Register now for Cisco Accomplice Summit 2025 – November 3-5, San Diego, California.
Once I lately took on this function, I made a dedication to our companion neighborhood: you’ll get consistency, honesty, and transparency from me. As we method my first Cisco Accomplice Summit because the International Accomplice Gross sales chief, I wish to share a easy method for our partnerships.
After 25+ years at Cisco, I’ve realized that probably the most highly effective ideas are sometimes the best ones. That’s why I wish to discuss two questions that ought to information how we work collectively, and a framework I name “sturdy progress.”
The Questions That Drive Progress
These two questions work collectively however serve completely different functions. The primary drives how we collaborate internally at Cisco, making certain each staff is concentrated on advancing alternatives for our companions. The second is about our exterior partnership success, although there’s pure overlap as inside alignment immediately impacts companion profitability.
First: Are we transferring offers ahead? This isn’t nearly closing enterprise. Are you positioned early in alternatives? Are you leveraging our joint portfolio to create aggressive differentiation? Are you utilizing deal registration as an funding in mutual success? When prospects perceive the mutual good thing about what we will ship collectively, our win charge approaches 100%. I’m not conscious of a deal we’ve misplaced when prospects actually comprehend the entire worth we ship collectively.
Second: Are we constructing worthwhile partnerships? Worthwhile partnerships are the inspiration of sturdy progress. Whenever you make cash with Cisco, you possibly can reinvest in your small business, increasing experience, hiring licensed engineers, and reaching new markets. That reinvestment creates a flywheel: deeper capabilities that gasoline buyer outcomes, which in flip drive extra progress.
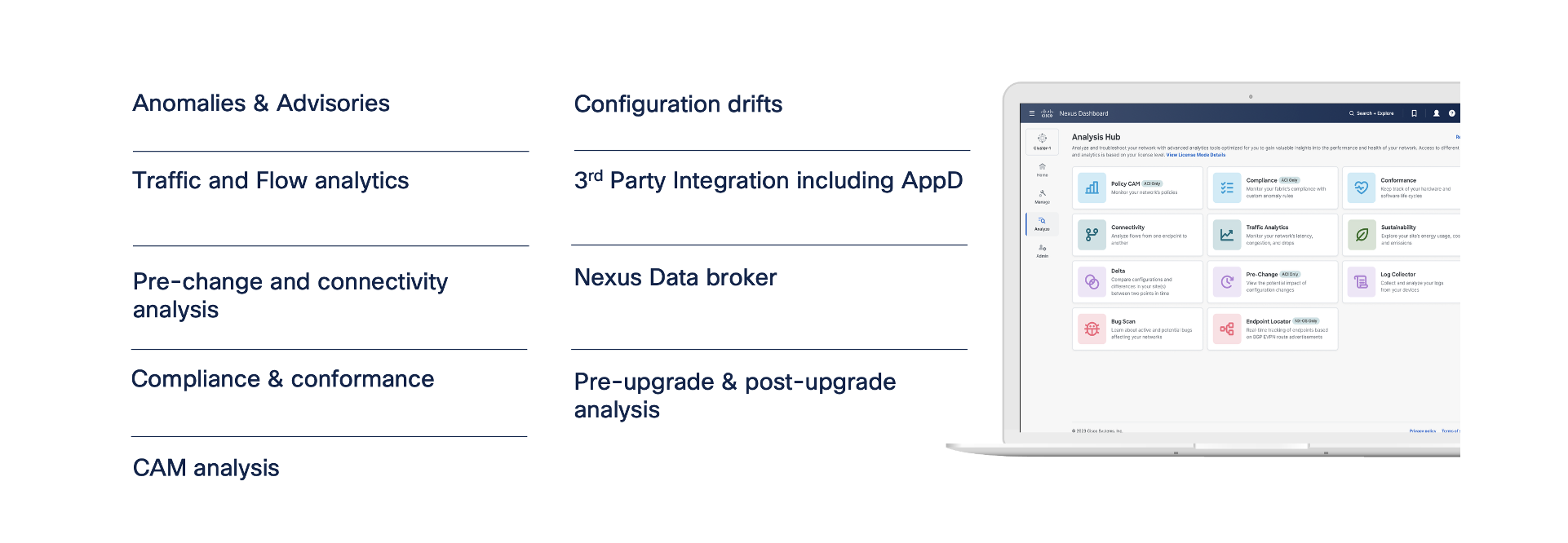
Accomplice profitability is on the core of the brand new Cisco 360 Accomplice Program. It builds on probably the most trusted companion program within the trade whereas evolving to fulfill at present’s market. It honors previous investments, rewards present worth creation, and positions us collectively for future market alternatives.
Prospects aren’t simply shopping for know-how; they’re shopping for outcomes. Companions who ship these outcomes win. The Cisco 360 Accomplice Program acknowledges and rewards that worth, serving to you translate buyer impression into worthwhile progress.
I typically ask companions: would you quite compete deal by deal, or construct relationships that develop organically? Companions who promote level options compete on value each renewal cycle. Companions who ship built-in outcomes turn into trusted advisors who seize a number of alternatives inside the similar account. Solely Cisco provides the portfolio breadth to develop margin profiles throughout architectures, industries, and buyer wants at scale.
What Sturdy Progress Means for Your Enterprise
Accomplice progress with Cisco must be 4 issues:
Constant. Whenever you ship constant outcomes, prospects turn into loyal advocates who develop their investments and refer new alternatives. Consistency turns tasks into relationships.
Predictable. When your Cisco apply delivers predictable outcomes, you possibly can develop into adjoining markets. Predictability means that you can plan for progress quite than hope for it.
Forward of market. We’re in markets experiencing unprecedented demand in AI infrastructure, cybersecurity, and campus modernization. Companions who seize disproportionate share place themselves forward of the curve.
Worthwhile. Whenever you make cash with Cisco, you spend money on our mutual success. You develop specialised experience and turn into the companion prospects search out, not accept.
Why Your Partnership with Cisco is Totally different
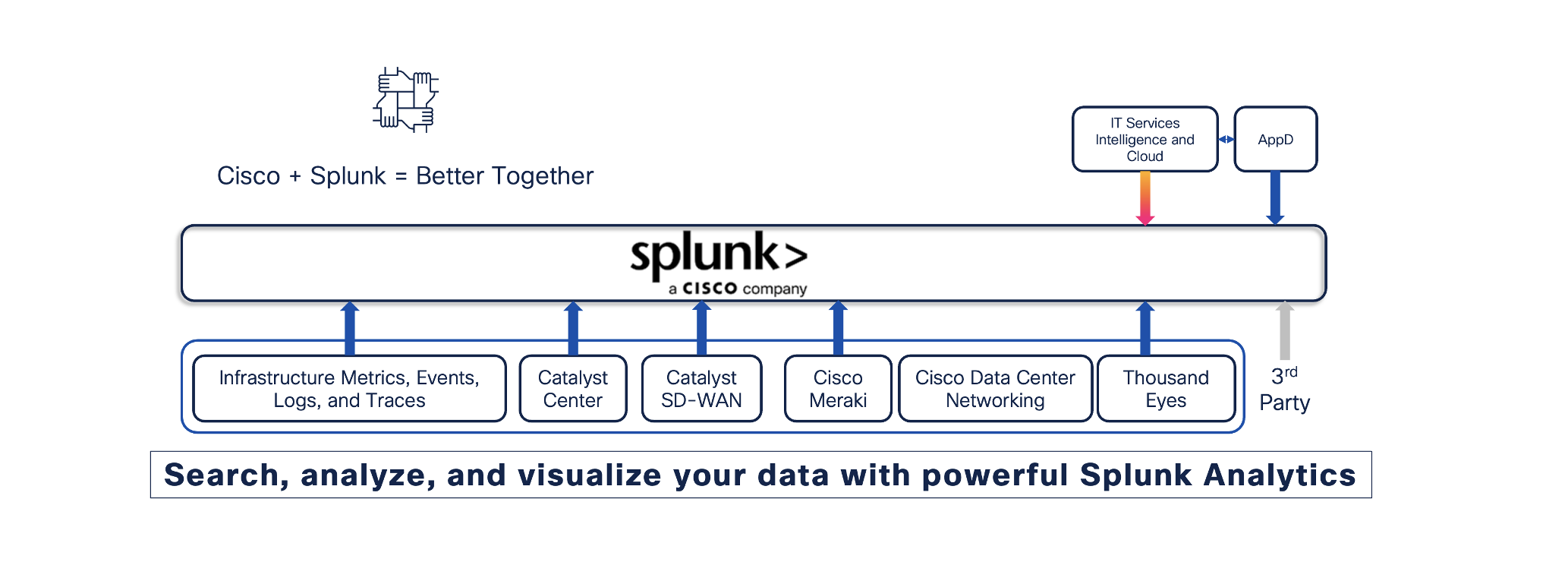
Our “One Cisco” technique delivers deeply built-in options combining networking, safety, collaboration, and observability to unravel prospects’ largest AI-era challenges. With Splunk, you will have a defining second to redefine choices and differentiate within the market.
Whether or not you’re powering AI-ready knowledge facilities, creating future-proofed workplaces, or constructing digital resilience, you’re positioned to ship sturdy progress spanning a number of buyer wants. You’re not simply promoting merchandise; you’re architecting complete options that create lasting aggressive benefits.
Right here’s what makes us completely different: we’ve constructed our enterprise mannequin round your success, and we’re dedicated to true collaboration at each step. We work alongside you to know market challenges, co-create buyer options, and guarantee you will have the assist wanted to win. Our incentive packages are designed that can assist you construct worthwhile practices. Our enablement is aggressive benefit.
The brand new Cisco Accomplice Incentive unifies incentives like VIP right into a easy framework rewarding companions throughout the total lifecycle from touchdown alternatives to adoption, enlargement, and renewal. With extra funding flowing into lifecycle and companies, companions proceed incomes at present whereas opening higher alternatives tomorrow.
Cisco Accomplice Summit 2025: A New Perspective
I’m honored to host Cisco Accomplice Summit this yr. I don’t come from a standard companion background, however these aren’t conventional occasions. What I deliver is 25+ years of watching our companion ecosystem ship extraordinary outcomes.
Profitable partnerships aren’t constructed on what we will do for you. They’re constructed on what we accomplish collectively. Once we mix Cisco’s innovation together with your market experience and buyer relationships, we create options no competitor can match.
Accomplice Summit 2025 is the place we’ll present you learn how to flip these ideas into income progress. You’ll see how Cisco 360 creates new pathways to profitability and perceive how our improvements mix to create aggressive benefits. You’ll go away with a transparent innovation, answer, and partnership roadmap.
The Selection Forward
You’ve gotten selections about the place to speculate your time, folks, and assets. Each vendor desires your consideration. Each know-how shift creates new alternatives and opponents.
However the future belongs to companions who perceive what’s coming earlier than it turns into apparent to everybody else. Companions who construct capabilities at present for tomorrow’s alternatives.
Be a part of us November 3-5 in San Diego, California. Are we transferring offers ahead? Are we constructing worthwhile partnerships? Let’s flip these two easy questions into sturdy progress for your small business.
As a result of once we get this proper, once we constantly transfer offers ahead collectively and construct mutually worthwhile partnerships, we don’t simply develop. We dominate.
I’ll see you there.
We’d love to listen to what you suppose. Ask a Query, Remark Beneath, and Keep Related with #CiscoPartners on social!
Cisco Companions Fb | @CiscoPartners X/Twitter | Cisco Companions LinkedIn
Share: