A safety researcher has uncovered crucial vulnerabilities in Eight Sleep’s internet-connected sensible beds, revealing uncovered Amazon Net Companies (AWS) credentials, distant SSH backdoors, and potential entry to customers’ whole house networks.
The findings underscore rising considerations about IoT gadget safety as shoppers more and more undertake linked home equipment for on a regular basis use.
Researcher Discovers AWS Keys and Distant Entry Protocols
The investigation started when the researcher, who bought the $2,000 temperature-regulated Eight Sleep Pod mattress cowl, found stay AWS credentials embedded within the gadget’s firmware.
These keys granted write entry to Amazon Kinesis information streams, doubtlessly permitting attackers to control sleep information or inflict substantial monetary injury by extreme API requests.
Whereas Eight Sleep revoked the keys after being notified, the incident highlighted systemic safety gaps.
Additional evaluation revealed a extra alarming difficulty: a distant SSH backdoor accessible through remote-connectivity-api.8slp.web.

Configuration information confirmed engineers at eng@eightsleep.com may bypass commonplace code evaluate processes to execute arbitrary instructions on customers’ beds, which function on Linux-based programs.


“This isn’t nearly adjusting mattress temperatures,” the researcher famous. “It’s a gateway to each gadget in your Wi-Fi—laptops, sensible locks, safety cameras.”
The SSH vulnerability grants unprecedented entry to delicate information, together with:
- Sleep patterns and mattress occupancy detection
- Distant activation of vibration alerts or alarms
- Community traversal capabilities to linked gadgets
Notably, Eight Sleep’s system lacks user-accessible logs to observe such entry.
The researcher in contrast the danger to Uber’s 2014 “God Mode” scandal, the place workers tracked politicians and celebrities, stressing that compromised engineering credentials may allow comparable abuses.
Firm Response and Shopper Alternate options
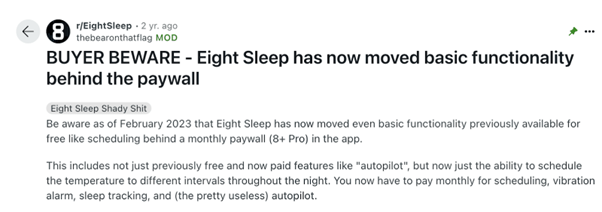
Eight Sleep has not publicly addressed the SSH backdoor considerations however beforehand marketed sleep-tracking options by social media posts like “We’re watching you sleep.”

In the meantime, the researcher devised a low-tech workaround utilizing a $150 aquarium chiller—a tool using the identical thermoelectric expertise—by rerouting the mattress’s cooling tubes.


This modification preserves temperature management with out web dependency, subscription charges, or assault surfaces.
This incident displays widespread points in IoT ecosystems, the place comfort usually overshadows safety.
The researcher urged producers to undertake zero-trust architectures and encrypted native controls: “Your mattress shouldn’t be a Malicious program for hackers.”
For now, shoppers should weigh the advantages of linked gadgets in opposition to dangers to their digital and bodily security.
Analogies to historic breaches (e.g., Uber’s “God Mode”) present layperson-friendly parallels, whereas the aquarium chiller answer presents actionable recommendation with out promotional language.
Free Webinar: Higher SOC with Interactive Malware Sandbox for Incident Response, and Risk Looking - Register Right here
