A 20-year-old U.S. Military soldier, Cameron John Wagenius, has been arrested and indicted by federal authorities for allegedly promoting confidential buyer name information stolen from main telecommunications firms AT&T and Verizon.
Recognized on-line as “Kiberphant0m,” Wagenius was apprehended close to an Military base in Fort Hood, Texas, on December 20. He faces two felony counts of unlawfully transferring delicate cellphone information.


Cybercrime Allegations and Surprising Ties
Wagenius, who served as a communications specialist within the U.S. Military and was just lately stationed in South Korea, is accused of utilizing his technical experience to orchestrate a collection of cybercrimes.
The indictment hyperlinks him to the sale and leakage of delicate information from no less than 15 telecommunications firms. These information allegedly included name logs belonging to high-profile people, resembling authorities officers.
In accordance with Grebs On Safety, the investigation gained traction in November 2024 after cybersecurity journalist Brian Krebs recognized Wagenius as a possible suspect.
The path of proof, present in Telegram messages and hacker boards like BreachForums, pointed to his involvement in numerous felony actions, together with SIM-swapping companies and distributed denial-of-service (DDoS) assaults.
Wagenius reportedly collaborated with Canadian cybercriminal Connor Riley Moucka, also referred to as “Judische,” who was arrested in October for extorting firms and stealing information from cloud service supplier Snowflake.
Moucka had entrusted Kiberphant0m to promote stolen info, together with information from AT&T and Verizon clients, in addition to providing entry to U.S. protection contractor methods.
After Moucka’s arrest, Kiberphant0m escalated his actions, posting AT&T name logs allegedly belonging to President-elect Donald Trump and Vice President Kamala Harris, additional threatening to leak further authorities name information.
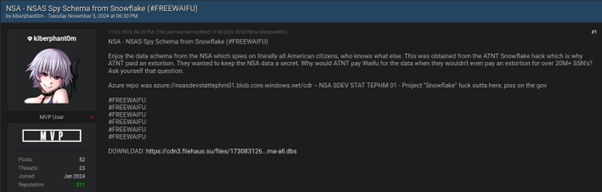

On November 5, he provided Verizon push-to-talk (PTT) name logs — a service often utilized by U.S. authorities businesses and emergency responders.
In his ultimate on-line actions, Kiberphant0m claimed to have stolen information from the Nationwide Safety Company (NSA) and marketed compromised credentials of a U.S. protection contractor.
Wagenius’ digital footprint, together with Fb photographs exhibiting him in uniform, additional linked his real-world identification to his on-line persona.
Cybersecurity analyst Allison Nixon, from Unit 221B, performed a key function in uncovering Wagenius’ identification.
She highlighted the unprecedented pace of legislation enforcement response, stating it was the quickest decision to a U.S. federal cyber case in her expertise.
Nixon additionally warned different younger cyber criminals of the extreme penalties of partaking in unlawful actions.“This could function a wake-up name,” Nixon mentioned. “Regulation enforcement is getting higher and quicker at unmasking cybercriminals. It’s not well worth the threat.”
The case has been transferred to the U.S. District Court docket for the Western District of Washington in Seattle, the place Wagenius will face trial.
If convicted, this case will underscore the rising sophistication of legislation enforcement in tackling cybercrime and the dangers posed by insiders with entry to delicate methods.
Examine Actual-World Malicious Hyperlinks, Malware & Phishing Assaults With ANY.RUN – Attempt for Free


