
Forty new variants of the TrickMo Android banking trojan have been recognized within the wild, linked to 16 droppers and 22 distinct command and management (C2) infrastructures, with new options designed to steal Android PINs.
That is being reported by Zimperium, following an earlier report by Cleafy that regarded into some, however not all variants at present in circulation.
TrickMo was first documented by IBM X-Pressure in 2020, however it’s thought to have been utilized in assaults in opposition to Android customers since not less than September 2019.
Faux lock display screen steals Android PINs
Key options of the brand new TrickMo model embrace one-time password (OTP) interception, display screen recording, knowledge exfiltration, distant management, and extra.
The malware makes an attempt to abuse the highly effective Accessibility Service permission to grant itself extra permissions and faucet on prompts robotically as wanted.
As a banking trojan, it serves customers overlays of phishing login screens to varied banks and monetary institutes to steal their account credentials and allow the attackers to carry out unauthorized transactions.
Supply: Zimperium
Zimperium analysts dissecting these new variants additionally report a brand new misleading unlock display screen mimicking the actual Android unlock immediate, designed to steal the person’s unlock sample or PIN.
“The misleading Consumer Interface is an HTML web page hosted on an exterior web site and is displayed in full-screen mode on the gadget, making it appear to be a authentic display screen,” explains Zimperium.
“When the person enters their unlock sample or PIN, the web page transmits the captured PIN or sample particulars, together with a singular gadget identifier (the Android ID) to a PHP script.”
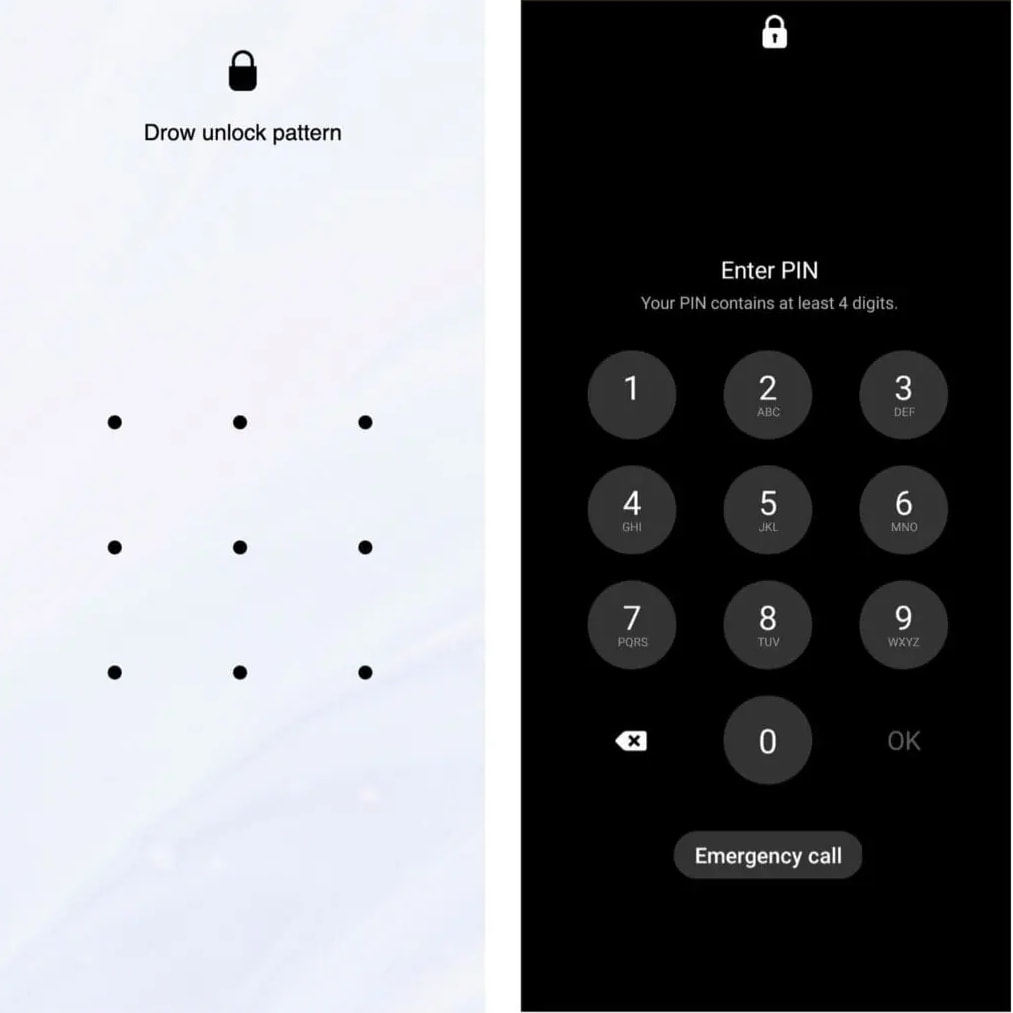
Supply: Zimperium
Stealing the PIN permits the attackers to unlock the gadget when it is not actively monitored, probably in late hours, to carry out on-device fraud.
Uncovered victims
Because of improperly secured C2 infrastructure, Zimperium was additionally in a position to decide that not less than 13,000 victims, most situated in Canada and important numbers additionally discovered within the United Arab Emirates, Turkey, and Germany, are impacted by this malware.
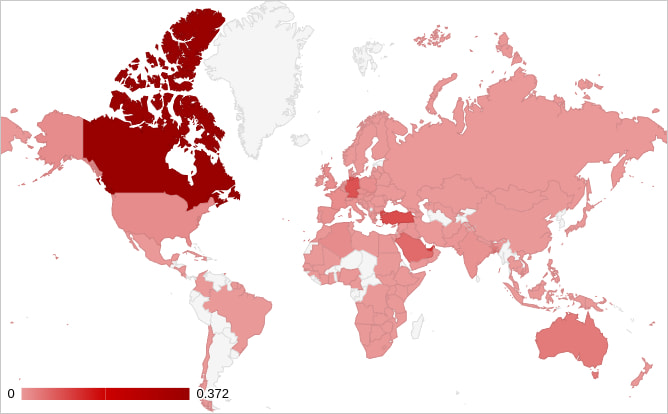
Supply: Zimperium
This quantity corresponds to “a number of C2 servers,” in keeping with Zimperium, so the whole variety of TrickMo victims is probably going greater.
“Our evaluation revealed that the IP listing file is commonly up to date each time the malware efficiently exfiltrates credentials,” explains Zimperium.
“We found tens of millions of data inside these recordsdata, indicating the intensive variety of compromised gadgets and the substantial quantity of delicate knowledge accessed by the Risk Actor.”
Cleafy beforehand withheld indicators of compromise from the general public as a result of misconfigured C2 infrastructure that would expose sufferer knowledge to the broader cybercrime group. Zimperium has now opted to put up the whole lot on this GitHub repository.
Nevertheless, TrickMo’s focusing on scope seems broad sufficient to embody app sorts (and accounts) past banking, together with VPN, streaming platforms, e-commerce platforms, buying and selling, social media, recruitment, and enterprise platforms.
Cleafy beforehand withheld indicators of compromise from the general public as a result of misconfigured C2 infrastructure that would expose sufferer knowledge to the broader cybercrime group, however Zimperium now opted to put up the whole lot on this GitHub repository.
TrickMo is at present spreading by means of phishing, so to attenuate the chance of an infection, keep away from downloading APKs from URLs despatched by way of SMS or direct messages by individuals you do not know.
Google Play Defend identifies and blocks recognized variants of TrickMo, so guaranteeing it is energetic on the gadget is essential in defending in opposition to the malware.
