In 2017, a malicious actor exploited the alerts in Dallas’s emergency siren system and set off alarms for over 90 minutes. These kind of assaults can have an effect on units that use radio frequency (RF) expertise, from sensible safety methods to plane. RF additionally performs a essential position in lots of army methods, akin to navigation, radar, and communication methods. Frequent DoD use circumstances embrace satellite tv for pc communication (SATCOM), radio, radar, or tactical information hyperlinks that assist coordinate troop actions, sign place data a couple of goal, or assist keep communication between plane and drones. A current report indicated the DoD is prone to potential RF assault vectors, indicating the necessity to higher perceive and stop vulnerabilities.
On this RF 101 information, we discover among the fundamentals of radio frequency communication, delve into the generalities of protocols and gadget interactions, talk about frequent RF instruments, and uncover methods malicious actors can assault methods. We summarize the fundamentals of RF expertise and the dangers related to it and talk about how the SEI helps to safe wi-fi communications.
RF Fundamentals
The flexibility of RF waves to journey via completely different mediums allows long-distance communication with out the necessity for bodily connections. RF is key to trendy communication methods, which allow all the things from tv, radio broadcasts, mobile phone alerts, and WiFi connections. RF additionally performs an important position in house domains, akin to satellite tv for pc communications to floor stations, which allow transmissions of telemetry information, GPS, and different alerts. The electromagnetic waves themselves can range in frequency and sometimes vary from 20 kilohertz (kHz) to round 300 gigahertz (GHz). This radio spectrum might be divided into bands starting from very low frequency (VLF) to extraordinarily excessive frequency (EHF) as seen under.

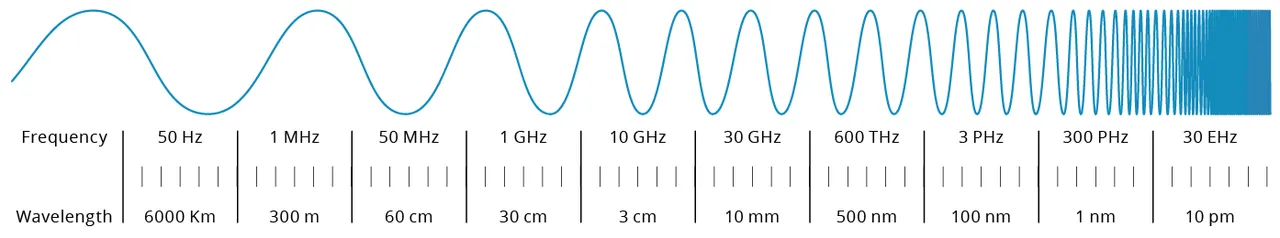
Determine 1: Radio frequency spectrum and wavelengths
Modulation is the method of various a service sign to encode information after which demodulating that obtained sign from one other gadget to decode information. Modulation strategies decide how data is transmitted over RF waves, affecting the effectivity and high quality of communication.

Determine 2: The modulation and demodulation processes
What Are Protocols and RF Modules?
RF modules are small digital units which might be used to transmit and obtain radio alerts between two units which might be bodily separated. Transmitters are liable for transmitting radio waves—service alerts—that carry analog or digital data, and receivers obtain the radio waves and recuperate the data from the service. The general sign is damaged down into the service frequency and modulations that encode analog or digital data. There are completely different ways in which the data might be carried: Frequent analog modulations are amplitude modulation (AM) and frequency modulation (FM). AM modulates a excessive frequency service with a decrease frequency sign by adjusting the amplitude of the service. FM modulates by making comparatively small changes to the frequency of the service. These two strategies characterize the sorts of RF alerts on the acquainted AM and FM radio bands. Frequent digital modulations, constructing on AM and FM, embrace amplitude-shift keying (ASK) and frequency-shift keying (FSK).
Inside a system, transmitters and receivers might be packaged collectively as transceivers, which carry out each capabilities. Moreover, system on a chip (SoC) configurations embrace transceivers together with microcontrollers that enable protocol administration akin to information packetization.
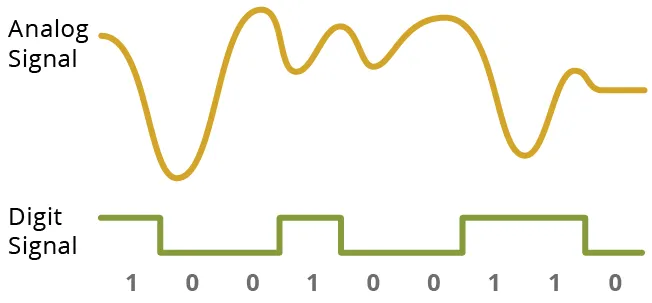
Determine 3: Sign varieties
Communication protocols are units of guidelines that dictate how units work together and trade data. They guarantee information is transmitted in a constant format, permitting units from completely different producers to speak effectively so long as they respect the protocol. There are a lot of completely different sorts of protocols in use. Some steadily used wi-fi protocols embrace:
- ZigBee: This low-power wi-fi mesh community protocol is underneath the IEEE 802.15.4 radio specification. It operates on the 868 megahertz (MHz) radio band in Europe, the 915 MHz radio band within the Americas, and globally at 2.4 GHz. It could transmit over a distance of as much as 100 meters (line of sight) and may obtain uncooked information throughput charges as much as 500kbps. Its modulation approach known as direct-sequence unfold spectrum (DSSS), and it operates on 16 mounted channels which might be 5 MHz aside within the 2.5 GHz band. It’s primarily utilized in residence automation, sensible power, wi-fi sensing and industrial automation.

Determine 4: ZigBee channels
- Wi-Fi: That is the acquainted wi-fi IEEE 802.11-based protocol that operates within the 2.4 GHz ISM band. It additionally makes use of DSSS modulation within the 2.4 GHz vary, with 14 channels spaced 5 MHz aside. In america, channels 1 via 11 are generally used, particularly channels 1, 6 and 11, that are the one non-overlapping channels. Wi-Fi is utilized in houses, metropolis infrastructures, geolocation, industrial environments, and IoT purposes.
- Bluetooth low power: That is the acquainted low-power protocol used for on various units for shut proximity communication. It operates within the 2.4 GHz ISM band. Frequency-hopping unfold spectrum (FHSS) is the modulation approach used, and its band is split into 40 2-MHz channels. It’s utilized in sensible residence units, healthcare purposes, location-based providers, and extra.
How Do Units Talk with One One other?
Units talk by changing information into electrical alerts, that are then modulated onto a service wave at a selected frequency. For instance, ZigBee, as famous above, operates on 16 channels within the 2.4 GHz vary. As seen in Determine 4, two ZigBee radios speaking on channel 19 can be speaking on the frequency of 2445 MHz.
Antennas play a vital position in RF since they’re liable for radiating alerts into the air and receiving incoming alerts. Antenna designs are decided by the character of the communication utility, the meant frequencies and modulation technique, together with high quality elements akin to vary, bandwidth, and working setting.
Some configurations are designed to assist a number of communications concurrently, or multiplexing. Frequency division multiplexing separates alerts into completely different channels to transmit a number of alerts without delay. Time division multiplexing schemes assist handle entry to a channel to keep away from colliding transmissions.
RF Assaults
RF assaults exploit vulnerabilities to intercept, disrupt, or manipulate methods and related protocols. The implications of RF assaults can vary from information breaches and lack of confidentiality to denial of service and disruption of essential communications. An instance that illustrates RF safety dangers is railroad and practice jacking, the place the current Poland railway assault stopped 20 trains in 2023. As wi-fi expertise grows, so do the assault area and threats.
What Are Frequent Kinds of RF Assaults?
A number of frequent RF assault vectors exploit weaknesses in wi-fi communications. Frequent vectors embrace the next:
- Eavesdropping entails intercepting and listening to wi-fi communications with out authorization. This may enable a malicious actor to achieve entry to delicate data akin to passwords, authentication processes, private data, or import system processes. Attackers can make the most of software-defined radios (SDRs) to seize and decode transmitted information in a versatile method, enabling attackers to quickly adapt as they be taught extra about frequencies, modulation strategies, and protocols.
- Replay assaults, that are analogous to man-in-the-middle (MITM) assaults in cybersecurity, happen when an attacker captures legitimate transmissions after which retransmits them to impersonate a authentic gadget or person. These assaults can bypass authentication or achieve unauthorized entry to methods. For instance, a malicious actor may sniff the transmissions that carry the code from a sensible lock to unlock/lock a door or sniff and replay the rolling code from a automobile’s key fob to acquire entrance to a automotive.
- Relay assaults improve a legitimate radio sign and use it to entry a legitimate goal. In contrast to a replay assault, which captures and resends the sign, a relay assault permits a sign to journey farther and be used at longer distances. Good fobs and keys are prone to this kind of assault.
- Jamming is a denial-of-service assault the place the attacker transmits radio alerts on the identical frequency because the focused communication, successfully disrupting or blocking the authentic alerts. This may forestall units from speaking, which may result in service outages or operational disruptions.
RF Vulnerabilities
On this part, we analyze current examples of notable RF assaults which were written about within the public press.
Replay Assault
Keyless entry methods have modified how folks use automotive keys and entry safe areas, changing previous bodily keys with key fobs. Nevertheless, these methods are susceptible to RF assaults. Automobile key fobs use RF alerts to ship a code to autos, permitting them to be unlocked and even began. From the late Eighties to early 2000s, keyless entry methods emerged as a premium on a whole lot of automobiles. Like a storage door opener, a button can be pressed on the keyless entry gadget, transmitting an RF sign to the automotive, and a code would enable the automotive to be locked or unlocked. With little-to-no safety included of their preliminary design, early keyless entry methods have been susceptible to cloning and replay assaults. Because the expertise grew to become extra plentiful, safety elevated, including primary encryption to keyless entry units and options such because the rolling key technique. Within the rolling key technique, a brand new code is generated every time a button is pressed on the important thing fob. With the introduction of rolling keys, primary replay assaults not labored as a result of the captured and replayed code didn’t match the newly generated code.
In response to this stronger protection, two new forms of replay assaults emerged: the RollBack assault and the RollJam assault. RollBack captures two alerts: when a secret is pressed, the primary sign is jammed, and the second sign is allowed. The primary sign is then replayed, after which inside 5 seconds, the second sign is replayed to permit entry. Just like the RollBack assault, the RollJam assault captures two alerts. In contrast to RollBack, each alerts one and two are jammed, after which sign one is replayed shortly, permitting the proprietor entry to the automotive. Then the second sign is replayed later by the attacker.
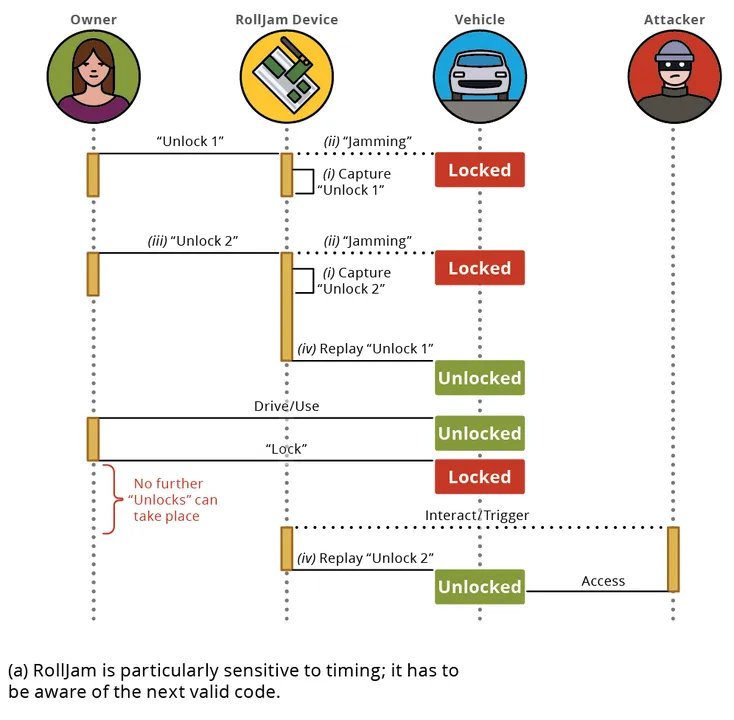
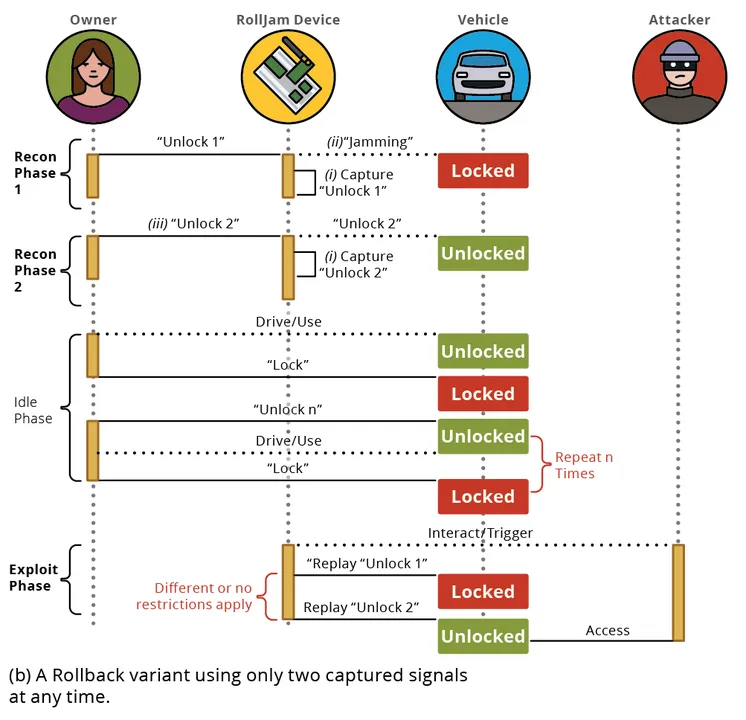
Determine 5: Illustrations of RollJam and RollBack assaults
Automobile theft is a well-liked use of replay assault. Nevertheless, residence automation methods may also be victims of some of these assaults. RF doorbell alerts might be cloned and replayed, as proven on this demonstration.
Relay Assault
Keyless entry methods at the moment are frequent options on most automobiles, and a brand new premium function has emerged. With keyless automotive fobs, a sign from the important thing fob is all the time transmitting, and the proprietor doesn’t have to hit a button to unlock the automotive. Just like the replay assault, relay assaults use a tool to seize a radio sign. As a substitute of copying the sign, the gadget boosts the sign to a second gadget to make it look like a key fob is close to the automotive. This assault often requires two folks. The primary thief stands near the automotive, whereas the second thief is close to the home making an attempt to pay attention for the always-transmitted sign from the important thing fob. As soon as the second thief can get the sign from the important thing fob, they replay that sign to the primary thief. As soon as the primary thief is within the automotive, the second thief will relay one other sign to the primary thief, who’s now in a position to begin the automotive.
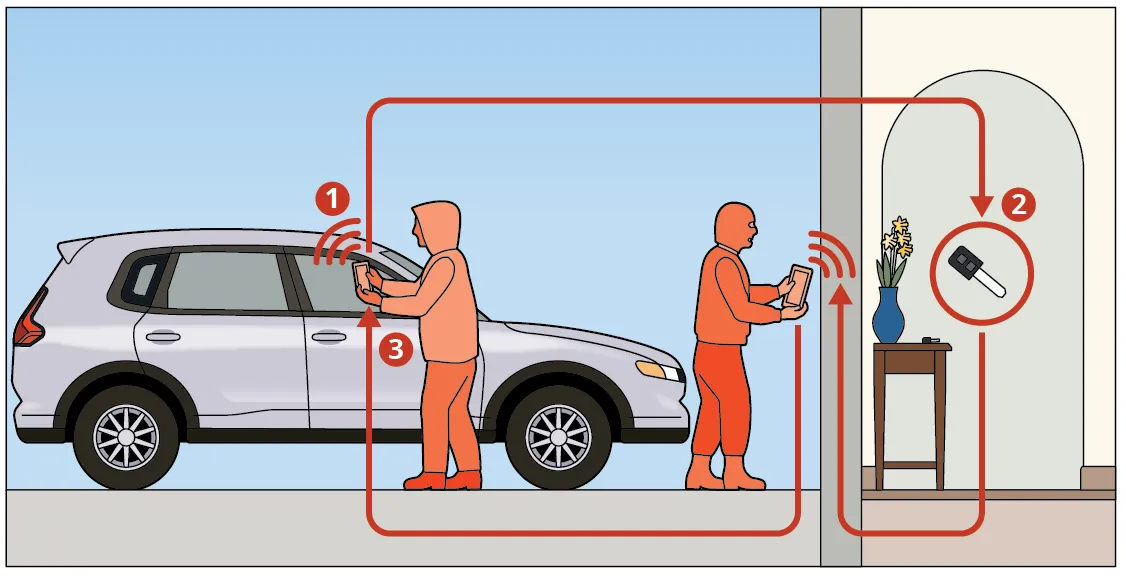
Determine 6: An instance of a relay assault
Compounding the problem, all communication alerts that use radio frequency should register with the Federal Communication Fee (FCC). Key fobs have an FCC ID, which tells the frequency used. There are industrial instruments accessible that enable an attacker to make use of the ID to set the frequency on their gadget, simplifying the method since they don’t have to make use of different instruments to scan RF alerts and decide the frequency.
Affiliation Flood Assault
In an affiliation flood assault, an attacker exploits the method by which a brand new ZigBee node joins a community. In a ZigBee community, there’s a coordinator (grasp of the community), a router, and endpoints. The assault begins when a malicious actor replicates the becoming a member of procedures, the place a brand new node sends a beacon request to the coordinator of the community, adopted by an affiliation request. By flooding the coordinator with quite a few pretend requests, the attacker can overwhelm the community. This permits the malicious actor to achieve unauthorized entry in a community of residence or workplace units to delicate information, management units, or simply typically trigger disruptions to the ZigBee community.
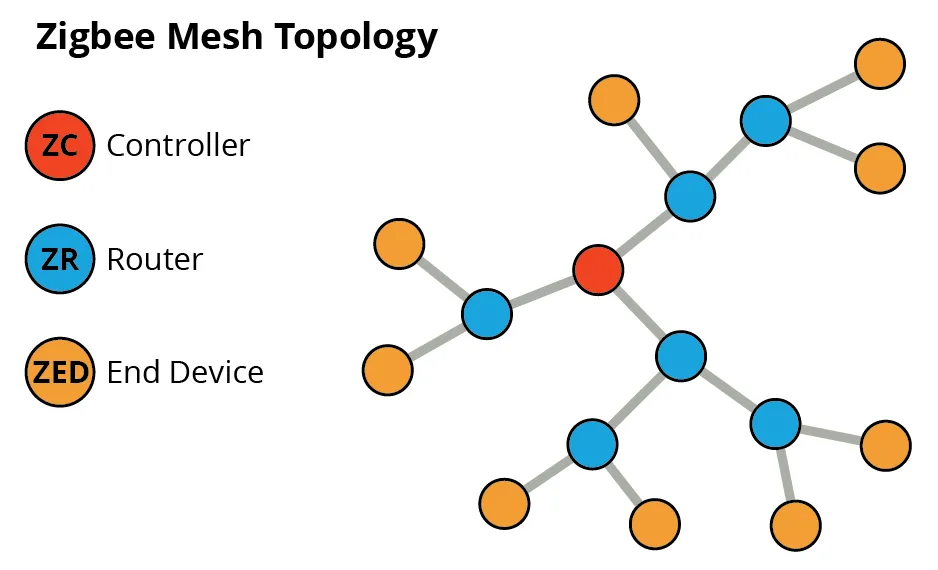
Determine 7: The ZigBee mesh topology
RF Vulnerabilities in Protection Purposes
RF expertise is closely utilized in protection purposes since superior radio expertise is used to hold out operations. Wi-fi communications have performed an integral position in tactical missions and common warfare and protection operations. Safe alerts are used to guard voice and information communications throughout operations. For instance, Single Channel Floor and Airborne Radio Techniques (SINCGARS) are army methods that present voice and information to command and management operations. There are military-specific GPS alerts which might be designed to withstand jamming and assist management the operational setting. Spectrum utilization within the army house is an important a part of trendy army operations that assist assist coordination and administration. Whether or not offering voice, information, or cell ad-hoc networking capabilities to warfighters, RF helps the monitoring of kit or autos or coordinating items with plane and drones. It’s a vital software for battle planning.
Spoofing and Jamming in GPS and Radar Techniques
GPS alerts, essential for navigation and sustaining dependable positioning information for operations, are an integral part of army operations. Nevertheless, there was an increase of GPS assaults inside the previous few years, as these methods might be spoofed or jammed by adversaries. Spoofing entails creating counterfeit alerts that may deceive receivers, akin to giving an incorrect location. GPS and radar methods are prone to affiliation flood assaults, making the whole community consider there are extra legitimate nodes then there actually are. The confusion created can be utilized to mislead drones or unmanned aerial autos (UAV) to a mistaken vacation spot.
GPS spoofing in army operations is conceptually just like the automotive key fob assault described above. In a GPS spoofing assault, an adversary may use ground-based methods to broadcast false GPS alerts that deceive army GPS receivers, main them to navigate to incorrect coordinates. Simply as a automotive might be tricked into accepting a replayed key fob sign, army methods counting on GPS might be misled by a replayed or pretend sign. Equally, an adversary may use an RF jamming gadget to intrude with a radar system, stopping it from detecting incoming plane or deceptive radar operators into pondering an incoming plane is coming from a unique location.
In these circumstances, the vulnerability lies within the transmission of RF alerts with out correct safeguards in opposition to interception, replay, or manipulation. Additional analysis into safeguarding and securing these methods in opposition to dangers with extra anti-jamming strategies, superior encryptions, or different pathways will assist guarantee nationwide safety.
Work with the SEI
Understanding RF vulnerabilities and dangers is step one in studying the right way to mitigate them. Right here on the SEI, we’re creating instruments and processes to securely harness the facility of RF. For instance, we’re creating machine studying (ML) capabilities to foretell RF sign energy extra shortly than a physics-based mannequin. This elevated velocity can allow purposes at present not possible, akin to large-scale threat evaluation with uncertainty quantification, design optimization over very massive determination areas, and extra lifelike real-time war-gaming. Moreover, the SEI is working to modernize current processes, information, and digital infrastructure by creating software program instruments and information pipelines that assist RF spectrum operations. If you’re fascinated with studying extra about this work or collaborating with the SEI, please contact us.










