The MacroPack framework, initially designed for Pink Group workouts, is being abused by menace actors to deploy malicious payloads, together with Havoc, Brute Ratel, and PhatomCore.
Safety researchers at Cisco Talos have analyzed malicious doc submissions on VirusTotal from numerous nations, together with the US, Russia, China, and Pakistan.
These paperwork assorted of their lures, sophistication, and an infection vectors, indicating that MacroPack is being abused by a number of menace actors, signifying a possible pattern.
MacroPack payload technology
MacroPack is a proprietary software centered on Pink Group workouts and adversary simulations, created by French developer Emeric Nasi (dba BallisKit).
It affords superior options reminiscent of anti-malware bypass, anti-reversing strategies, and the power to construct numerous doc payloads with code obfuscation and embed undetectable VB scripts.
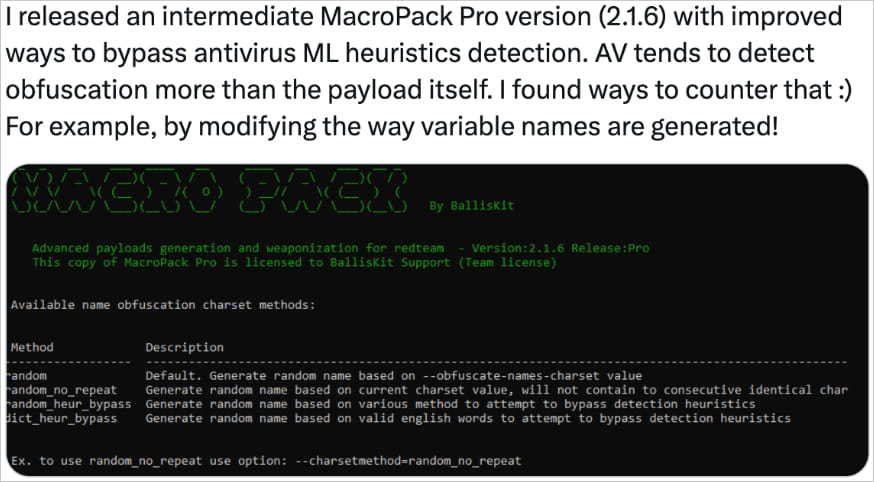
Supply: Cisco
There’s additionally a “lite” open-source model known as MacroPack Group, which is now not maintained.
Cisco reviews catching many doc samples within the wild that carry indicators they have been created on MacroPack, together with Markov-chain-based operate and variable renaming, elimination of feedback and surplus house characters that decrease static evaluation detection charges, and strings encoding.
The giveaway attribute on all these paperwork indicating they have been constructed on MacroPack Professional is the existence of 4 non-malicious VBA subroutines that the researchers say they confirmed have been added by the skilled model of the framework.
Supply: Cisco
Victims opening these Microsoft Workplace paperwork will set off a first-stage VBA code, which masses a malicious DLL that connects to the attacker’s command and management (C2) server.
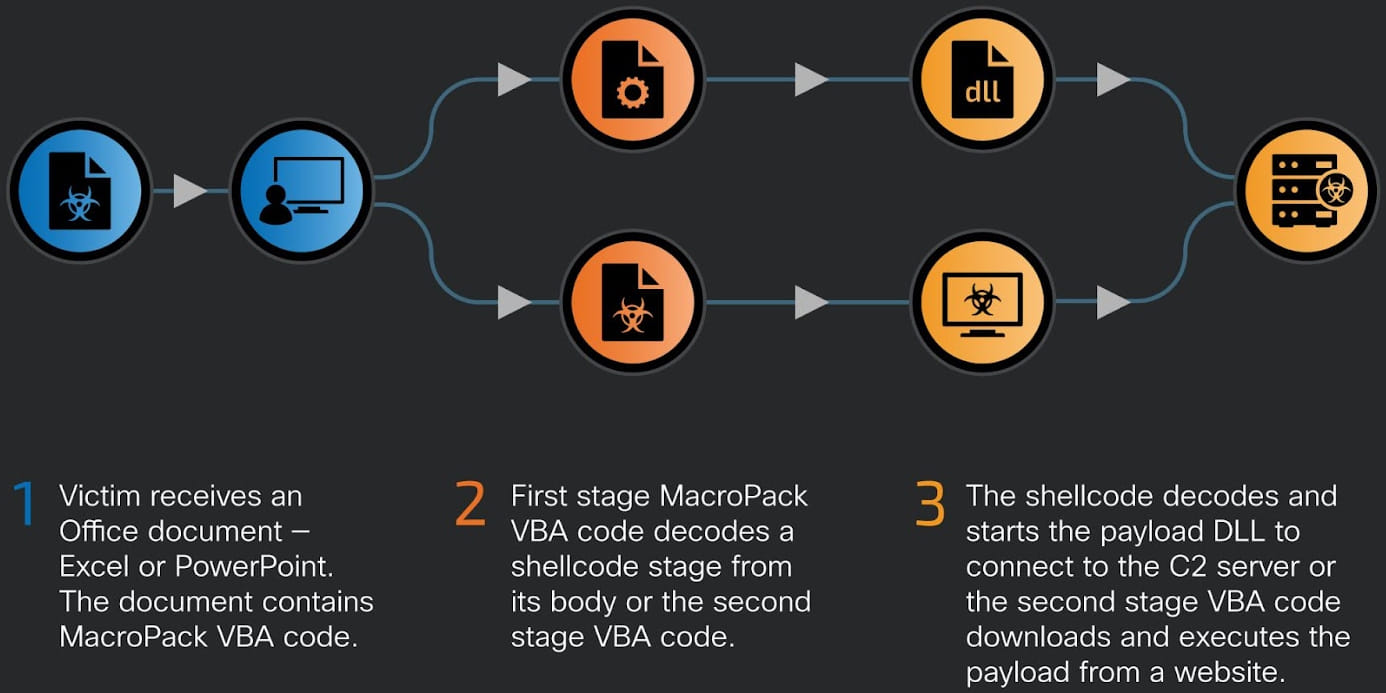
Supply: Cisco
Paperwork within the wild
Cisco Talos’ report identifies 4 vital clusters of malicious exercise related to MacroPack abuse, that are summarized as follows:
- China: Paperwork from IP addresses in China, Taiwan, and Pakistan (Could-July 2024) instructed customers to allow macros, delivering Havoc and Brute Ratel payloads. These payloads related to C2 servers positioned in Henan, China (AS4837).
- Pakistan: Paperwork with Pakistani navy themes have been uploaded from areas in Pakistan. One doc, posing as a round from the Pakistan Air Drive, and one other as an employment affirmation, deployed Brute Ratel badgers. The paperwork communicated utilizing DNS over HTTPS and Amazon CloudFront, with one embedding a base64-encoded blob for Adobe Expertise Cloud monitoring.
- Russia: A clean Excel workbook uploaded from a Russian IP in July 2024 delivered PhantomCore, a Golang-based backdoor used for espionage. The doc ran multi-stage VBA code, which tried to obtain the backdoor from a distant URL.
- U.S.: A doc uploaded in March 2023 posed as an encrypted NMLS renewal kind and used Markov Chain-generated operate names to evade detection. The doc contained multi-stage VBA code, which checked for sandbox environments earlier than trying to obtain an unknown payload by way of mshta.exe.
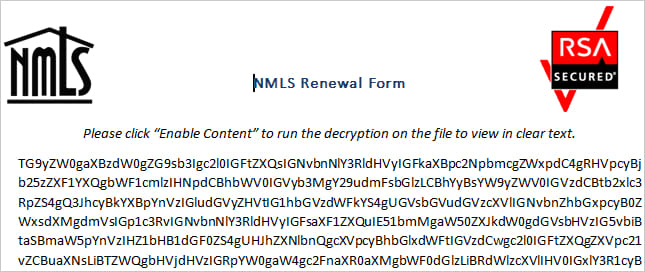
Supply: Cisco
Brute Ratel is a post-exploitation assault framework hackers have been deploying as an alternative choice to Cobalt Strike since mid-2022.
Ransomware teams have been additionally noticed utilizing a cracked model of the software to evade EDRs and AVs throughout assaults.
The abuse of MacroPack provides one other layer of stealth to those assaults and is a worrying improvement for defenders.
BleepingComputer has contacted Emeric Nasi concerning the noticed abuse, however now we have not acquired a response but.
