Generative AI (GenAI) is making waves the world over. Its reputation and widespread use has additionally attracted the eye of cybercriminals, resulting in numerous cyberthreats. But a lot dialogue round threats related to instruments like ChatGPT has targeted on how the know-how will be misused to assist fraudsters create convincing phishing messages, produce malicious code or probe for vulnerabilities.
Maybe fewer persons are speaking about the usage of GenAI as a lure and a Computer virus wherein to cover malware. Examples will not be too tough to come back by. Final yr, for example, we wrote a few marketing campaign that urged Fb customers to check out the newest model of Google’s official AI instrument “Bard”; as a substitute, the adverts served a malicious imposter instrument.
Such campaigns are examples of a worrying development, they usually’re clearly not going anyplace. It’s, due to this fact, key to grasp how they work, study to identify the warning indicators, and take precautions in order that your identification and funds aren’t in danger.
How are the dangerous guys utilizing GenAI as a lure?
Cybercriminals have numerous methods of tricking you into putting in malware disguised as GenAI apps. These embody:
Phishing websites
Within the second half of 2023, ESET blocked over 650,000 makes an attempt to entry malicious domains containing “chapgpt” or comparable textual content. Victims almost definitely arrive there after clicking via from a hyperlink on social media, or through an electronic mail/cell message. A few of these phishing pages could include hyperlinks to put in malware disguised as GenAI software program.
Net browser extensions
ESET’s H1 2024 menace report particulars a malicious browser extension which customers are tricked into putting in after being lured by Fb adverts promising to take them to the official web site of OpenAI’s Sora or Google’s Gemini. Though the extension masquerades as Google Translate, it’s really an infostealer often known as “Rilide Stealer V4,” which is designed to reap customers’ Fb credentials.
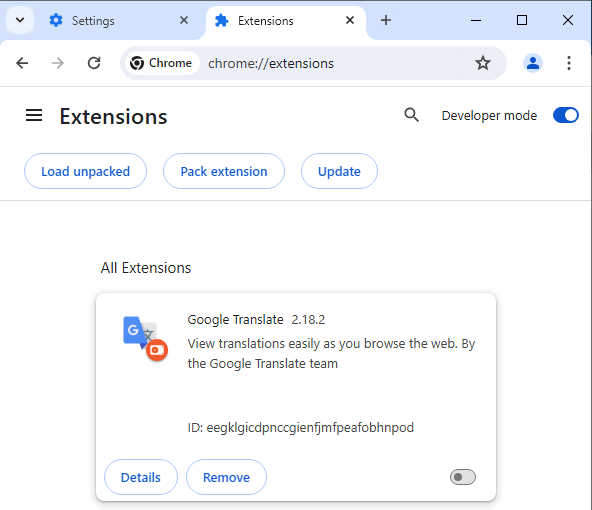
Since August 2023, ESET telemetry recorded over 4,000 makes an attempt to put in the malicious extension. Different malicious extensions declare to supply GenAI performance, and may very well accomplish that in a restricted type, in addition to ship malware, in accordance with Meta.
Pretend apps
There have additionally been numerous stories of faux GenAI apps posted particularly to cell app shops, with many of those apps containing malware. Some are laden with malicious software program designed to steal delicate info from the person’s system. This could embody login credentials, private identification particulars, monetary info, and extra.
Others are scams designed to generate income for the developer by promising superior AI capabilities, typically for a payment. As soon as downloaded, they could bombard customers with adverts, solicit in-app purchases, or require subscriptions for providers which can be both non-existent or of extraordinarily poor high quality.
Malicious adverts
Malicious actors are using the recognition of GenAI instruments to trick customers into clicking on malicious promoting. Malicious Fb adverts are notably prevalent. Meta warned final yr that many of those campaigns are designed to compromise “companies with entry to advert accounts throughout the web.”
Risk actors hijack a official account or web page, change the profile info to make it seems as if an genuine ChatGPT or different GenAI-branded web page, after which use the accounts to run faux adverts. These provide hyperlinks to the newest model of GenAI instruments, however in actuality deploy infostealer malware, in accordance with researchers.
The artwork of the lure
People are social creatures. We wish to imagine the tales we’re instructed. We’re additionally covetous. We wish to pay money for the newest devices and apps. Risk actors exploit our greed, our concern of lacking out, our credulity and our curiosity to get us to click on on malicious hyperlinks or obtain apps with malware hidden inside.
However for us to hit that set up button, what’s on provide needs to be fairly head turning, and – like all the perfect lies – it needs to be grounded in a kernel of fact. Social engineers are notably adept at mastering these darkish arts – persuading us to click on on salacious information tales about celebrities, or present affairs (keep in mind these tall tales about faux COVID-19 vaccines?). Generally they’ll provide us one thing at no cost, at an unbelievable low cost, or earlier than anybody else will get it. As we defined right here, we fall for these tips as a result of:
- We’re in a rush, particularly if we’re viewing the content material on our cell system
- They’re good storytellers, and are more and more fluent, utilizing (mockingly) GenAI to inform their tales seamlessly in a number of languages
- We like to get one thing for nothing, even when it’s too good to be true
- The dangerous guys are good at sharing data on what works and what doesn’t, whereas we’re much less good at in search of out or taking recommendation
- We’re hardwired to respect authority, or at the very least the legitimacy of a proposal, so long as it’s “formally” branded
With regards to GenAI, malware-slingers are getting more and more refined. They use a number of channels to unfold their lies. They usually’re disguising malware as every little thing from ChatGPT and video creator Sora AI, to picture generator Midjourney, DALL-E and photograph editor Evoto. Lots of the variations they tout aren’t but out there, which pulls within the sufferer: “ChatGPT 5” or “DALL-E 3” for instance.
They guarantee malware continues to fly underneath the radar by usually adapting their payloads to keep away from detection by safety instruments. They usually take quite a lot of effort and time to make sure their lures (similar to Fb adverts) look the half. If it doesn’t look official, who’s going to obtain it?
What could possibly be in danger?
So what’s the worst that might occur? In the event you click on to obtain a faux GenAI app in your cell or an internet site and it installs malware, what’s the tip purpose for the dangerous guys? In lots of instances it’s an info-stealer. These items of malware are designed, because the identify suggests, to reap delicate info. It may embody credentials on your on-line accounts, similar to work log-ins, or saved bank cards, session cookies (to bypass multifactor authentication), property saved in crypto wallets, information streams from immediate messaging apps, and far more.
It’s not nearly info-stealer malware, in fact. Cybercriminals may theoretically disguise any sort of malware in apps and malicious hyperlinks, together with ransomware and distant entry Trojans (RATs). For the sufferer, this might result in:
- A hacker gaining full distant management over your PC/cell phone and something saved on it. They may use entry to steal your most delicate private and monetary info, or flip your machine right into a “zombie” laptop to launch assaults on others
- They may use your private info for identification fraud which will be extraordinarily distressing, to not point out costly, for the sufferer
- They may use monetary and identification particulars to acquire new credit score traces in your identify, or to steal crypto property and entry and drain financial institution accounts
- They may even use your work credentials to launch an assault in your employer, or a companion/provider group. A latest digital extortion marketing campaign which used infostealer malware to achieve entry to Snowflake accounts led to the compromise of tens of hundreds of thousands of buyer particulars
Learn how to keep away from malicious GenAI lures
Some tried-and-tested greatest practices ought to maintain you heading in the right direction and away from GenAI threats. Take into account the next:
- Solely set up apps from official app shops
Google Play and the Apple App Retailer have rigorous vetting processes and common monitoring to weed out malicious apps. Keep away from downloading apps from third-party web sites or unofficial sources, as they’re way more prone to host malicious wares.
- Double verify the builders behind apps and any critiques of their software program
Earlier than downloading an app, confirm the developer’s credentials and search for different apps they’ve developed and browse person critiques. Suspicious apps typically have poorly written descriptions, restricted developer historical past, and adverse suggestions highlighting points.
- Be cautious of clicking on digital adverts
Digital adverts, particularly on social media platforms like Fb, is usually a widespread vector for distributing malicious apps. As a substitute of clicking on adverts, instantly seek for the app or instrument in your official app retailer to make sure you’re getting the official model.
- Verify internet browser extensions earlier than putting in them
Net browser extensions can improve your internet expertise however may also pose safety dangers. Verify the developer’s background and browse critiques earlier than putting in any extensions. Keep on with well-known builders and extensions with excessive scores and substantial person suggestions.
- Use complete safety software program from a good vendor
Guarantee you may have sturdy safety software program from a good vendor put in in your PC and all cell units. This gives real-time safety towards malware, phishing makes an attempt, and different on-line threats.
Phishing stays a perennial menace. Be cautious of unsolicited messages that immediate you to click on on hyperlinks or open attachments. Confirm the sender’s identification earlier than interacting with any electronic mail, textual content, or social media message that seems suspicious.
- Allow multi-factor authentication (MFA) for all of your on-line accounts
MFA provides an additional layer of safety to your on-line accounts by requiring a number of verification strategies. Allow MFA wherever potential to guard your accounts even when your password is compromised.
As proven above, cybercriminals can’t resist exploiting the joy round new releases. In the event you see a proposal to obtain a brand new model of a GenAI instrument, confirm its availability via official channels earlier than continuing. Verify the official web site or trusted information sources to verify the discharge.
GenAI is altering the world round us at a speedy tempo. Be sure that it doesn’t change yours for the more serious.