Join each day information updates from CleanTechnica on e-mail. Or observe us on Google Information!
In line with our newest Preliminary Month-to-month Electrical Generator Stock, builders and energy plant house owners added 20.2 gigawatts (GW) of utility-scale electrical producing capability in america in the course of the first half of 2024. This new capability is 3.6 GW (21%) greater than the capability added in the course of the first six months of 2023. Based mostly on essentially the most lately reported information, builders and house owners count on so as to add one other 42.6 GW of capability within the second half of the yr.
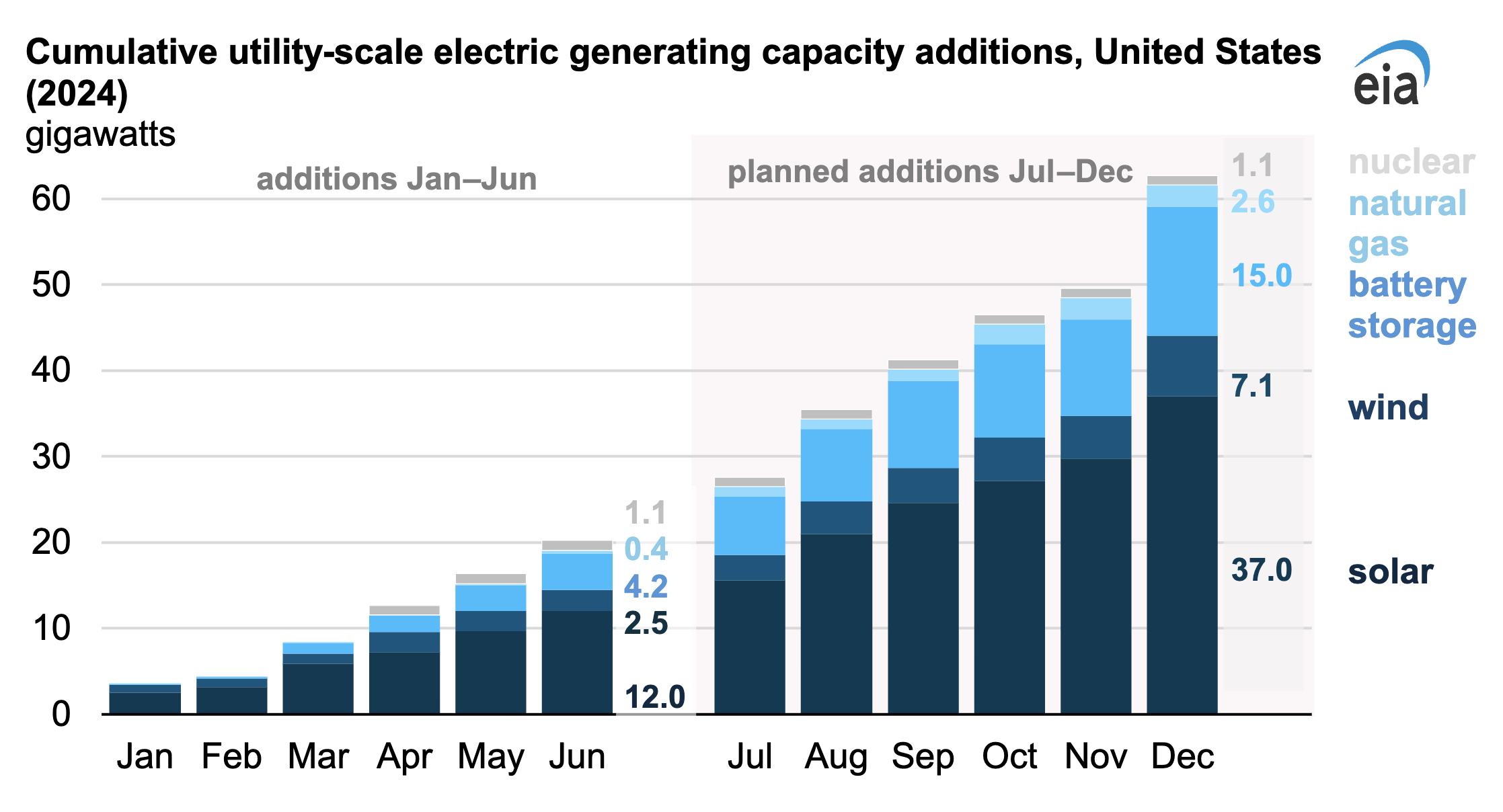
Operational capability additions: As in 2023, photo voltaic accounted for the most important share of newly working producing capability in america in the course of the first half of 2024. Photo voltaic additions totaled 12 GW, 59% of all additions. Texas and Florida made up 38% of U.S. photo voltaic additions. The 690-megawatt (MW) photo voltaic and storage Gemini facility in Nevada and the 653-MW Lumina Photo voltaic Challenge in Texas had been the most important photo voltaic tasks that got here on-line within the first six months of 2024.
The second-most capability additions thus far this yr had been battery storage, which made up 21% (4.2 GW). Battery additions had been concentrated in 4 states: California (37% of the U.S. complete), Texas (24%), Arizona (19%), and Nevada (13%). The 380-MW battery storage capability at Gemini and the 300-MW Eleven Mile Photo voltaic Middle in Arizona had been the 2 largest tasks that got here on-line within the first half of 2024.
Wind energy made up 12% (2.5 GW) of U.S. capability additions. Canyon Wind (309 MW) and Goodnight (266 MW), each positioned in Texas, had been the most important wind tasks that got here on-line within the first half of the yr.
Nuclear energy elevated in america throughout 2024 as effectively. Unit 4 (1,114 MW) at Georgia’s Vogtle nuclear energy plant started industrial operations in April, making Vogtle the most important nuclear facility in america and the one one with 4 nuclear energy reactors.
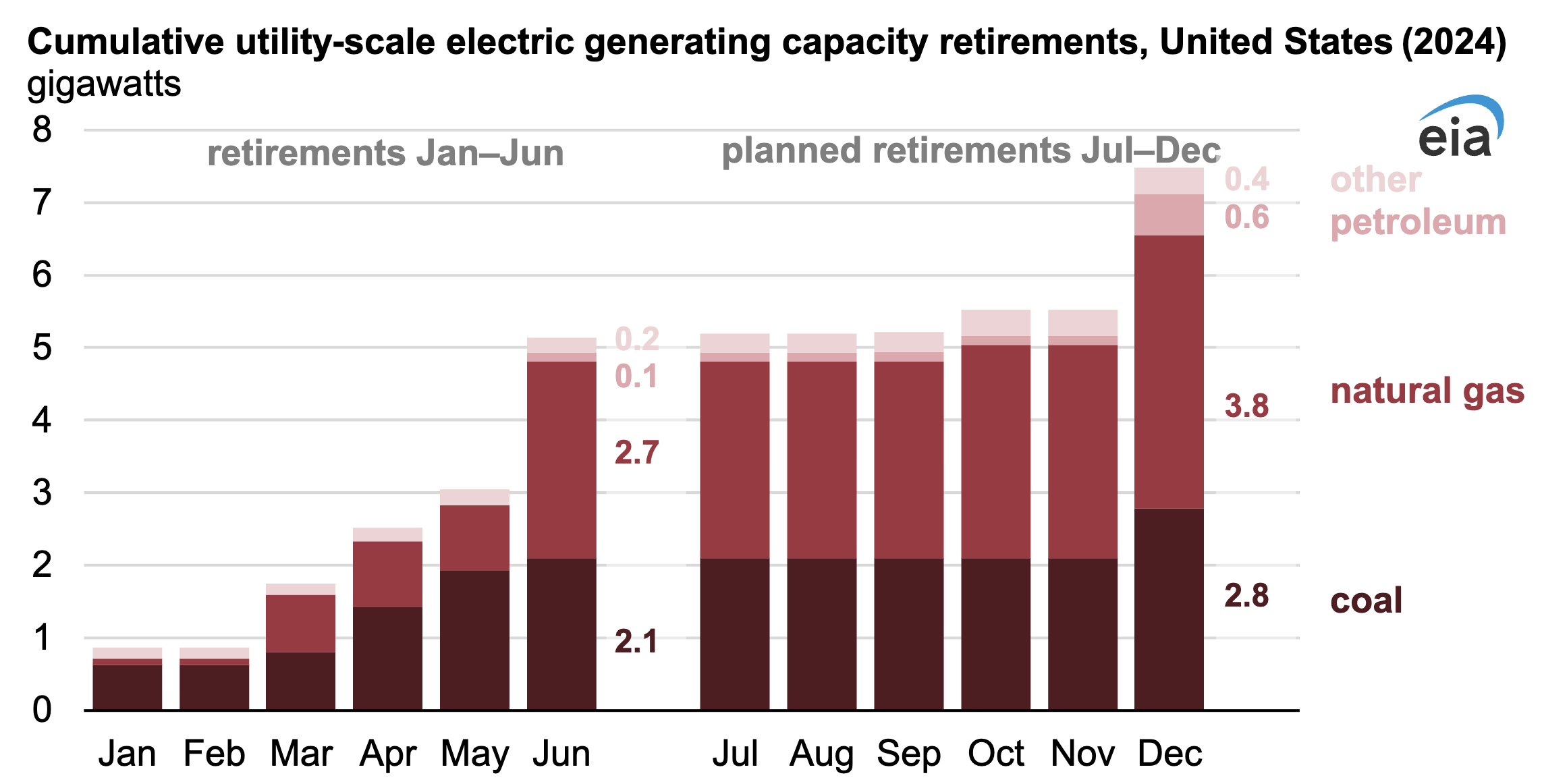
Retired capability: Retirement of U.S. electrical producing capability has slowed in 2024. Operators retired 5.1 GW of producing capability within the first half of the yr. In the course of the first six months of 2023, operators retired 9.2 GW of era. Within the first half of 2024, greater than half (53%) of the retired capability had used pure fuel as its gas, adopted by coal at 41%.
The most important U.S. coal retirements embrace Seminole Electrical Cooperative’s Unit 1 (626.0 MW) in Florida, which retired in January, and Homer Metropolis Producing Station’s Unit 1 (626.1 MW) in Pennsylvania, which retired in April. The six-unit, 1,413-MW Mystic Producing Station combined-cycle facility in Massachusetts was the most important pure fuel retirement this yr and had been the third-largest energy plant in New England.
Plans for adjustments in capability: Builders plan so as to add 42.6 GW of recent capability in america within the second half of 2024. Almost 60% of that deliberate capability is from photo voltaic (25 GW), adopted by battery storage (10.8 GW) and wind (4.6 GW).
If utilities add all of the photo voltaic capability they’re at present planning, photo voltaic capability additions will complete 37 GW in 2024, a document in anybody yr and virtually double final yr’s 18.8 GW.
Utilities may additionally add a document quantity of battery storage capability this yr (15 GW) if all deliberate additions come on-line. Plans for storage capability in Texas and California at present account for 81% of recent battery storage capability within the second half of the yr.
About 2.4 GW of capability is scheduled to retire in the course of the second half of 2024, together with 0.7 GW of coal and 1.1 GW of pure fuel.
Initially printed on As we speak in Vitality. Principal contributor: Suparna Ray
Have a tip for CleanTechnica? Need to promote? Need to counsel a visitor for our CleanTech Discuss podcast? Contact us right here.
Newest CleanTechnica.TV Movies
CleanTechnica makes use of affiliate hyperlinks. See our coverage right here.
CleanTechnica’s Remark Coverage

















.png)