Understanding the general value of palletizing options is a vital step within the resolution making course of. This weblog offers insights into the elements influencing this value, together with preliminary funding, ongoing bills, ROI, intangible advantages, and scalability issues.
Preliminary funding
There are various elements to think about with the preliminary automated palletizing resolution funding, so let’s begin with the quoting stage.
Finances pricing vs. quoted pricing
Make a transparent distinction between estimated (budgetary prices) and particular worth quotes. This strategy is essential to make sure a good and correct comparability of every different. Pay attention to the seller’s beneficial price range contingency or the additional room they suggest as a precautionary measure to accommodate extra prices.
Important vs. nice-to-have options
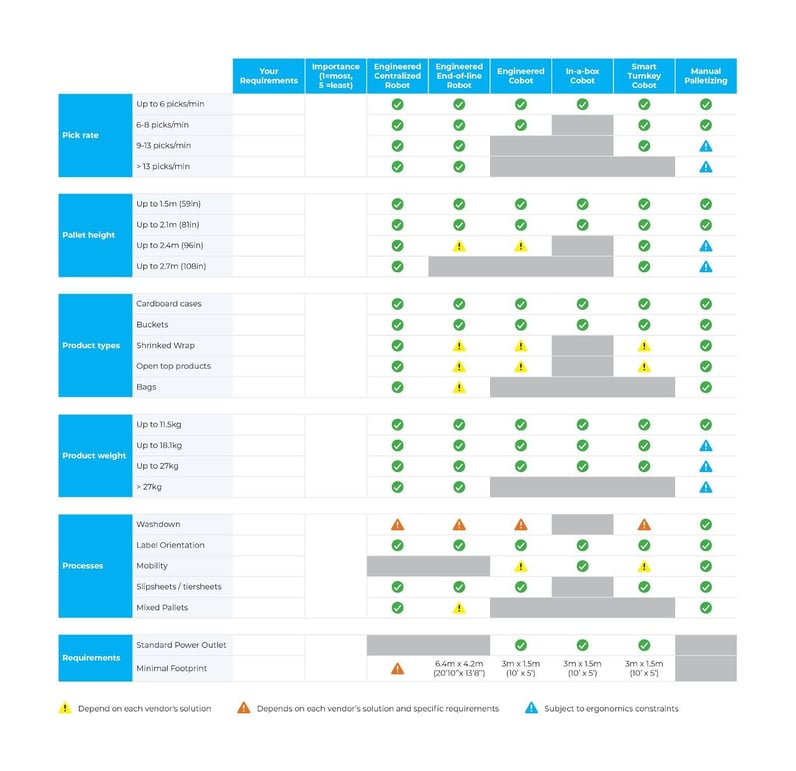
The Robotiq Purchaser’s Information features a instrument to help in evaluating the wants of the palletizing course of and figuring out the importance of every requirement. Based mostly on these wants, sure resolution classes will change into obvious as potential candidates. This instrument is named the Detailed Specification Sheet and will be downloaded with this hyperlink. It is strongly recommended that this instrument is used previous to assessing system prices so it may be used as a reference.
Detailed Specification Sheet (from The Automated Palletizing Purchaser’s Information)
Integration
Sure automated palletizing options could require extra substantial (and maybe intricate) integration efforts. The extent to which an answer aligns with the present manufacturing unit processes, structure, and techniques is essential to grasp. Listed below are inquiries to ask the seller to assist kick begin that dialogue:
- Will the chosen platform mean you can automate different stations in your manufacturing unit or in sister firms?
- How nicely does the answer accommodate our present manufacturing unit structure?
- What stage of compatibility does the answer have with our present techniques?
- How intensive are the mixing efforts?
- Are there any conditions or modifications wanted in our present processes for profitable integration?
- Are you able to present examples of profitable integrations with related manufacturing unit setups?
Customization
If the answer doesn’t cowl the important options required for the palletizing software, there is perhaps extra customization prices. The preliminary customization prices needs to be thought of, in addition to the necessity for ongoing cost- of-ownership bills to keep up the system’s relevance and performance. This consists of extra customization bills over time because the system evolves and stays in operation. Referring to the Detailed Specs, bills related to every customization to include the important options needs to be thought of.
Vender lock-in
When assessing the preliminary value of palletizing options, the potential long-term prices and penalties of choosing the seller should even be thought of. Vendor lock-in could have an effect on adjustments, scalability, and different elements. Contemplating this within the assessment of the alternate options can have an effect on the price of possession portion of the ROI calculation.
Scalability
Lastly, you will need to take into account the scalability of an answer and the way it would possibly affect the price of possession. Listed below are some questions to think about:
- Does this resolution require a bigger upfront funding however then cut back the prices of subsequent upgrades?
- Does this resolution allow a modest funding and supply the likelihood to increase as wanted?
- Will it’s doable to scale the answer and increase its capability as the necessities evolve?
- What could be the improve prices?
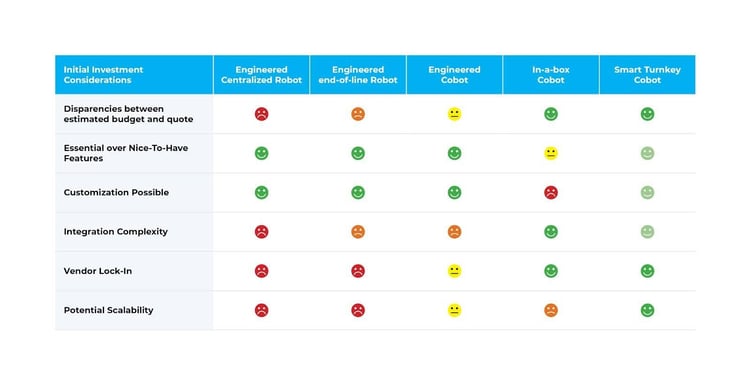
The next desk outlines the Preliminary Funding Issues for every resolution kind. These are relative representations between every class to help with choices.
Preliminary Funding Issues (from The Automated Palletizing Purchaser’s Information)
Working prices
The working prices for a robotic palletizer can fluctuate considerably relying on a number of elements:
- Vitality prices: Vitality prices depend upon system effectivity, runtime, and the native electrical energy charges.
- Upkeep and repairs: Common upkeep and repairs contribute to working prices. It is very important perceive who is permitted to carry out upkeep, proposed service contracts, and the way spare elements are bought. If doable, a present buyer of the seller can present insights from the person’s standpoint. The proposed upkeep and assist packages provided by the provider ought to meet the corporate’s expectations.
- Coaching prices: The price of coaching present and new workers on the system needs to be in contrast. Present clients can present a transparent view of the coaching expertise their crew acquired.
- Programming and software program updates: It is very important doc software program license prices and subscription prices. Equally as essential is clarifying the tasks for program additions and adjustments. Can present workers deal with these duties, or does it contain exterior people?
Sudden prices are irritating. Maintaining monitor of all potential bills will increase the chance of acquiring a extra correct estimate of the preliminary funding and working true prices.
ROI issues
Now, understanding the preliminary and possession prices from the earlier chapter, the logical subsequent step is to mission the Return on Funding (ROI).
The earlier monetary data needs to be supplemented with productiveness beneficial properties and labor influence data with the intention to evaluate with guide palletizing operations.
As a reference, listed here are a couple of funding calculations which might be used at this step:
ROI system: (Internet Achieve from Funding / Preliminary Funding Value) x 100
Internet acquire system: Financial savings in prices (labor, downtime, and so on.) + Extra income from elevated productiveness.
Quantifying productiveness beneficial properties:
- Cycle time: Period to finish a particular activity or produce an merchandise.
- Output: Variety of items processed per unit of time.
- Scalability: Skill to extend quantity with minimal extra value.
Quantifying influence on labor:
- Labor prices: Present guide labor prices, together with wages and advantages.
- Labor effectivity: Productiveness and effectivity of guide labor.
- Labor flexibility: Skill to reassign labor for numerous duties.
Value of possession
Any funding can have dangers. It is very important take into account them and have a mitigation plan in the event that they occur.
- Determine dangers: Potential dangers reminiscent of technological failures, market adjustments, or regulatory points.
- Danger mitigation: Doc methods to mitigate every threat and calculate the potential value related to mitigation.
- Embody a threat think about ROI comparability: Have a look at the manufacturing unit’s earlier, large-scale, cross- purposeful funding initiatives. Had been they on time and on price range? If not, add that threat issue to the ROI calculation for Centralized and Engineered options which might be of an identical nature.
Funding threat evaluation
These might not be clear numbers, however they’re qualitative beneficial properties that must be thought of within the resolution course of.
- Security: Lower prices related to office accidents, medical go away, accidents, and near-misses.
- Worker engagement: Consider the affect on workforce morale and the rise in worker retention.
- High quality enchancment: Calculate the discount of prices associated to errors.
- Market status: Estimate the constructive influence on the corporate’s status (each with clients and job candidates) for innovation and effectivity.
Conclusion
Understanding the value of palletizing options is essential for knowledgeable decision-making. This weblog has make clear numerous elements influencing prices, reminiscent of preliminary funding, integration, customization, vendor lock-in, and scalability. It has emphasised the significance of distinguishing between budgetary estimates and particular worth quotes, in addition to contemplating long-term working bills and ROI calculations. Furthermore, the dialogue on intangible advantages highlights the broader impacts past monetary metrics, together with security enhancements, worker engagement, high quality enhancement, and market status.
By fastidiously analyzing these monetary issues, companies could make strategic investments in palletizing options that align with their operational objectives and ship long-term worth.
Obtain the Robotiq Automated Palletizing Purchaser’s Information or extra instruments, useful suggestions, and tangible assets.
Prepared to begin? Speak with considered one of our palletizing consultants.