Edge computing is now extra related than ever on this planet of synthetic intelligence (AI), machine studying (ML), and cloud computing. On the sting, low latency, trusted networks, and even connectivity usually are not assured. How can one embrace DevSecOps and trendy cloud-like infrastructure, reminiscent of Kubernetes and infrastructure as code, in an surroundings the place units have the bandwidth of a fax machine and the intermittent connectivity and excessive latency of a satellite tv for pc connection? On this weblog publish, we current a case examine that sought to import components of the cloud to an edge server surroundings utilizing open supply applied sciences.
Open Supply Edge Applied sciences
Not too long ago members of the SEI DevSecOps Innovation crew had been requested to discover an alternative choice to VMware’s vSphere Hypervisor in an edge compute surroundings, as current licensing mannequin modifications have elevated its price. This surroundings would wish to assist each a Kubernetes cluster and conventional digital machine (VM) workloads, all whereas being in a limited-connectivity surroundings. Moreover, it was necessary to automate as a lot of the deployment as potential. This publish explains how, with these necessities in thoughts, the crew got down to create a prototype that will deploy to a single, naked metallic server; set up a hypervisor; and deploy VMs that will host a Kubernetes cluster.
First, we needed to contemplate hypervisor options, such because the open supply Proxmox, which runs on prime of the Debian Linux distribution. Nonetheless, because of future constraints, reminiscent of the power to use a Protection Data Techniques Company (DISA) Safety Technical Implementation Guides (STIGs) to the hypervisor, this selection was dropped. Additionally, as of the time of this writing, Proxmox doesn’t have an official Terraform supplier that they preserve to assist cloud configuration. We needed to make use of Terraform to handle any sources that needed to be deployed on the hypervisor and didn’t wish to depend on suppliers developed by third events outdoors of Proxmox.
We determined to decide on the open supply Harvester hyperconverged infrastructure (HCI) hypervisor, which is maintained by SUSE. Harvester gives a hypervisor surroundings that runs on prime of SUSE Linux Enterprise (SLE) Micro 5.3 and RKE Authorities (RKE2). RKE2 is a Kubernetes distribution generally present in authorities areas. Harvester ties along with Cloud Native Computing Basis-supported initiatives, reminiscent of KubeVirt and Longhorn. Utilizing Kernel Digital Machine (KVM), KubeVirt permits the internet hosting of VMs which are managed by way of Kubernetes and Longhorn and supply a block storage answer to the RKE2 cluster. This answer stood out for 2 foremost causes: first, the provision of a DISA STIG for SUSE Linux Enterprise and second, the immutability of OS, which makes the basis filesystem learn solely in post-deployment.
Making a Deployment State of affairs
With the hypervisor chosen, work on our prototype might start. We created a small deployment situation: a single node can be the goal for a deployment that sat in a community with out wider Web entry. A laptop computer with a Linux VM working is hooked up to the community to behave as our bridge between required artifacts from the Web and the native space community.
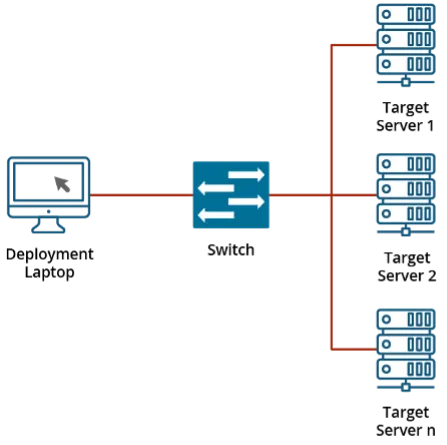
Determine 1: Instance of Community
Harvester helps an automatic set up utilizing the iPXE community boot surroundings and a configuration file. To attain this, an Ansible playbook was created to configure this VM, with these actions: set up software program packages together with Dynamic Host Configuration Protocol (DHCP) assist and an online server, configure these packages, and obtain artifacts to assist the community set up. The playbook helps variables to outline the community, the variety of nodes so as to add, and extra. This Ansible playbook helps work in direction of the thought of minimal contact (i.e., minimizing the variety of instructions an operator would wish to make use of to deploy the system). The playbook might be tied into an online software or one thing related that will current a graphical person interface (GUI) to the tip person, with a aim of eradicating the necessity for command-line instruments. As soon as the playbook runs, a server might be booted within the iPXE surroundings, and the set up from there may be automated. As soon as accomplished, a Harvester surroundings is created. From right here, the subsequent step of establishing a Kubernetes cluster can start.
A fast apart: Although we deployed Harvester on prime of an RKE2 Kubernetes cluster, one ought to keep away from deploying extra sources into that cluster. There’s an experimental function utilizing vCluster to deploy extra sources in a digital cluster alongside the RKE2 cluster. We selected to skip this step since VMs would must be deployed for sources anyway.
With a Harvester node stood up, VMs might be deployed. Harvester develops a first-party Terraform supplier and handles authentication by way of a kubeconfig file. The usage of Harvester with KVM permits the creation of VMs from cloud photos and opens potentialities for future work with customization of cloud photos. Our check surroundings used Ubuntu Linux cloud photos because the working system, enabling us to make use of cloud-init to configure the methods on preliminary start-up. From right here, we had a separate machine because the staging zone to host artifacts for standing up an RKE2 Kubernertes cluster. We ran one other Ansible playbook on this new VM to begin provisioning the cluster and initialize it with Zarf, which we’ll get again to. The Ansible playbook to provision the cluster is basically based mostly on the open supply playbook revealed by Rancher Authorities on their GitHub.
Let’s flip our consideration again to Zarf, a device with the tagline “DevSecOps for Airgap.” Initially a Naval Academy post-graduate analysis undertaking for deploying Kubernetes in a submarine, Zarf is now an open supply device hosted on GitHub. By way of a single, statically linked binary, a person can create and deploy packages. Principally, the aim right here is to assemble all of the sources (e.g., helm charts and container photos) required to deploy a Kubernetes artifact right into a tarball whereas there may be entry to the bigger Web. Throughout package deal creation, Zarf can generate a public/personal key for package deal signing utilizing Cosign.
A software program invoice of supplies (SBOM) can also be generated for every picture included within the Zarf package deal. The Zarf instruments assortment can be utilized to transform the SBOMs to the specified format, CycloneDX or SPDX, for additional evaluation, coverage enforcement, and monitoring. From right here, the package deal and Zarf binary might be moved into the sting gadget to deploy the packages. ZarfInitPackageestablishes parts in a Kubernetes cluster, however the package deal might be custom-made, and a default one is supplied. The 2 foremost issues that made Zarf stand out as an answer right here had been the self-contained container registry and the Kubernetes mutating webhook. There’s a chicken-and-egg drawback when attempting to face up a container registry in an air-gapped cluster, so Zarf will get round this by splitting the information of the Docker registry picture right into a bunch of configmaps which are merged to get it deployed. Moreover, a standard drawback of air-gapped clusters is that the container photos have to be re-tagged to assist the brand new registry. Nonetheless, the deployed mutating webhook will deal with this drawback. As a part of the Zarf initialization, a mutating webhook is deployed that can change any container photos from deployments to be mechanically up to date to seek advice from the brand new registry deployed by Zarf. These admission webhooks are a built-in useful resource of Kubernetes.
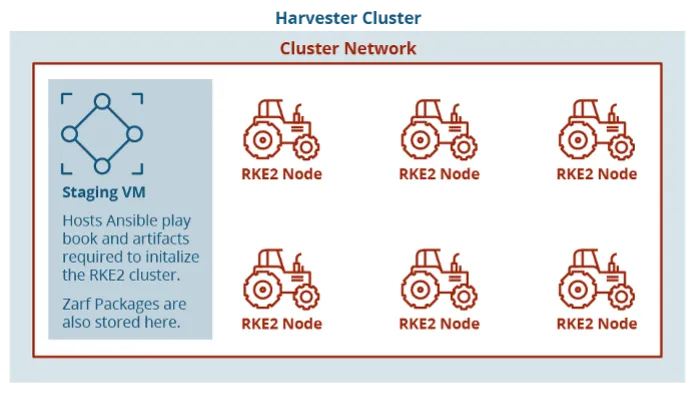
Determine 2: Format of Digital Machines on Harvester Cluster
Automating an Air-Gapped Edge Kubernetes Cluster
We now have an air-gapped Kubernetes cluster that new packages might be deployed to. This solves the unique slender scope of our prototype, however we additionally recognized future work avenues to discover. The primary is utilizing automation to construct auto-updated VMs that may be deployed onto a Harvester cluster with none extra setup past configuration of community/hostname data. Since these are VMs, extra work might be performed in a pipeline to mechanically replace packages, set up parts to assist a Kubernetes cluster, and extra. This automation has the potential to take away necessities for the operator since they’ve a turn-key VM that may be deployed. One other answer for coping with Kubernetes in air-gapped environments is Hauler. Whereas not a one-to-one comparability to Zarf, it’s related: a small, statically linked binary that may be run with out dependencies and that has the power to place sources reminiscent of helm charts and container photos right into a tarball. Sadly, it wasn’t made accessible till after our prototype was principally accomplished, however we have now plans to discover use circumstances in future deployments.
This can be a quickly altering infrastructure surroundings, and we look ahead to persevering with to discover Harvester as its growth continues and new wants come up for edge computing.








