A number of essential safety vulnerabilities in computerized tank gauge (ATG) methods, some unpatched, threaten essential infrastructure amenities with disruption and bodily harm, researchers are warning.
ATGs are sensor methods that monitor and handle gas storage tanks to make sure that fill ranges aren’t too low or too excessive, to see that leaks are detected in real-time, and to handle stock. ATGs might be discovered the place you’d anticipate them to be, like at gasoline stations and airports, but in addition in much less apparent installations.
“Within the US, for instance, we have been informed that you’re required by legislation to have an ATG system put in in any gas tank of a sure dimension,” Pedro Umbelino, principal analysis scientist at Bitsight’s TRACE unit, explains to Darkish Studying. “Fuel stations are the most important and most evident use case, however the second largest use case for ATGs are essential amenities that require massive backup turbines — you typically see these in amenities like hospitals, army installations and airports.”
Worryingly, many of the newly found vulnerabilities permit for an attacker to have full management of an ATG as an administrator. And based on Umbelino, the 11 bugs throughout six ATG methods from 5 completely different distributors can thus open the door to a gamut of nefarious actions, starting from making fueling unavailable to wreaking environmental havoc.
“What’s much more regarding is that, in addition to a number of warnings previously, 1000’s of ATGs are nonetheless at present on-line and instantly accessible over the Web, making them prime targets for cyberattacks, particularly in sabotage or cyberwarfare situations,” Umbelino stated in an evaluation launched on Sept. 24.
The bugs have been found six months in the past, with Bitsight, the US Cybersecurity and Infrastructure Safety Company (CISA), and the affected distributors working in tandem to mitigate the issues. Because of these efforts, “Maglink and Franklin have launched patches,” Umbelino says. “The affected OPW product has been EOL’d [end of life] and is now not being supported by the seller, so they won’t be releasing a patch. Proteus and Alisonic haven’t engaged with us or with CISA as a part of the disclosure course of, so it is unclear to us in the event that they’ve launched or are engaged on a mitigation plan.”
Patching is not the place the remediation wants cease, although.
“Even for gadgets which have had patches issued, my high suggestion is to disconnect these gadgets from the general public Web,” Umbelino says. “Most of them have been by no means designed to be related in the best way they’re at the moment, in order that they weren’t constructed with the extent of safety that’s required for Web-connected gadgets. They’re being utilized in ways in which distributors hadn’t initially supposed, and that is what is on the core of those vulnerabilities. Taking them off the general public Web is the one true answer.”
Main Cyber-Threat From ATG Tampering
ATGs not solely mechanically measure and file the extent, quantity, and temperature of merchandise in storage tanks, however they’re often related to sirens, emergency shutoff valves, air flow methods, and peripherals like gas dispensers.
“A part of what makes these gadgets engaging to safety researchers, or a malicious actor for that matter, is the potential potential to manage bodily processes that might result in disastrous penalties if they’re abused in unintended methods,” Umbelino famous.
As Umbelino defined, “We discovered vanilla mirrored cross-site scripting (XSS). The authentication bypasses have been direct path entry. The command injections lacked filtering. There have been hardcoded administrator credentials. The arbitrary file learn was a direct path traversal entry, yielding admin credentials. The SQL injection could possibly be exploited aided by full SQL error logs.”
The vulnerabilities are as follows:
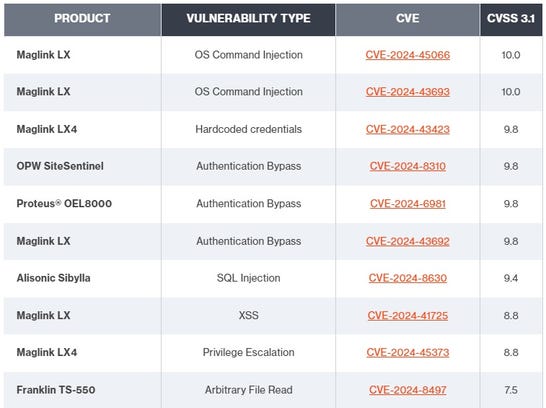
Supply: Bitsight TRACE.
For instance of these penalties, attackers might exploit the bugs to alter the quantity of liquid a tank is able to taking over, whereas additionally tampering with overflow alarms. The consequence could possibly be an undetected tank overflow, which might trigger gasoline spills and environmental chaos.
And as Umbelino defined within the put up, “Probably the most damaging assault is making the gadgets run in a approach which may trigger bodily harm to their elements or elements related to it. In our analysis, we have proven that an attacker can achieve entry to a tool and drive the relays at very quick speeds, inflicting everlasting harm to them.”
Different unhealthy outcomes embrace making the methods inaccessible by way of denial of service (DoS), exposing aggressive operations knowledge (supply dates, pricing, stock intel, sorts of alarms, and so forth.), or the lack of compliance knowledge resulting in potential regulatory fines. In a DoS situation as an example, an assault might “result in downtime and would often require human intervention,” Umbelino defined within the posting. “In actual fact, these kinds of assaults are at present ongoing, with claims of exploitation of at the least one model of gadgets for which we printed a vulnerability on simply two weeks in the past.”
Vital Infrastructure Beneath Growing Cyber Menace
The essential infrastructure risk panorama continues to be a thorny downside for safety practitioners, beginning with the truth that ICS methods and the operational expertise (OT) that controls them are designed to prioritize reliability and effectivity, not safety.
“Consequently, they typically lack fashionable protections,” Umbelino famous. “As well as … distributors just lately began to combine them with newer expertise to enhance effectivity and distant entry and this considerably modifications their risk mannequin. In fact, there may be additionally a scarcity of cybersecurity consultants which are acquainted with ICS methods. It’s laborious to search out vulnerabilities if nobody is in search of them.”
Menace actors have taken discover: Chinese language APTs like Volt Storm and others need to achieve a foothold inside bodily infrastructure, for operational espionage in addition to cultivating the potential for disruptive assaults. Ransomware gangs have their very own causes for concentrating on ICS, as seen within the notorious Colonial Pipeline cyberattack.
“Whereas not associated to the vulnerabilities we discovered, there’s a group persistently claiming ICT/OT disruption within the Ukraine-Russia conflict, together with ATG methods,” Umbelino says. “In this tweet, we will see an OPW ATG system being focused, however they declare to have affected many different ICT/OT gadgets too, indicating that attackers do see these components inside essential infrastructure as a goal.”
CISA itself has flagged elevated threats to water provide organizations, energy crops, manufacturing, telecom carriers, army footprints, and extra — assaults which are largely being spearheaded by APTs backed by China, Russia, and Iran.
Up to now, defenders have headed off catastrophic assaults on the cross, and there is no cause to anticipate mass gasoline spills anytime quickly, given the complexity and class required to use the bugs, nevertheless it’s vital to remain forward of the danger.
“It’s not nearly fixing vulnerabilities, it’s about adopting safety practices that make them troublesome to exist within the first place,” Umbelino defined within the evaluation. “And it’s not simply in regards to the vulnerabilities themselves, it is about their publicity. Organizations want to know they mustn’t expose these kinds of essential methods to the general public Web. They should successfully assess their publicity, perceive their present danger and begin addressing such points, no matter distributors potential to replace their methods in a well timed trend.”
Safety researchers even have an vital position to play, he provides, noting that stakeholders needs to be increasing their ICS focus.
“We must always begin paying extra shut consideration to these kinds of methods that management crucial elements of our society and that, if abused, can have a bodily impact on the world, typically catastrophic,” Umbelino says. “We have to systematically uncover, classify and mitigate the danger of them being overtly uncovered to the Web quicker than the attackers, and be capable of talk that danger to all affected events. It isn’t a simple job.”
