Cybersecurity researchers have uncovered a complicated Android malware marketing campaign often known as “Tria Stealer,” which is concentrating on customers in Malaysia and Brunei to gather delicate data comparable to SMS knowledge, name logs, WhatsApp messages, and emails.
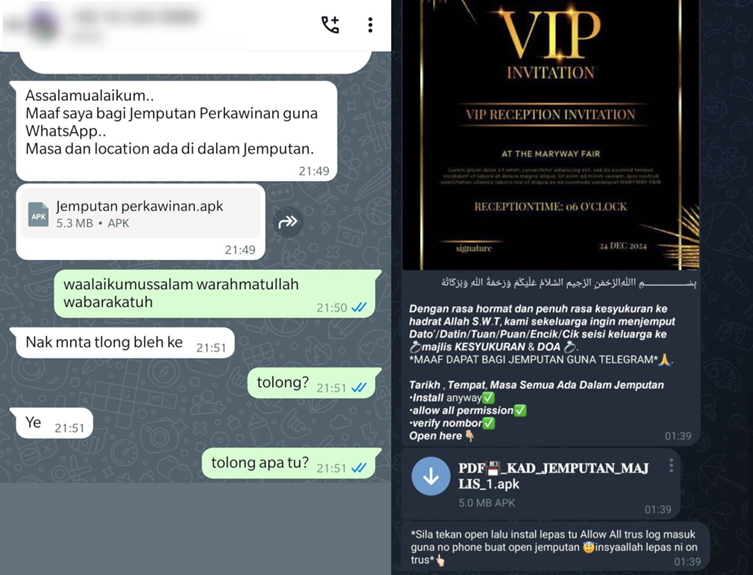
The malware marketing campaign, which has been lively since March 2024, makes use of wedding ceremony invites as a lure to trick victims into downloading malicious apps.
This marketing campaign showcases the rising sophistication of Android threats, in addition to the potential dangers of information breaches and account hijacking.
How Tria Stealer Operates
The Tria Stealer malware disguises itself as a official Android app, usually themed round wedding ceremony invites. Victims are tricked into putting in the app by receiving messages through WhatsApp or Telegram, usually despatched by compromised accounts.
As soon as downloaded and put in, the app requests harmful permissions, comparable to entry to SMS, name logs, and community state. It additionally masquerades as a system settings app to keep away from suspicion.
Upon set up, Tria Stealer collects delicate data, together with SMS messages, name logs, machine particulars, and even messages from apps like WhatsApp and Gmail.
This knowledge is then exfiltrated to the attackers via Telegram bots, which act as Command and Management (C2) servers.
The researchers recognized two variations of Tria Stealer, with the second model, launched in August 2024, introducing superior options.
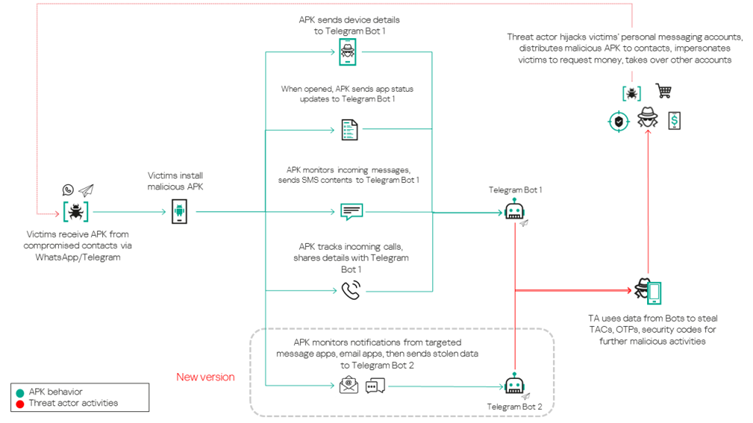

The malware makes use of the BroadcastReceiver perform to watch incoming messages and calls, enabling it to intercept essential data like one-time passwords (OTPs) and transaction authorization codes (TACs).
These codes are then used to hijack accounts on platforms comparable to WhatsApp, Telegram, and banking purposes.
Moreover, newer variants of the malware embody performance for stealing knowledge from notifications posted by fashionable messaging and e mail apps, together with Gmail, WhatsApp Enterprise, and Yahoo Mail.

The stolen knowledge is repackaged into particular codecs and despatched to totally different Telegram bots primarily based on its kind, showcasing an organized strategy by the menace actors.
Penalties of the Assault
As soon as Tria Stealer compromises accounts, it serves two main functions:
- Distribution of Malware: The malware sends the malicious app hyperlink to the sufferer’s contacts through group chats and direct messages, tricking extra customers into downloading it and perpetuating the an infection.
- Monetary Fraud: Impersonating the account proprietor, attackers request cash transfers from the sufferer’s contacts, usually leading to monetary losses.
Specialists warn that the stolen data may be used for different nefarious functions, comparable to resetting account passwords, accessing on-line banking methods, or compromising extra platforms reliant on SMS or e mail authentication.
Suspected Origin and Goal Victims
Investigations recommend that the marketing campaign is orchestrated by an Indonesian-speaking menace actor, evidenced by embedded Indonesian language strings and naming patterns within the malware.
Whereas no particular person concentrating on has been noticed, the vast majority of victims are in Malaysia and Brunei, with Malaysia being probably the most affected.
An identical malware marketing campaign, UdangaSteal, was lively in Southeast Asia in 2023 and early 2024. Nonetheless, researchers don’t attribute Tria Stealer to the identical menace actor, because it demonstrates distinctive code buildings, totally different Telegram bot setups, and enhanced performance.
Given the rise of such refined malware, cybersecurity specialists suggest the next precautions:
- Keep away from Downloading APK Recordsdata from Unknown Sources: Solely obtain apps immediately from trusted sources just like the Google Play Retailer.
- Confirm Messages Earlier than Clicking: Be cautious of messages requesting app installations, even when they seem to return from mates or trusted contacts.
- Allow Two-Issue Authentication (2FA): Use 2FA wherever potential to safe your accounts.
- Use Dependable Safety Options: Set up cellular antivirus instruments to detect and block malware.
The Tria Stealer malware marketing campaign highlights the evolving techniques of cybercriminals concentrating on Android customers.
By leveraging social engineering strategies and superior knowledge exfiltration strategies, this malware poses a critical menace to private and monetary safety. Customers are urged to stay vigilant and undertake finest practices to safeguard in opposition to such assaults.
Acquire Risk Intelligence with TI Lookup to enhance your organization’s safety - Get 50 Free Request
