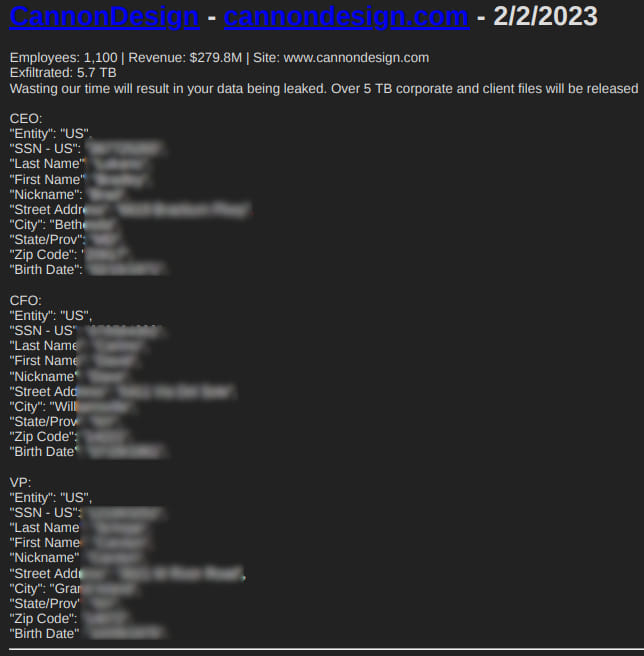
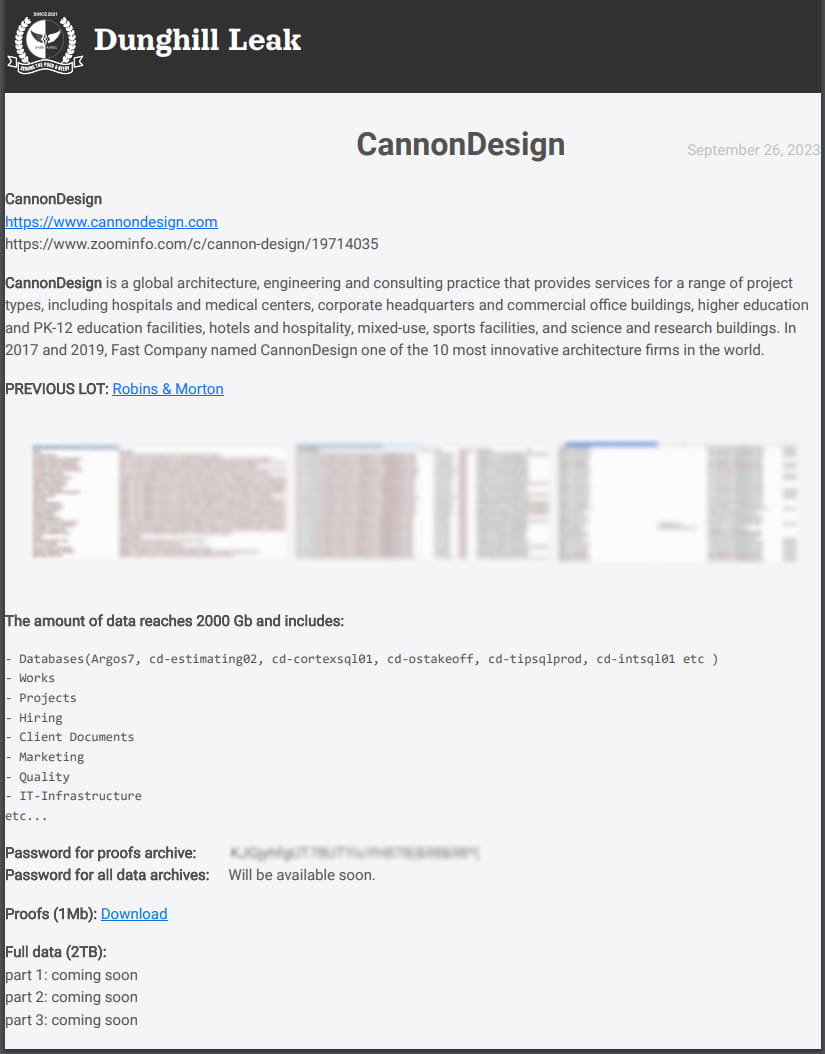
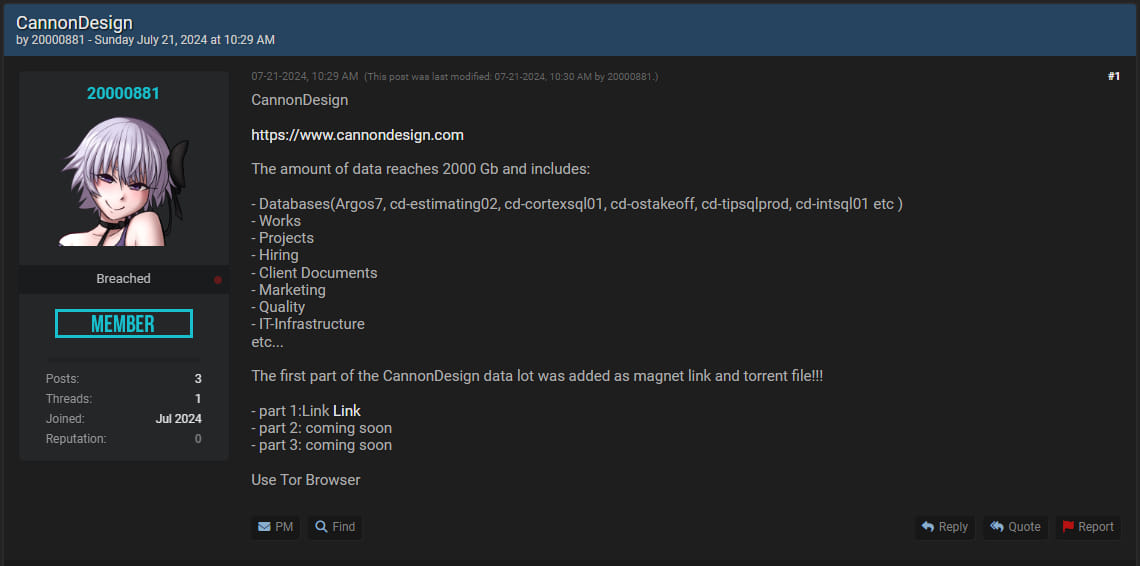
WWDC gave us many causes to each migrate libraries to SwiftPM and to develop new ones to help our work. The mixing between Xcode growth and SwiftPM dependencies retains rising stronger and extra essential.
Apple’s Modifying a Package deal Dependency as a Native Package deal assumes you’ll drag in your bundle to an Xcode undertaking as a neighborhood bundle overrides one which’s imported by way of a standard bundle dependency.
In Growing a Swift Package deal in Tandem with an App, Apple writes, “To develop a Swift bundle in tandem with an app, you possibly can leverage the habits whereby a neighborhood bundle overrides a bundle dependency with the identical identify…when you launch a brand new model of your Swift bundle or wish to cease utilizing the native bundle, take away it from the undertaking to make use of the bundle dependency once more.”
I don’t use this strategy. It’s not dangerous or incorrect, it simply doesn’t match my type.
However, opening the Package deal.swift file on to develop has drawbacks in that it doesn’t totally provide Xcode’s suite of IDE help options but.
So I’ve been engaged on a private answer that greatest works for me. I need my bundle growth and its assessments to reside individually from any particular shopper app exterior a testbed. I want to make sure that my code will swift construct and swift take a look at correctly however I additionally wish to use Xcode’s built-in compilation and unit testing with my glad inexperienced checks.
I set out to determine how greatest, no less than for me, to develop Swift packages underneath the xcodeproj umbrella.
I first explored swift bundle generate-xcodeproj. This builds an Xcode library undertaking full with assessments and a bundle goal. You should use the --type flag to set the bundle to executable, system-module, or manifest as a substitute of the default (library) throughout swift bundle init:
Generate% swift bundle init Creating library bundle: Generate Creating Package deal.swift Creating README.md Creating .gitignore Creating Sources/ Creating Sources/Generate/Generate.swift Creating Assessments/ Creating Assessments/LinuxMain.swift Creating Assessments/GenerateTests/ Creating Assessments/GenerateTests/GenerateTests.swift Creating Assessments/GenerateTests/XCTestManifests.swift Generate% swift bundle generate-xcodeproj generated: ./Generate.xcodeproj
Though SwiftPM creates a .gitignore file for you as you see, it doesn’t initialize a git repository. Additionally, I all the time find yourself deleting the .gitignore as I take advantage of a personalized world ignore file. That is what the ensuing undertaking seems like:

As you see, the generated Xcode undertaking has the whole lot however a testbed for you. I actually like having an on-hand testbed, whether or not a easy SwiftUI app or a command line utility to play with concepts. I regarded into utilizing a playground however let’s face it: too sluggish, too glitchy, too unreliable.
It’s a ache so as to add a testbed to this set-up, so I got here up with a distinct technique to construct my base bundle surroundings. It’s hacky however I a lot desire the end result. As a substitute of producing the undertaking, I begin with a testbed undertaking after which create my bundle. This strategy naturally packs a pattern with the bundle however none of that pattern leaks into the bundle itself:

I find yourself with three targets: the pattern app, a library constructed from my Sources, and my assessments. The library folder you see right here accommodates solely an Data.plist and a bridging header. It in any other case builds from no matter Sources I’ve added.
I a lot desire this set-up to the generate-xcodeproj strategy, though it takes barely longer to set-up. The explanation for that is that SwiftPM and Xcode use completely different philosophies for the way a undertaking folder is structured. SwiftPM has its Sources and Assessments. Xcode makes use of a supply folder named after the undertaking.
So I take away that folder, add a Sources group to the undertaking, and be sure that my construct phases sees and compiles these recordsdata. The Assessments want related tweaks, plus I’ve so as to add a symbolic hyperlink from Xcode’s assessments identify (e.g. “ProjectNameAssessments”) to my SwiftPM Assessments folder on the prime degree of my undertaking to get it to all dangle collectively. As soon as I’ve achieved so my inexperienced checks are prepared and ready simply as if I had opened the Package deal.swift file instantly. However this time, I’ve all the precise instruments at hand.
Since I’m speaking about set-up, let me add that my duties additionally embrace organising the README, including a license and creating the preliminary change log. These are SwiftPM setup duties that swift bundle init doesn’t cowl the way in which I like. I trash .gitignore however since I’ve Xcode set-up to routinely initialize model management, I don’t should git init by hand.
I believe it is a short-term workaround as I count on the combination of SwiftPM and Xcode to proceed rising over the following couple of years. Since WWDC, I’ve been notably enthusiastic about creating, deploying, and integrating SwiftPM packages. I assumed I’d share this in case it would assist others. Let me know.