On Android and iOS, accessibility options can be found to assist folks use their smartphones: audio feedback, subtitles, customized show… Some cellular functions designed with an inclusive strategy are appropriate with accessibility providers.
To allow these providers in an software, it requires the accessibility permission. However this permission provides functions full entry to the consumer’s machine. At the moment, an increasing number of cybercriminals are leveraging it to take management of smartphones and tablets. When this occurs, customers discover themselves in a bind, unable to uninstall the app and even reset their machine.
Not too long ago, the Pradeo Safety answer neutralized an software utilizing Android accessibility providers for malicious functions on a protected machine. The recognized malware was put in via a phishing hyperlink. It pretends to be a QR code scanning software however really exploits the accessibility permission to carry out fraudulent banking transactions.
The dangers of cellular accessibility providers
An software can use the android.permission.BIND_ACCESSIBILITY_SERVICE permission so as to profit from superior options facilitating accessibility to customers with disabilities. With this permission, an software can management the entire display (clicks, strikes…) in addition to the keyboard, learn what’s displayed and shut or open functions.
These options are delicate as a result of they allow the management of virtually all layers of a tool. When a malicious software is granted the accessibility permission, it might ship all the data displayed on the display and typed on the keyboard to a distant server, forestall its personal elimination or a system reset, and even launch itself robotically when the machine is rebooted. Sadly, the distribution channels utilized by hackers similar to unofficial software shops and messaging providers (SMS) don’t present any safety towards this risk.
Case research: QR-Code Scanner
Title of the analyzed app: QR-Code Scanner
Package deal identify: com.sq..boss
OS: Android
The “QR-Code Scanner” software seems as a QR code scanning software. Its icon and identify are usually not suspicious. Nonetheless, when launched, no QR code scanning performance is obtainable.
Instantly, the appliance sends a notification that urges to grant the accessibility possibility, which is important for the execution of its assault. So long as the consumer doesn’t permit it, it constantly sends the identical permission request.
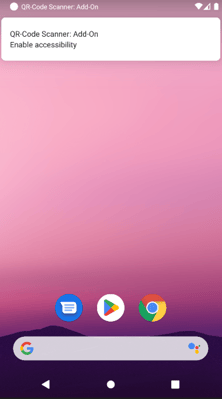
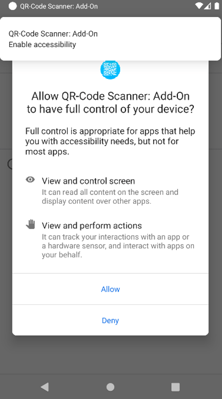
As soon as licensed, the malware can silently approve its personal permission requests rather than the consumer. Thus, it grants itself all of the permissions that may permit it to hold out its assault.
On this case, our evaluation of the malware means that the aim of the hacker behind the appliance is to commit fraud, by accumulating knowledge that the consumer varieties or shows on his display (login, password, bank card numbers …) and intercepting the non permanent authentication code despatched.
First, the QR-Code Scanner software accesses the checklist of functions put in on the sufferer’s machine to gauge curiosity. When banking or e-commerce functions are used, there’s a better probability that banking knowledge is manipulated by the consumer. When it occurs, the hacker collects them.
To enter the sufferer’s account or make a cost along with his bank card, the hacker intercepts the one-time password contained in an SMS or a notification. Therefore, he bypasses all safety measures that authenticate funds and connections utilizing a code. Solely verification protocols that use biometric knowledge are protected at this level.
Lastly, the appliance makes use of the sufferer’s cellphone to unfold to different gadgets. To do that, it sends an SMS containing a phishing hyperlink to the whole contact checklist. This fashion, the message comes from a identified quantity and has a greater probability of convincing the recipients to put in the malware.
All through the assault, the malware exploits accessibility providers to:
- Spy on customers exercise
- Grant and stop the rejection of the permissions it wants
- Forestall elimination of the appliance, both from the homepage or from the settings
- Forestall manufacturing unit reset, even from a third-party machine
- Forestall sleep or shutdown of its course of
- Launch at startup
The permissions utilized by the malware are the next:
android.permission.QUERY_ALL_PACKAGES
android.permission.QUICKBOOT_POWERON
android.permission.RECEIVE_LAUNCH_BROADCASTS
android.permission.GET_TASKS
android.permission.SYSTEM_ALERT_WINDOW
android.permission.RECEIVE_SMS
android.permission.READ_SMS
android.permission.WRITE_SMS
android.permission.SEND_SMS
android.permission.REQUEST_IGNORE_BATTERY_OPTIMIZATIONS
android.intent.motion.BOOT_COMPLETED
com.htc.intent.motion.QUICKBOOT_POWERON
android.intent.motion.QUICKBOOT_POWERON
android.permission.RECEIVE_BOOT_COMPLETED
android.permission.QUICKBOOT_POWERON
Protecting measures
Regardless of the plain want for accessibility providers, the superior rights they provide on the system imply that they have to be used (on the developer facet) and licensed (on the consumer facet) with due consideration.
At the moment, only some instruments and remediation actions are efficient to neutralize the analyzed malware:
- Blocking the appliance earlier than launching it with Pradeo Safety
- Forcing the uninstallation of the appliance with Pradeo Safety for Samsung
- Uninstalling by way of a tool administration answer (UEM, MDM)
- Uninstalling by way of ADB command
