You may get wealthy topographical mountaineering maps of native trails and U.S. nationwide parks in your iPhone, proper in Apple Maps. New in iOS 18, you possibly can construct customized routes connecting strolling paths and save them to your system for offline entry.
You should utilize this characteristic to plan a hike as a day journey. Planning your route upfront might prevent the effort of getting misplaced with out a sign — or hold you from beginning a very bold hike.
In accordance with Apple, the replace comes with information for “all 63 U.S. nationwide parks.” In my testing, Apple Maps confirmed an intensive information of the paths in northeastern and Appalachian Ohio, too. It might comprise detailed path information about your native park as properly.
Right here’s take advantage of out of the brand new mountaineering maps in iOS 18.
Easy methods to get mountaineering instructions in Apple Maps
Word: These mountaineering options are new to iOS 18 — out there now in a public beta. Apple will launch iOS 18 this September, and the replace will work with any system presently working iOS 17.
Desk of contents: Easy methods to get mountaineering instructions in Apple Maps
- Discover mountaineering maps and trails
- Get particulars on trails and hikes
- Construct customized paths in Apple Maps
Discover mountaineering maps and trails

Screenshot: D. Griffin Jones/Cult of Mac
After you replace to iOS 18, yow will discover mountaineering trails in a number of other ways in Apple Maps. Simply search “mountaineering” to carry up ends in your space and present them on the map. You possibly can filter for size, elevation and extra. You can also faucet on a park and discover a listing of hikes by scrolling all the way down to the “Hikes” part on the web page.
Apple Maps shows mountaineering trails as white dotted traces. Small circles on the map designate intersections. Whenever you zoom into an space whereas a park, path or path, you’ll see contour traces drawn on the map indicating the topography.
Get particulars on trails and hikes

Screenshot: D. Griffin Jones/Cult of Mac
You possibly can faucet on a path in Apple Maps to see particulars like its size, highest and lowest elevations, and the varied trailheads (entrances and exits) alongside the trail. If the path falls exterior of typical cell protection, faucet Obtain to be sure to can navigate round in your hike always.
Scroll down and you might even see predesigned hikes alongside the path. You’ll see within the preview card a top level view of the trail, the general distance and the change in elevation. Faucet to see particulars with an elevation map and strolling time estimate. Tapping Add to Library will allow you to obtain the map and enter a customized title and outline of the hike to your library. Tapping Instructions will navigate to the beginning of the hike out of your present location.
Construct customized paths in Apple maps
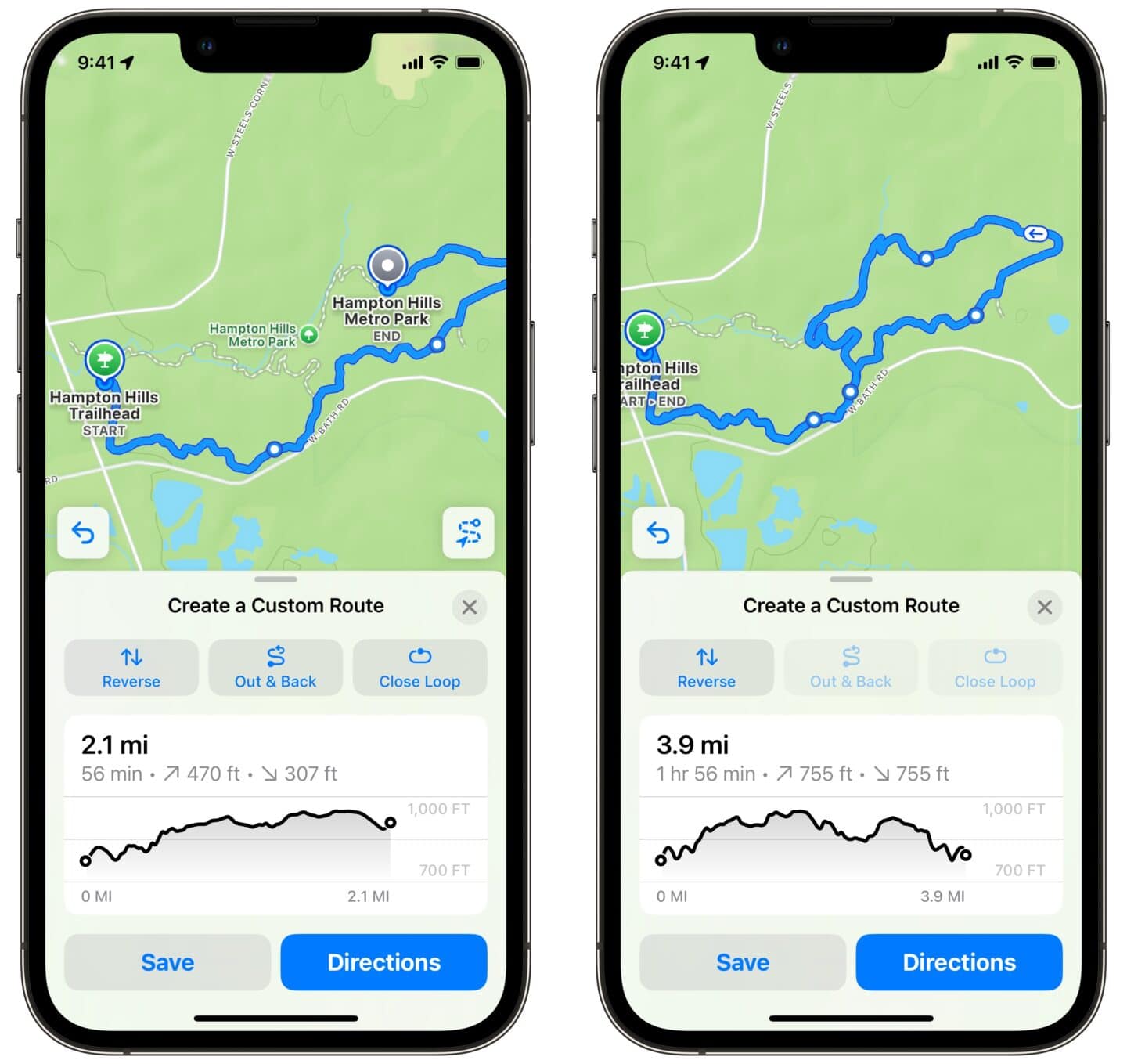
Screenshot: D. Griffin Jones/Cult of Mac
If a trailhead is a part of a community of paths, you’ll see an choice to Create a Customized Route. Faucet on completely different elements of the path to attract out the trail you wish to stroll. When you make a mistake, faucet the Undo button to the left.
Slide up on the sheet on the backside of the mountaineering map for more information and choices. After you begin drawing a path, you possibly can faucet Out & Again if you wish to flip round and return the best way you got here, or Shut Loop if you wish to take the shortest route again to the trailhead. The graph under the path map will present your elevation and estimated strolling time.
Hitting Save will allow you to give the route a customized title and outline, and mean you can obtain the trail. Instructions will begin navigating to the trailhead. Faucet the × to delete the route or begin over.
Extra iOS 18 options
Now that you understand how to create customized mountaineering maps in Apple Maps, try a few of the different nice new options in iOS 18:






