
The Underground ransomware gang has claimed duty for an October 5 assault on Japanese tech large Casio, which brought on system disruptions and impacted a few of the agency’s companies.
Earlier this week, Casio disclosed the assault on its web site however withheld particulars concerning the incident, saying it had engaged exterior IT specialists to analyze whether or not private information or different confidential info was stolen within the assault.
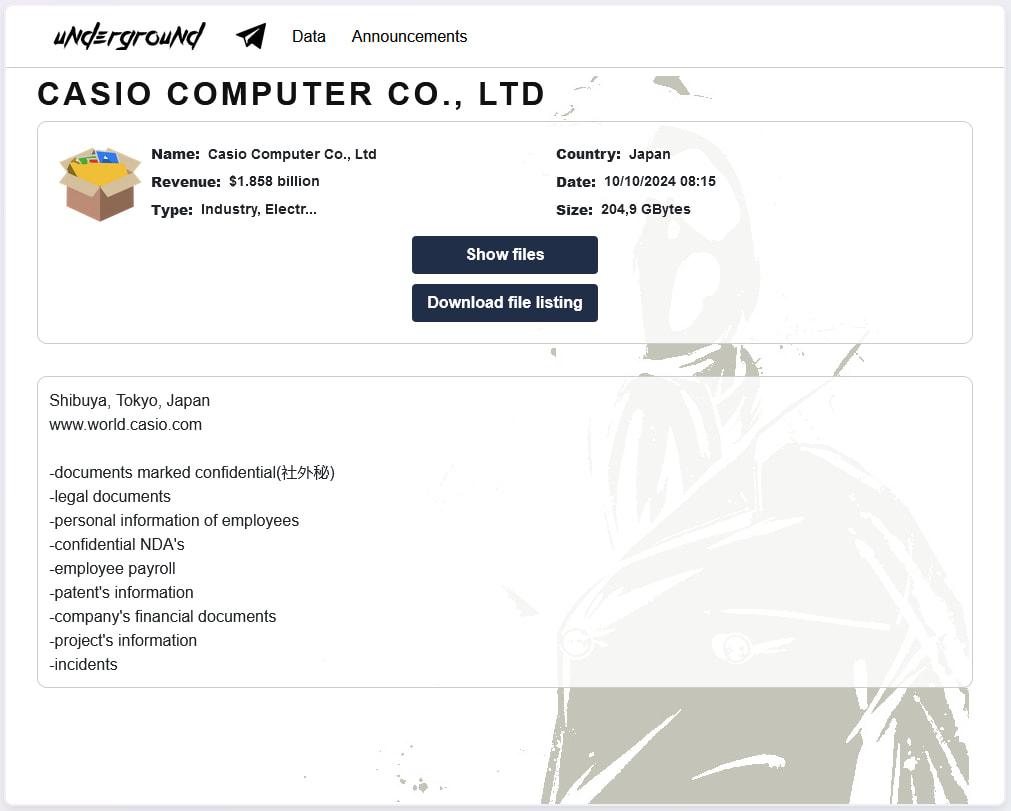
At the moment, the Underground ransomware group has added Casio on its darkish internet extortion portal, leaking troves of information allegedly stolen from the Japanese agency.
The leaked information consists of:
- Confidential paperwork (社外秘)
- Authorized paperwork
- Private information of workers
- Confidential NDA’s
- Worker payroll info
- Patents info
- Firm monetary paperwork
- Challenge info
- Incident studies
If the above is true, the assault has compromised Casio’s workforce and mental property, which may negatively influence its enterprise.
Supply: BleepingComputer
BleepingComputer has contacted Casio once more requesting a touch upon the risk actors’ claims and information leak, however we have now not acquired a response by publication. Due to this fact, the risk actor’s claims stay unverified.
Underground ransomware overview
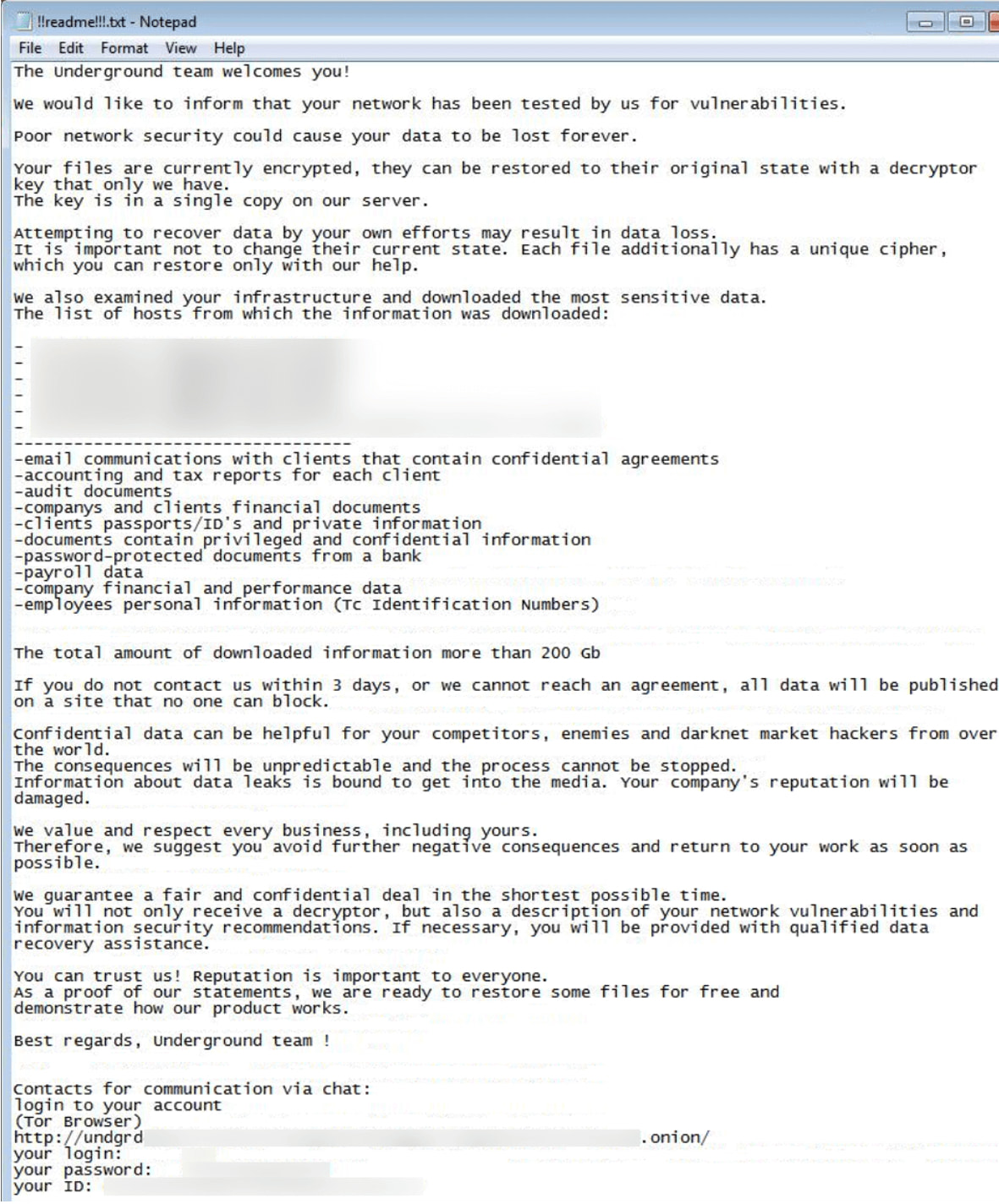
In response to a Fortinet report from late August 2024, Underground is a comparatively small-scale ransomware operation focusing on Home windows techniques since July 2023.
The pressure has been related to the Russian cybercrime group ‘RomCom‘ (Storm-0978), who beforehand delivered Cuba ransomware on breached techniques.
Fortinet studies that throughout the summer season, Underground ransomware operators engaged in exploiting CVE-2023-36884, a distant code execution flaw in Microsoft Workplace, doubtless used as an an infection vector.
As soon as a system is breached, the attackers modify the registry to maintain Distant Desktop periods alive for 14 days after person disconnection, giving them a snug window to take care of entry to the system.
Underground doesn’t append any file extensions to encrypted recordsdata, and it is configured to skip file varieties important for Home windows operation to keep away from rendering the system unusable.
Furthermore, it stops the MS SQL Server service to unencumber information for theft and encryption, maximizing the assault’s influence.
As is the case with most Home windows ransomware, Underground deletes shadow copies to make simple information restoration not possible.
Supply: Fortinet
An uncommon trait in Underground’s extortion ways is that it additionally leaks the stolen information on Mega, selling hyperlinks to archives hosted there through its Telegram channel, maximizing the publicity and availability of the information.
Underground ransomware’s extortion portal at present lists 17 victims, most of whom are primarily based within the USA.
Whether or not or not the Casio assault would be the risk group’s breakthrough into the mainstream, adopted by a better assault quantity/tempo, stays to be seen.
