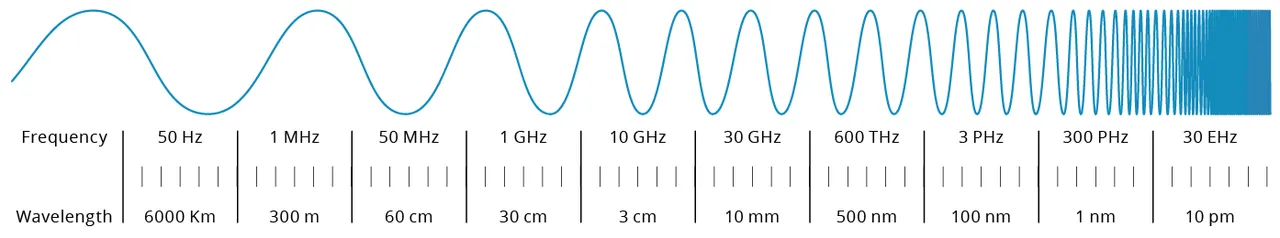
TUV SUD has audited the Security Case Analysis and useful security for Gatik’s self-driving vehicles. Supply: Gatik
Gatik AI Inc. goals to set the bar excessive for autonomous truck security. The corporate immediately asserting that it has acquired unbiased validation for the Security Case Analysis and Practical Security phases of its Security Evaluation Framework from TÜV SÜD. It claimed that this third-party audit was the primary of its sort and that it marks a big milestone towards commercialization of self-driving freight operations.
“We strongly consider that the way forward for autonomous automobiles will probably be outlined by those that prioritize security above all else,” said Gautam Narang, CEO of Gatik. “This independently validated audit of our Security Case and Practical Security methodology represents a radical departure from the self-certified security audits which have develop into the trade norm.”
“By participating TÜV SÜD to offer this validation from an exterior vantage level, Gatik is setting a brand new benchmark for the trade — one which places security and transparency on the forefront of the autonomous car revolution,” he asserted.
Based in 2017, Gatik has developed autonomous automobiles (AVs) for middle-mile and short-haul logistics. The Mountain View, Calif.-based firm launched its first driverless industrial transportation service with Walmart in 2021 and Kroger in 2023.
Isuzu Motors, Cummins, Ryder, and Goodyear are amongst Gatik’s companions. Its medium-duty autonomous vehicles are working in Texas, Arkansas, Arizona, and Ontario.

Register now so you do not miss out!
TÜV SÜD carried out an intensive analysis
Whereas self-certification has develop into the accepted customary for security within the AV trade, Gatik stated it has gone above and past by way of traceability and transparency with its Security Evaluation Framework.
“We don’t should to do that. The automotive and trucking industries self-certify,” stated Dr. Adam Campbell, Gatik’s head of security. “In autonomous trucking, its basically the identical, testing for what’s minimally anticipated.”
“We made the selection to conduct a rigorous degree of analysis,” he informed The Robotic Report. “It’s what our prospects need and what the standard roadway person desires. Belief shouldn’t be simple to come back by on this trade, and it’s simply misplaced.”
“The unbiased validation that we’ve got pursued at Gatik meets the extent of transparency that policymakers, first responders, enterprise companions, and on a regular basis drivers count on and deserve,” added Campbell. “Exterior validation is our approach of assuring the general public and all stakeholders that we’re doing the suitable factor.”
Gatik stated its Security Evaluation Framework identifies greater than 700 portfolios to handle key pillars of AV security. They embody organizational security tradition, engineering high quality (useful, behavioral, and operational security of the self-driving system), cybersecurity, car security, and Security Case conformity to UL4600 and different trade requirements.
“We offered documentation, check outcomes, and personnel to be interviewed,” recalled Campbell. “For instance, TÜV SÜD checked out peer growth and design validation.”
“One other step was having data translated into one thing that’s human-readable to be audited,” he defined. “That translation was fairly an train. Outcomes may make sense to our engineering staff, however we would have liked to make it digestible and readable.”
Munich, Germany-based TÜV SÜD has testing places throughout the U.S. The firm‘s Autonomous Automobile Conformity Framework concerned an end-to-end evaluate of Gatik’s Practical Security portfolios. It regarded on the following:
- Operational design area (ODD)
- Merchandise definition
- Testing
- Hazard evaluation and danger evaluation (HARA)
- Protection/security evaluation
- Security Tradition
These and different gadgets associated to security assist a complete Security Case permitting for applicable oversight of the complete system, stated Gatik. TÜV SÜD concluded that the firm’s strategy demonstrated “substantial rigor and compliance” with its necessities underneath the Autonomous Automobile Conformity Framework.
“This can be a course of that no different firm to our data has taken,” stated Campbell. “We’ve realized loads about what audit readiness seems to be like. Security is a journey and an addition to our engineering course of. We consider we’re on the suitable path.”

Click on right here to enlarge. Supply: Gatik
Gatik plans to launch freight service at scale
Gatik stated it additionally plans to publicly share additional data on its progress towards completion of the Security Evaluation Framework previous to deployment of freight-only operations at scale this yr. The corporate final month stated it plans to speed up mass manufacturing of SAE Degree 4 autonomous vehicles utilizing NVIDIA in-vehicle compute.
“TÜV SÜD’s evaluation represents an amazing vote of confidence in our approaches to scaling security in our Security Evaluation Framework,” stated Campbell. “We’ve been in conversations with state and federal governments, explaining why we’ve carried out essentially the most in depth working security plan and audits for autonomous programs thus far.”
“It will assist us get forward of allowing applications,” he acknowledged. “We wish to share our perspective of what we consider the excessive water mark ought to be for the trade. Our buyer base consists of a few of the largest delivery corporations in North America.”
Since Gatik has co-developed and operated its self-driving vehicles with companions, the firm has a transparent understanding of their security wants, Campbell stated. This consists of the interactions amongst automobiles, items, and staffs at distribution facilities and shops.
“Legislation enforcement can also be integral to scaling deployment of our expertise,” stated Campbell. “We offered police in Texas with a coaching video and hands-on alternatives. We don’t wish to shock anybody, which is why we’re so diligent in exhibiting all events that our use case is totally scoped, together with documentation to justify secure operations.”
The place is Gatik autonomous freight rolling to subsequent?
“We’re working to densify networks which have already been validated, including extra vehicles and shops inside these networks,” replied Campbell. “This permits us to make use of the testing and validation work that has already been finished to scale safely.”
“We’re trying to develop into many different jurisdictions; we’d like each scale and security to satisfy industrial demand,” he added. “This milestone doesn’t imply that we are able to sit again and calm down, but it surely frees the flywheel of innovation to develop extra merchandise.”