A classy cyber marketing campaign orchestrated by the Chinese language Superior Persistent Risk (APT) group, Silver Fox, has been uncovered, concentrating on healthcare providers in North America.
The attackers exploited Philips DICOM Viewer software program to deploy malicious payloads, together with a backdoor distant entry software (RAT), a keylogger, and a crypto miner.
This marketing campaign highlights the evolving techniques of cybercriminals concentrating on important sectors like healthcare.
Technical Evaluation of the Assault
The Silver Fox group employed trojanized variations of MediaViewerLauncher.exe, the executable for Philips DICOM Viewer, as their major assault vector.
These malicious samples had been submitted to VirusTotal from america and Canada between December 2024 and January 2025.
The malware cluster demonstrated superior evasion methods, together with PowerShell exclusions to bypass Home windows Defender and encrypted payloads to keep away from detection.
The an infection course of started with reconnaissance actions utilizing native Home windows utilities similar to ping.exe and ipconfig.exe.
Following this, the malware contacted an Alibaba Cloud bucket to obtain encrypted payloads disguised as picture recordsdata.
In response to ForeScout, these payloads had been decrypted into executable recordsdata that included TrueSightKiller (used to disable antivirus software program), a backdoor (ValleyRAT), a keylogger, and a crypto miner.
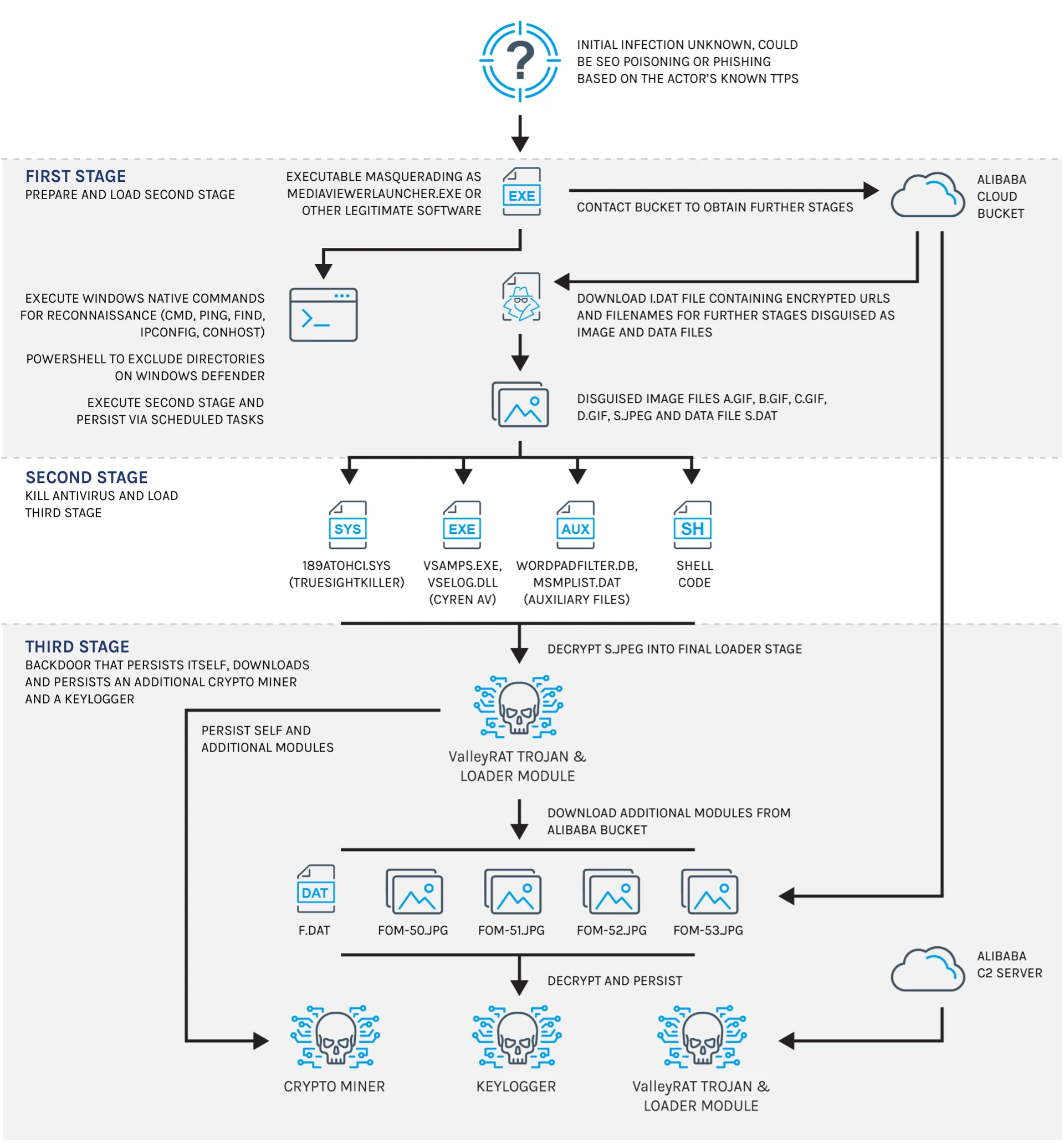

Every stage of the malware was designed to evade detection by way of obfuscation methods like API hashing and oblique management stream manipulation.
As soon as deployed, the ValleyRAT backdoor established communication with a command-and-control (C2) server hosted on Alibaba Cloud.
This allowed attackers to take care of persistent entry to compromised programs whereas concurrently logging consumer exercise and exploiting system sources for cryptocurrency mining.
Broader Implications for Healthcare Safety
Silver Fox’s marketing campaign underscores the vulnerability of healthcare organizations to cyber threats past ransomware.
By concentrating on medical functions like DICOM viewers, which are sometimes utilized by sufferers to entry their medical photos, the attackers exploit potential entry factors into healthcare networks.
Contaminated affected person units introduced into hospitals or linked by way of telehealth providers might function conduits for additional community compromise.
This marketing campaign additionally marks an evolution in Silver Fox’s techniques.
Traditionally targeted on Chinese language-speaking victims and governmental establishments, the group has expanded its scope to incorporate sectors similar to finance, e-commerce, and now healthcare.
Their use of superior methods like DLL sideloading, course of injection, and driver-based antivirus evasion displays their rising sophistication.
To counter such threats, healthcare supply organizations (HDOs) ought to undertake sturdy cybersecurity measures:
- Limit Software program Sources: Keep away from downloading software program from untrusted sources or affected person units.
- Community Segmentation: Isolate untrusted units from important hospital infrastructure.
- Endpoint Safety: Deploy up-to-date antivirus or endpoint detection and response (EDR) options.
- Steady Monitoring: Monitor community visitors and endpoint exercise for indicators of compromise (IoCs).
- Proactive Risk Looking: Actively seek for malicious exercise aligned with identified APT conduct.
This incident serves as a stark reminder of the necessity for heightened vigilance in securing healthcare programs towards rising cyber threats.
Accumulate Risk Intelligence on the Newest Malware and Phishing Assaults with ANY.RUN TI Lookup -> Strive free of charge
