Clients throughout various industries depend on Amazon OpenSearch Service for interactive log analytics, real-time utility monitoring, web site search, vector database, deriving significant insights from knowledge, and visualizing these insights utilizing OpenSearch Dashboards. Moreover, prospects usually hunt down capabilities that allow easy sharing of visible dashboards and seamless embedding of those dashboards inside their purposes, additional enhancing person expertise and streamlining workflows.
On this submit, we present methods to embed a stay Amazon Opensearch dashboard in your utility, permitting your finish prospects to entry a consolidated, real-time view with out ever leaving your web site.
Answer overview
We reveal methods to deploy a pattern flight knowledge dashboard utilizing OpenSearch Dashboards and embed it into your utility by means of an iFrame. The next diagram gives a high-level overview of the end-to-end answer.

The workflow consists of the next steps:
- The person requests for the embedded dashboard by opening the static internet server’s endpoint in a browser.
- The request reaches the NGINX endpoint. The NGINX endpoint routes the site visitors to the self-managed OpenSearch Dashboards server. The OpenSearch Dashboards server acts because the UI layer that connects to the OpenSearch Service area because the server.
- The self-managed OpenSearch Dashboards server interacts with the Amazon managed OpenSearch Service area to fetch the required knowledge.
- The requested knowledge is distributed to the OpenSearch Dashboards server.
- The requested knowledge is distributed from the self-managed OpenSearch Dashboards server to the net server utilizing the NGINX proxy.
- The dashboard renders the visualization with the info and shows it on the web site.
Conditions
You’ll launch a self-managed OpenSearch Dashboards server on an Amazon Elastic Compute Cloud (Amazon EC2) occasion and hyperlink it to the managed OpenSearch Service area to create your visualization. The self-managed OpenSearch Dashboards server acts because the UI layer that connects to the OpenSearch Service area because the server. The submit assumes the presence of a VPC with public in addition to personal subnets.
Create an OpenSearch Service area
If you have already got an OpenSearch Service area arrange, you’ll be able to skip this step.
For directions to create an OpenSearch Service area, confer with Getting began with Amazon OpenSearch Service. The area creation takes round 15–20 minutes. When the area is in Lively standing, observe the area endpoint, which you will want to arrange a proxy in subsequent steps.
Deploy an EC2 occasion to behave because the NGINX proxy to the OpenSearch Service area and OpenSearch Dashboards
On this step, you launch an AWS CloudFormation stack that deploys the next sources:
- A safety group for the EC2 occasion
- An ingress rule for the safety group connected to the OpenSearch Service area that permits the site visitors on port 443 from the proxy occasion
- An EC2 occasion with the NGINX proxy and self-managed OpenSearch Dashboards arrange
Full the next steps to create the stack:
- Select Launch Stack to launch the CloudFormation stack with some preconfigured values in
us-east-1. You possibly can change the AWS Area as required.

- Present the parameters on your OpenSearch Service area.
- Select Create stack.
The method might take 3–4 minutes to finish because it units up an EC2 occasion and the required stack. Wait till the standing of the stack modifications to CREATE_COMPLETE.
- On the Outputs tab of the stack, observe the worth for
DashboardURL.
Entry OpenSearch Dashboards utilizing the NGINX proxy and set it up for embedding
On this step, you create a brand new dashboard in OpenSearch Dashboards, which will probably be used for embedding. Since you launched the OpenSearch Service area throughout the VPC, you don’t have direct entry to it. To ascertain a reference to the area, you utilize the NGINX proxy setup that you simply configured within the earlier steps.
- Navigate to the hyperlink for
DashboardURL (as demonstrated within the earlier step) in your internet browser.
- Enter the person identify and password you configured whereas creating the OpenSearch Service area.

You’ll use a pattern dataset for ease of demonstration, which has some preconfigured visualizations and dashboards.
- Import the pattern dataset by selecting Add knowledge.

- Select the Pattern flight knowledge dataset and select Add knowledge.

- To open the newly imported dashboard and get the iFrame code, select Embed Code on the Share menu.
- Underneath Generate the hyperlink as, choose Snapshot and select Copy iFrame code.

The iFrame code will look much like the next code:
- Copy the code to your most well-liked textual content editor, take away the
/_dashboards half, and alter the body top and width from top="600" width="800" to top="800" width="100%".
- Wrap the iFrame code with HTML code as proven within the following instance and put it aside as an
index.html file in your native system:
Host the HTML code
The following step is to host the index.html file. The index.html file will be served from any native laptop computer or desktop with Firefox or Chrome browser for a fast take a look at.
There are totally different choices accessible to host the net server, corresponding to Amazon EC2 or Amazon S3. For directions to host the net server on Amazon S3, confer with Tutorial: Configuring a static web site on Amazon S3.
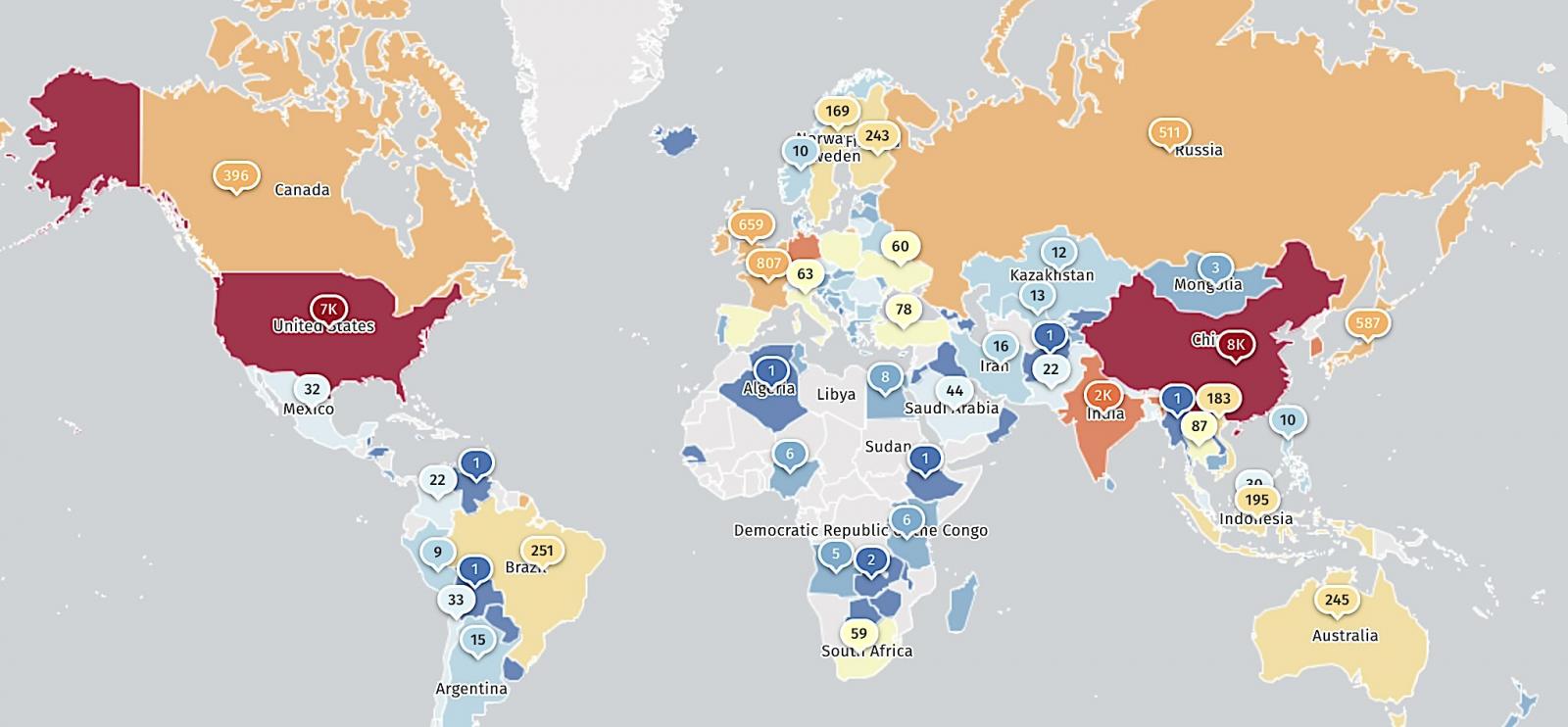
The next screenshot reveals our embedded dashboard.

Clear up
For those who now not want the sources you created, delete the CloudFormation stack and the OpenSearch Service area (should you created a brand new one) to forestall incurring extra costs.
Abstract
On this submit, we confirmed how one can embed your dashboard created with OpenSearch Dashboards into your utility to offer insights to customers. For those who discovered this submit helpful, take a look at Utilizing OpenSearch Dashboards with Amazon OpenSearch Service and OpenSearch Dashboards quickstart information.
Concerning the Authors
 Vibhu Pareek is a Sr. Options Architect at AWS. Since 2016, he has guided prospects in cloud adoption utilizing well-architected, repeatable patterns. Together with his specialization in databases, knowledge analytics, and AI, he thrives on remodeling complicated challenges into revolutionary options. Outdoors work, he enjoys brief treks and sports activities like badminton, soccer, and swimming.
Vibhu Pareek is a Sr. Options Architect at AWS. Since 2016, he has guided prospects in cloud adoption utilizing well-architected, repeatable patterns. Together with his specialization in databases, knowledge analytics, and AI, he thrives on remodeling complicated challenges into revolutionary options. Outdoors work, he enjoys brief treks and sports activities like badminton, soccer, and swimming.
 Kamal Manchanda is a Senior Options Architect at AWS, specializing in constructing and designing knowledge options with concentrate on lake home architectures, knowledge governance, search platforms, log analytics options in addition to generative AI options. In his spare time, Kamal likes to journey and spend time with household.
Kamal Manchanda is a Senior Options Architect at AWS, specializing in constructing and designing knowledge options with concentrate on lake home architectures, knowledge governance, search platforms, log analytics options in addition to generative AI options. In his spare time, Kamal likes to journey and spend time with household.
 Adesh Jaiswal is a Cloud Help Engineer within the Help Engineering workforce at Amazon Net Companies. He focuses on Amazon OpenSearch Service. He gives steering and technical help to prospects thus enabling them to construct scalable, extremely accessible, and safe options within the AWS Cloud. In his free time, he enjoys watching motion pictures, TV collection, and naturally, soccer.
Adesh Jaiswal is a Cloud Help Engineer within the Help Engineering workforce at Amazon Net Companies. He focuses on Amazon OpenSearch Service. He gives steering and technical help to prospects thus enabling them to construct scalable, extremely accessible, and safe options within the AWS Cloud. In his free time, he enjoys watching motion pictures, TV collection, and naturally, soccer.












 Vibhu Pareek is a Sr. Options Architect at AWS. Since 2016, he has guided prospects in cloud adoption utilizing well-architected, repeatable patterns. Together with his specialization in databases, knowledge analytics, and AI, he thrives on remodeling complicated challenges into revolutionary options. Outdoors work, he enjoys brief treks and sports activities like badminton, soccer, and swimming.
Vibhu Pareek is a Sr. Options Architect at AWS. Since 2016, he has guided prospects in cloud adoption utilizing well-architected, repeatable patterns. Together with his specialization in databases, knowledge analytics, and AI, he thrives on remodeling complicated challenges into revolutionary options. Outdoors work, he enjoys brief treks and sports activities like badminton, soccer, and swimming. Kamal Manchanda is a Senior Options Architect at AWS, specializing in constructing and designing knowledge options with concentrate on lake home architectures, knowledge governance, search platforms, log analytics options in addition to generative AI options. In his spare time, Kamal likes to journey and spend time with household.
Kamal Manchanda is a Senior Options Architect at AWS, specializing in constructing and designing knowledge options with concentrate on lake home architectures, knowledge governance, search platforms, log analytics options in addition to generative AI options. In his spare time, Kamal likes to journey and spend time with household. Adesh Jaiswal is a Cloud Help Engineer within the Help Engineering workforce at Amazon Net Companies. He focuses on Amazon OpenSearch Service. He gives steering and technical help to prospects thus enabling them to construct scalable, extremely accessible, and safe options within the AWS Cloud. In his free time, he enjoys watching motion pictures, TV collection, and naturally, soccer.
Adesh Jaiswal is a Cloud Help Engineer within the Help Engineering workforce at Amazon Net Companies. He focuses on Amazon OpenSearch Service. He gives steering and technical help to prospects thus enabling them to construct scalable, extremely accessible, and safe options within the AWS Cloud. In his free time, he enjoys watching motion pictures, TV collection, and naturally, soccer.