
Join day by day information updates from CleanTechnica on e mail. Or comply with us on Google Information!
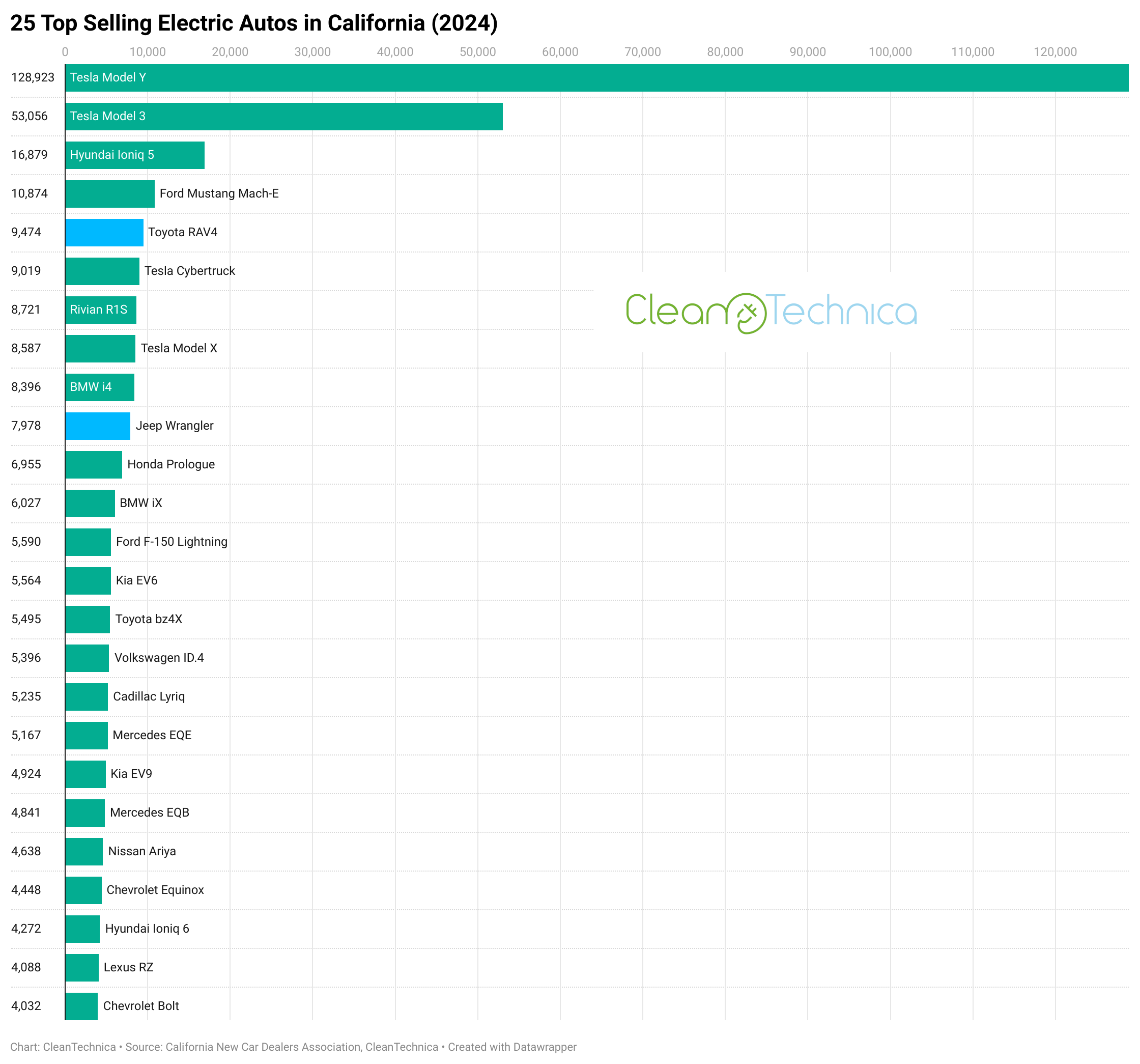
Humorous factor — I wrote about California’s total electrical car market and stats in addition to market leaders, and I wrote about electrical autos topping the charts in varied car courses, however I uncared for to provide and share in all probability the obvious chart of all from this market. That may be a chart on the 25 high promoting electrical car fashions.
A few fast notes right here: 1) The California New Automotive Sellers Affiliation (CNCDA) consists of full electrics (ZEVs) and plugin hybrids (PHEVs) on this rating, in order that’s what I’m together with on this case (I may simply exclude the PHEVs, in fact, however I really do prefer to see how they examine, so I’m together with them right here), and a couple of) Tesla’s high two fashions are to date above different fashions in gross sales, particularly the Tesla Mannequin Y, that it makes the chart much less attention-grabbing and enjoyable in relation to these different fashions, however that’s the truth we’re in. Hopefully different electrical fashions can scale up far more in 2025….
Clearly, Tesla’s high two fashions dominate. The primary shock is that the Hyundai IONIQ 5 is definitely setting itself aside in California in third. Not dangerous. Now are you able to double or triple that, Hyundai?
The Ford Mustang Mach-E held robust for 4th, the one different mannequin above 10,000 gross sales, however, once more, it could be good to see Ford double, triple, or quadruple these gross sales. We’ll see what occurs in 2025 as Tesla continues to endure extreme model injury from Elon Musk.
A pleasant shock is that solely two plugin hybrid fashions ranked within the high 25. The Toyota Prius Prime takes fifth place, however what would a completely electrical model of the extraordinarily in style mannequin do in gross sales? Additionally, how a lot is Toyota really making an attempt to promote its plugin fashions in California, versus doing the naked minimal? One has to surprise.
The, humorous sufficient, the Tesla Cybertruck and Rivian R1S are proper subsequent to one another, and the Tesla Mannequin X proper on their tail. I ponder if Rivian will shoot above the 2 largest Tesla fashions this 12 months?
Another ideas or questions from this California EV gross sales rating?
Whether or not you may have solar energy or not, please full our newest solar energy survey.
Chip in a number of {dollars} a month to assist help unbiased cleantech protection that helps to speed up the cleantech revolution!
Have a tip for CleanTechnica? Wish to promote? Wish to recommend a visitor for our CleanTech Speak podcast? Contact us right here.
Join our day by day e-newsletter for 15 new cleantech tales a day. Or join our weekly one if day by day is just too frequent.
CleanTechnica makes use of affiliate hyperlinks. See our coverage right here.
CleanTechnica’s Remark Coverage









.webp)


