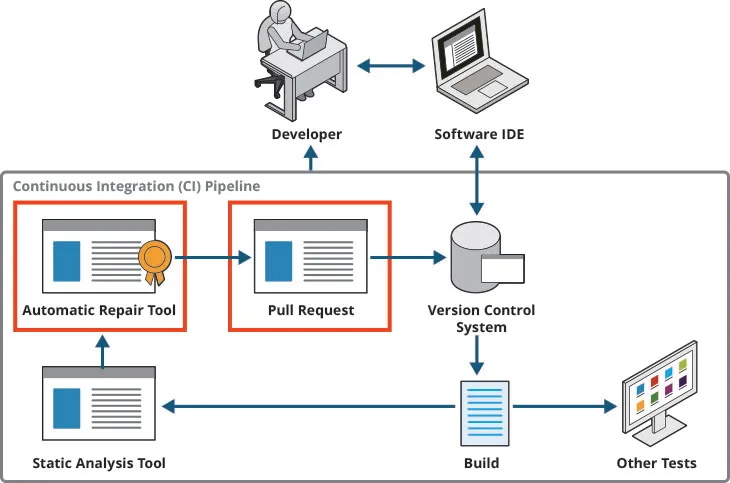
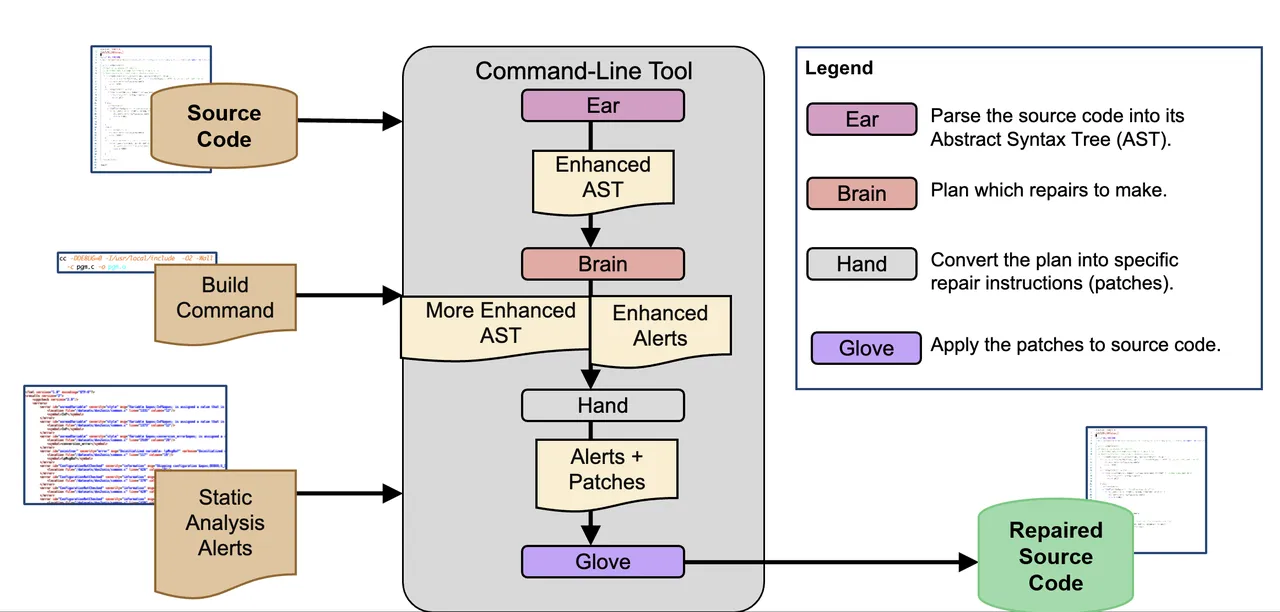
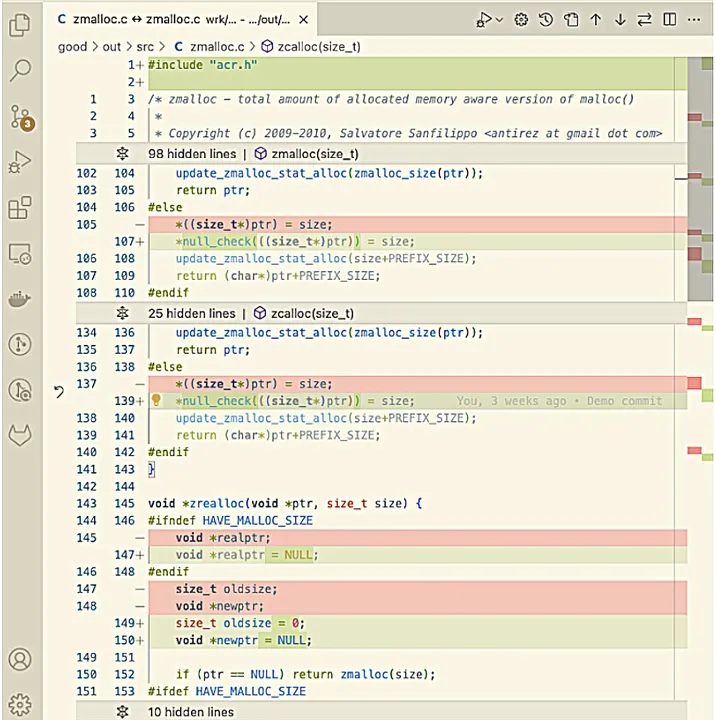
Change is a continuing within the know-how business. The latest entity on the town that’s revamping knowledge facilities is the info processing unit (DPU).
Why? The DPU is on the core of a rearchitect of processing energy the place servers have expanded properly past a central processing unit (CPU) to a collection of specialty processors, every offloading a particular set of duties so CPU can fly.
By offloading lifeblood knowledge dealing with capabilities from central processor models (CPU), DPUs are driving an information middle makeover that may lower the quantity of electrical energy used for cooling by 30%, decreasing the variety of costly servers wanted whereas boosting efficiency.
Unraveling the Magic of DPUs
DPUs are gadgets that give knowledge middle operators the flexibility to revamp operations and notice giant ensuing advantages in decreased vitality prices and server consolidation whereas boosting server efficiency. The DPUs assist knowledge middle servers deal with and improve new and rising workloads.
At the moment, with way more distributed workloads and purposes are extra distributed, they’re composed of unstructured knowledge corresponding to textual content, photographs, and huge information. In addition they use microservices that enhance east-west workload visitors throughout the info middle, edge, and cloud and require close to real-time efficiency. All this requires extra knowledge dealing with by infrastructure providers with out the expense of taking computing assets away from their essential aim of supporting day by day enterprise purposes.
Associated:The Rise of DPUs: Revolutionizing App Efficiency and Supply
What’s a DPU?
The DPU is a comparatively new machine that offloads processing-intensive duties from the CPU onto a separate card within the server. This mini onboard server is very optimized for community, storage and administration duties. Why the DPU? As a result of the final CPU was not designed for a majority of these intensive knowledge middle workloads, operating extra of them on the server can weight it down, which reduces efficiency.
The usage of DPUs can, for the above-mentioned causes, make an information middle way more environment friendly and cheaper to function, all whereas boosting efficiency.
How does a DPU differ from CPUs and GPUs?
Within the evolution of server computing energy, the CPU got here first, adopted by the graphics processing unit (GPU), which handles graphics, photographs, and video whereas supporting gaming. DPUs can work with their predecessors to tackle extra fashionable knowledge workloads. DPUs have risen in recognition by offloading knowledge processing duties corresponding to AI, IoT, 5G, and machine studying.
(Credit score: Dzmitry Skazau / Alamy Inventory Picture)
Essential Components that Complement DPUs to Energy Your Workloads
There are a collection of components that may successfully and effectively assist your DPUs create a staff designed to deal with your ever-changing and extra demanding knowledge middle workloads. Working as one, the processers will help you supercharge your data processing efforts. They’re:
GPU (Graphics Processing Unit)
GPUs complement the DPUs in a server by specializing in processing excessive bandwidth photographs and video, thus offloading this demanding perform from CPUs. This addition to the processor structure frees the brand new entrant to sort out extra knowledge and utilizing much less assets. GPUs are frequent in gaming techniques.
CPUs
A CPU consists of a few highly effective processing cores which are optimized for serial or sequential processing. Which means dealing with one activity after yet one more. In contrast, GPUs have quite a few less complicated cores for parallel processing to deal with simultaneous duties. DPUs mix processing core, {hardware}, and accelerators, in addition to a high-performance community interface with which to deal with data-centric duties in quantity.
Excessive-Efficiency Storage
One other factor in your knowledge middle that enhances using DPUs is excessive efficiency storage. Since DPUs facilitate improved community visitors administration, enhance safety measures, and improve storage processing the ensuing heightened effectivity sometimes results in an general enhance in systemwide efficiency.
“Storage, together with succesful high-performance networking, completes the computing help infrastructure and is essential throughout preliminary scoping to make sure most effectivity of all elements,” in line with Sven Oehme. CTO at DDN Storage.
Excessive-speed Community Connectivity
Usually, high-speed community connectivity enhances DPUs by letting them take in your heaviest workloads, corresponding to AI. These purposes additionally demand high-speed I/O. Due to this fact, most DPUs are configured with 100 Gbps ports these days and, in some instances, as much as 400 Gbps. Quicker supported speeds are anticipated quickly.
Compute Specific Hyperlink (CXL)
Compute Specific LINK (CXL) offers an essential help in knowledge middle efficiency as it’s an open interconnect normal for enabling environment friendly, coherent reminiscence entry between a number, corresponding to a processor, and a tool, corresponding to {hardware} accelerator or SmartNIC, as was defined in “CXL: A New Reminiscence Excessive-Velocity Interconnect Cloth.”
The usual goals to sort out what is named the von Neumann bottleneck during which laptop pace is proscribed to the speed at which the CPU can retrieve directions and knowledge from the reminiscence’s storage. CXL solves this downside in a number of methods, in line with the article. It takes a brand new method to reminiscence entry and sharing between a number of computing nodes. It permits reminiscence accelerators to grow to be disaggregated, enabling knowledge facilities to be totally software-defined.
Area Programmable Gate Array (FPGA)
FPGA can complement DPUs to assist energy your workloads. There are a number of DPU architectures, together with these based mostly on ARM SoCs, and there are these based mostly on the FPGA structure. Intel has been profitable with its FPGA-based Good NICs, or IPUs. “FGPAs supply some variations in comparison with ARM-based DPUs when it comes to the software program framework and growth. However the disadvantage is that FPGA programming is mostly extra complicated than that of ARM,” defined Baron Fung, Senior Analysis Director at Dell’Oro Group, a worldwide analysis and evaluation agency. That’s the reason most FPGA-based Good NICs are deployed by the hyperscalers and bigger Tier 2 Clouds, he added.
IPU (Infrastructure Processing Models)
IPUs are {hardware} accelerators designed to dump compute-intensive infrastructure duties like packet processing, visitors shaping, and digital switching from CPUs as we wrote in What’s an IPU (Infrastructure Processing Unit) and How Does it Work? An IPU, like a DPU and CXL, makes a brand new sort of acceleration know-how accessible within the knowledge middle.
Whereas GPUs, FPGAs, ASICS, and different {hardware} accelerators offload computing duties from CPUs, these gadgets and applied sciences concentrate on dashing up knowledge dealing with, motion, and networking chores.

(Credit score: Aleksey Odintsov / Alamy Inventory Picture)
Accelerating Efficiency in Knowledge Facilities with DPUs
The rising DPU processor class has the potential to extend server efficiency for AI purposes. It focuses on knowledge processing by means of the community, delivering environment friendly knowledge motion across the knowledge middle, and the offloading of community, safety, and storage actions from a system’s CPUs.
DPUs mixed with different perform accelerators are energy cutters, which interprets into financial savings to your group. About 30% of a server’s processing energy is devoted to performing community and storage capabilities in addition to accelerating different key actions, together with encryption, storage virtualization, deduplication, and compression.
Storage, together with succesful high-performance networking, completes the computing help infrastructure and is essential throughout preliminary scoping to make sure most effectivity of all elements.
Optimizing knowledge middle effectivity with NVIDIA BlueField DPUs
Utilizing a DPU to dump and speed up networking, safety, storage, or different infrastructure capabilities and control-plane purposes reduces server energy consumption by as much as 30%, claimed NVIDIA in a paper. “The quantity of energy financial savings will increase as server load will increase and might simply save $5.0 million in electrical energy prices for a big knowledge middle with 10,000 servers over the 3-year lifespan of the servers.”
Attaining supercomputing efficiency within the cloud
You’ll be able to obtain the aim of cloud-native supercomputing, which blends the facility of high-performance computing with the safety and ease of use of cloud computing providers, in line with NVIDIA. The seller offers NVIDIA Cloud-Native Supercomputing platform that it claims leverages the NVIDIA BlueField knowledge processing unit (DPU) structure with high-speed, low-latency NVIDIA Quantum InfiniBand networking “to ship bare-metal efficiency, person administration and isolation, knowledge safety, and on-demand high-performance computing (HPC) and AI providers,” in line with the seller.
Mixed with NVIDIA Quantum InfiniBand switching, this structure delivers optimum bare-metal efficiency whereas natively supporting multi-node tenant isolation.
Creating power-efficient knowledge facilities with DPUs
DPUs, Infrastructure Processing Models (IPUs), and Pc Specific Hyperlink (CXL) applied sciences, which offload switching and networking duties from server CPUs, have the potential to considerably enhance the info middle energy effectivity, as we famous in “How DPUs, IPUs, and CXL Can Enhance Knowledge Heart Energy Effectivity.” Actually, the Nationwide Renewable Power Laboratory (NREL) believes that using such strategies and concentrate on energy discount can lead to a 33 p.c enchancment in energy effectivity.
Integration hurdles in AI infrastructure
There are but different challenges in rolling out DPUs in your knowledge facilities must you select to incorporate AI within the setting. First, DPUs aren’t a prerequisite for AI infrastructure per se. Normally, the identical advantages of DPU apply to each AI and non-AI infrastructure, corresponding to the advantages of managing multi-tenants and safety, offloading the host CPU, load stability, and so on. Nevertheless, one distinctive case of DPUs for AI infrastructure is using DPUs for Ethernet-based back-end networks of GPU/AI server clusters. Within the case of the NVIDIA platform, DPU is a part of their Spectrum-X resolution set, which permits Ethernet-based back-end AI networks.
In distinction, different distributors, corresponding to Broadcom, use RDMA with their NICs to allow Ethernet-based back-end AI networks. “I believe anytime you are incorporating a number of items of processors along with the CPU (such GPUs and DPUs), there’s further value and software program optimization work that might be wanted,” cautioned Fung.
Balancing GPU vs CPU utilization
It is essential so that you can know that DPUs may assist enhance the utilization of each CPUs and GPUs. DPUs can offload community and storage infrastructure-related providers from the CPU, enhancing CPU utilization. “This may increasingly indirectly have an effect on GPU utilization. Nevertheless, DPUs can enhance the utilization of GPUs by means of multi-tenant help,” defined Fung. “For instance, in a big AI compute cluster of hundreds of GPUs, that cluster may be subdivided and shared for various customers and purposes in a safe and remoted method.”

(Credit score: Federico Caputo / Alamy Inventory Picture)
A Sneak-Peak into the Way forward for DPUs
It ought to come as little shock that the DPU market is poised for wholesome development. The worldwide DPU market is projected to succeed in $5.5 billion by 2031, rising at a CAGR of 26.9% from 2022 to 2031, in line with Allied Analytics LLP.
DPUs are extensively used to speed up AI and ML workloads by offloading duties corresponding to neural community inference and coaching from CPUs and GPUs. In AI purposes, DPUs are essential in processing giant datasets and executing complicated algorithms effectively, enabling quicker mannequin coaching and inference, in line with KBV Analysis. Industries corresponding to healthcare, finance, retail, and autonomous automobiles make the most of DPUs to energy AI-driven options for duties like picture recognition, pure language processing, and predictive analytics.
Navigating the longer term trajectory of knowledge processing models
Analysts challenge DPUs have a big development alternative, particularly for these AI networks. Sooner or later, hyperscalers will use DPUs extensively, as they do now. The query is whether or not the non-hyperscalers can make the most of DPUs. For these markets, DPUs might be helpful for superior workloads corresponding to AI based mostly on the above causes. Adoption of DPUs for non-hyperscalers conventional server purposes might take extra time, and the seller ecosystem wants to handle the three following gadgets: (DPU adoptions for the hyperscale have been progressing as a result of they’ve the 1) quantity/scale, 2) inner software program growth capabilities, and three) specialised server/rack infrastructure allow environment friendly and economical use of DPUs,)
Monitoring developments in DPU know-how environments
You’ll be able to count on to see a continued evolution and growth of specialty processors for servers to assist knowledge facilities function extra effectively, much less expensively, and with much less energy than their predecessors. Overloaded server CPUs are giving method to the GPU, the DPU, and, most just lately, the IPU. Intel has championed the IPU to dump infrastructure providers corresponding to safety, storage and digital switching. This frees up CPU cores for higher utility efficiency and decreased energy consumption.
Transferring Ahead with Rising Knowledge Heart Applied sciences
Sometimes delivered in programmable and pluggable playing cards, or “models,” a rising household of gadgets may be plugged into servers to dump CPU intensive duties, doubtlessly slicing cooling prices, decreasing server headcount and liberating up current horsepower for lifeblood workloads.
With at present’s fashionable and evolving workloads, mixed with spending limits and the necessity to save vitality in knowledge facilities, are you able to afford to not get good on this development?