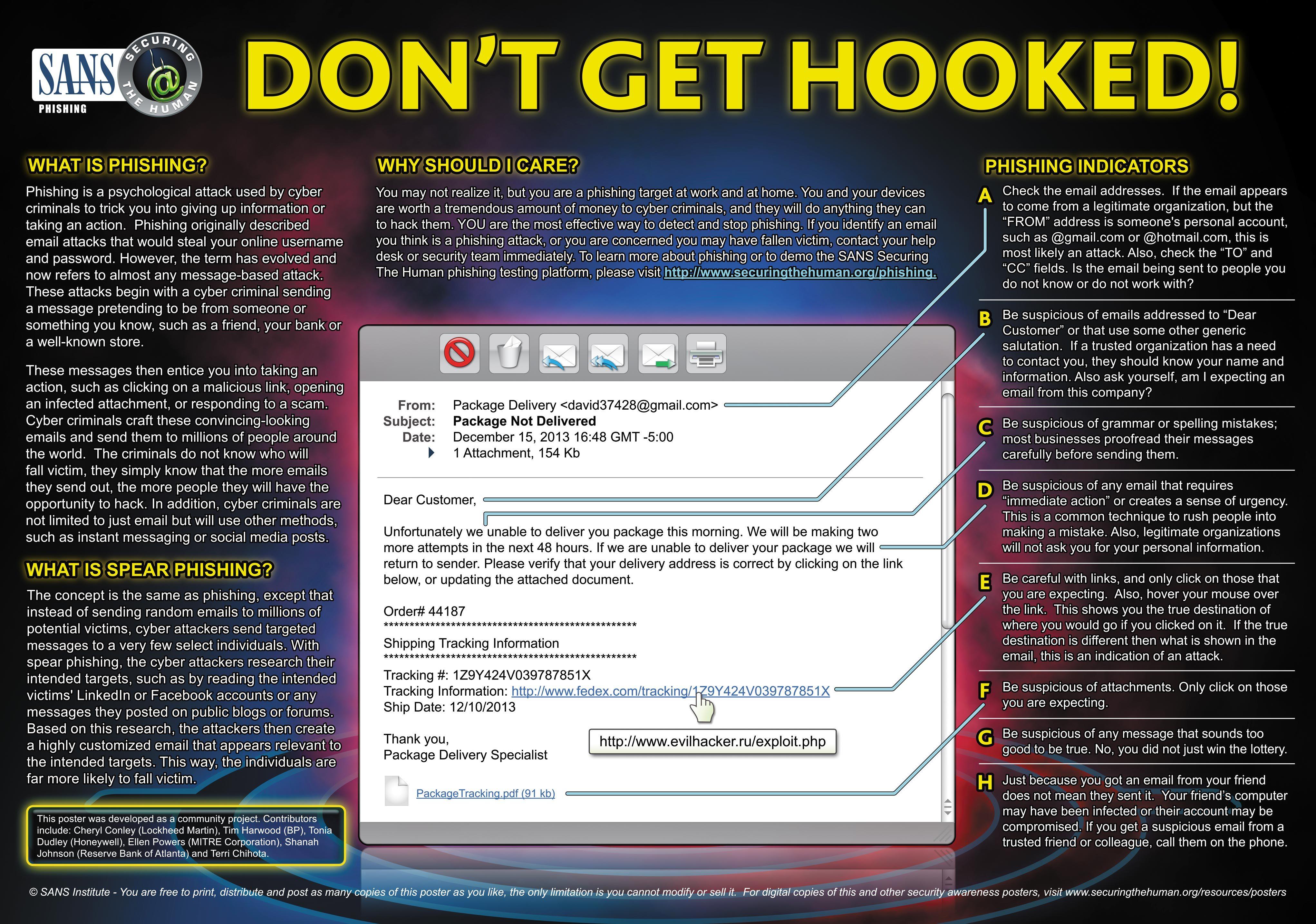
In right now’s interconnected world, the place digital communication and transactions dominate, phishing assaults have develop into an ever-present menace.
By masquerading as reliable entities, phishing assaults deceive customers and organizations into divulging delicate info, comparable to passwords, monetary knowledge, and private particulars.
Phishing assaults, among the many most prevalent strategies cyber criminals make use of, will be simple but extremely efficient.
Not like breaching fortified firewalls and different sturdy defenses, tricking people into clicking malicious hyperlinks or opening contaminated attachments is relatively extra simple.
The aims of phishing assaults differ, starting from delivering malware to stealing funds and pilfering credentials.
Nonetheless, exercising adequate vigilance can detect most makes an attempt to extract private info.
What’s Phishing Assault?


A phishing assault is a misleading tactic employed by cybercriminals to trick people or organizations into revealing delicate info or performing sure actions that may be exploited for malicious functions.
Phishing assaults sometimes contain impersonating a reliable entity by emails, textual content messages, or fraudulent web sites, comparable to a respectable firm, authorities company, or monetary establishment.
The attackers goal to govern their targets into divulging confidential knowledge, comparable to passwords, bank card numbers, social safety numbers, or login credentials.
They steadily make use of varied psychological, urgency, and social engineering strategies to create a perception in legitimacy and urgency, luring victims to carry out the specified actions.
Phishing assaults can result in extreme penalties, together with identification theft, monetary loss, unauthorized entry to accounts, and compromised programs. Consequently, it’s important to keep up vigilance and implement preventative measures to defend towards such assaults.
Sorts of Phishing Assaults

Cybercriminals make use of a number of varieties of phishing assaults to take advantage of people and organizations. Some widespread sorts embody:
- Electronic mail Phishing: Attackers ship misleading emails, typically impersonating respectable organizations, desiring to trick recipients into revealing delicate info or performing malicious actions.
- Spear Phishing: This assault addresses particular people or organizations, utilizing personalised info to look extra genuine and enhance the chance of success.
- Whaling: Much like spear phishing, whaling targets high-profile people, comparable to CEOs or high executives, aiming to achieve entry to helpful firm info or monetary belongings.
- Smishing: Phishing assaults are performed by way of SMS or textual content messages, wherein perpetrators persuade targets to click on on fraudulent hyperlinks or present private info.
- Vishing: Vishing, also referred to as voice phishing, entails attackers making telephone calls, posing as representatives of respected organizations, and convincing victims to disclose delicate info.
- Pharming: Intruders manipulate DNS settings or make use of malware to reroute customers from respectable web sites to fraudulent ones, the place they will harvest delicate knowledge.
- Clone Phishing: Attackers create a reproduction of a respectable electronic mail or web site, making minor modifications to deceive recipients into offering their credentials or different delicate knowledge.
- Man-in-the-Center (MitM) Assaults: In any such assault, the attacker intercepts communication between two events, gaining unauthorized entry to info shared throughout the dialog.
- Enterprise Electronic mail Compromise (BEC): Attackers impersonate firm executives or workers to trick workers into initiating unauthorized wire transfers or revealing delicate enterprise info.
- Angler Phishing: This sort of assault targets social media platforms, the place attackers create faux buyer help accounts or pages to steal login credentials or private info.
How Does a Easy Phishing Assault Result in Main Cyber Assaults
- Preliminary Compromise: In a easy phishing assault, an attacker sends a fraudulent electronic mail or message to trick a person into divulging delicate info, comparable to login credentials or account particulars. The attacker good points unauthorized entry to the sufferer’s account or community if profitable.
- Credential Harvesting: With the compromised credentials, the attacker can entry the sufferer’s electronic mail, social media, or different accounts. This enables them to assemble extra details about the sufferer, together with contacts, private particulars, and probably extra login credentials.
- Lateral Motion: With entry to the sufferer’s account or community, the attacker can transfer laterally inside the group’s programs, escalating their privileges and looking for extra targets. They could exploit vulnerabilities within the community, seek for weakly protected accounts, or goal privileged customers with greater entry ranges.
- Inside Reconnaissance: As soon as contained in the community, the attacker conducts reconnaissance to assemble details about the group’s infrastructure, programs, and potential high-value targets. They could seek for helpful knowledge, mental property, or delicate info that could possibly be monetized or used for future assaults.
- Persistence and Persistence: The attacker could set up persistence inside the compromised programs by putting in backdoors, creating extra person accounts, or modifying current configurations. This enables them to keep up entry even when preliminary entry factors are found and patched.
- Growth of the Assault: With a foothold within the group’s community, the attacker can launch extra superior assaults comparable to spear-phishing, ransomware deployment, or knowledge exfiltration. They’ll leverage compromised accounts and programs to distribute malicious payloads, infect different units, or acquire unauthorized entry to vital infrastructure.
- Superior Malware Deployment: The attacker could ship refined malware or exploit kits to compromise extra programs or acquire management over vital infrastructure. This will embody deploying ransomware, stealing delicate knowledge, or conducting sabotage actions.
- Information Breach and Injury: A profitable phishing assault can lead to an information breach, exposing delicate info, buyer knowledge, or proprietary info. The implications embody monetary losses, reputational harm, authorized ramifications, and regulatory non-compliance.
Prime Prevention Guidelines for Phishing Assaults
Phishing assaults have emerged as a big menace in right now’s digital panorama, exploiting human vulnerability moderately than relying solely on technical vulnerabilities.
Cybercriminals make the most of misleading techniques to trick people and organizations into divulging delicate info or performing malicious actions. Implementing sturdy preventive measures is essential to fight this pervasive menace.
The next prevention guidelines supplies a complete and detailed strategy to shutting down phishing assaults.
By following these pointers, people and organizations can improve their defenses, reduce the chance of falling sufferer to phishing makes an attempt, and safeguard helpful info and belongings.


- Increase Consciousness
- Educate people concerning the nature of phishing assaults, commonplace strategies employed, and potential penalties.
- Prepare workers to acknowledge phishing indicators, comparable to suspicious electronic mail senders, unfamiliar URLs, or sudden requests for private info.
- Conduct common consciousness campaigns, emphasizing the significance of vigilance and reporting any suspicious exercise.
- Implement Electronic mail Safety Measures
- To detect and stop spoofed emails, make the most of spam filters and electronic mail authentication protocols, comparable to SPF (Sender Coverage Framework) and DKIM (DomainKeys Recognized Mail).
- Allow electronic mail encryption to guard delicate info in transit.
- Deploy superior menace safety options to establish and block malicious attachments or hyperlinks.
- Strengthen Password Safety
- Encourage the usage of robust, distinctive passwords for all accounts.
- Implement multi-factor authentication (MFA) wherever doable so as to add an additional layer of safety.
- Repeatedly replace and alter passwords, notably after any suspected phishing incident.
- Confirm Web site Authenticity
- Prepare people to test for safe connections (HTTPS) and legitimate SSL certificates when visiting web sites.
- Encourage utilizing respected browser extensions or anti-phishing instruments to establish fraudulent web sites.
- Warning towards clicking on hyperlinks from unsolicited emails or unfamiliar sources.
- Allow Safety Software program
- Set up respected antivirus, anti-malware, and firewall software program on all units.
- Hold safety software program up to date to make sure safety towards the newest phishing threats.
- Carry out common system scans to detect and take away any potential malware.
- Foster a Tradition of Reporting
- Encourage people to report any suspected phishing emails or incidents promptly.
- Set up clear reporting procedures and supply accessible channels for reporting.
- Implement a swift response mechanism to research and mitigate reported incidents.
- Keep Knowledgeable and Up to date
- Hold abreast of the newest phishing developments, strategies, and vulnerabilities.
- Repeatedly replace software program, purposes, and working programs to patch any identified safety vulnerabilities.
- To remain knowledgeable about rising threats, subscribe to related safety alerts and trade information sources.
By diligently following this detailed prevention guidelines, people and organizations can considerably scale back the chance of falling sufferer to phishing assaults.
It’s essential to stay proactive, repeatedly consider and strengthen safety measures, and foster a security-conscious tradition to counter the ever-evolving phishing panorama.
Bear in mind, shutting down phishing assaults requires a multi-layered strategy that mixes expertise, schooling, and person consciousness. By working collectively, you’ll be able to fight this pervasive menace and safeguard your digital ecosystem.
Finest Phishing Assaults Prevention Instruments
- Electronic mail Safety Gateways: Electronic mail safety gateways scan incoming emails for suspicious content material, attachments, and URLs. They use varied strategies comparable to machine studying, heuristics, and blacklisting to establish and block phishing makes an attempt.
- Anti-Phishing Software program: Anti-phishing software program helps detect and block phishing web sites by analyzing URLs, web site repute, and content material. These instruments will be put in on internet browsers, working programs, or as browser extensions.
- Internet Filtering and Content material Filtering: Internet filtering instruments block entry to identified malicious web sites and limit customers from visiting probably harmful or unauthorized web sites. They’ll additionally filter out suspicious or malicious content material from internet pages.
- Multi-Issue Authentication (MFA): Implementing MFA provides an further layer of safety by requiring customers to supply a number of authentication elements, comparable to a password and a singular code despatched to their cell system, decreasing the effectiveness of stolen credentials.
- Safety Consciousness Coaching: Conducting common safety consciousness coaching for workers is essential. Coaching packages educate workers about phishing strategies, crimson flags to observe for, and finest practices for dealing with suspicious emails or hyperlinks.
- Internet Browser Safety Options: Fashionable internet browsers typically include built-in security measures that may assist shield towards phishing assaults. These options embody anti-phishing filters, warnings about probably dangerous web sites, and protected searching modes.
- DNS Filtering: DNS filtering options block entry to identified malicious domains by analyzing and filtering DNS queries. They might help forestall customers from accessing phishing web sites or downloading malicious content material.
- Safety Info and Occasion Administration (SIEM): SIEM instruments gather and analyze safety occasion knowledge from varied sources to detect and reply to safety incidents, together with phishing assaults. They’ll present real-time alerts and insights into suspicious actions.
- Endpoint Safety Software program: Endpoint safety options supply antivirus, anti-malware, and anti-phishing options to detect and block malicious information, hyperlinks, and attachments on endpoints comparable to laptops, desktops, and cell units.
- Incident Response and Reporting Instruments: Having incident response instruments in place allows organizations to reply to and mitigate phishing assaults rapidly. These instruments facilitate incident documentation, monitoring, and reporting for post-incident evaluation and enchancment.
How do you Prepare your Worker for Phishing Assaults?

- What’s Phishing: Educate workers on what phishing is and the way it works. Clarify that phishing entails fraudulent emails, messages, or web sites that trick people into revealing delicate info, comparable to login credentials or monetary particulars.
- Normal Phishing Methods: Describe widespread phishing strategies, comparable to electronic mail spoofing, misleading URLs, and social engineering. Clarify that attackers typically use social engineering techniques to govern people into taking actions that compromise safety.
- Figuring out Phishing Emails: Present pointers for figuring out phishing emails. Educate workers to search for indicators of suspicious emails, comparable to generic greetings, spelling or grammatical errors, requests for private info, pressing or threatening language, and unfamiliar senders.
- Suspicious Attachments and Hyperlinks: Instruct workers to be cautious with electronic mail attachments and hyperlinks. Advise towards opening attachments or clicking on hyperlinks in suspicious emails, particularly if they’re sudden or come from unknown sources.
- Verifying Requests: Encourage workers to confirm any uncommon or suspicious requests they obtain, particularly these associated to delicate info or monetary transactions. Present clear channels for workers to substantiate the legitimacy of requests, comparable to contacting the individual instantly or the related division.
- Safe Password Practices: Emphasize the significance of robust passwords and password hygiene. Instruct workers to create distinctive and sophisticated passwords, keep away from reusing passwords throughout totally different accounts, and allow two-factor authentication the place obtainable.
- Reporting Phishing Makes an attempt: Set up an easy course of for reporting phishing makes an attempt. Encourage workers to promptly report suspicious emails or incidents to the designated IT or safety staff. Please present them with the required contact info or reporting instruments.
- Safety Updates and Patching: Stress the significance of retaining software program, working programs, and purposes up to date with the newest safety patches. Clarify that attackers typically goal vulnerabilities in outdated software program.
- Common Coaching and Refreshers: Conduct common coaching periods and refreshers to bolster safety consciousness. Present real-life examples of phishing emails and encourage workers to actively take part in simulated phishing workout routines to check their skill to establish and reply to phishing makes an attempt.
- Ongoing Communication: Keep ongoing communication about phishing threats and finest practices by varied channels, comparable to electronic mail newsletters, inner messaging platforms, and bulletin boards. Share real-world examples of phishing assaults to maintain workers knowledgeable and vigilant.
Conclusion
The prevention guidelines supplies a complete and detailed strategy to shutting down phishing assaults.
By implementing these preventive measures, people and organizations can considerably scale back their susceptibility to phishing makes an attempt and shield helpful info and belongings.
By elevating consciousness, implementing electronic mail safety measures, strengthening password safety, verifying web site authenticity, enabling safety software program, fostering a tradition of reporting, and staying knowledgeable and up to date, we are able to set up a sturdy protection towards phishing assaults.
Bear in mind, combating phishing assaults requires a collective effort that entails steady schooling, proactive safety measures, and vigilant person consciousness.
By following this prevention guidelines and staying proactive within the face of evolving threats, we are able to create a safer digital setting and shield ourselves from the dangerous penalties of phishing assaults.
Collectively, let’s shut down phishing assaults and make sure the safety and integrity of our digital interactions.

