A wave of assaults that began in July 2024 depend on a much less widespread approach referred to as AppDomain Supervisor Injection, which might weaponize any Microsoft .NET utility on Home windows.
The approach has been round since 2017, and a number of proof-of-concept apps have been launched over time. Nevertheless, it’s usually utilized in purple group engagements and seldomly noticed in malicious assaults, with defenders not actively monitoring it.
The Japanese division of NTT has tracked assaults that finish with deploying a CobaltStrike beacon that focused authorities businesses in Taiwan, the navy within the Philippines, and vitality organizations in Vietnam.
Techniques, methods, and procedures, and infrastructural overlaps with latest AhnLab studies and different sources, recommend that the Chinese language state-sponsored risk group APT 41 is behind the assaults, though this attribution has low confidence.
AppDomain Supervisor Injection
Much like customary DLL side-loading, AppDomainManager Injection additionally includes the usage of DLL recordsdata to attain malicious targets on breached techniques.
Nevertheless, AppDomainManager Injection leverages .NET Framework’s AppDomainManager class to inject and execute malicious code, making it stealthier and extra versatile.
The attacker prepares a malicious DLL that accommodates a category inheriting from the AppDomainManager class and a configuration file (exe.config) that redirects the loading of a legit meeting to the malicious DLL.
The attacker solely wants to position the malicious DLL and config file in the identical listing because the goal executable, while not having to match the identify of an current DLL, like in DLL side-loading.
When the .NET utility runs, the malicious DLL is loaded, and its code is executed inside the context of the legit utility.
In contrast to DLL side-loading, which might be extra simply detected by safety software program, AppDomainManager injection is tougher to detect as a result of the malicious habits seems to return from a legit, signed executable file.
GrimResource assaults
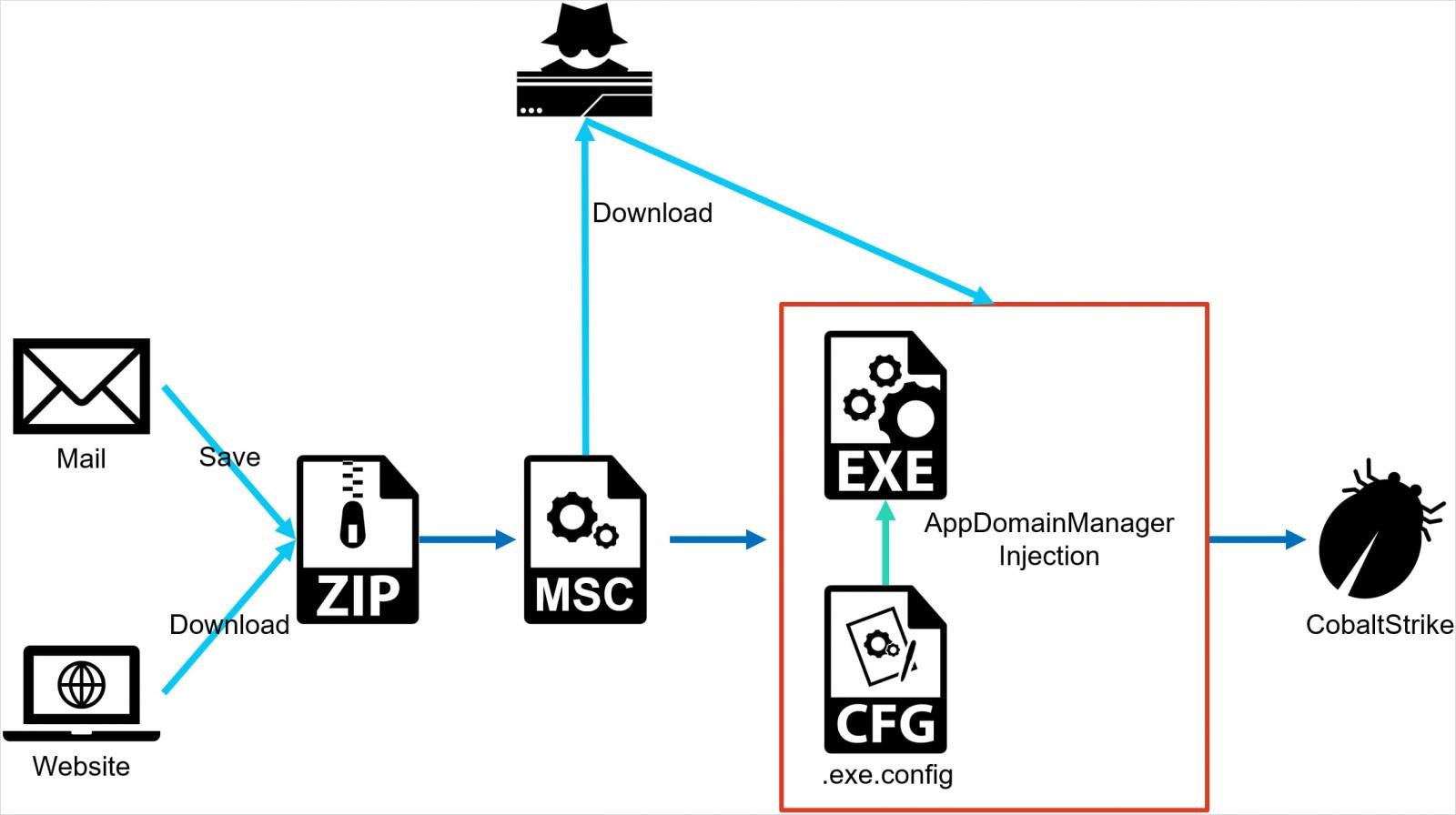
The assaults NTT noticed begin with the supply of a ZIP archive to the goal that accommodates a malicious MSC (Microsoft Script Part) file.
When the goal opens the file, malicious code is executed instantly with out additional consumer interplay or clicks, utilizing a method referred to as GrimResource, described intimately by Elastic’s safety group in June.
GrimResource is a novel assault approach that exploits a cross-site scripting (XSS) vulnerability within the apds.dll library of Home windows to execute arbitrary code by way of Microsoft Administration Console (MMC) utilizing specifically crafted MSC recordsdata.
The approach permits attackers to execute malicious JavaScript, which in flip can run .NET code utilizing the DotNetToJScript technique.
The MSC file within the newest assaults seen by NTT creates an exe.config file in the identical listing as a legit, signed Microsoft executable file (e.g. oncesvc.exe).
This configuration file redirects the loading of sure assemblies to a malicious DLL, which accommodates a category inheriting from the .NET Framework’s AppDomainManager class and is loaded as a substitute of the legit meeting.
Finally, this DLL executes malicious code inside the context of the legit and signed Microsoft executable, fully evading detection and bypassing safety measures.
Supply: NTT
The ultimate stage of the assault is loading a CobaltStrike beacon on the machine, which the attacker could use to carry out a broad vary of malicious actions, together with introducing further payloads and lateral motion.
Though it is not sure that APT41 is answerable for the assaults, the mixture of the AppDomainManager Injection and GrimResource methods signifies that the attackers have the technical experience to combine novel and less-known methods in sensible instances.