
A hybrid espionage/affect marketing campaign performed by the Russian menace group ‘UNC5812’ has been uncovered, focusing on Ukrainian navy recruits with Home windows and Android malware.
In response to Google’s menace intelligence, the marketing campaign impersonated a “Civil Protection” persona together with a web site and devoted Telegram channel to distribute malware by way of a faux recruitment avoidance app dubbed “Sunspinner” by the researchers.
The marketing campaign targets Home windows and Android gadgets utilizing distinct malware for every platform, giving the attackers knowledge theft and real-time spying capabilities.
Google has carried out protections to dam the malicious exercise, however the operation highlights Russia’s continued use and intensive capabilities within the cyber-warfare area.
Faux “Civil Protection” persona
UNC5812’s persona doesn’t try and impersonate Ukraine’s Civil Protection or any authorities businesses however is as an alternative promoted as a official Ukraine-friendly group that gives Ukrainian conscripts with useful software program instruments and recommendation.
The persona makes use of a Telegram channel and a web site to have interaction potential victims and ship narratives in opposition to Ukraine’s recruitment and mobilization efforts, aiming to stir mistrust and resistance among the many inhabitants.
When Google found the marketing campaign on September 18, 2024, the “Civil Protection” channel on Telegram had 80,000 members.
Supply: Google
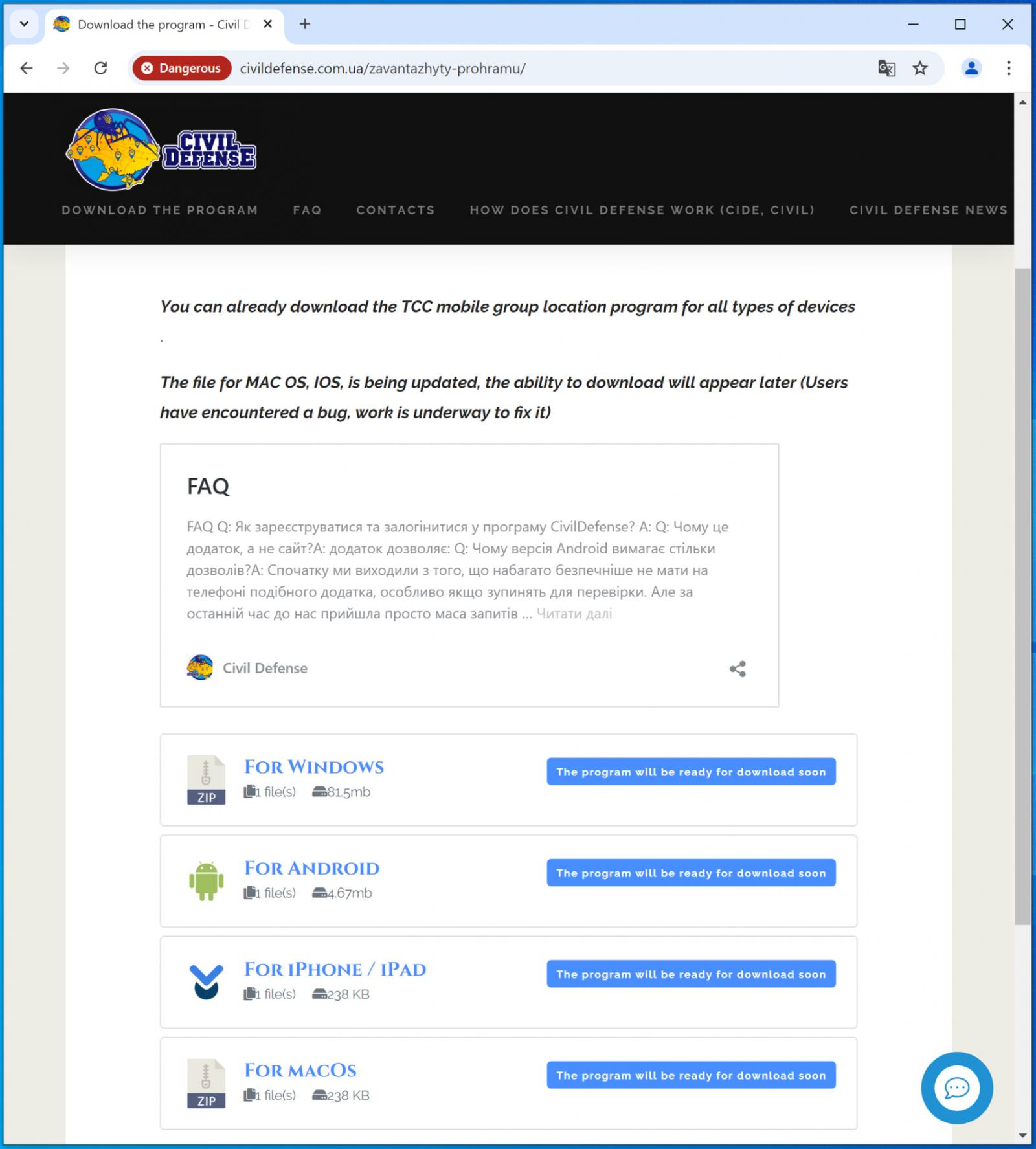
Customers tricked into visiting Civil Protection’s web site are taken to a obtain web page for a malicious software promoted as a crowd-sourced mapping instrument that may assist customers monitor the places of recruiters, and keep away from them.
Google calls this app “Sunspinner, and though the app includes a map with markers, Google says the info is fabricated. The app’s solely goal is to cover the set up of malware that takes place within the background.
Supply: Google
Dropping Home windows and Android malware.
The faux apps presents Home windows and Android downloads, and guarantees so as to add iOS and macOS quickly, so Apple platforms should not supported but.
The Home windows obtain installs Pronsis Loader, a malware loader that fetches further malicious payloads from UNC5812’s server, together with the commodity info-stealer ‘PureStealer.’
PureStealer targets data saved in net browsers, like account passwords, cookies, cryptocurrency pockets particulars, e mail purchasers, and messaging app knowledge.
On Android, the downloaded APK file drops CraxsRAT, additionally a commercially out there backdoor.
CraxsRAT permits the attackers to trace the sufferer’s location in actual time, log their keystrokes, activate audio recordings, retrieve contact lists, entry SMS messages, exfiltrate recordsdata, and harvest credentials.
To carry out these malicious actions undeterred, the app methods customers into disabling Google Play Shield, Android’s in-built anti-malware instrument, and manually grant it dangerous permissions.

Supply: Google
Google up to date Google Play protections to detect and block the Android malware early and likewise added the domains and recordsdata related to the marketing campaign to its ‘Protected Searching’ characteristic on Chrome.
The entire record of indicators of compromise related to the most recent UNC5812 marketing campaign is offered right here.
