
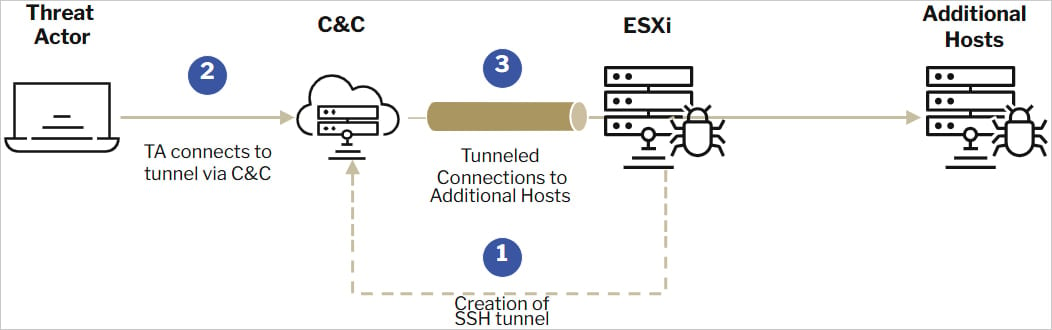
Ransomware actors focusing on ESXi naked steel hypervisors are leveraging SSH tunneling to persist on the system whereas remaining undetected.
VMware ESXi home equipment have a vital function in virtualized environments as they will run on a single bodily server a number of digital machines of a company.
They’re largely unmonitored and have been a goal for hackers trying to entry company networks the place they will steal knowledge and encrypt recordsdata, thus crippling a whole enterprise by rendering all digital machines inaccessible.
Cybersecurity firm Sygnia studies that in lots of instances the compromise is achieved by exploiting recognized flaws or utilizing compromised administrator credentials.
SSHing into the hypervisor
ESXi incorporates a built-in SSH service that enables directors to remotely handle the hypervisor by way of a shell.
Sygnia says that ransomware actors abuse this characteristic to determine persistence, transfer laterally, and deploy ransomware payloads. Since many organizations don’t actively monitor ESXi SSH exercise, attackers can use it stealthily.
“As soon as [the hackers are] on the gadget, establishing the tunneling is an easy job utilizing the native SSH performance or by deploying different widespread tooling with comparable capabilities,” explains Sygnia.
“For instance, by utilizing the SSH binary, a distant port-forwarding to the C2 server could be simply setup by utilizing the next command: ssh –fN -R 127.0.0.1:
“Since ESXi home equipment are resilient and barely shutdown unexpectedly, this tunneling serves as a semi-persistent backdoor throughout the community.”
Supply: Sygnia
Gaps in logging
Sygnia additionally highlights challenges in monitoring ESXi logs, which result in important visibility gaps that ransomware actors know how you can make the most of.
Not like most programs the place logs are consolidated in a single syslog file, ESXi distributes logs throughout a number of devoted log recordsdata, so discovering proof requires piecing collectively info from a number of sources.
The safety agency means that system admins look into these 4 log recordsdata to detect SSH tunneling and ransomware exercise:
- /var/log/shell.log → Tracks command execution in ESXi Shell
- /var/log/hostd.log → Logs administrative actions and person authentication
- /var/log/auth.log → Captures login makes an attempt and authentication occasions
- /var/log/vobd.log → Shops system and safety occasion logs
The hostd.log and vodb.log are prone to additionally include traces of firewall guidelines modification, which is important for permitting persistent SSH entry.
It needs to be famous that ransomware actors typically clear logs to erase proof of SSH entry, modify timestamps, or truncate logs to confuse investigators, so discovering proof isn’t all the time simple.
Finally, it is strongly recommended that organizations centralize ESXi logs by way of syslog forwarding and combine logs right into a Safety Data & Occasion Administration (SIEM) system to detect anomalies.
