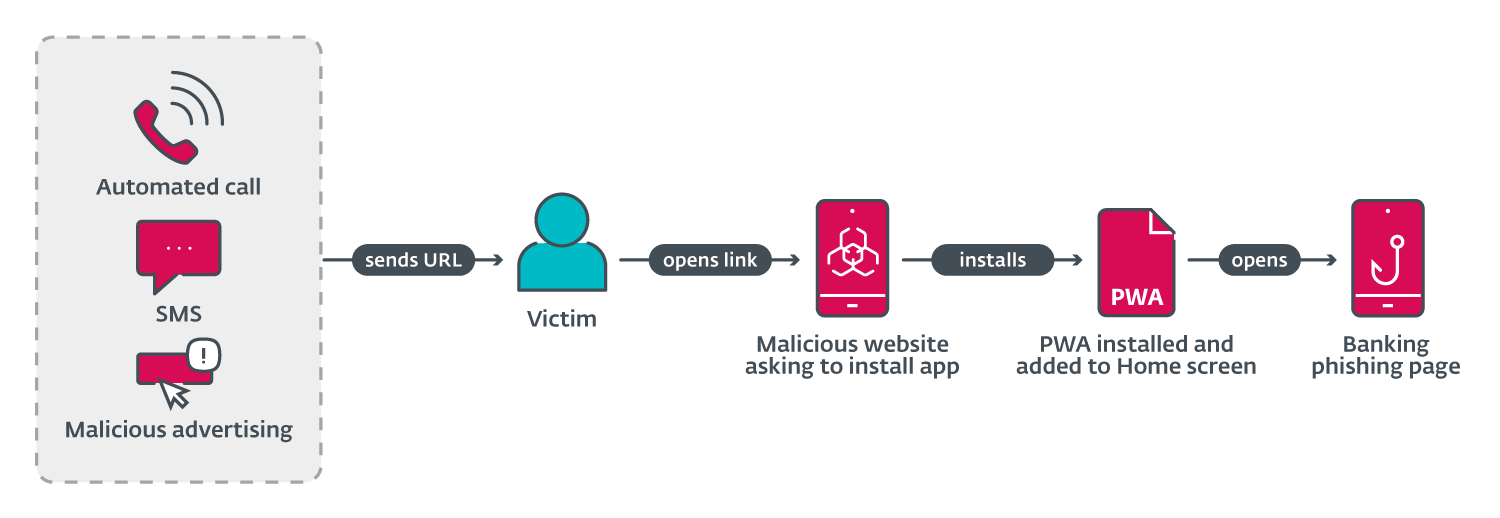
.png?width=1000&height=556&name=Do%20LLMs%20Reign%20Supreme%20in%20Few-Shot%20NER_%20(1).png)
In our earlier weblog posts within the collection, we’ve described conventional strategies for few-shot named entity recognition (NER) and mentioned how massive language fashions (LLMs) are getting used to unravel the NER activity. On this submit, we shut the hole between these two areas and apply an LLM-based technique for few-shot NER.
As a reminder, NER is the duty of discovering and categorizing named entities in textual content, for instance, names of individuals, organizations, places, and many others. In a few-shot situation, there are solely a handful of labeled examples out there for coaching or adapting an NER system, in distinction to the huge quantities of information sometimes wanted to coach a deep studying mannequin.
Instance of a labeled NER sentence
Utilizing LLMs for few-shot NER
Whereas Transformer-based fashions, comparable to BERT, have been used as a spine for fashions fine-tuned to NER for fairly a while, not too long ago there’s growing curiosity in understanding the effectiveness of prompting pre-trained decoder-only LLMs with few-shot examples for a wide range of duties.
GPT-NER is a technique of prompting LLMs to carry out NER proposed by Shuhe Wang et al. They immediate a language mannequin to detect a category of named entities, displaying just a few enter and output examples within the immediate, the place within the output the entities are marked with particular symbols (@@ marks the beginning and ## the top of a named entity).
A GPT-NER immediate. All occasion entities within the instance outputs within the immediate are marked with “@@” (starting of the named entity) and “##” (finish of the named entity)
Whereas Wang et al. consider their technique within the low-resource setting, they imitate this situation by deciding on a random subset of a bigger, general-purpose dataset (CoNLL-2003). Additionally they put appreciable emphasis on selecting the very best few-shot examples to incorporate within the immediate; nevertheless, in a really few-shot situation there is no such thing as a wealth of examples to select from.
To shut this hole, we apply the prompting technique in a real few-shot situation, utilizing a purposefully constructed dataset for few-shot NER, particularly, the Few-NERD dataset.
What’s Few-NERD?
The duty of few-shot NER has gained recognition in recent times, however there’s not a lot benchmark knowledge targeted on this particular activity. Typically, knowledge shortage for the few-shot case is simulated by utilizing a bigger dataset and deciding on a random subset of it to make use of for coaching. Few-NERD is one dataset that was designed particularly for the few-shot NER activity.
The few-shot dataset is organized in episodes. Every episode consists of a help set containing a number of few-shot examples (labeled sentences), and a question set for which labels must be predicted utilizing the knowledge of the help set. The dataset has coaching, improvement, and check splits; nevertheless, as we’re utilizing a pre-trained LLM with none fine-tuning, we solely use the check cut up in our experiments. The help units function the few-shot examples offered within the immediate, and we predict the labels for the question units.
Coarse- and fine-grained entity varieties within the Few-NERD dataset (Ding et al., 2021)
The categories, or lessons, of named entities in Few-NERD have two ranges: coarse-grained (particular person, location, and many others.) and fine-grained (e.g. actor is a subclass of particular person, island is a subclass of location, and many others.). In our experiments described right here, we solely take care of the simpler coarse-grained classification.
The total dataset features a few duties. There’s a supervised activity, which isn’t few-shot and isn’t organized in episodes: the information is cut up into practice (70% of all knowledge), improvement (10%), and check (20%) units. The few-shot activity organizes knowledge in episodes. Furthermore, there’s a distinction between the inter and intra duties. Within the intra activity, every coarse-grained entity sort will solely be labeled in one of many practice, improvement, and check splits, and will likely be utterly unseen within the different two. We use the second activity, inter, the place the identical coarse-grained entity sort might seem in all knowledge splits (practice, improvement, and check), however any fine-grained sort will solely be labeled in one of many splits. Moreover, the dataset contains variants the place both 5 or 10 entity varieties are current in an episode, and the place both 1-2 or 5-10 examples per class are included within the help set of an episode.
How good are LLMs at few-shot NER?
In our experiments, we aimed to judge the GPT-NER prompting setup, however a) do this in a really few-shot situation utilizing the Few-NERD dataset, and b) use LLMs from Llama 2 household, which can be found on the Clarifai platform, as an alternative of the closed fashions utilized by the GPT-NER authors. Our code might be present in this Github repository.
We intention to reply these questions:
- How can the prompting type of GPT-NER be utilized to the really few-shot NER setting?
- How do in a different way sized open LLMs examine to one another on this activity?
- How does the variety of examples have an effect on few-shot efficiency?
Outcomes
We examine the outcomes alongside two dimensions: first, we examine the efficiency of various Llama 2 mannequin sizes on the identical dataset; then, we additionally examine the conduct of the fashions when a special variety of few-shot input-output examples are proven within the immediate.
1) Mannequin dimension
We in contrast the three different-sized Llama-2-chat fashions out there on the Clarifai platform. For example, allow us to have a look at the scores of 7B, 13B, and 70B fashions on the inter 5-way 1-2-shot Few-NERD check set.
The most important, 70B mannequin has the perfect F1 scores, however the 13B mannequin is worse on this metric than the smallest 7B mannequin.
F1 scores of Llama 2 7B (blue), 13B (cyan), and 70B (black) fashions on the “inter” 5-way, 1~2-shot check set of Few-NERD
Nevertheless, if we have a look at the precision and recall metrics which contribute to F1, the state of affairs turns into much more nuanced. The 13B mannequin seems to have the perfect precision scores out of all three mannequin sizes, and the 70B mannequin is, actually, the worst on precision for all lessons.
Precision scores of Llama 2 7B (blue), 13B (cyan), and 70B (black) fashions on the “inter” 5-way, 1~2-shot check set of Few-NERD
That is compensated by recall, which is way greater for the 70B mannequin than for the smaller ones. Thus, evidently the most important mannequin detects extra named entities than the others, however the 13B mannequin must be extra sure about named entities to detect them. From these outcomes, we will anticipate the 13B mannequin to have the fewest false positives, and the 70B the fewest false negatives, whereas the smallest, 7B mannequin falls someplace in between on each kinds of errors.
Recall scores of Llama 2 7B (blue), 13B (cyan), and 70B (black) fashions on the “inter” 5-way, 1~2-shot check set of Few-NERD
2) Variety of examples in immediate
We additionally examine in a different way sized Llama 2 fashions on datasets with totally different numbers of named entity examples in few-shot prompts: 1-2 or 5-10 examples per (fine-grained) class.
As anticipated, all fashions do higher when there are extra few-shot examples within the immediate. On the similar time, we discover that the distinction in scores is way smaller for the 70B mannequin than for the smaller ones, which means that the bigger mannequin can do effectively with fewer examples. The development will not be solely in line with mannequin dimension although: for the medium-sized 13B mannequin, the distinction between seeing 1-2 or 5-10 examples within the immediate is probably the most drastic.
F1 scores of Llama 2 7B (left), 13B (middle), and 70B (proper) fashions on the “inter” 5-way 1~2-shot (blue) and 5~10-shot (cyan) check units of Few-NERD
Challenges with utilizing LLMs for few-shot NER
A couple of points must be thought of once we immediate LLMs to do NER within the GPT-NER type.
- The GPT-NER immediate template solely makes use of one set of tags within the output, and the mannequin is simply requested to search out one particular sort of named entity at a time. Which means that, if we have to establish just a few totally different lessons, we have to question the mannequin a number of occasions, asking a few totally different named entity class each time. This may occasionally develop into resource-intensive and gradual, particularly because the variety of totally different lessons grows.
A single sentence usually comprises multiple entity sort, which suggests the LLM must be prompted individually for every sort
- The subsequent difficulty can be associated to the truth that the LLM is queried for every entity sort individually. A conventional token classification system would sometimes predict one set of sophistication possibilities for every token. Nevertheless, in our case, if we’re utilizing the LLM as a black field (solely its textual content output and never inside token possibilities), we solely get sure/no solutions, however a number of of them for every token (as many as there are attainable lessons). Which means that, if the mannequin’s prediction for a similar token is constructive for multiple class, there is no such thing as a simple technique to know which of these lessons is extra possible. This reality additionally makes it exhausting to calculate total metrics for a check set, and we’ve to make do with per-class analysis solely.
- The model-generated output can be not all the time well-formed. Typically, the mannequin will generate the opening tag for an entity (@@), however not the closing one (##), or another invalid mixture. As with many purposes of LLMs to formalized duties, this requires an additional step of verifying the validity of the mannequin’s free-form output and parsing it into structured predictions.
Typically, the mannequin output will not be well-formed: in output 1, there’s the opening tag “@@”, however the closing tag “##” by no means seems; in output 2, the mannequin used the opening tag as an alternative of the closing one
- There are just a few different points associated to the mannequin’s manner of producing output. As an illustration, it tends to over-generate: when requested to solely tag one enter sentence in response to the given format, it does that, however then continues creating its personal input-output examples, persevering with the sample of the immediate, and generally additionally tries to offer explanations. Attributable to this, we discovered it greatest to restrict the utmost size of the mannequin’s output to keep away from pointless computation.
After producing the output sentence, the LLM retains inventing new input-output pairs
- Furthermore, the LLM’s output sentence doesn’t have to precisely replicate the enter. For instance, though the enter sentences in GPT-NER are tokenized, the mannequin outputs de-tokenized texts, in all probability as a result of it has realized to supply solely (or virtually solely) well-formed, de-tokenized textual content. Whereas this provides one other further step of tokenizing the output textual content once more to do analysis later, that step is straightforward to do. A much bigger downside might seem when the mannequin doesn’t really use all the identical tokens as got within the enter. We have now seen, for instance, that the mannequin might translate overseas phrases into English, which makes it tougher to match output tokens to enter ones. These points associated to output might doubtlessly be mitigated by extra subtle immediate engineering.
Typically the LLM might generate tokens that are totally different from these within the enter, for instance, translating overseas phrases into English
-
As just some entity lessons are labeled in every cut up of the Few-NERD episode knowledge and annotations for all different lessons are eliminated, the mannequin is not going to have full data for coarse-grained lessons by the character of the information. Solely the information for the supervised activity comprises full labels, and a few further processing must be accomplished if we wish to match these. As an illustration, within the instance under solely the character is labeled within the episode knowledge, however the actors usually are not labeled. This may occasionally trigger points for each prompting and analysis. This can be one of many causes for the bigger mannequin’s low precision scores: if the LLM has sufficient prior data to label all of the particular person entities, a few of them could also be recognized as false positives.
Not all entities are labeled within the episode knowledge of Few-NERD, solely the supervised activity comprises full labels - The authors of GPT-NER put appreciable emphasis on deciding on probably the most helpful few-shot examples to incorporate into the immediate given to the LLM. Nevertheless, in a really few-shot situation we don’t have the posh of additional labeled examples to select from. Thus, we barely modified the setup and easily included all help examples of a given check episode within the immediate.
- Lastly, although the information in Few-NERD is human-annotated, the labeling will not be all the time excellent and unambiguous, and a few errors are current. However extra importantly, Few-NERD is a relatively exhausting dataset typically: for a human, it isn’t all the time simple to say what the proper class of some named entities must be!
The labels usually are not all the time clearly appropriate: for instance, right here the character Spider-Man is labeled as a portray, and a racehorse is labeled as an individual
Future work
An vital word is that in Few-NERD, the lessons have two ranges of granularity: for instance, “person-actor”, the place “particular person” is the coarse-grained, and “actor” the fine-grained class. For now, we solely think about the broader coarse-grained lessons, that are simpler for the fashions to detect than the extra particular fine-grained lessons can be.
Within the GPT-NER pre-print, there’s some emphasis positioned on the self-verification approach. After discovering a named entity, the mannequin is then prompted to rethink its determination: given the sentence and the entity that the mannequin present in that sentence, it has to reply whether or not that entity does certainly belong to the category in query. Whereas we’ve replicated the essential GPT-NER setup with Few-NERD and Llama 2, we’ve not but explored the self-verification approach intimately.
We deal with recreating the primary setup of GPT-NER and use the prompts as proven within the pre-print. Nevertheless, we expect that the outcomes could possibly be improved and among the points described above could possibly be fastened with extra subtle immediate engineering. That is additionally one thing we go away for future experiments.
Lastly, there are different thrilling LLMs to experiment with, together with the not too long ago launched Llama 3 fashions out there on the Clarifai platform.
Abstract
We utilized the prompting strategy of GPT-NER to the duty of few-shot NER utilizing the Few-NERD dataset and the Llama 2 fashions hosted by Clarifai. Whereas there are just a few points to be thought of, we’ve discovered that, as can be anticipated, the fashions do higher when there are extra few-shot examples proven within the immediate, however, much less expectedly, the tendencies associated to mannequin sizes are diverse. There’s nonetheless rather a lot to be explored as effectively: higher immediate engineering, extra superior strategies comparable to self-verification, how the fashions carry out when detecting fine-grained as an alternative of coarse-grained lessons, and rather more.
Check out one of many LLMs on the Clarifai platform in the present day. Can’t discover what you want? Seek the advice of our docs web page or ship us a message in our Group Discord channel.