Cybersecurity researchers have unveiled a complicated method to uncover hackers’ operational infrastructure utilizing passive DNS knowledge.
This groundbreaking methodology sheds gentle on how attackers set up and keep their networks to perpetrate malicious actions whereas remaining resilient to detection.
By leveraging passive DNS evaluation, specialists have made vital strides in figuring out threats earlier than they wreak havoc, thus fortifying defenses towards evolving cyber threats.
Understanding Assault Infrastructure
The spine of any cyberattack lies in its infrastructure, which consists of servers, domains, and compromised gadgets. Attackers make use of varied techniques to keep up their operations whereas evading detection.
A well-liked methodology is infrastructure churn, the place hackers continuously change domains and IPs when one server is detected and blocked. This differs from DNS quick flux, which includes fast, automated IP rotation for a single area.
Leveraging 2024 MITRE ATT&CK Outcomes for SME & MSP Cybersecurity Leaders – Attend Free Webinar
For instance, the CatDDoS botnet, an evolution of the notorious Mirai malware, exemplifies infrastructure churn.
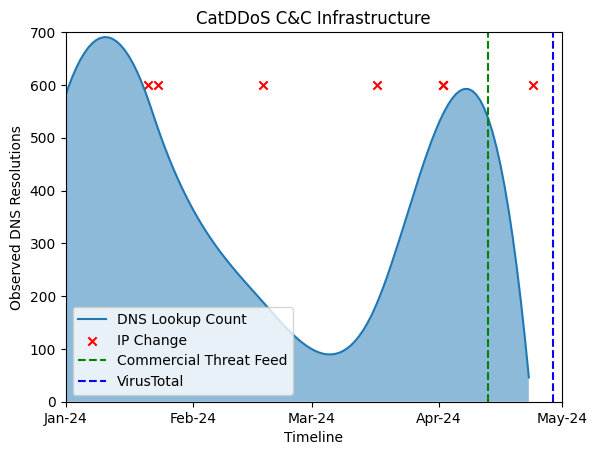

It makes use of different area techniques, akin to OpenNIC domains, alongside refined payload encryption methods like ChaCha20.
Over six months, researchers noticed frequent modifications within the botnet’s command-and-control (C&C) server infrastructure, making conventional detection methods ineffective.
How Passive DNS Works
Passive DNS is a core instrument for uncovering malicious networks. It includes accumulating and analyzing DNS logs from community transit paths, with out actively querying domains.
This historic knowledge contains data of domain-IP relationships, timestamps, and question counts, permitting researchers to map out how attackers function.
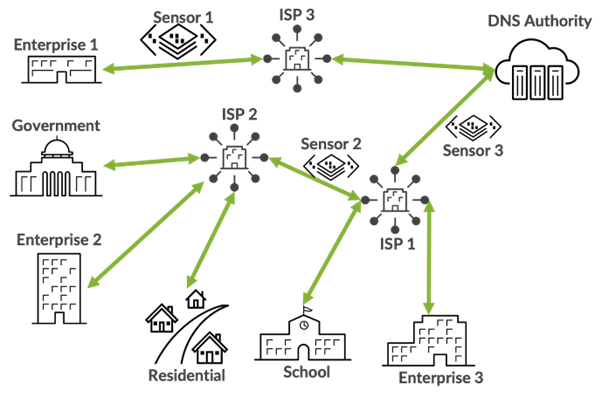
As an example, passive DNS sensors will be deployed throughout numerous community paths like enterprise, authorities, or residential environments.
Even a single DNS question from a malicious area can reveal connections to different suspicious domains or servers. Researchers meticulously clear this knowledge to take away noise (e.g., queries from reputable web sites or content material supply networks).

Actual-Life Purposes of Passive DNS
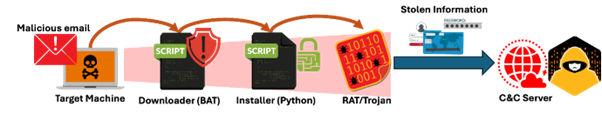
Juniper Menace Labs has successfully used passive DNS knowledge to determine malicious infrastructure earlier than assaults unfold. One standout case concerned the invention of menace actors abusing Cloudflare’s tunneling service to ship distant entry trojans (RATs).
Cybercriminals used phishing emails to contaminate victims with trojans like XWorm, AsyncRAT, and VenomRAT, which then exfiltrated delicate knowledge.

Key Discoveries
- Researchers noticed attackers testing domains and IPs earlier than large-scale assaults.
- By analyzing passive DNS knowledge, they uncovered further C&C servers past public menace feeds.
- Over 13 months, they recognized and mitigated a number of cyber campaigns.
For instance, a marketing campaign energetic between July and August 2024 revealed that attackers created as much as three new domains each 10 days to bypass detection.
Passive DNS sensors have been instrumental in uncovering these domains, highlighting their rising question counts and suspicious domain-IP associations.
The proactive use of passive DNS offers cybersecurity groups a definite benefit. By figuring out zero-day infrastructure earlier, researchers can embrace these domains in blocklists earlier than attackers deploy them at full scale.
This forces hackers to constantly put money into new assets, growing their operational prices and lowering profitability.
Moreover, passive DNS knowledge allows safety suppliers to strengthen their menace intelligence feeds, benefiting organizations subscribed to superior protection options.
As an example, Juniper’s clients obtained up to date SecIntel feeds that blocked newly recognized malicious domains and IPs.
Cybersecurity specialists warning that whereas passive DNS is highly effective, its efficacy will depend on the standard of knowledge and sensor placement. Nonetheless, its advantages in growing attacker prices and lowering the success of cyber campaigns are simple.
This system not solely supplies visibility into rising threats but in addition equips organizations with the instruments to remain one step forward within the ever-changing panorama of cyber warfare.
Examine Actual-World Malicious Hyperlinks,Malware & Phishing Assaults With ANY.RUN - Strive for Free

