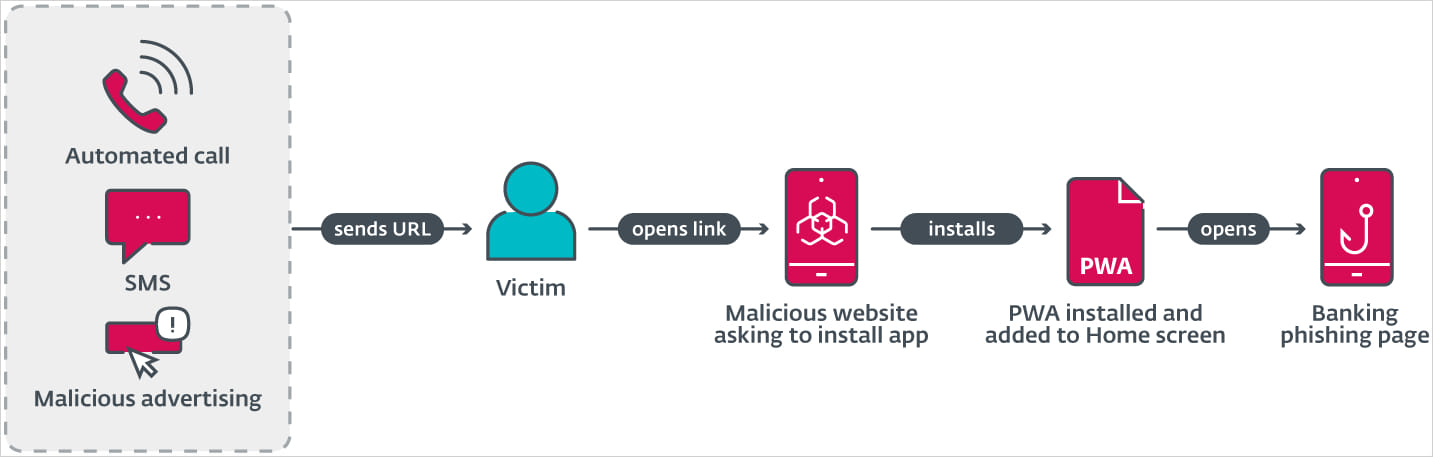
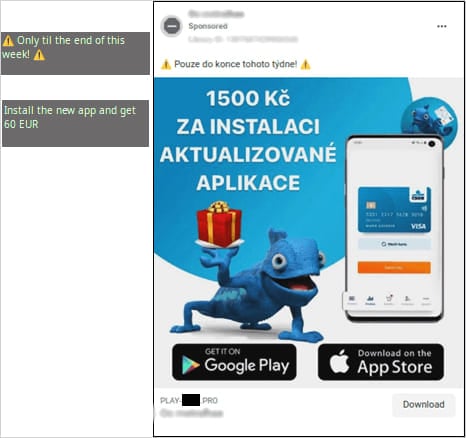
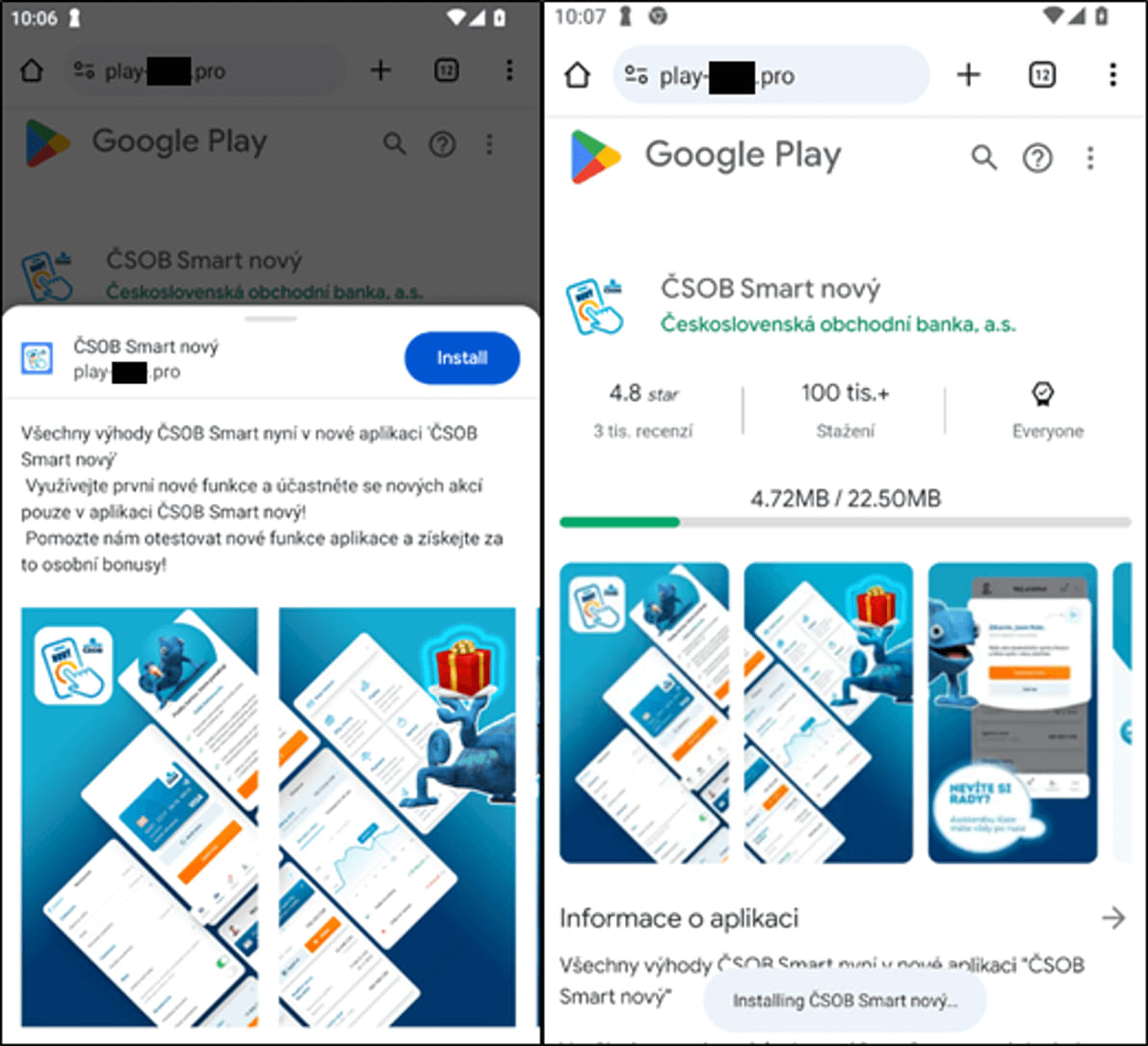
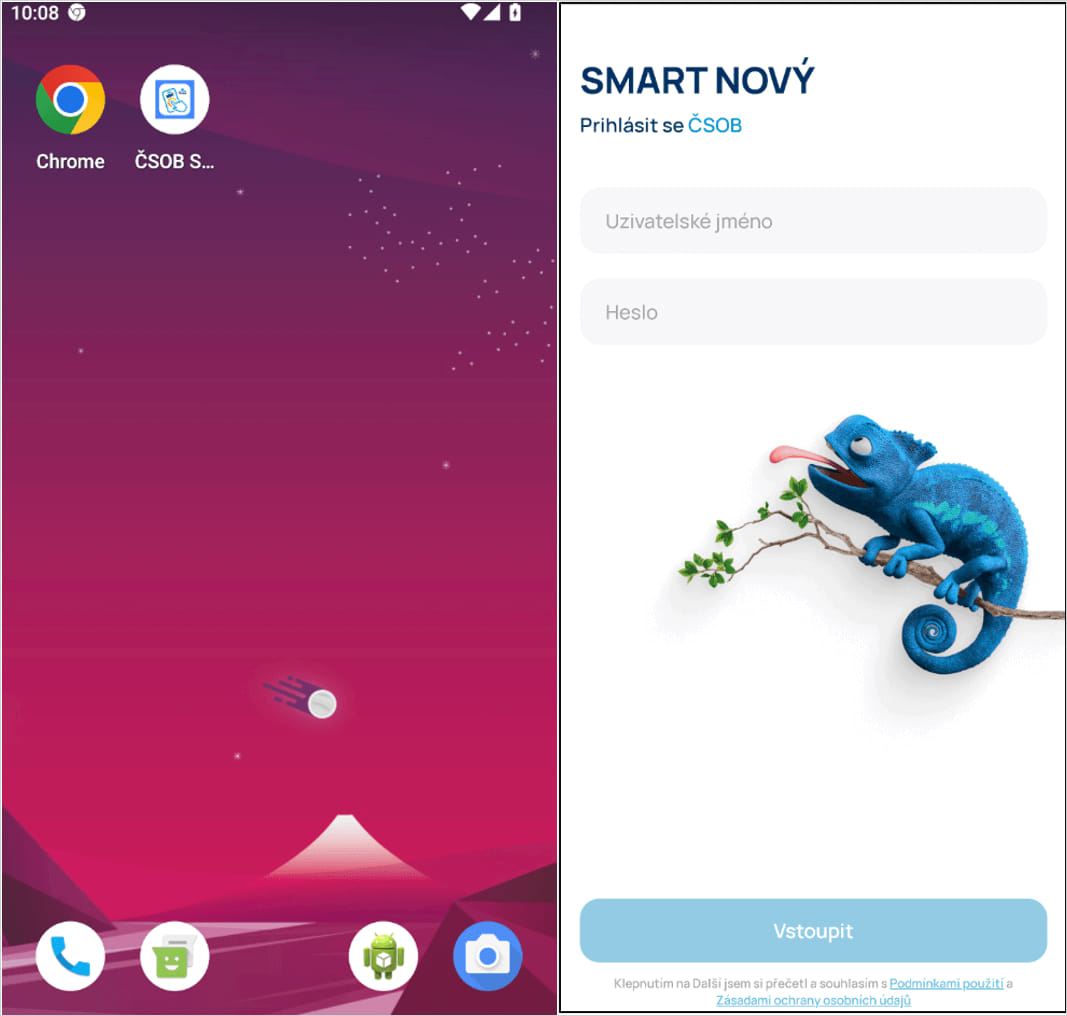
Posted in
Enterprise |
August 01, 2024
3 min learn
Enterprise IT leaders throughout industries are tasked with getting ready their organizations for the applied sciences of the long run – which is not any easy process. With using AI exploding, Cloudera, in partnership with Researchscape, surveyed 600 IT leaders who work at firms with over 1,000 workers within the U.S., EMEA and APAC areas. The survey, ‘The State of Enterprise AI and Trendy Information Structure’ uncovered the challenges and limitations that exist with AI adoption, present enterprise AI deployment plans, and the state of information infrastructures and knowledge administration.
The State of Enterprise AI
It can seemingly come as little shock that companies the world over are swiftly incorporating AI into their operations, with 88% of surveyed firms already using this transformative expertise. AI is beginning to revolutionize industries by altering how a enterprise operates and the groups inside. The departments main this adoption are IT (92%), Buyer Service (52%), and Advertising and marketing (45%). Throughout these enterprise areas, AI is enhancing effectivity in IT processes, bettering buyer assist with chatbots, and leveraging analytics for higher decision-making.
Amongst varied AI implementations, Generative AI (GenAI) stands out as the preferred, with 67% of respondents using generative fashions in some capability. Firms are deploying GenAI utilizing a number of architectures: exposing knowledge to open-source fashions with out coaching on it (60%), coaching open-source fashions on their knowledge (57%), utilizing open-source fashions skilled on-premises or in non-public clouds (50%), and growing proprietary Massive Language Fashions (LLMs) or Small Language Fashions (26%).
Along with GenAI, respondents famous they’re deploying predictive (50%), deep studying (45%), classification (36%) and supervised studying (35%) functions.
Challenges in Implementing AI
Implementing AI doesn’t come with out challenges for a lot of organizations, primarily on account of outdated or insufficient knowledge infrastructures. Whereas each enterprise has adopted some type of knowledge structure, the categories they use fluctuate extensively. The vast majority of organizations retailer their knowledge in non-public clouds (81%), however different architectures are additionally prevalent, together with public clouds (58%), on-premises mainframes (42%), on-premises distributed techniques (31%), different bodily environments (29%), and knowledge lakehouses (19%).
Navigating the complexity of recent knowledge landscapes brings its personal set of challenges. Key points embrace knowledge safety and reliability (66%), escalating knowledge administration prices (48%), compliance and governance challenges (38%), overly advanced processes (37%), siloed and difficult-to-access knowledge (36%), distrust in connecting non-public knowledge and inaccuracies in AI fashions (32%), and the necessity for standardized knowledge codecs (29%).
Including to those complexities is the quickly evolving nature of information applied sciences and the rising quantity of information companies should handle. Making certain that AI implementations are efficient and safe requires steady adaptation and funding in strong, scalable knowledge infrastructures. That is important for companies aiming to leverage AI for aggressive benefit and operational effectivity.
Leveraging Trendy Information Architectures
In as we speak’s panorama, the one means to make sure knowledge reliability is thru the adoption of recent knowledge architectures. These superior architectures present important flexibility and visibility, appearing as a blueprint for accelerating the extraction of insights and worth from knowledge. They simplify knowledge entry throughout organizations, breaking down silos and making knowledge simpler to grasp and act upon.
When requested about essentially the most priceless benefits of hybrid knowledge architectures, respondents highlighted knowledge safety (71%) as the first profit. Different important benefits embrace improved knowledge analytics (59%), enhanced knowledge administration (58%), scalability (53%), value effectivity (52%), flexibility (51%), and compliance (37%).
Trendy knowledge architectures assist the mixing of numerous knowledge sources and codecs, offering a cohesive and environment friendly framework for knowledge operations. This integration is important for companies aiming to leverage data-driven methods, making certain that their knowledge infrastructure can meet the calls for of evolving applied sciences and rising knowledge volumes. By adopting these architectures, organizations can place themselves to unlock new alternatives and drive innovation by means of dependable and accessible knowledge.
The improved safety, transparency, accessibility, and insights offered by trendy knowledge architectures straight contribute to a enterprise’s agility, adaptability, and knowledgeable decision-making. These elements are essential for future-proofing knowledge infrastructure, making certain it stays strong over time, and reaching tangible ROI from AI implementations.
To realize extra insights from Cloudera’s newest survey report, click on right here.