A big vulnerability has been recognized in TP-Hyperlink’s HomeShield perform, affecting a spread of their gadgets, together with the Archer, Deco, and Tapo collection routers.
This vulnerability, labeled CVE-2024-53375, permits attackers to take advantage of a flaw within the gadget firmware, resulting in the potential injection of malicious instructions by unauthorized customers.
This text explores the small print of this vulnerability, its implications, and the mandatory steps for mitigation.
Understanding the Vulnerability
The vulnerability resides within the TP-Hyperlink routers’ firmware, particularly in capabilities associated to executing system instructions.
Leveraging 2024 MITRE ATT&CK Outcomes for SME & MSP Cybersecurity Leaders – Attend Free Webinar
Found in each older and the newest firmware variations (as of November 2024), this flaw can result in Distant Code Execution (RCE) on the gadgets.

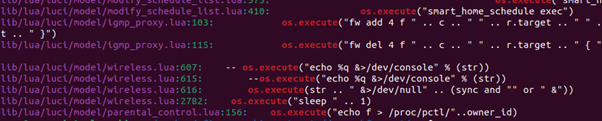
In line with the report from Thottysploity, the core subject lies in a perform related to TP-Hyperlink’s avira.lua file, the place an improperly sanitized variable, ownerId, is handed to the os.execute perform.
This oversight permits attackers to execute arbitrary instructions with root privileges, gaining full management over the gadget.
The Exploitation Course of
To use this vulnerability, an attacker should authenticate themselves, though the authentication course of has already been streamlined, due to current exploit frameworks obtainable on-line.
The attacker can craft a malicious payload that manipulates the ownerId parameter, granting them entry to delicate recordsdata, corresponding to /and so on/passwd and /and so on/shadow, successfully exposing person credentials. Under is a pattern code snippet used for the exploitation:
-- Weak Lua code in avira.lua
native perform tmp_get_sites(information)
native ownerId = information.ownerId -- That is the place the vulnerability lies
os.execute("command with " .. ownerId) -- Malicious command injection level
finish
-- Exploit code
native payload = {
ownerId = "malicious command",
other_params = "values"
}
-- Perform name that triggers the vulnerability
tmp_get_sites(payload)Technical Evaluation and Code Execution
The firmware evaluation concerned extracting and emulating the firmware utilizing instruments like binwalk and qemu-arm-static.
Safety researchers had been in a position to delve into the firmware’s filesystem and determine the susceptible code paths that result in the os.execute misuse.
This detailed examination revealed the particular misuse instances, permitting them to assemble a dependable proof-of-concept exploit.Under is an instance command used to extract the firmware:
binwalk -e firmware.binAfter extracting and emulating the firmware, researchers may navigate the filesystem and determine key vulnerability factors, particularly within the /usr/lib/lua/luci listing the place the Lua scripts had been positioned.

To deal with this vulnerability, TP-Hyperlink customers are suggested to replace their router firmware as quickly as TP-Hyperlink releases a patch. Within the meantime, listed below are some beneficial mitigation technique.
Guarantee all enter information, corresponding to ownerId, is correctly validated and sanitized utilizing capabilities like tonumber in Lua to stop injection assaults.
The TP-Hyperlink HomeShield vulnerability underscores the crucial significance of correct enter validation in firmware improvement.
Whereas TP-Hyperlink is anticipated to launch a patch quickly, customers should stay vigilant and apply beneficial safety practices.
By understanding and addressing these points, customers can higher defend their gadgets and private info from potential cyber threats.
Analyse Superior Malware & Phishing Evaluation With ANY.RUN Black Friday Offers : Rise up to three Free Licenses.

