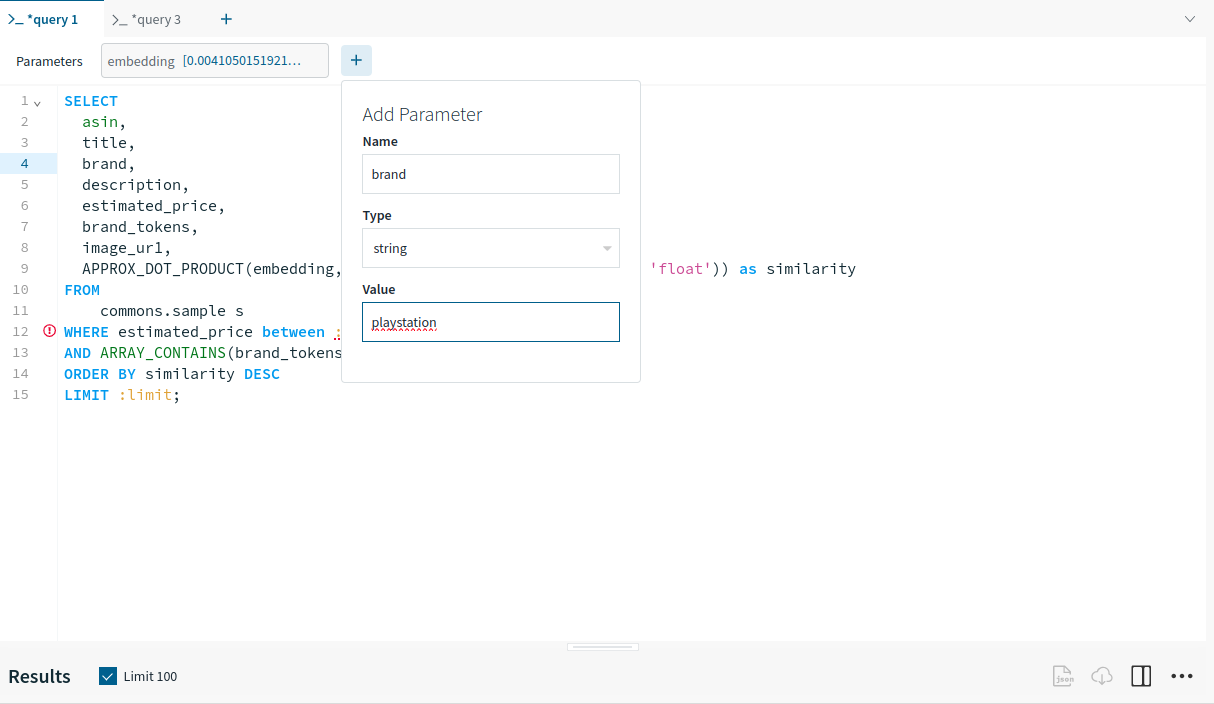
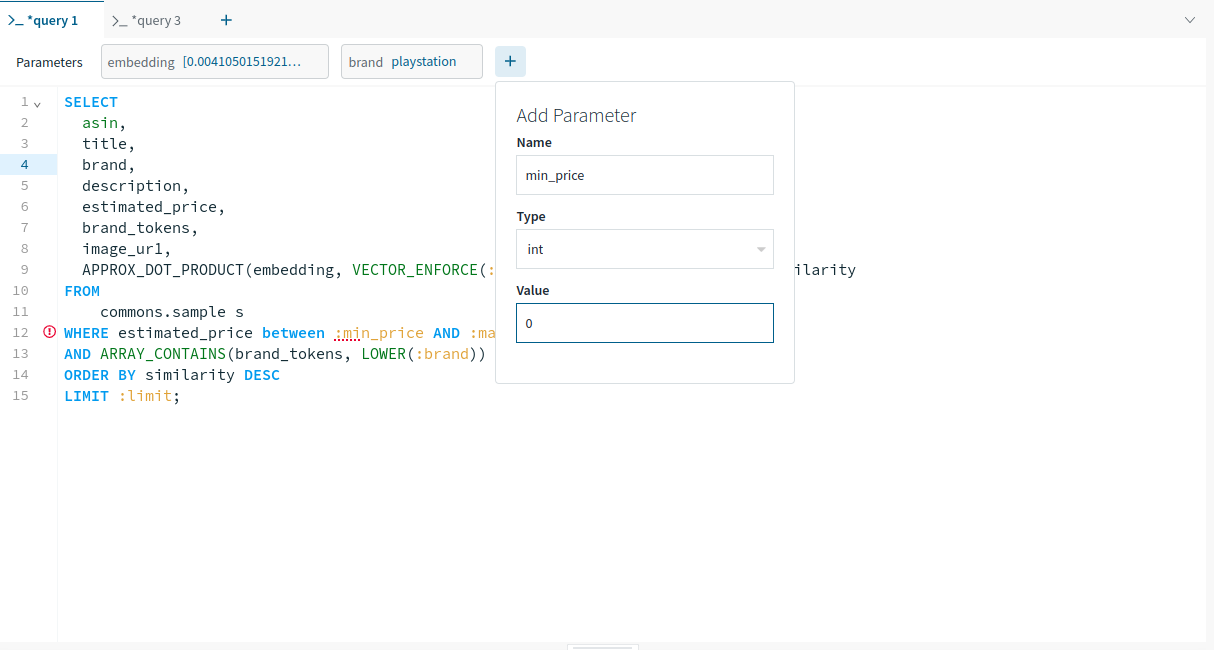
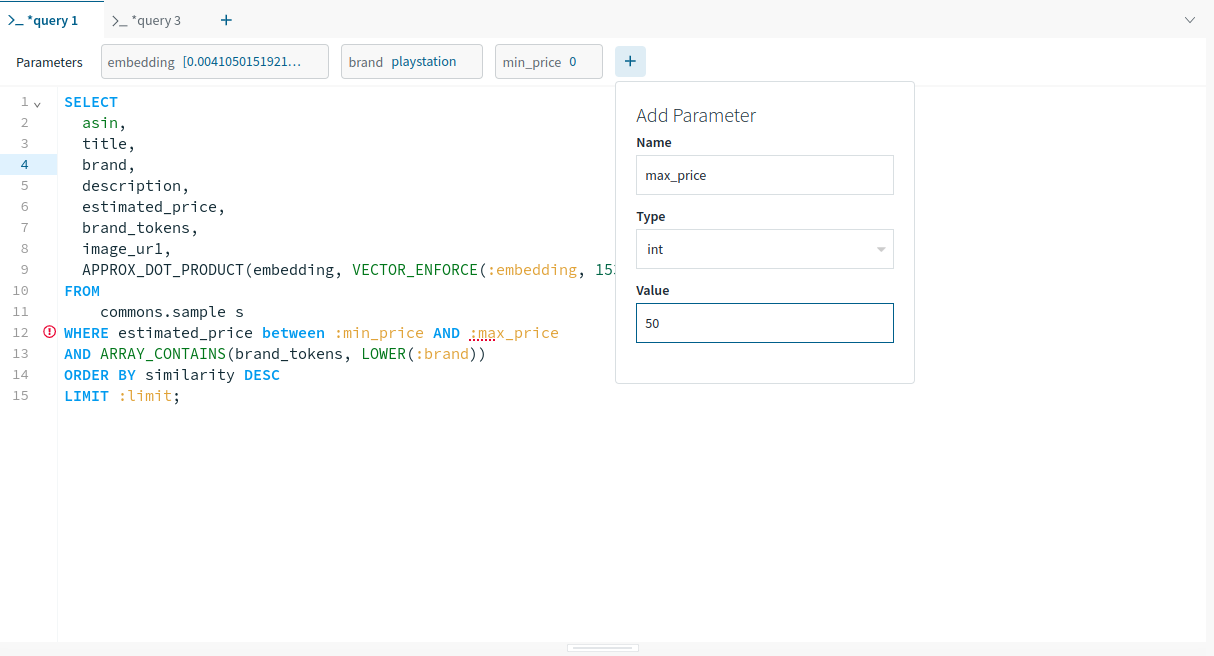
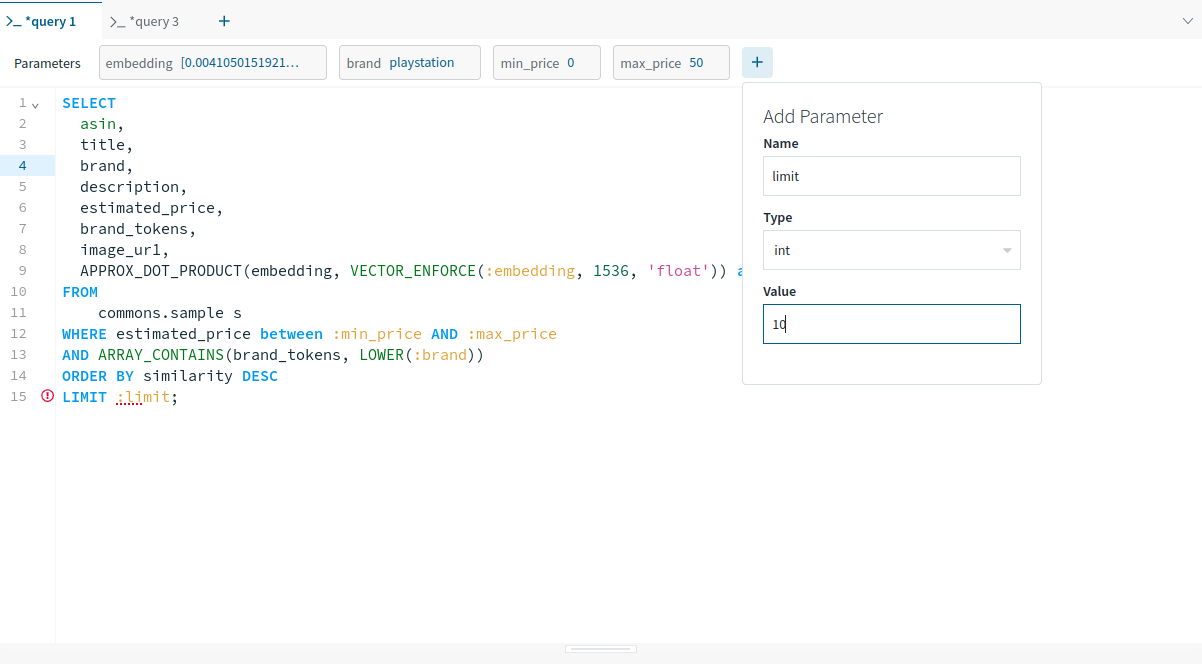
As Apple gears as much as launch new iPhones later in 2024, there’s a brand new iPhone replace coming to all iPhones from the iPhone XR up: iOS 18.
On the WWDC 2024 keynote on June 10, Apple unveiled the brand new iPhone options coming in iOS 18. Amongst them are a redesigned Pictures app, new methods to customise your House display and wallpaper, new Messages reactions, privacy-related options and dozens of different smaller modifications.
This free software program replace will convey a raft of interface tweaks, bug fixes, and new options. It’s like getting a brand new iPhone with out paying a penny. On this article, we talk about every thing it’s essential to find out about iOS 18, together with when iOS 18 is popping out, which iPhones will be capable to run iOS 18, the options which might be coming within the new OS, and those that received’t be prepared in time for the launch of iOS 18.
Up to date August 20: The seventh beta of iOS 18 is now obtainable for builders and public beta testers.
iOS 18 launch date – when does iOS 18 come out?
iOS 18 is prone to arrive within the week of Monday, September 16, 2024, though Apple is but to substantiate the discharge date. We imagine Apple will reveal the discharge date throughout a September Apple Occasion on or round 10 September.
In 2023 iOS 17 arrived on Monday, September 18, 2023, so we count on an identical timing for 2024.
Over the previous a number of years, the discharge of the brand new model of iOS has been pretty constant, often falling on the Monday following Apple’s iPhone launch occasion:
- iOS 17: Monday, September 18, 2023
- iOS 16: Monday, September 12, 2022
- iOS 15: Monday, September 20, 2021
- iOS 14: Wednesday, September 16, 2020
- iOS 13: Thursday, September 19, 2019
- iOS 12: Monday, September 17, 2018
As soon as the ultimate launch comes out, putting in iOS 18 can be a breeze. Open the Settings app in your iPhone and go to Normal > Software program Replace; iOS will examine for any obtainable updates and information you thru the method of putting in them. You merely need to observe the directions, which we clarify in our iOS updating information. And it’s simpler nonetheless in case you’ve turned on Computerized Updates, which you are able to do from the identical display.
iOS 18 beta: newest model of the developer beta/public beta
- iOS 18 beta 7 – developer beta launched August 20
- iOS 18.1 beta 2 – developer beta up to date August 12
Apple started the beta program quickly after it revealed the main points of iOS 18 at WWDC. The developer beta is on the market for anybody who desires to run the beta, but it surely ought to be famous betas–particularly developer betas–are prone to be buggy, so we don’t advocate putting in it on a major gadget. Learn: Methods to set up the iOS beta in your iPhone.
Apple began parallel growth of iOS 18.1 on July 29 with the discharge of the iOS 18.1 beta to builders with supported {hardware} (iPhone 15 Professional and Professional Max). This model consists of Apple Intelligence options which received’t be obtainable within the preliminary launch of iOS 18. See: Every thing Apple Intelligence can (and may’t) do in iOS 18.1.
Because of this, there are a number of variations of the iOS 18 beta: A developer beta of iOS 18, a developer beta of iOS 18.1, and a public beta of iOS 18, however not of iOS 18.1.
The newest developer betas are iOS 18 beta 6 and iOS 18.1 beta 2, each launched on August 12. iOS 18.1 beta 2 features options that have been in iOS 18 beta 5. iOS 18 beta 6 provides extra tweaks the Pictures app, a brand new Bluetooth management for Management Middle, and quite a lot of “what’s new” splash screens.
The newest public beta is iOS 18 beta 4. It was launched on the identical day because the developer beta, iOS 18 beta 6, which is uncommon as there may be often a day or extra between releases. There are modifications to the Music app, a brand new technique to entry Bluetooth controls, and a few new splash screens (app launch screens).
The beta testing will proceed even after Apple releases iOS 18 to most of the people as Apple develops new options not obtainable at launch.
For those who’d like to affix the beta for the subsequent model of iOS learn this: Methods to be part of Apple’s beta program and check out new software program. If you wish to take away the beta out of your gadget learn this: Methods to take away an iOS beta out of your iPhone.
Methods to set up the iOS beta
If you wish to set up a developer beta, you want, unsurprisingly, to be a registered Apple software program developer, which has each free and paid ($99/£79) variations. Since June 2023 Apple has opened the beta to all registered builders–so everybody can get the earliest doable entry to the iOS 16 beta. To join an account and set up the developer beta you want solely observe these steps:
- Obtain the Apple Developer App from the App Retailer.
- Open the app and click on on Account.
- Faucet on Signal In and sign up utilizing your standard Apple ID.
As soon as you might be logged in it is best to see the beta in Normal > Software program Replace > Beta Updates. You might want to be operating iOS 16.5 or later for this to work.
We cowl this course of in additional element in our Methods to get the iOS beta article. If you wish to take away the iOS 18 beta learn: Methods to take away an iOS beta out of your iPhone.
Must you set up the iOS 18 beta? Our recommendation is that quite than putting in the developer beta it is best to set up the general public beta to keep away from too many issues.
Learn Methods to be part of Apple’s beta program for extra recommendation.
iOS 18 compatibility: Which iPhones get iOS 18?
The next iPhones get assist for iOS 18, the identical lineup of supported units as iOS 17.
- iPhone 15, iPhone 15 Plus, Professional, Professional Max
- iPhone 14, iPhone 14 Plus, Professional, Professional Max
- iPhone 13, iPhone 13 mini, Professional, Professional Max
- iPhone 12, iPhone 12 mini, Professional, Professional Max
- iPhone 11, iPhone 11 Professional, Professional Max
- iPhone XS, iPhone XS Max
- iPhone XR
- iPhone SE (2nd gen or later)
Learn: iOS 18 compatibility: Which iPhones assist iOS 18
It’s doubtless that among the coolest new options is not going to be supported on the older telephones, as a result of they lack the {hardware} needed (a robust sufficient Neural Engine or GPU to run AI stuff, or sufficient RAM). That is typical of recent iOS releases. In 2022, for instance, the iPhone 8 and iPhone X missed out on a bunch of cool stuff resulting from their older processor.
It’s no shock, subsequently, that the {hardware} necessities are steep for the AI-related options—iPhone 15 Professional or later.
iOS 17 didn’t assist iPhone 8 or the iPhone X which got here out in 2017, however since these telephones are capable of run iOS 16, they are going to proceed to get assist by safety updates for at the very least one other yr. With the discharge of iOS 18 although, Apple might cease supporting iOS 15, which is able to imply that iPhone 7, 7 Plus, iPhone 6S, 6S Plus, and iPhone SE (1st era) will now not get assist.
Usually, Apple has offered software program updates for the previous two variations of iOS. See: How lengthy does Apple assist iPhones.
Examine: How iOS 17 and iOS 18 evaluate.
iOS 18 options: new options coming in iOS 18
There have been many new options in iOS 17 together with a brand new app known as Journal, Reside Voicemail, and a brand new manner to make use of Stickers, amongst dozens of different smaller modifications. Rumors urged that iOS 18 can be “one of many greatest iOS updates — if not the most important — within the firm’s historical past.” It was anticipated that Apple would showcase some main new AI options. The {hardware} necessities are anticipated to be steep—iPhone 15 Professional or later.
Not all the brand new options can be obtainable at launch. Some options, comparable to the brand new classes in Mail, will come “later this yr” in a subsequent software program replace. Learn: These options can be lacking when iOS 18 launches this fall.
Customization
There can be a extra customizable House Display screen, Lock Display screen, and Management Middle in iOS 18.
A number of studies had claimed that Apple would permit higher personalization of the House display, together with permitting customers to put icons wherever on the grid, permitting areas between them. Presently, icons might be reordered or put into folders, however all the time fill the display from left to proper and prime to backside.
In iOS 18 customers will be capable to prepare apps and widgets wherever on the House Display screen, together with proper above the dock or framing a wallpaper. It should even be doable to alter the lock display icons or take away them.
As well as, App icons and widgets can have a darkish or tinted impact to mix in. Learn: iOS 18: Methods to change the colour of the app icons on your own home display and Methods to put app icons, widgets, and folders wherever you need in addition to iOS 18: Methods to make your app icons giant and label-free.
This “put icons wherever you need” function is one thing we’ve needed from Apple for a few years, and has been a staple of many Android telephones seemingly perpetually.
The Management Centre is getting a redesign to provide simpler entry to a person’s most-utilized controls. Customers may also be capable to add controls from supported third-party apps into Management Middle.
Is it sufficient? Learn: Apple is lastly letting you have got it your manner–kinda.
Pictures
New options in Pictures will assist customers discover their images and preserve massive libraries organized. It’s the most important redesign of Pictures ever and is meant to assist customers discover images quick. It is going to be simplified however nonetheless acquainted, based on Apple and can embody a brand new Unified View, new Collections, and customization options.
Customers will be capable to filter out muddle to slender all the way down to particular kinds of content material. It is going to be doable to browse by subjects, time, folks, reminiscences, journeys, Latest Days and Individuals and Pets.
A brand new carousel view will current highlights that replace every day – that includes favourite folks, pets, and locations.
Messages
Messages will achieve new methods to specific your self. Count on enhancements to textual content formatting and enjoyable new textual content results. Tapbacks are getting redesigned and can allow you to faucet again with any emoji or sticker. You’ll additionally be capable to amplify and animate letters, phrase, phrases, and emoji, and add formatting like daring, underline, italics, and strikethrough.
Additionally, you will be capable to schedule a message to ship later.
Messages may also assist RCS for extra dependable group messaging with those that should not have an Apple gadget. Examine how your conversations with Android customers will look in iOS 18 and RCS on iPhone with iOS 18: Each query answered.
Apple can be making it doable to ship Messages by way of Satellite tv for pc so you’ll be able to textual content when off the grid from Messages app. iMessages despatched over satellite tv for pc are encrypted.
Mail
Mail will enable you handle incoming electronic mail higher with new on-device categorization. As electronic mail arrives it will likely be sorted into Main (private and time-sensitive), Transactions (confirmations and receipts), Updates (information and social notifications), and Promotions (advertising and marketing and coupons).
A brand new Digest will pull collectively all related emails from a enterprise, so for instance, it may convey all flight info collectively.
The Mail Categorization options can be obtainable later this yr.
Safari
A brand new Highlights function is designed to make it simpler to find info on the internet.
A redesigned Reader expertise will use machine studying to floor key info on a webpage in order that customers can evaluation a abstract to get the gist of an article. A desk of contents can be included for longer articles
Apple says customers may also be capable to shortly see the situation of a restaurant, resort, or landmark; or hearken to an artist’s observe proper from an article concerning the music or album.
Pockets and Apple Pay
There can be new methods to pay with Apple Pay. Customers can ship and obtain Apple Money by holding two iPhones collectively: Faucet to Money will allow you to share money with out exchanging electronic mail or quantity.
Tickets in Apple Pockets together with key occasion info like an occasion information with information concerning the venue, and really helpful Apple Music playlists
iPhone mirroring on the Mac
iPhone Mirroring will grant customers entry to their iPhone by way of their Mac. It is going to be doable to see notifications from the iPhone on the Mac, and drag and drop recordsdata between the units.
Learn: How iPhone Mirroring allows you to entry your iPhone in your Mac in macOS Sequoia.
Different app updates:
- Journal – New options that can assist you preserve observe of targets, Insights view, calendar, writing streak, and truly search
- Maps – New topographic maps with trails (US nationwide parks solely)
- Recreation Mode – Will reduce background exercise for the very best body charges
- Notes app – formulation and equations entered whereas typing can be solved
- Calendar – incorporates duties from Reminders and a brand new month-to-month view
- Well being app – Medical ID redesigned
- Emergency SOS Reside Video
- House app – visitor entry
- Accessibility – Eye Monitoring
- iCloud – Apple is including a “Preserve Downloaded” choice that stops the file from being moved to iCloud and retains the file on the gadget. Learn concerning the new Preserve Downloaded choice.
Apple didn’t talk about every thing at WWDC. There have been a variety of options that didn’t make the WWDC keynote.
Additionally see: Unannounced iOS 18 tweak allows you to see the time even when your iPhone is useless.
Privateness options
iOS 18 will enhance privateness. It is possible for you to to manage who can see your apps, which contacts you share with that app, and which equipment apps can connect with.
It’s also possible to management whether or not others can view your apps in your iPhone by locking an app so it received’t open with out Face ID or a passcode. A brand new locked hidden apps folder can be coming with iOS 18.
Builders may have a technique to seamlessly join third-party equipment with iPhones with out letting an app see all the opposite units on a person’s community.
Apple Intelligence
Apple’s new synthetic intelligence system is coming to iPhone, Mac, and iPad with iOS 18, macOS Sequoia, and iPadOS 18. Apple Intelligence will solely be supported by iPhone 15 Professional and iPhone 15 Professional Max although. (Right here’s why you’ll must improve your iPhone to get Apple Intelligence, additionally learn: Right here’s why newer iPhones and Imaginative and prescient Professional can’t run Apple Intelligence).
The {hardware} necessities are steep—iPhone 15 Professional or later. iPads will want at the very least an M1 chip or later as will Macs. Apple Intelligence options will largely be processed on the gadget, which is completely different from different platforms the place AI processing is completed within the cloud. However Apple Intelligence will be capable to decide if cloud processing is required and can use it when applicable.
Apple Intelligence options embody the next:
Writing – Apple Intelligence will assist customers improve their writing and communications. Writing Instruments are inbuilt systemwide that may provide to rewrite, proofread, and summarize textual content in writing targeted apps comparable to Mail, Notes, Pages, and third-party apps.
Pictures – New picture capabilities may also come to M-series Macs. In Picture Playground customers will be capable to create photos in three kinds: Animation, Illustration, or Sketch.
Pictures – A brand new Reminiscences in Pictures function will create a video from images and movies primarily based on an outline offered by the person. Apple Intelligence will select the images and movies, develop a storyline primarily based on the images, and prepare them right into a film. As well as, a brand new Clear Up software will establish and take away undesirable objects from the background of a photograph.
Learn: Apple Intelligence FAQ: What it’s, what it does, and while you’ll get it
Siri
Siri can be getting some AI updates and ChatGPT is to be built-in into Siri. As a result of some queries can be dealt with off-device Apple is introducing Non-public Cloud Compute in order that when knowledge is shipped to server-based fashions for processing it’s not saved or made accessible to Apple.
One of many easiest modifications to Siri is that it will likely be simpler to sort to Siri quite than having to talk to the on-device assistant. Apple might have lastly twigged that folks don’t all the time need to speak to their telephones.
The brand new Siri is alleged to be extra “conversational” and pure, with options that “assist customers of their day-to-day lives.”
A brand new sensible responses framework will assist Siri have in mind your personal private particulars in its replies: like folks, corporations, calendar occasions, areas, dates, and extra.
Later this yr, Siri is alleged to get cross-device media management. So you’ll be able to speak to Siri on one in all your units to manage media playback on one other.
In an replace scheduled for early 2025, Siri is alleged to realize the flexibility to manage almost any app, with lots of of doable instructions. This function will begin off with single instructions for Apple’s personal apps and develop to incorporate third-party apps and instructions with a number of steps. As well as, Siri will be capable to react to and take actions primarily based on what’s in your display. That is mentioned to enter beta for builders in January, with a rollout to customers in iOS 18.4 within the spring.
New accessibility options
Apple is planning a number of new accessibility options for iOS 18, together with Adaptive Voice Shortcuts, which is able to let customers activate or off particular accessibility options utilizing a customized phrase, and Reside Speech, which lets customers sort what they need to say and have it learn out loud on telephone calls or video conferences, will get the flexibility so as to add saved phrases to classes.
Options coming after the iOS 18 launch
Some iOS 18 options received’t be part of the preliminary launch. Reasonably, they are going to be launched later in 2024 or in 2025 as a part of an iOS 18 level launch (iOS 18.2 or iOS 18.4, for instance).
Listed here are among the extra vital options we count on to come later in an iOS 18 replace:
Mail app options – Auto-categorizing of mail, mail digests, and summaries in your inbox are all options anticipated later in 2024.
House assist for robotic vacuums – The House app received’t be capable to begin or cease your Roomba till later in 2024.
Drag and Drop between iPhone and Mac – You’ll be capable to see and management your iPhone in your Mac when iOS 18 and macOS 15 are launched, however drag-and-drop assist between your Mac and iPhone will are available an replace.
ChatGPT integration – The power to name upon ChatGPT when utilizing Apple’s AI instruments will doubtless come later in 2024.
Superior Siri options – Siri options like its potential to see and react to what’s in your show, semantic indexing (the place Siri is aware of and makes use of info from throughout Messages, Mail, Contacts, and extra), and superior management over apps is all coming in 2025.
As well as, the entire Apple Intelligence options will initially assist solely American English, and could also be restricted to just some areas. Extra languages and areas are prone to be obtainable by 2025 and past.