Researchers have uncovered a systemic vulnerability throughout the Home windows working system, leveraging its “Finest-Match” charset conversion characteristic to bypass safety checks and execute distant code.
The findings spotlight widespread implications throughout varied purposes, with real-world exploitation eventualities impacting broadly used instruments reminiscent of Microsoft Excel, PHP-CGI, and others.
Charset Conversion and “Finest-Match” Conduct
Home windows programs function on twin encoding programs, Unicode (UTF-16) for contemporary compatibility and legacy ANSI for older purposes.
To bridge these, Home windows employs an inner characteristic referred to as “Finest-Match” mapping, which approximates characters unsupported by a selected code web page to their visually or functionally related counterparts.
For instance, the infinity image (∞) could also be mapped to the digit “8.”Whereas designed with compatibility in thoughts, researchers have demonstrated that this habits inadvertently creates assault vectors, together with Path Traversal, Argument Splitting, and Distant Code Execution (RCE).
Examine Actual-World Malicious Hyperlinks & Phishing Assaults With Menace Intelligence Lookup - Strive for Free
Exploited Vulnerabilities
The research revealed a number of CVEs, together with:
- CVE-2024-4577 (PHP-CGI RCE):
An attacker can compromise PHP-CGI servers with Chinese language or Japanese code pages by appending a specifically crafted question string, ?%ADs, to bypass safety checks. Right here, the Unicode character “Tender Hyphen” (U+00AD) is mapped to a splash (“-“), enabling malicious argument injection—in the end resulting in RCE. - CVE-2024-49026 (Microsoft Excel RCE):
Researchers exploited Excel’s “Open-With” characteristic to bypass argument parsing controls. By renaming an Excel file utilizing fullwidth Unicode characters and injecting malicious arguments, attackers achieved NTLM Relay-based RCE.
How the Exploits Work
Filename Smuggling
This assault depends on characters transformed into path delimiters (/ or ) on particular code pages. For instance, the Yen (¥) and Gained (₩) symbols in Japanese and Korean code pages are transformed into backslashes (), enabling listing traversal.
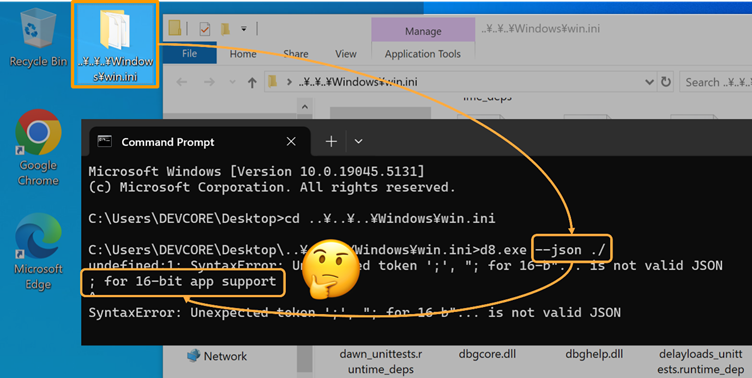

Unintended file entry on the C:/home windows/win.ini:
#embody
int principal() {
LPCWSTR filePath = L"AAAA¥..¥..¥..¥..¥..¥conf¥cuckoo.conf";
HANDLE hFile = CreateFileW(filePath, GENERIC_WRITE, 0, NULL, CREATE_ALWAYS, FILE_ATTRIBUTE_NORMAL, NULL);
CloseHandle(hFile);
return 0;
} On this exploit, malicious filenames bypass listing restrictions, exposing delicate recordsdata like configuration settings.
Argument Splitting
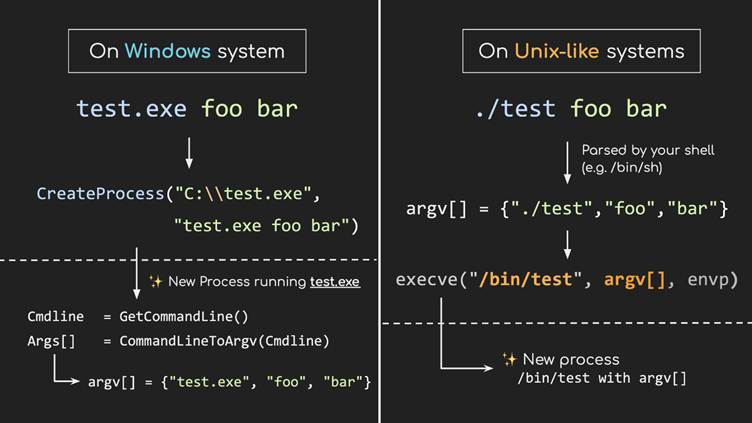
Utilizing fullwidth variations of particular characters (e.g., " for double quotes), attackers inject extra arguments into Home windows command-line processes.

In a Python instance:
subprocess.run(['wget', '-q', f"https://test.tld/{path}.txt"])Right here, offering malicious enter like " –use-askpass=calc " launches calc.exe by splitting the meant command into surprising arguments.
Atmosphere Variable Confusion
This assault exploits finest match habits for atmosphere variables. For instance, question strings and HTTP headers handed through CGI scripts are manipulated to bypass character restrictions, leading to Native File Inclusion (LFI) or different assaults.
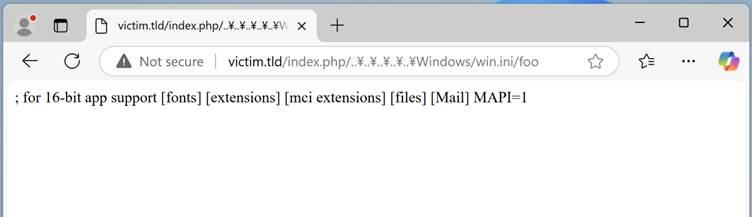

Case Research
- Cuckoo Sandbox Exploit:
Leveraging Python’s reliance on ANSI APIs, researchers infiltrated sandbox hosts by smuggling filenames that traversed into restricted directories. - ElFinder RCE:
A malicious tar archive title, crafted with fullwidth characters, injected arbitrary instructions, launching calc.exe through GNU tar’s –use-compress-program flag.
Although extreme, the vulnerabilities have sparked debate over accountability and repair feasibility. Whereas some distributors, like Putty, promptly patched their software program, others, reminiscent of Curl, deferred to builders to sanitize inputs.
As per a report by Devco report, Microsoft acknowledged the severity of sure instances, reminiscent of CVE-2024-49026, however didn’t situation fixes for broader systemic points tied to legacy Home windows performance.
- Choose Extensive-Character APIs: Utilizing Unicode APIs (e.g., CreateProcessW) prevents unintended ANSI conversions.
- Sanitize Inputs: Guarantee sturdy escaping or validation for all user-supplied information.
- Allow Safe Default Settings: Purposes ought to allow UTF-8 by default, avoiding reliance on legacy code pages.
- Monitor Updates: Builders ought to keep vigilant about patches from affected distributors and libraries.
This revelation of deeply entrenched vulnerabilities, reminiscent of CVE-2024-4577 and CVE-2024-49026, underscores the dangers of legacy compatibility options in fashionable software program ecosystems.
As attackers capitalize on low-level quirks like Home windows’ “Finest-Match” charset habits, each builders and safety consultants should prioritize systemic modifications and safe coding requirements.
Integrating Utility Safety into Your CI/CD Workflows Utilizing Jenkins & Jira -> Free Webinar
