Programming outsourcing is a way of rushing up improvement and price discount by outsourcing to third-party specialists. All through this tutorial, we’ll contemplate giant outsourcing fashions, how to decide on a dependable outsourcing accomplice, develop a improvement course of, and handle mission necessities for profitable IT tasks.
What Is Programming Outsourcing?
Outsourcing programming is the delegation of software program improvement work to third-party professionals or corporations. This technique allows firms to focus on central objectives, lower your expenses, and acquire specialised abilities not current throughout the agency.
At present, increasingly more firms are outsourcing programming with the intention to launch merchandise sooner, cowl the scarcity of specialists, and handle their groups flexibly. It often works like this: you formulate what you want — objectives, targets, deadlines — and the technical half is taken over by an exterior contractor. He develops, exams, and implements the answer, when you keep within the loop and management the important thing phases.
Programming Outsourcing Fashions
There are a number of approaches to aligning with an outsourcing firm, and all of it relies on your objectives, deadlines, and inside workforce.
Devoted Groups
Some of the well-liked choices is a devoted workforce. On this case, your outsourcing accomplice selects builders for you who will work completely in your mission.
You might have a workforce, however you haven’t invested in hiring, HR, and infrastructure. In case you’re planning a protracted product improvement effort and want the workforce to be all the time on and deeply engaged, this format is the way in which to go.

Employees Augmentation
This selection is appropriate in the event you urgently want one or two specialists to cowl bottlenecks in your present mission. You merely add the fitting folks to your inside workforce with out spending months on hiring.
They’re utterly below your management, combine into your present course of, and assist transfer the mission ahead. That is particularly helpful whenever you lack particular technical abilities or time.
Mission-based Outsourcing
And the third, most “contactless” possibility is the mission mannequin. You give you an concept and a prepared set of necessities, and the contractor takes care of the remainder of the method — planning, improvement, administration, and high quality management.
You might have a completed end result below the agreed time and with low involvement. This setup is appropriate in the event you should not have an inside technical workforce or should not inclined to spend on executing the mission in-house.
Kinds of Programming Outsourcing
Outsourcing is commonly categorized by location into three varieties: onshore, nearshore, and offshore.
Onshore outsourcing implies cooperation with a workforce situated in the identical nation because the buyer. This strategy ensures most ease of interplay: widespread language, related enterprise pondering, no important time distinction, and facilitated authorized clearance. This mannequin has been used often when the excessive pace of communication and a deep understanding of the native context are vital, though it comes at the next price.
Nearshore outsourcing is the switch of improvement to firms from neighboring nations or areas inside a detailed time zone. For instance, for European firms nearshore could imply cooperation with groups from Jap Europe.
This mannequin is advantageous as a result of it permits you to cut back prices in comparison with onshore whereas minimizing the issues related to time zones and cultural variations. Simplified logistics and the flexibility to prepare enterprise journeys additionally make nearshore a handy possibility.
Offshore outsourcing entails working with groups situated in distant nations, typically in different time zones and areas. The principle purpose for this mannequin is often a big discount in the price of improvement and entry to numerous certified specialists.
Nevertheless, this mannequin requires extra cautious mission administration, clear tasking, clear communication processes, and consideration of potential cultural variations. Correctly organized, offshore will be an efficient option to scale improvement with out severe compromises in high quality.
Selecting the Proper Outsourcing Mannequin for Your Enterprise
For outsourcing to essentially be helpful, it’s vital to decide on the fitting geographic partnership mannequin based mostly on the mission objectives, finances, timeline, and the extent of management you need to retain.

Onshore outsourcing is appropriate for individuals who worth pace of interplay, full cultural alignment, and authorized transparency. It’s a sensible choice for tasks that require shut every day contact and fast decision-making, regardless of the upper price of the providers.
The Nearshore mannequin is good for firms that don’t need to spend some huge cash however nonetheless need to keep comfy with communication. If it’s important so that you can work in an analogous time zone, communicate the identical language, and keep away from difficulties with mentality, this mannequin is good.
Offshore outsourcing is commonly chosen due to its reasonably priced price and an enormous choice of certified IT specialists world wide. That is particularly handy when you might want to shortly construct up your workforce or launch a large-scale mission with out overloading inside assets.
Nevertheless, this strategy emphasizes the necessity to not let issues go to waste: you must take into consideration how administration will likely be organized prematurely, select a confirmed accomplice, and construct clear, common communication.
Key Advantages of Outsourcing Programming
At present, outsourcing programming isn’t just a means to economize. It’s a full-fledged technique that helps companies scale, keep agile, and launch digital merchandise shortly.
In accordance with Statista, IT-related providers — together with expertise consulting, managed providers, and workers augmentation — account for over 60% of all world skilled outsourcing gross sales. This clearly exhibits that software program outsourcing isn’t a brief repair — it’s a broadly adopted and sustainable enterprise technique.
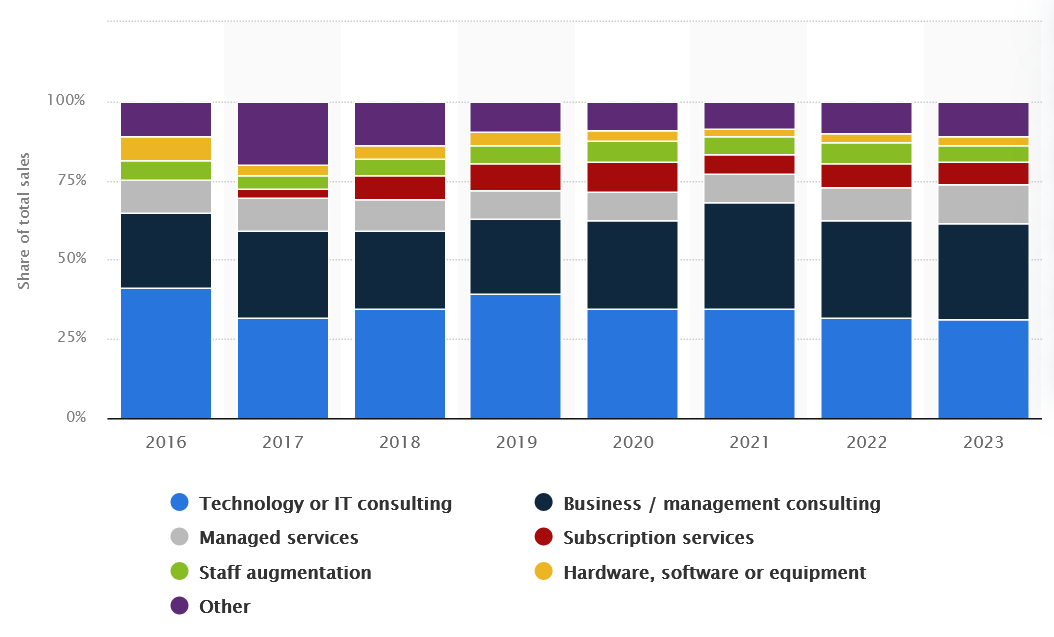
Sort of labor offered by skilled providers organizations worldwide from 2016 to 2023, Statista
Value Discount
Growing in areas with decrease labor prices can prevent as much as 40-60% of your finances with out sacrificing high quality. You don’t spend cash on hiring, salaries, taxes, and jobs — all that is left to the contractor. That is particularly vital for startups and firms that need to optimize their IT finances.
Entry to World Expertise
Outsourcing opens up entry to builders everywhere in the world. You possibly can rent the very best expertise from Poland, India, or Latin America with out being restricted to the native market. That is particularly priceless in the event you want specialised abilities which are exhausting to seek out regionally.
Scalability and Flexibility
While you work with an exterior workforce, you’ll be able to shortly enhance assets or, quite the opposite, cut back them with out forms and dangers for the enterprise. That is handy if a mission is rising shortly or requires short-term reinforcement. You merely choose the fitting workforce configuration and maintain shifting ahead.
Software program Improvement Outsourcing vs. In-Home
An inside workforce means management, company tradition, and stability. Nevertheless it requires a number of funding: in hiring, onboarding, coaching, salaries, and gear. And most significantly, it takes time. It could possibly take months to construct a robust workforce from scratch.
Outsourcing, alternatively, permits you to begin shortly. You discover a accomplice, formulate duties, and in a number of weeks you can begin improvement. This lowers the entry barrier and is very related when deadlines are tight or budgets are restricted.
After all, every thing relies on the duties. Generally you’ll be able to’t do with out an in-house workforce, particularly if the product is the core of the enterprise. However for startups, MVPs, or mission assist, outsourcing will be rather more affordable.
Under is a comparative desk that may enable you to to obviously assess the variations between in-house improvement and outsourcing providers.
| Standards |
In-Home improvement |
Outsourcing providers |
| Begin pace |
Low — takes time to recruit and onboarding |
Excessive — the workforce is offered virtually instantly |
| Management |
Most management over processes |
Management is restricted, and requires customization of processes |
| Value |
Excessive — salaries, taxes, gear |
Under — solely the work on the mission is paid |
| Scaling flexibility |
Restricted by inside assets |
Simply scalable via exterior instructions |
| In-depth product data |
Excessive — the workforce is deeply immersed within the enterprise and product |
Restricted – requires effort and time to enter |
| Cultural integration |
Full — workers are a part of the company surroundings |
Partial — potential distinction in strategy and mentality |
| Sustainability and stability |
Depends upon inside technique and worker retention |
Depends upon the reliability of the accomplice and the phrases of the contract |
| Good for |
Key, long-term, and strategically vital merchandise |
MVP, pilot tasks, technical assist, fast improvement |
Software program Improvement Mission Outsourcing vs. In-Home
Well-known Corporations That Use Outsourcing Improvement Providers
In case you thought outsourcing was the area of startups, it’s time to alter your perceptions. Massive firms have been utilizing exterior groups for years and are getting highly effective outcomes.
For instance, Slack developed its interface early on with the assistance of an exterior company. GitHub, Skype, and Alibaba are all examples of manufacturers which have scaled exactly via outsourcing. Even giants like Google and Microsoft outsource particular person elements on occasion, be it assist, testing, or cellular improvement.
This as soon as once more confirms that outsourcing programming is just not a compromise, however a aware alternative that even market leaders make.
Indicators You Ought to Outsource Programming Providers
If you’re a enterprise proprietor or a mission supervisor, you commonly face the query: must you develop tasks in-house or entrust them to an exterior workforce? Follow exhibits that outsourcing turns into the optimum resolution in a number of key conditions.
Lack of In-house Experience
Think about: you’re launching a brand new product, however your builders lack expertise with the mandatory applied sciences. Hiring new specialists is pricey and time-consuming, and coaching present ones is dangerous and time-consuming.

On this case, outsourcing provides you instantaneous entry to professionals with the fitting experience. For instance, in the event you want a blockchain developer for a fintech mission or a machine studying specialist, it’s simpler and extra worthwhile to have interaction a ready-made workforce than to construct one from scratch.
Tight Deadlines
The shopper requires the product to be launched by a particular date? Traders are ready for a demo model for a presentation? The in-house workforce bodily can’t get every thing accomplished in time? On this case, outsourcing is an insurance coverage coverage in opposition to missed deadlines. Exterior builders can bounce into the mission instantly and work at an accelerated tempo whereas your workforce focuses on core duties.
Price range Constraints
Open your individual improvement workplace overseas or rent a distant workforce via outsourcing? The second possibility can save as much as 60% of your finances. You solely pay for the precise work — no bills for workplace hire, gear, worker advantages, or taxes.
On the identical time, you get the identical stage of high quality — many outsourcing firms observe worldwide requirements (ISO, CMMI) and use superior improvement methodologies.
Outsource Programming Providers for Startups and Enterprises
Younger firms typically can’t afford costly specialists. Outsourcing provides them entry to senior-level software program builders. What’s extra, an exterior workforce can’t solely construct the product but additionally advise on the tech stack, assist with product structure, and even assist investor negotiations.
When you might want to launch a pilot mission, take a look at a speculation, or cowl a brief expertise hole, outsourcing is the right resolution. You don’t decide to long-term contracts however nonetheless get the outcomes. Many firms go for a hybrid mannequin: they maintain key builders in-house whereas outsourcing routine or extremely specialised duties.
Learn how to Select the Proper Outsourcing Accomplice
Choosing the proper outsourcing accomplice is without doubt one of the key elements of mission success. The flawed alternative can result in missed deadlines, finances overruns, and poor product high quality. Under are elements to contemplate which are value contemplating when making your alternative.
Technical Experience
Be certain your potential accomplice has expertise with the applied sciences and kinds of tasks you want. Overview their portfolio, case research, and the tech stack they use. What issues isn’t simply data of programming languages, but additionally a strong understanding of structure, CI/CD processes, safety, and scalability.
Communication and Collaboration
Efficient communication is essential to profitable collaboration. Take note of how the workforce responds to your requests, how clearly they impart their concepts, and the way they manage their workflows. It’s finest to decide on companions who observe agile methodologies like Scrum or Kanban and are open to clear reporting.
Time Zone and Cultural Compatibility
Time zone variations can both be a problem or a bonus. It’s splendid when working hours overlap a minimum of partially — that means, you’ll be able to schedule real-time calls.
Cultural compatibility additionally issues: shared views on enterprise ethics, problem-solving approaches, accountability, and engagement could make an enormous distinction in how easily the collaboration goes.
Significance of Relationships in Outsourcing
Profitable outsourcing isn’t nearly expertise — it’s about relationships. It’s vital to construct a partnership, not simply rent somebody to “do the job.”
A dependable vendor will take the initiative, flag potential dangers early, and keep targeted on delivering actual outcomes. Shared objectives, common suggestions, and mutual belief are the inspiration of long-term collaboration.
Outsourcing Cowl: What Ought to Be Included in Contracts
A contract isn’t only a formality — it’s a software that protects the pursuits of each events. An outsourcing settlement ought to clearly define the next:
- Scope of Work – an in depth description of duties, performance, and mission phases.
- Timeline & Milestones – what must be delivered and when. This helps observe progress.
- Price range and Fee Mannequin – whether or not it’s a set price, hourly price, or milestone-based (T&M, Mounted Worth, Devoted Group).
- Change Requests – how adjustments will likely be documented and paid for.
- Duties – who’s accountable for what, together with code high quality, availability, testing, and bug fixes.
- Mental Property – the shopper should obtain full rights to the ultimate product and supply code.
- NDA, Knowledge Safety – particularly vital when working with delicate information.
Programming Providers You Can Outsource
Outsourcing improvement is a option to delegate technical duties to a dependable workforce, saving time and finances with out compromising on high quality. Under, we’ll have a look at essentially the most generally outsourced providers and the way they profit companies.

Internet and Cellular Improvement
If you might want to construct an internet site or cellular app, you’ll be able to absolutely entrust the duty to an exterior workforce. They’ll deal with every thing — from design and improvement to testing and launch.
Internet tasks usually use fashionable applied sciences like React or Vue, whereas cellular apps typically depend on cross-platform options corresponding to Flutter and React Native. That is particularly handy if you wish to shortly launch an MVP, enhance buyer expertise, or adapt your product for telephones and tablets.
Backend and API Improvement
The backend is what works behind the scenes of any digital product — dealing with information processing, utility logic, and connections to databases and exterior providers.
In case your workforce lacks the fitting specialists or just doesn’t have the time, bringing in exterior builders is commonly simpler and more cost effective. They may also help arrange a dependable technical basis that’s scalable and ensures your product runs easily.
Legacy System Modernization
Many firms nonetheless depend on outdated software program that’s troublesome to keep up and improve. Outsourcing may also help fastidiously transition these programs to fashionable applied sciences with out placing the enterprise in danger. This may contain migrating to the cloud, bettering the person interface, or rewriting the code to make the product sooner, safer, and simpler to scale.
Coding Outsourcing: Scope and Finest Practices
Generally the in-house workforce simply doesn’t have sufficient fingers — perhaps you want an additional developer, a DevOps engineer, or a tester. On this case, you’ll be able to herald exterior specialists for a set interval and particular duties.
The bottom line is to agree prematurely on the scope of labor, collaboration format, and the way progress will likely be tracked. This strategy helps maintain the mission shifting with out the additional prices and delays of full-time hiring.
Challenges and Dangers of Programming Outsourcing
Like several partnership, outsourcing comes with its personal set of dangers. That will help you navigate the method easily, we’ve highlighted the most typical points — and keep away from them.
Frequent Pitfalls and Learn how to Keep away from Them
One of many greatest challenges in outsourcing is easy — the shopper and the workforce simply don’t perceive one another. You’re pondering one factor, however the builders construct one thing utterly totally different. This often occurs when duties are described too vaguely or when the workforce doesn’t ask sufficient clarifying questions.
That’s why it’s essential to get aligned from the very starting: agree on objectives, stroll via every thing in plain language, and clearly outline the phases and priorities. It’s higher to spend a few days upfront than to redo every thing from scratch later.
One other all-too-common state of affairs: the workforce is busy working behind the scenes, however you’re left at nighttime, questioning what’s really occurring. Are they on schedule? What’s already accomplished? What’s subsequent? That feeling of not understanding will be irritating.
To remain easy and arranged, it’s nicely value organising a easy system from the outset — common check-ins, brief weekly stories, and one agreed-upon place to trace progress, whether or not a activity board, a Gantt chart, or no matter software feels acceptable to your workflow. A bit of construction makes an enormous distinction.
And one different vital element — selecting the right accomplice. Essentially the most widespread mistake is specializing in value solely. Chopping prices is tempting, naturally, but when the workforce is unhealthy at communication, unaware of your enterprise wants, and sloppy by way of execution — you’ll find yourself spending extra money.
It’s extra priceless to take a look at their expertise, case research, and most significantly, how they impart with you from day one.
Guaranteeing High quality and Safety
When outsourcing improvement work for the primary time, one of many major considerations is the standard of labor you might be getting. That’s the place a pilot activity will be helpful. Begin small — give them one thing they will handle and see how they strategy it.
How clear is the code? Have they got a great strategy to testing? Do they ask the fitting questions and shut issues down shortly? If all goes nicely, you’ll be able to comfortably transfer ahead with extra.
The identical applies for safety. In case your product has person information, cash elements, or delicate enterprise information, this half is non-negotiable.
Make sure that the workforce has concrete procedures in place for retaining issues safe: we’re speaking about safe environments for the event work (isolate builds), entry controls (add me when you’re accomplished), and correct encryption.
If you’re working with a accountable accomplice they need to not wait so that you can ask — they need to be elevating these factors themselves as a result of defending your information protects their fame too.
Outsource Software program Improvement: Authorized and IP Concerns
And, after all, you’ll be able to’t do with out authorized points. You should have all rights to the code, design, and interfaces. This needs to be spelled out within the contract instantly. Even in case you are not but fascinated with scaling or promoting the enterprise, it’s higher to formalize every thing accurately from the very starting.
It is usually value fixing within the contract phrases, cost, who’s chargeable for what, and what to do if one thing doesn’t go in response to plan.
And don’t overlook the NDA — particularly in the event you’re sharing inside data, technique, or product concepts. It’s not as difficult because it sounds, particularly in the event you work with a great workforce — they’ll enable you to get it proper.
Learn how to Work Successfully with Outsourcing Corporations
Collaboration with an exterior workforce will be very efficient — in the event you manage the method accurately. Under we now have ready for you the important thing factors that may enable you to manage your work with outsourced builders effectively and stress-free.

Setting Clear Objectives and KPIs
Any mission begins with a objective, and the clearer it’s, the higher the end result. An exterior workforce mustn’t simply “write code”, however perceive what you need to obtain. It may be a fast launch of an MVP, decreasing utility response time, bettering UX, or, for instance, switching to a brand new expertise.
It’s best when the objectives are expressed in particular indicators: first launch date, acceptable variety of bugs, web page load pace, and person attain. Such KPIs assist you to objectively assess progress and remove the state of affairs when everybody understands the duty in their very own means.
It is usually vital to prioritize. What’s extra vital to you — pace, high quality, scalability, or finances? The workforce will be capable to make higher technical choices in the event that they perceive what you might be specializing in.
Managing Time Zones and Communication
Time zone variations aren’t an issue — so long as you handle them correctly. The bottom line is to agree prematurely on overlapping hours. Even simply 1–2 shared hours a day will be sufficient to sync up, ask questions, and maintain issues shifting.
It additionally helps create a routine rhythm: weekly stories, demos frequently each couple of weeks, and brief every day progress stories. This offers a way of stability and retains you updated with out having to nag for outcomes.
And don’t overlook to align on communication instruments. Whether or not it’s Slack, Microsoft Groups, or Telegram — the software itself doesn’t matter as a lot as having one clear, energetic channel. Use emails for formal docs, however maintain day-to-day conversations and fast check-ins in chats or video calls.
Instruments for Managing Outsourcing Programming Groups
The correct instruments could make a world of distinction in the case of working easily with an outsourced workforce. They bring about readability, and construction, and assist everybody keep on the identical web page.
For monitoring duties, most groups use instruments like Jira, Trello, ClickUp, or YouTrack — these allow you to go in at any time and see what’s being labored on, what’s developing subsequent, and what’s nonetheless within the backlog.
Code usually lives in model management programs like GitHub, GitLab, or Bitbucket. These not solely maintain every thing organized but additionally make it simple to evaluation the code, see what’s been accomplished, and hint any adjustments again if wanted.
In the case of documenting issues — particularly on tasks with complicated structure or uncommon enterprise logic — instruments like Notion, Confluence, or Google Docs come in useful. They assist accumulate all of the vital data in a single place so nothing will get misplaced or forgotten.
And gaining access to all of this? It’s not about micromanaging or distrust — it’s simply good. It provides you a transparent view of what’s occurring, so if one thing begins to float off beam, you’ll be able to catch it early and steer issues again on observe. That’s simply good teamwork.
What a High Software program Outsourcing Accomplice Seems Like
Selecting the proper improvement accomplice is essential to a profitable mission. Within the sections under, we’ll stroll you thru what to search for in an outsourcing firm, what actual collaboration appears to be like like in observe, and why SCAND rightfully stands among the many high software program improvement suppliers in 2025.
Standards for Choosing a Supplier
For outsourcing to really work, you might want to look past simply value tags or supply guarantees. A dependable accomplice is a workforce that speaks your language — not simply actually, however by way of understanding your enterprise objectives.
They don’t simply “observe the spec,” they assume proactively and counsel technical options that suit your wants, not simply what’s at present fashionable.
A powerful outsourcing firm is clear in communication, comfy working with agile methodologies, and versatile in the case of scaling the workforce. Most significantly, they will again up their experience with actual case research, strong tech stacks, and real shopper suggestions.
Overview of Corporations That Outsource Programming
At present, outsourcing software program improvement is widespread throughout the board — from startups and small companies to giant enterprises. It lets firms keep targeted on their core enterprise whereas leaving the technical aspect to specialists.
Essentially the most generally outsourced areas embody frontend and cellular improvement, backend programs and APIs, testing, assist, modernization of legacy programs, and constructing MVPs.
Companies that worth flexibility, need to pace up time-to-market, and don’t need to spend months hiring an in-house workforce are more and more turning to outsourcing. It’s a sensible option to save time and finances — with out sacrificing high quality.
High Coding Outsourcing Corporations in 2025: Why Select SCAND
SCAND is a software program improvement firm with over 20 years of expertise serving to purchasers world wide deliver their concepts to life. We’re based mostly in Poland and provide a full improvement cycle — from early ideas and prototypes to launch, testing, and long-term assist.
Right here’s what makes us a trusted accomplice:
- Robust technical know-how — Whether or not it’s constructing smooth net and cellular apps with React, Angular, Flutter, or Kotlin, or creating complicated backend programs utilizing Java, .NET, Python, or Go — we’ve received it coated.
- Clear communication and adaptability — We bounce into tasks shortly, adapt to your workflow, and collaborate as if we’re a part of your in-house improvement workforce.
- A workforce that really cares — No random hires right here. Each developer goes via a cautious choice course of, works to excessive requirements, and is targeted on delivering actual outcomes.
- Safety and belief — We’re severe about defending your information. Meaning signing NDAs, sticking to clear contracts, and making certain you absolutely personal your code.
- Expertise throughout industries — From finance and e-commerce to logistics, schooling, healthcare, and gaming — we’ve labored on all of it.
At SCAND, we’re not simply right here to jot down code. We’re right here that will help you construct one thing that works, launches on time, and makes an impression. Whether or not you’re ranging from scratch, scaling quick, or modernizing what you have already got — we’re prepared to leap in and get it accomplished.
Conclusion
Outsourcing improvement is a sensible option to transfer your enterprise ahead. It helps you scale sooner, launch merchandise directly, and produce within the tech experience you want — all with out stretching your inside workforce too skinny.
Whether or not you’re testing a brand new concept, modernizing an previous system, or kicking off a recent mission, outsourcing options can take a number of weight off your shoulders.
The important thing, although, is discovering the fitting accomplice. Not simply somebody who can write code, however a workforce that will get your objectives, communicates clearly, and genuinely cares in regards to the final result.
Search for transparency, strong expertise, technical depth, and a workflow that matches the way you prefer to work. And don’t overlook the authorized aspect — possession of the code and correct confidentiality agreements ought to all the time be a part of the deal.
A fantastic outsourcing workforce looks like an extension of your individual. They ask the fitting questions, flag points early, and enable you to make good choices — not simply ship what’s on the duty listing.
If that’s the form of partnership you’re searching for, we’re right here and able to dive in. Share your concept with SCAND and let’s determine one of the best ways to deliver it to life collectively.














