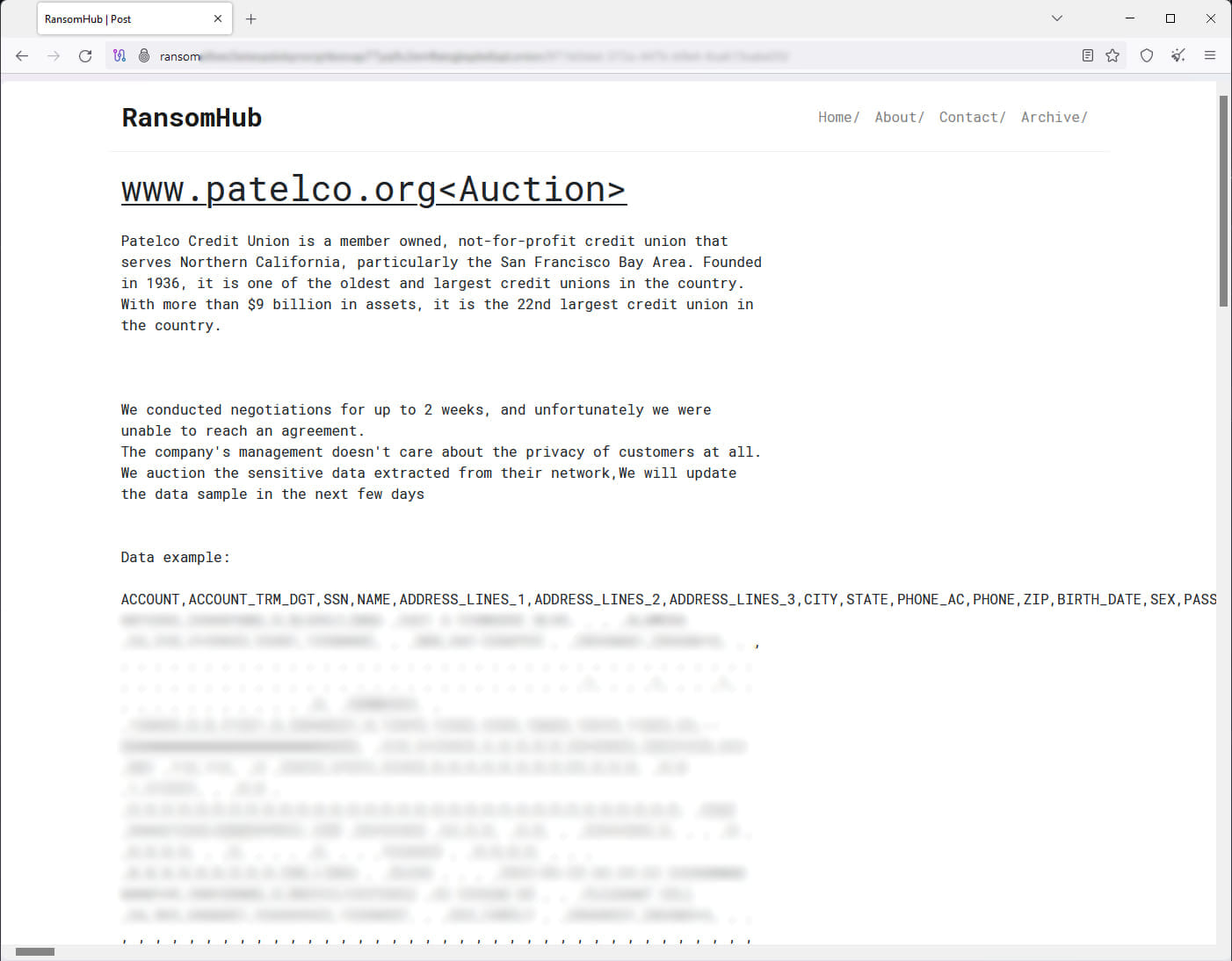
Privateness
Given the unhealthy data-collection habits of some mHealth apps, you’re nicely suggested to tread fastidiously when selecting with whom you share a few of your most delicate knowledge
19 Mar 2024
•
,
5 min. learn

In in the present day’s digital financial system there’s an app for nearly all the pieces. One space that’s booming greater than most is healthcare. From interval and fertility trackers to psychological well being and mindfulness, there are cellular well being (mHealth) purposes obtainable to assist with nearly any situation. In truth, it’s a market already experiencing double-digit development, and set to be price an estimated $861 billion by 2030.
However when utilizing these apps, you can be sharing among the most delicate knowledge you possess. In truth, the GDPR classifies medical data as “particular class” knowledge, that means it may “create vital dangers to the person’s elementary rights and freedoms” if disclosed. That’s why regulators mandate organizations present additional protections for it.
Sadly, not all app builders have the very best pursuits of their customers in thoughts, or at all times know tips on how to defend them. They could skimp on knowledge safety measures, or they might not at all times make it clear as to how a lot of your private data they share with third events. With that in thoughts, let’s check out the principle privateness and safety dangers of utilizing these apps, and how one can keep protected.
What are the highest well being app privateness and safety dangers?
The principle dangers of utilizing mHealth apps fall into three classes: inadequate knowledge safety, extreme knowledge sharing, and poorly worded or intentionally evasive privateness insurance policies.
1. Knowledge safety considerations
These typically stem from builders failing to observe finest apply guidelines on cybersecurity. They may embody:
- Apps which are now not supported or don’t obtain updates: Distributors might not have a vulnerability disclosure/administration program in place, or take little curiosity in updating their merchandise. Regardless of the purpose, if software program doesn’t obtain updates, it means it could be riddled with vulnerabilities which attackers can exploit to steal your knowledge.
- Insecure protocols: Apps that use insecure communications protocols might expose customers to the danger of hackers intercepting their knowledge in transit from the app to the supplier’s back-end or cloud servers, the place it’s processed.
- No multi-factor authentication (MFA): Most respected providers in the present day supply MFA as a approach to bolster safety on the log-in stage. With out it, hackers may get hold of your password by way of phishing or a separate breach (for those who reuse passwords throughout completely different apps) and log in as in the event that they have been you.
- Poor password administration: For instance, apps that permit customers to maintain manufacturing facility default passwords, or set insecure credentials akin to “passw0rd” or “111111.” This leaves the consumer uncovered to credential stuffing and different brute drive makes an attempt to crack their accounts.
- Enterprise safety: App firms may additionally have restricted safety controls and processes in place in their very own knowledge storage setting. This might embody poor consumer consciousness coaching, restricted anti-malware and endpoint/community detection, no knowledge encryption, restricted entry controls, and no vulnerability administration or incident response processes in place. These all improve the possibilities they may undergo a knowledge breach.
2. Extreme knowledge sharing
Customers’ well being data (PHI) might embody extremely delicate particulars about sexually transmitted illnesses, substance addition or different stigmatised situations. These could also be offered or shared to 3rd events, together with advertisers for advertising and focused advertisements. Among the many examples famous by Mozilla are mHealth suppliers that:
- mix data on customers with knowledge purchased from knowledge brokers, social media websites and different suppliers to construct extra full identification profiles,
- don’t permit customers to request deletion of particular knowledge,
- use inferences made about customers once they take sign-up questionnaires which ask revealing questions on sexual orientation, despair, gender identification and extra,
- permit third-party session cookies which establish and observe customers throughout different web sites to serve related advertisements,
- permit session recording, which screens consumer mouse actions, scrolling and typing.
3. Unclear privateness insurance policies
Some mHealth suppliers is probably not upfront about among the above privateness practices, utilizing obscure language or hiding their actions within the small print of T&Cs. This may give customers a false sense of safety/privateness.

What the regulation says
- GDPR: Europe’s flagship knowledge safety regulation is fairly unequivocal about organizations dealing with particular class PHI. Builders must conduct privateness influence assessments, observe the fitting to erasure and knowledge minimization rules, and take “applicable technical measures” to make sure “the mandatory safeguards” are baked-in, to guard private knowledge.
- HIPAA: mHealth apps supplied by business distributors to be used by people aren’t coated by HIPAA, as a result of distributors aren’t a “coated entity” or “enterprise affiliate.” Nevertheless, some are – and require the suitable administrative, bodily and technical safeguards in place, in addition to an annual Threat Evaluation.
- CCPA and CMIA: Californian residents have two items of laws defending their safety and privateness in an mHealth context: the Confidentiality of Medical Data Act (CMIA) and the California Shopper Privateness Act (CCPA). These demand a excessive customary of information safety and express consent. Nevertheless, they solely apply to Californians.
Taking steps to guard your privateness
Everybody can have a unique threat urge for food. Some will discover the commerce off between personalised providers/promoting and privateness one they’re prepared to make. Others might not bothered if some medical knowledge is breached or offered to 3rd events. It’s about discovering the fitting stability. If you’re involved, think about the next:
- Do your analysis earlier than downloading. See what different customers say and if there are any crimson flags from trusted reviewers
- Restrict what you share by way of these apps and assume something you say could also be shared
- Don’t join the app to your social media accounts or use them to register. This may restrict what knowledge may be shared with these firms
- Don’t give the apps permission to entry your system digicam, location, and many others.
- Restrict advert monitoring in your telephone’s privateness settings
- All the time use MFA the place supplied and create sturdy, distinctive passwords
- Preserve the app on the newest (most safe) model
Since Roe vs Wade was overturned, the controversy over mHealth privateness has taken a worrying flip. Some have raised the alarm that knowledge from interval trackers might be utilized in prosecutions in opposition to ladies looking for to terminate their pregnancies. For a rising variety of individuals in search of privacy-respecting mHealth apps, the stakes couldn’t be increased.







_Agnostus_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop&w=768&resize=768,0&ssl=1)