
The Web Archive was breached once more, this time on their Zendesk e-mail assist platform after repeated warnings that menace actors stole uncovered GitLab authentication tokens.
Since final night time, BleepingComputer has acquired quite a few messages from individuals who acquired replies to their outdated Web Archive removing requests, warning that the group has been breached as they didn’t appropriately rotate their stolen authentication tokens.
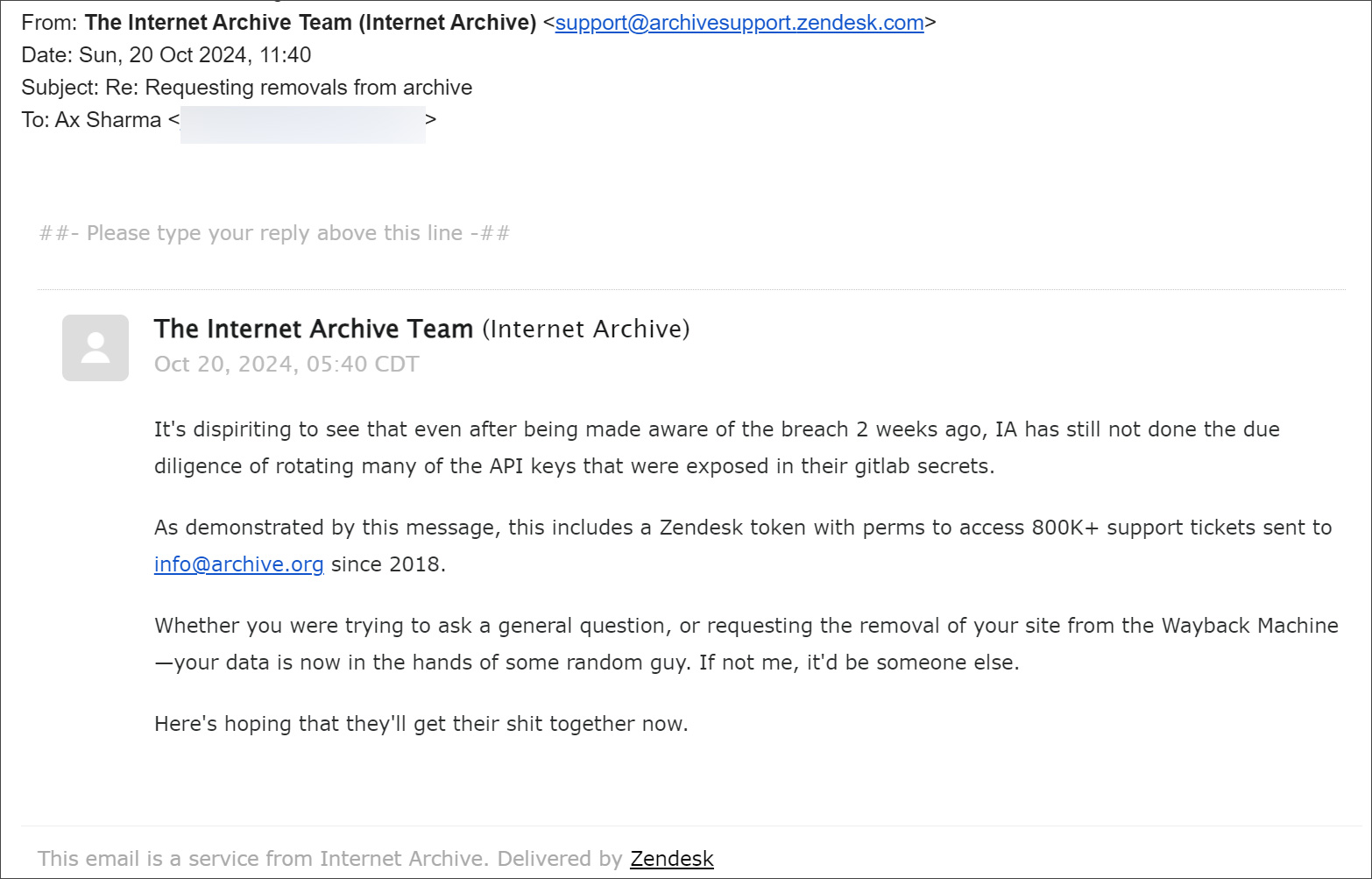
“It is dispiriting to see that even after being made conscious of the breach weeks in the past, IA has nonetheless not finished the due diligence of rotating most of the API keys that have been uncovered of their gitlab secrets and techniques,” reads an e-mail from the menace actor.
“As demonstrated by this message, this features a Zendesk token with perms to entry 800K+ assist tickets despatched to data@archive.org since 2018.”
“Whether or not you have been attempting to ask a common query, or requesting the removing of your web site from the Wayback Machine your knowledge is now within the arms of some random man. If not me, it would be another person.”
Supply: BleepingComputer
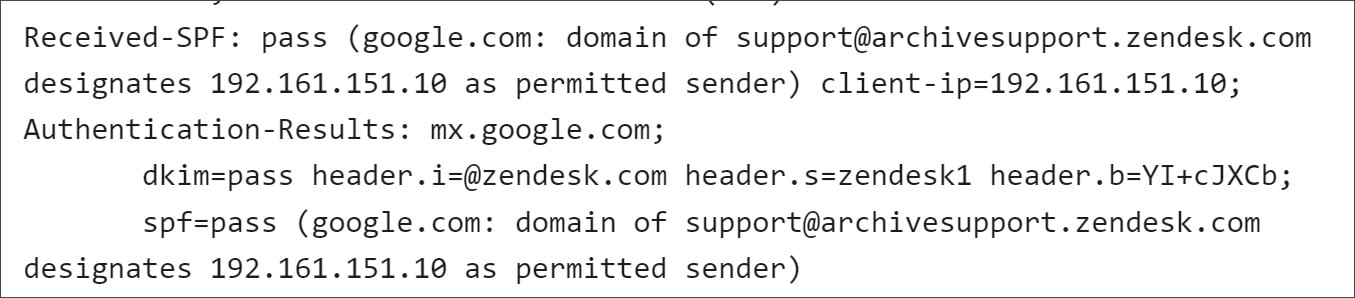
The e-mail headers in these emails additionally cross all DKIM, DMARC, and SPF authentication checks, proving they have been despatched by a licensed Zendesk server at 192.161.151.10.
Supply: BleepingComputer
After publishing this story, BleepingComputer was instructed by a recipient of those emails that they needed to add private identification when requesting a removing of a web page from the Wayback Machine.
The menace actor might now even have entry to those attachments relying on the API entry they needed to Zendesk and in the event that they used it to obtain assist tickets.
These emails come after BleepingComputer repeatedly tried to warn the Web Archive that their supply code was stolen by a GitLab authentication token that was uncovered on-line for nearly two years.
Uncovered GitLab authentication tokens
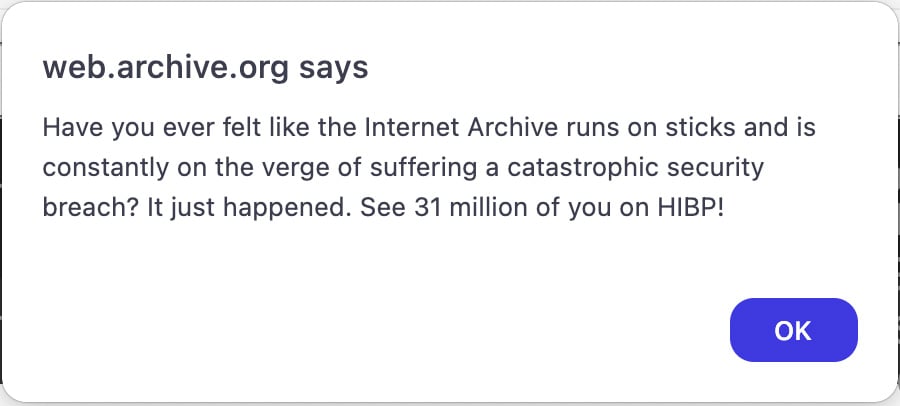
On October ninth, BleepingComputer reported that Web Archive was hit by two completely different assaults without delay final week—an information breach the place the location’s person knowledge for 33 million customers was stolen and a DDoS assault by a pro-Palestinian group named SN_BlackMeta.
Whereas each assaults occurred over the identical interval, they have been performed by completely different menace actors. Nonetheless, many shops incorrectly reported that SN_BlackMeta was behind the breach relatively than simply the DDoS assaults.
Supply: BleepingComputer
This misreporting pissed off the menace actor behind the precise knowledge breach, who contacted BleepingComputer by an middleman to assert credit score for the assault and clarify how they breached the Web Archive.
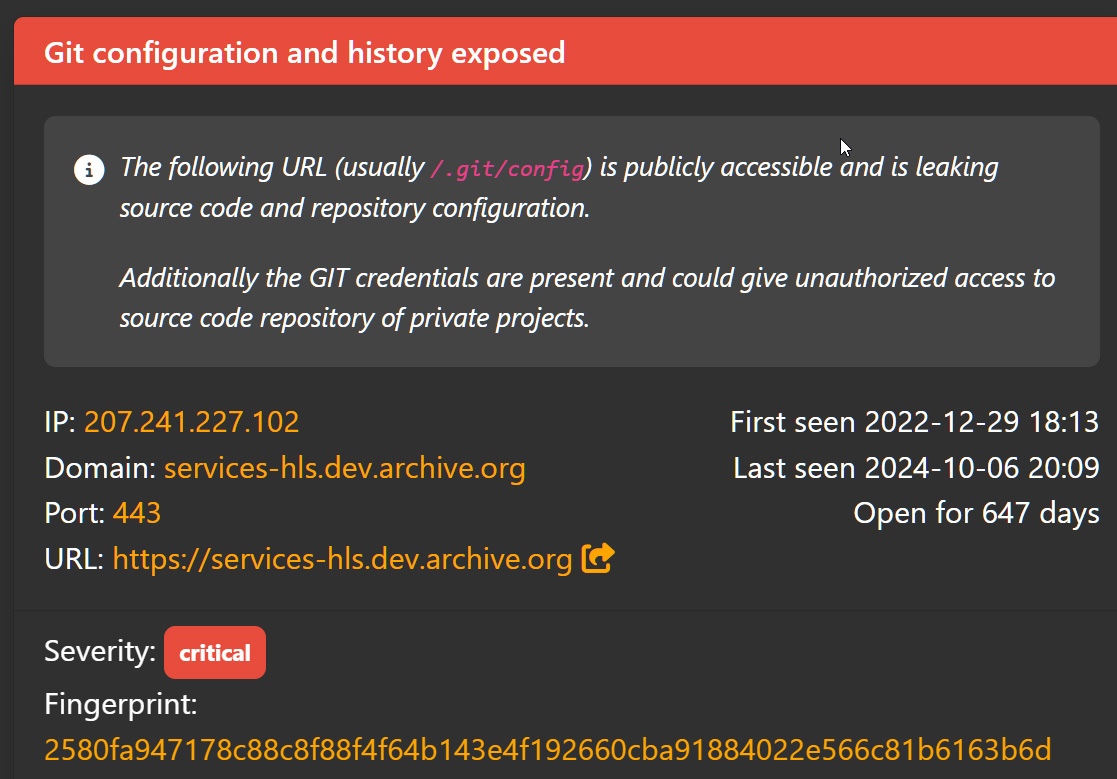
The menace actor instructed BleepingComputer that the preliminary breach of Web Archive began with them discovering an uncovered GitLab configuration file on one of many group’s growth servers, services-hls.dev.archive.org.
BleepingComputer was in a position to affirm that this token has been uncovered since not less than December 2022, with it rotating a number of occasions since then.
Supply: BleepingComputer
The menace actor says this GitLab configuration file contained an authentication token permitting them to obtain the Web Archive supply code.
The hacker say that this supply code contained extra credentials and authentication tokens, together with the credentials to Web Archive’s database administration system. This allowed the menace actor to obtain the group’s person database, additional supply code, and modify the location.
The menace actor claimed to have stolen 7TB of information from the Web Archive however wouldn’t share any samples as proof.
Nonetheless, now we all know that the stolen knowledge additionally included the API entry tokens for Web Archive’s Zendesk assist system.
BleepingComputer tried contact the Web Archive quite a few occasions, as just lately as on Friday, providing to share what we knew about how the breach occurred and why it was finished, however we by no means acquired a response.
Breached for cyber avenue cred
After the Web Archive was breached, conspiracy theories abounded about why they have been attacked.
Some mentioned Israel did it, the USA authorities, or companies of their ongoing battle with the Web Archive over copyright infringement.
Nonetheless, the Web Archive was not breached for political or financial causes however just because the menace actor may.
There’s a giant neighborhood of people that visitors in stolen knowledge, whether or not they do it for cash by extorting the sufferer, promoting it to different menace actors, or just because they’re collectors of information breaches.
This knowledge is commonly launched totally free to achieve cyber avenue cred, growing their popularity amongst different menace actors on this neighborhood as all of them compete for who has probably the most important and most publicized assaults.
Within the case of the Web Archive, there was no cash to be made by attempting to extort the group. Nonetheless, as a well known and intensely fashionable web site, it positively boosted an individual’s popularity amongst this neighborhood.
Whereas nobody has publicly claimed this breach, BleepingComputer was instructed it was finished whereas the menace actor was in a bunch chat with others, with many receiving a number of the stolen knowledge.
This database is now seemingly being traded amongst different individuals within the knowledge breach neighborhood, and we’ll seemingly see it leaked totally free sooner or later on hacking boards like Breached.
Replace 10/20/24: Added details about how some individuals needed to add private IDs when requesting removing from Web Archive.
