
Palo Alto Networks has lastly launched safety updates for 2 actively exploited zero-day vulnerabilities in its Subsequent-Technology Firewalls (NGFW).
The primary flaw, tracked as CVE-2024-0012, is an authentication bypass discovered within the PAN-OS administration net interface that distant attackers can exploit to achieve administrator privileges with out requiring authentication or person interplay.
The second (CVE-2024-9474) is a PAN-OS privilege escalation safety flaw that enables malicious PAN-OS directors to carry out actions on the firewall with root privileges.
Whereas CVE-2024-9474 was disclosed right now, the corporate first warned clients on November 8 to limit entry to their next-generation firewalls due to a possible RCE flaw tagged final Friday as CVE-2024-0012.
“Palo Alto Networks noticed risk exercise that exploits this vulnerability in opposition to a restricted variety of administration net interfaces which can be uncovered to web visitors coming from outdoors the community,” the corporate warned right now relating to each zero-days.
“Palo Alto Networks has actively monitored and labored with clients to establish and additional reduce the very small variety of PAN-OS gadgets with administration net interfaces uncovered to the Web or different untrusted networks, ” it added in a separate report offering indicators of compromise for ongoing assaults concentrating on the failings.
Whereas the corporate says these zero-days influence solely a “very small quantity” of firewalls, risk monitoring platform Shadowserver reported on Friday that it is monitoring greater than 8,700 uncovered PAN-OS administration interfaces.
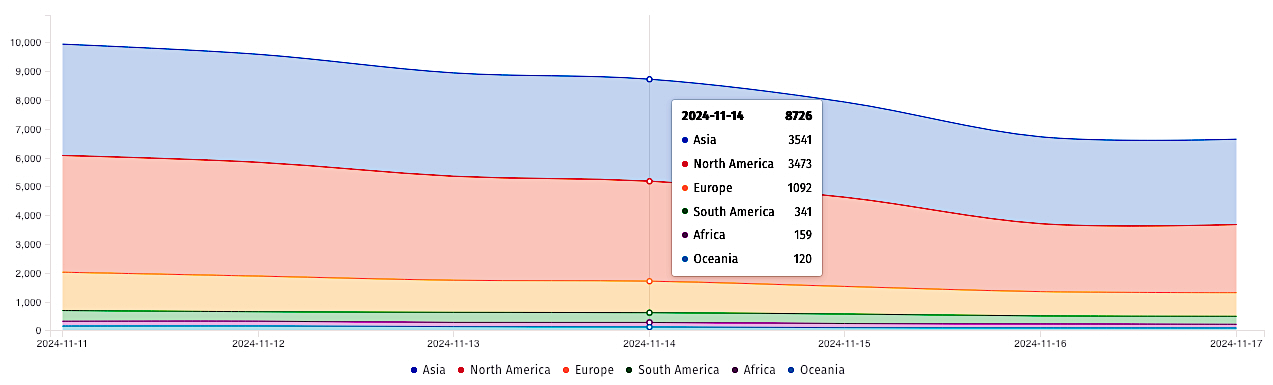
Macnica risk researcher Yutaka Sejiyama additionally advised BleepingComputer that he discovered over 11,000 IP addresses operating Palo Alto PAN-OS administration interfaces uncovered on-line utilizing Shodan. In keeping with Shodan, essentially the most susceptible gadgets are in america, adopted by India, Mexico, Thailand, and Indonesia.
The U.S. cybersecurity company added the CVE-2024-0012 and CVE-2024-9474 vulnerabilities to its Identified Exploited Vulnerabilities Catalog and ordered federal businesses to patch their techniques inside three weeks by December 9.
In early November, CISA additionally warned of ongoing assaults exploiting a important lacking authentication vulnerability (CVE-2024-5910) within the Palo Alto Networks Expedition firewall configuration migration instrument, a flaw patched in July that risk actors can remotely exploit it to reset utility admin credentials on Web-exposed Expedition servers.
“These kind of vulnerabilities are frequent assault vectors for malicious cyber actors and pose vital dangers to the federal enterprise,” CISA warns.
