.5
Modifying effectivity additionally varies considerably relying on the situation of the gene and the kind of cell. To beat these challenges, researchers are actively creating methods to enhance pegRNA design, reverse transcriptase exercise, and the mobile restore atmosphere.1
The misuse of genome modifying for non-therapeutic functions and the enhancement of designer traits is a main moral concern. To handle these points, regulatory our bodies comparable to the US Meals and Drug Administration (FDA) are creating frameworks for the accountable use of prime modifying know-how.10
Conclusions
Prime modifying represents a strong device for genetic engineering.
Additional analysis is required to proceed advancing gene modifying applied sciences, specializing in growing effectivity, enhancing DNA supply, and enhancing security. An interdisciplinary method and continued public engagement are additionally essential to make sure that prime modifying is used safely and ethically.
References
- Zhao, Z., Shang, P., Mohanraju, P., & Geijsen, N. (2023). Prime modifying: advances and therapeutic functions. Developments in Biotechnology, 41(8), 1000–1012. DOI:10.1016/j.tibtech.2023.03.004, https://www.sciencedirect.com/science/article/pii/S0167779923000859
- Anzalone, A. V., Randolph, P. B., Davis, J. R., Sousa, A. A., Koblan, L. W., Levy, J. M., Chen, P. J., Wilson, C., Newby, G. A., Raguram, A., & Liu, D. R. (2019). Search-and-replace genome modifying with out double-strand breaks or donor DNA. Nature, 576(7785), 149–157. DOI:10.1038/s41586-019-1711-4, https://www.nature.com/articles/s41586-019-1711-4
- Fu, Y., He, X., Gao, X. D., Li, F., Ge, S., Yang, Z., & Fan, X. (2023). Prime modifying: present advances and therapeutic alternatives in human ailments. Science Bulletin, 68(24), 3278–3291. DOI:10.1016/j.scib.2023.11.015, https://www.sciencedirect.com/science/article/pii/S2095927323007697
- Hosseini, S. Y., Mallick, R., Mäkinen, P., & Ylä-Herttuala, S. (2024). Insights into Prime Modifying Expertise: A Deep Dive into Fundamentals, Potentials, and Challenges. Human Gene Remedy, 35(17-18), 649–668. DOI:10.1089/hum.2024.043, https://www.liebertpub.com/doi/10.1089/hum.2024.043
- Li, M., Lin, Y., Cheng, Q., & Wei, T. (2025). Prime Modifying: A Revolutionary Expertise for Exact Remedy of Genetic Issues. Cell Proliferation, 58(4), e13808. DOI:10.1111/cpr.13808, https://onlinelibrary.wiley.com/doi/full/10.1111/cpr.13808
- Scholefield, J., & Harrison, P. T. (2021). Prime Modifying – An Replace on the Discipline. Gene Remedy, 28(7-8), 396–401. DOI:10.1038/s41434-021-00263-9, https://www.nature.com/articles/s41434-021-00263-9
- Gao, P., Lyu, Q., Ghanam, A. R., Lazzarotto, C. R., Newby, G. A., Zhang, W., Choi, M., Slivano, O. J., Holden, Okay., Walker, J. A., 2nd, Kadina, A. P., Munroe, R. J., Abratte, C. M., Schimenti, J. C., Liu, D. R., Tsai, S. Q., Lengthy, X., & Miano, J. M. (2021). Prime modifying in mice reveals the essentiality of a single base in driving tissue-specific gene expression. Genome Biology, 22(1), 83. DOI:10.1186/s13059-021-02304-3, https://genomebiology.biomedcentral.com/articles/10.1186/s13059-021-02304-3
- Everette, Okay.A., Newby, G.A., Levine, R.M. et al. Ex vivo prime modifying of affected person haematopoietic stem cells rescues sickle-cell illness phenotypes after engraftment in mice. Nature Biomedical Engineering 7, 616–628 (2023). DOI:10.1038/s41551-023-01026-0, https://www.nature.com/articles/s41551-023-01026-0
- Sousa, A. A., Hemez, C., Lei, L., Traore, S., Kulhankova, Okay., Newby, G. A., Doman, J. L., Oye, Okay., Pandey, S., Karp, P. H., McCray, P. B., Jr, & Liu, D. R. (2025). Systematic optimization of prime modifying for the environment friendly practical correction of CFTR F508del in human airway epithelial cells. Nature Biomedical Engineering, 9(1), 7–21. DOI:10.1038/s41551-024-01233-3, https://www.nature.com/articles/s41551-024-01233-3
- Rothschild J. (2020). Moral concerns of gene modifying and genetic choice. Journal of Common and Household Medication, 21(3), 37–47. DOI:10.1002/jgf2.321, https://onlinelibrary.wiley.com/doi/full/10.1002/jgf2.321





