Net software safety refers back to the measures taken to safeguard internet purposes from potential assaults.
It includes methods and processes to safe internet purposes from exterior threats that would compromise their performance, security, and knowledge integrity.
An efficient internet software safety technique includes figuring out doable vulnerabilities, assessing their related dangers, and implementing measures to stop assaults.
Many companies rely closely on internet purposes for his or her operations. A safety breach might result in important monetary loss, harm to the corporate’s repute, and potential authorized repercussions. Subsequently, organizations should be certain that their internet purposes are safe.
Desk of Contents
FAQ
Widespread Vulnerabilities in Net Purposes
SQL Injection
Cross-Website Scripting (XSS)
Cross-Website Request Forgery (CSRF)
Insecure Direct Object References (IDOR)
Safety Misconfigurations
The Position of Safety Frameworks and Requirements
OWASP (Open Net Utility Safety Venture)
ISO/IEC 27001
PCI DSS (Fee Card Trade Information Safety Commonplace)
NIST Cybersecurity Framework
CIS Crucial Safety Controls (CIS CSC)
Greatest Practices for Net Utility Safety
FAQ
1.What’s the Net software safety?
Net software safety protects web-based apps and companies from vulnerabilities. Safety is essential in in the present day’s digital world, as companies and shoppers use internet apps for a lot of functions. Net purposes may be attacked by SQL injection, XSS, CSRF, and extra.
Net software safety requires procedures and expertise to find, mitigate, and stop vulnerabilities and assaults. Net software firewalls, software program updates and patches, enter validation, entry controls, and vulnerability monitoring and testing could also be used.
Organizations can defend delicate knowledge, keep consumer belief, and scale back monetary and reputational danger from safety breaches by prioritizing internet software safety.
2. What’s knowledge safety in internet software?
When delicate info is saved, processed, or despatched inside an internet software or between this system and its customers, knowledge safety in internet purposes refers back to the deployment of strategies and insurance policies to stop the data from being accessed, disclosed, altered, or destroyed by unauthorized events.
Consumer credentials, private knowledge, monetary info, and every other knowledge that have to be saved confidential are examples of the sorts of delicate info that could be required to be saved confidential.
3. Why do we want internet software safety?
Immediately’s digital panorama requires internet software safety to safe delicate knowledge, consumer privateness, and web-based service integrity and availability.
Cyberattacks and knowledge breaches have escalated as extra organizations and shoppers use internet apps. Net purposes have to be secured towards XSS, SQL injection, CSRF, and different threats.
With out robust internet software safety, hostile actors can steal knowledge, hijack consumer accounts, disrupt companies, or achieve unauthorized entry to programs.
Thus, internet software safety insurance policies have to be applied and up to date to guarantee on-line platforms’ trustworthiness and safeguard enterprises and their customers from rising cyber threats.
4. How an internet software is developed?
A functioning and interactive internet software is developed utilizing a scientific technique that blends applied sciences and programming languages.
The tactic normally includes quite a few steps. The planning and conceptualization section defines the venture’s targets, necessities, and viewers.
The design course of then creates the applying’s visible and interactive options, together with the consumer interface (UI) and consumer expertise (UX).
After designing the app, builders code its frontend and backend utilizing HTML, CSS, JavaScript, Python, Ruby, or Node.js. Testing is important for locating and fixing bugs, safety vulnerabilities, and efficiency considerations.
Consumer entry is granted after this system is delivered to an internet server or cloud platform after testing. Updates and upkeep are wanted to fulfill consumer wants, safety threats, and program enhancements.
This technique requires collaboration between designers, builders, testers, and venture managers to ensure a profitable internet software improvement venture.
Widespread Vulnerabilities in Net Purposes
Regardless of the perfect efforts of builders and safety consultants, no internet software is fully resistant to safety dangers.
A number of frequent vulnerabilities typically exploited by attackers embrace SQL Injection, Cross-Website Scripting (XSS), Cross-Website Request Forgery (CSRF), Insecure Direct Object References (IDOR), and Safety Misconfigurations.
SQL Injection
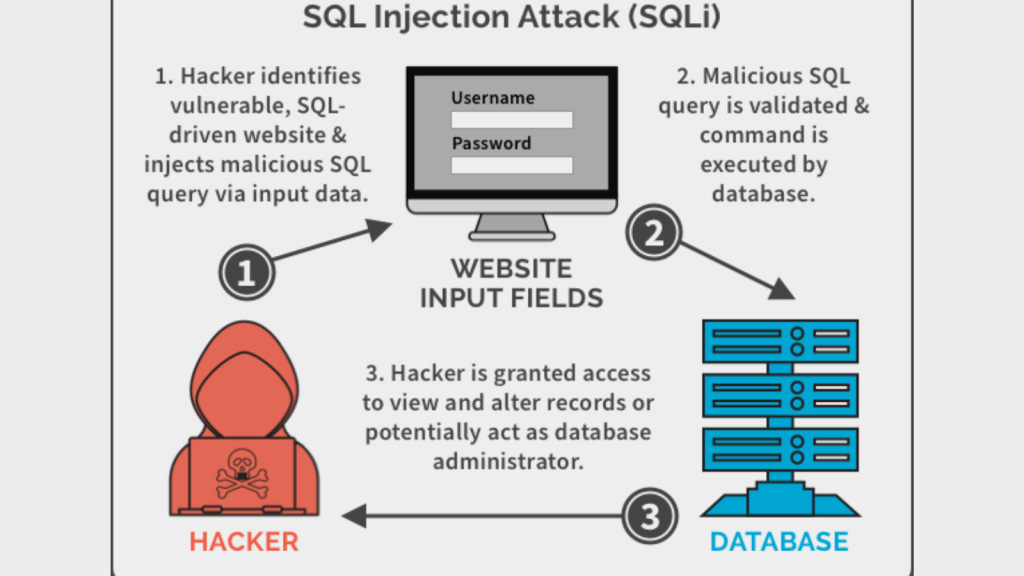

SQL Injection is an internet safety vulnerability that permits an attacker to intrude with an software’s database queries. It usually happens when a developer makes use of unvalidated or unencoded consumer enter inside a database question.
An attacker can manipulate the SQL question to view delicate info, modify the database, and even execute administrative operations on the database.
Cross-Website Scripting (XSS)
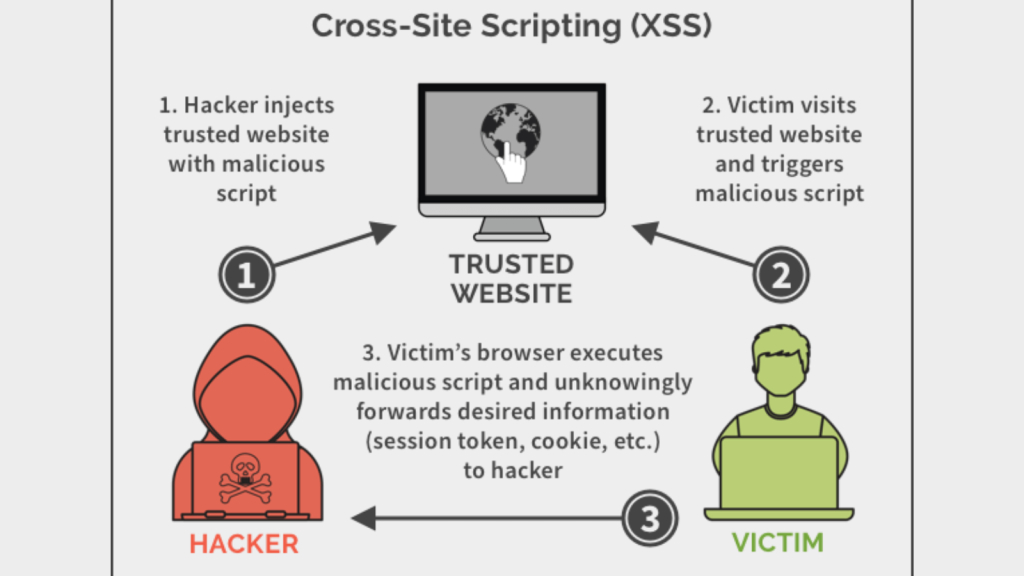

Cross-site scripting (XSS) happens when an attacker injects malicious scripts into internet pages seen by different customers.
The attacker makes use of these scripts to steal delicate info like session cookies, enabling them to impersonate the sufferer and carry out actions on their behalf.
The results of a profitable XSS assault vary from minor annoyance to important safety breaches.
Cross-Website Request Forgery (CSRF)


Cross-Website Request Forgery (CSRF) is an assault that methods the sufferer into submitting a malicious request. That is achieved by together with a hyperlink or script in a webpage that accesses a web site to which the consumer is authenticated.
A profitable CSRF assault can result in unauthorized modifications in knowledge, comparable to e mail addresses, passwords, and extra.
Insecure Direct Object References (IDOR)
Insecure Direct Object References (IDOR) happen when a developer exposes a reference to an inner implementation object, comparable to a file, listing, or database key.
Attorneys can manipulate these references to entry unauthorized knowledge with out an entry management test or different safety.
Safety Misconfigurations
Safety Misconfigurations are probably the most generally seen subject. This sometimes occurs when an software or its platform is configured insecurely.
An attacker can exploit these misconfigurations to entry unauthorized info or performance.
The Position of Safety Frameworks and Requirements
Safety frameworks and requirements are elementary in making certain internet software safety.
By offering a scientific method to managing safety dangers, these tips function roadmaps for organizations aiming to fortify their cybersecurity posture.
Adherence to those frameworks and requirements permits organizations to deal with numerous safety points and guarantee their internet purposes’ confidentiality, integrity, and availability.
OWASP (Open Net Utility Safety Venture)


OWASP is an open group that permits organizations to develop, buy, and keep purposes and APIs that may stand up to safety threats.
One among their most original sources is the OWASP High 10, an ordinary consciousness doc for builders and internet software safety.
It represents a broad consensus about internet purposes’ most crucial safety dangers. Utilizing the OWASP High 10 information, builders can prioritize safety measures, concentrate on probably the most important threats, and considerably enhance their internet software’s safety.
ISO/IEC 27001
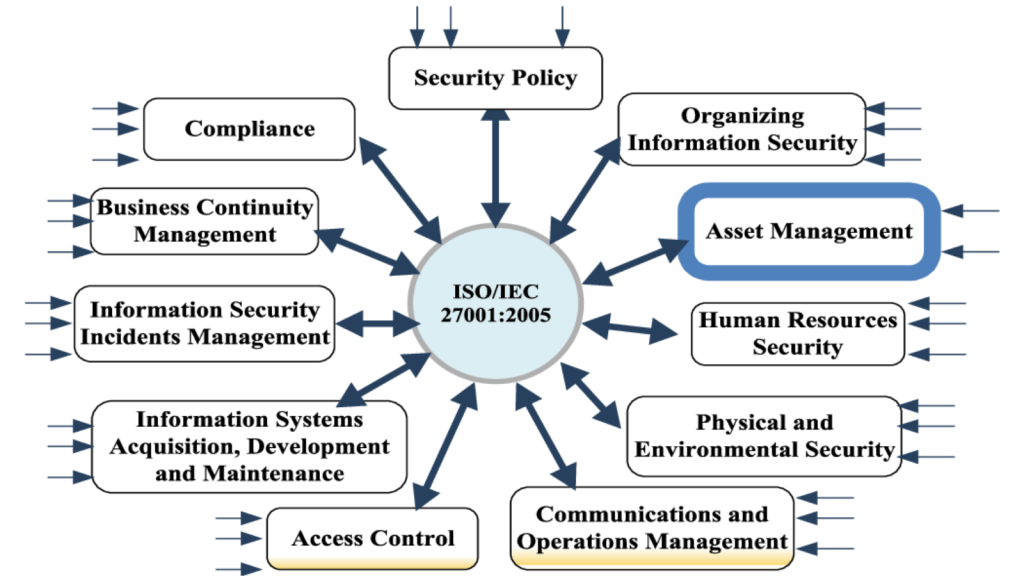

It is a globally acknowledged normal for establishing, implementing, sustaining, and constantly enhancing an Info Safety Administration System (ISMS).
This normal helps organizations constantly and cost-effectively handle their safety practices in a single place.
It covers numerous safety controls, from danger evaluation to entry management to incident administration.
Compliance with ISO/IEC 27001 demonstrates that a company is dedicated to following the perfect info safety practices.
PCI DSS (Fee Card Trade Information Safety Commonplace)
In case your internet software includes processing, storing, or transmitting cardholder knowledge, adhering to the PCI DSS is necessary.
This normal goals to safe bank card transactions towards knowledge theft and fraud.
It includes 12 necessities, together with common safety audits, safe networks and programs, entry management measures, and extra.
Organizations can defend delicate cardholder knowledge and construct prospects’ belief by complying with PCI DSS.
NIST Cybersecurity Framework
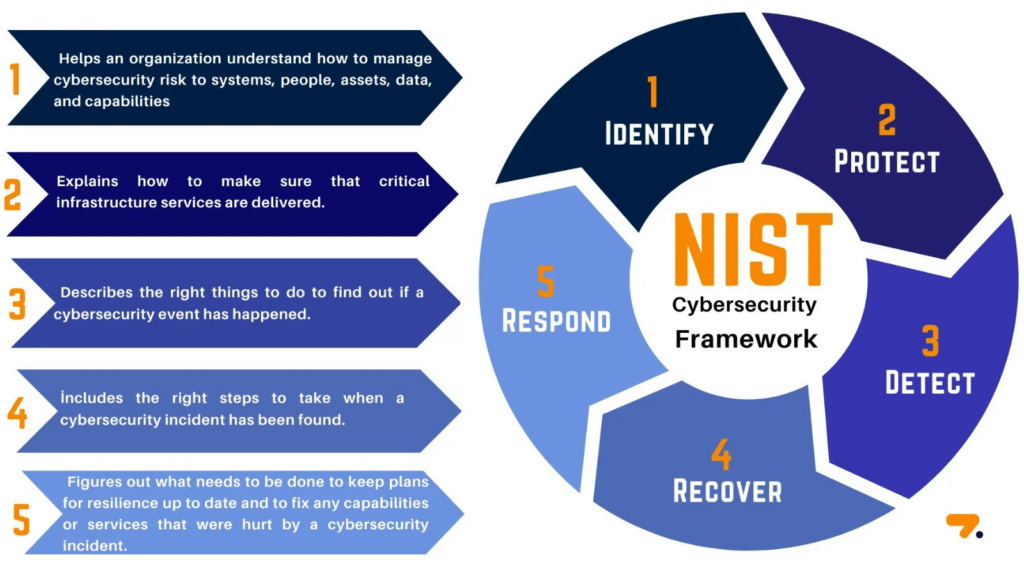

Developed by the Nationwide Institute of Requirements and Expertise (NIST), this voluntary framework supplies a coverage for managing cybersecurity dangers.
It includes requirements, tips, and finest practices to handle cybersecurity danger cost-effectively.
The framework core consists of 5 predominant capabilities: Identification, Shield, Detect, Reply, and Get well.
The NIST framework is extensively adopted throughout numerous industries as a consequence of its flexibility and comprehensiveness.
CIS Crucial Safety Controls (CIS CSC)
Developed by the Middle for Web Safety, CIS CSC is a set of 20 actions designed to offer a roadmap for organizations to boost their cybersecurity posture.
These controls are a collection of well-vetted and supported safety actions that, when applied, can forestall probably the most pervasive and harmful cyber assaults.
Greatest Practices for Net Utility Safety
The next finest practices will help you safe internet purposes and scale back enterprise dangers.
Safe Coding Practices
Safe coding is the observe of writing code for programs, purposes, and software program in a means that guards towards safety vulnerabilities.
It includes a collection of rules designed to get rid of classes of bugs that would result in system vulnerabilities.
Safe coding helps defend a system from potential threats by figuring out and eliminating software program bugs or flaws that cybercriminals might exploit.
Protected coding practices have turn out to be extra essential within the present expertise panorama. Safety is commonly compromised as builders are pressured to ship quick and environment friendly software program.
Nonetheless, builders should perceive that safe coding practices can enhance their code’s safety, high quality, and maintainability.
It could considerably scale back the time and value related to fixing bugs and vulnerabilities within the later phases of the software program improvement life cycle.
Consumer Enter Validation and Sanitization
Consumer enter validation and sanitization are vital points of internet software safety. They test and clear consumer enter to stop safety vulnerabilities comparable to SQL injection, cross-site scripting, and distant code execution.
Enhanced consumer enter validation and sanitization strategies embrace utilizing allow-lists as an alternative of deny-lists, safe APIs, and context-sensitive output encoding.
These strategies will help forestall frequent internet software safety vulnerabilities and defend the applying from potential assaults.
Automated Safety Testing
Automation performs an important position in safety testing by automating repetitive duties, lowering human error, and dashing up the testing course of.
Automated safety testing instruments can scan for identified vulnerabilities, execute check instances, and generate experiences, releasing up safety groups to concentrate on extra complicated duties.
Automation may assist companies sustain with the speedy tempo of software program improvement and deployment.
As new code is dedicated, automated instruments can shortly check for vulnerabilities, making certain safety is built-in all through the software program improvement lifecycle.
That is significantly necessary in an Agile or DevOps surroundings, the place velocity and effectivity are vital.
Patching and Updating Software program
In a DevOps surroundings, steady integration and deployment are the norms.
This implies code is steadily up to date and deployed, which may create potential safety vulnerabilities.
Subsequently, common patching and updating are essential to sustaining the applying’s safety.
Patching includes updating the software program to repair safety vulnerabilities. Common patch administration ensures that the applying is protected towards identified threats.
It’s additionally important to maintain all software program parts, together with third-party libraries and frameworks, up-to-date.
Information Encryption and Safe Information Transmission
Information encryption is the method of changing knowledge right into a format that’s unreadable to unauthorized customers. It’s important to internet software safety because it protects delicate knowledge from cybercriminals’ entry.
Safe knowledge transmission with HTTPS can also be vital for internet software safety. HTTPS, or Hypertext Switch Protocol Safe, is an web communication protocol that protects the integrity and confidentiality of information between the consumer’s pc and the location.
It ensures that knowledge transmitted between the consumer and the online software is encrypted and safe.
Conclusion
In conclusion, understanding and implementing internet software safety finest practices is crucial for companies in in the present day’s digital age.
Safe coding practices, automation in safety testing, AI in WAFs, common patching and updating, enhanced enter validation and sanitization, knowledge encryption, and safe transmission with HTTPS are all vital points of internet software safety that companies should prioritize.
Keep in mind, the safety of your internet software is not only about defending your online business; it’s additionally about safeguarding your prospects’ belief and loyalty.
