In terms of designing visually interesting and intuitive person interfaces in iOS growth, SF Symbols are a useful asset. It provides a complete library of over 5,000 customizable icons, designed particularly for iOS and macOS purposes. The newest iOS 17 replace brings SF Symbols 5, which introduces a improbable assortment of expressive animations. SwiftUI provides builders the power to leverage these animations utilizing the brand new symbolEffect modifier.
This characteristic empowers builders to create numerous and charming animations inside their apps. By incorporating symbolEffect into your SwiftUI code, builders can improve person interactions and create visually participating interfaces. On this tutorial, we’ll present you work with this new modifier to create varied forms of animations.
The Fundamental Utilization of SymbolEffect
To animate a SF image, you possibly can connect the brand new symbolEffect modifier to the Picture view and specify the specified animation sort. Right here is an instance:
struct ContentView: View {
@State non-public var animate = false
var physique: some View {
Picture(systemName: "ellipsis.message")
.font(.system(measurement: 100))
.symbolRenderingMode(.palette)
.foregroundStyle(.purple, .grey)
.symbolEffect(.bounce, worth: animate)
.onTapGesture {
animate.toggle()
}
}
}There are a variety of built-in animations together with Seem, Disappear, Bounce, Scale, Pulse, Variable Coloration, and Change. Within the code above, we use the bounce animation. So, if you faucet the image within the preview canvas, it reveals a bouncing impact.

Make it Repeatable
By default, the animation is simply performed as soon as. To make it repeatable, you possibly can set the choices parameter of the modifier to .repeating like this:
.symbolEffect(.bounce, choices: .repeating, worth: animate)This may obtain an animated impact that repeats indefinitely. Should you need to repeat the impact for a particular variety of occasions, you possibly can make the most of the .repeat perform and point out the specified repeat rely as proven under:
.symbolEffect(.bounce, choices: .repeat(5), worth: animate)Controlling the animation pace

As well as, you may have the flexibleness to customise the animation pace by using the .pace perform throughout the choices parameter. As an example, should you want to decelerate the animation, you possibly can set the worth of the .pace perform to 0.1, as demonstrated under:
.symbolEffect(.bounce, choices: .pace(0.1), worth: animate)Animation Sorts
As said earlier, SwiftUI offers a wide range of built-in animation varieties, similar to Bounce, Scale, Pulse, Variable Coloration, and Change. Up till now, we have now completely used the bounce animation. Now, let’s discover and take a look at out different animation varieties utilizing the supplied code snippet:
struct SymbolAnimationView: View {
@State non-public var animate = false
var physique: some View {
VStack(alignment: .main, spacing: 50) {
HStack {
Picture(systemName: "mic.and.sign.meter")
.font(.system(measurement: 60))
.symbolRenderingMode(.palette)
.foregroundStyle(.purple, .grey)
.symbolEffect(.bounce, choices: .repeating, worth: animate)
Textual content("Bounce")
.font(.largeTitle)
}
HStack {
Picture(systemName: "mic.and.sign.meter")
.font(.system(measurement: 60))
.symbolRenderingMode(.palette)
.foregroundStyle(.purple, .grey)
.symbolEffect(.bounce.down, choices: .repeating, worth: animate)
Textual content("Bounce (down)")
.font(.largeTitle)
}
HStack {
Picture(systemName: "mic.and.sign.meter")
.font(.system(measurement: 60))
.symbolRenderingMode(.palette)
.foregroundStyle(.purple, .grey)
.symbolEffect(.pulse, choices: .repeating, worth: animate)
Textual content("Pulse")
.font(.largeTitle)
}
HStack {
Picture(systemName: "mic.and.sign.meter")
.font(.system(measurement: 60))
.symbolRenderingMode(.palette)
.foregroundStyle(.purple, .grey)
.symbolEffect(.pulse.wholeSymbol, choices: .repeating, worth: animate)
Textual content("Pulse (entire)")
.font(.largeTitle)
}
HStack {
Picture(systemName: "mic.and.sign.meter")
.font(.system(measurement: 60))
.symbolRenderingMode(.palette)
.foregroundStyle(.purple, .grey)
.symbolEffect(.variableColor, choices: .repeating, worth: animate)
Textual content("Variable colour")
.font(.largeTitle)
}
}
.onTapGesture {
animate.toggle()
}
}
}By tapping any of the pictures within the preview canvas, you possibly can see the animations coming to life. Compared to the bounce animation, the Pulse animation provides a definite impact by progressively fading the opacity of particular or all layers throughout the picture. However, the variableColor animation replaces the opacity of variable layers within the picture, offering a novel visible transformation.
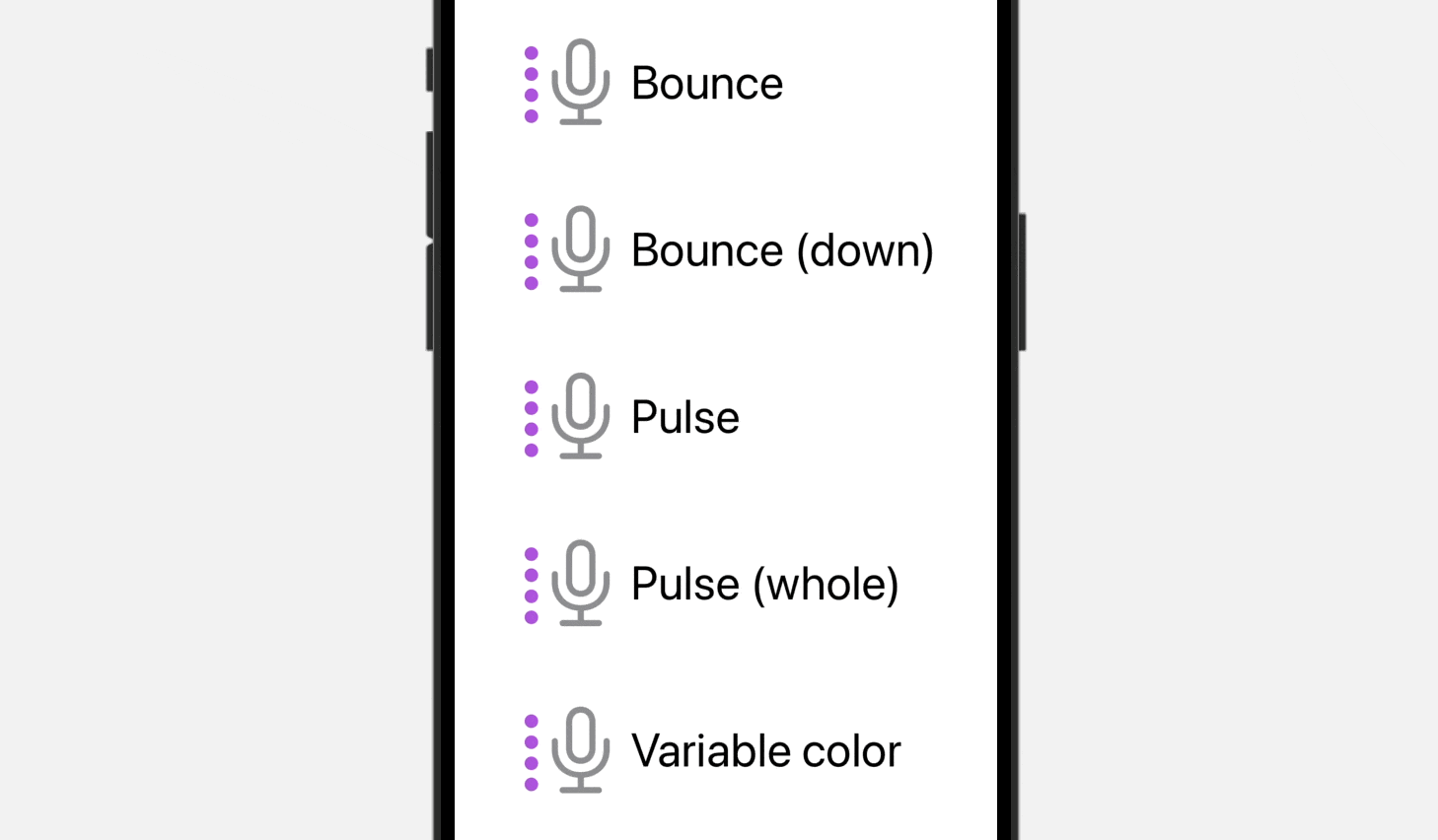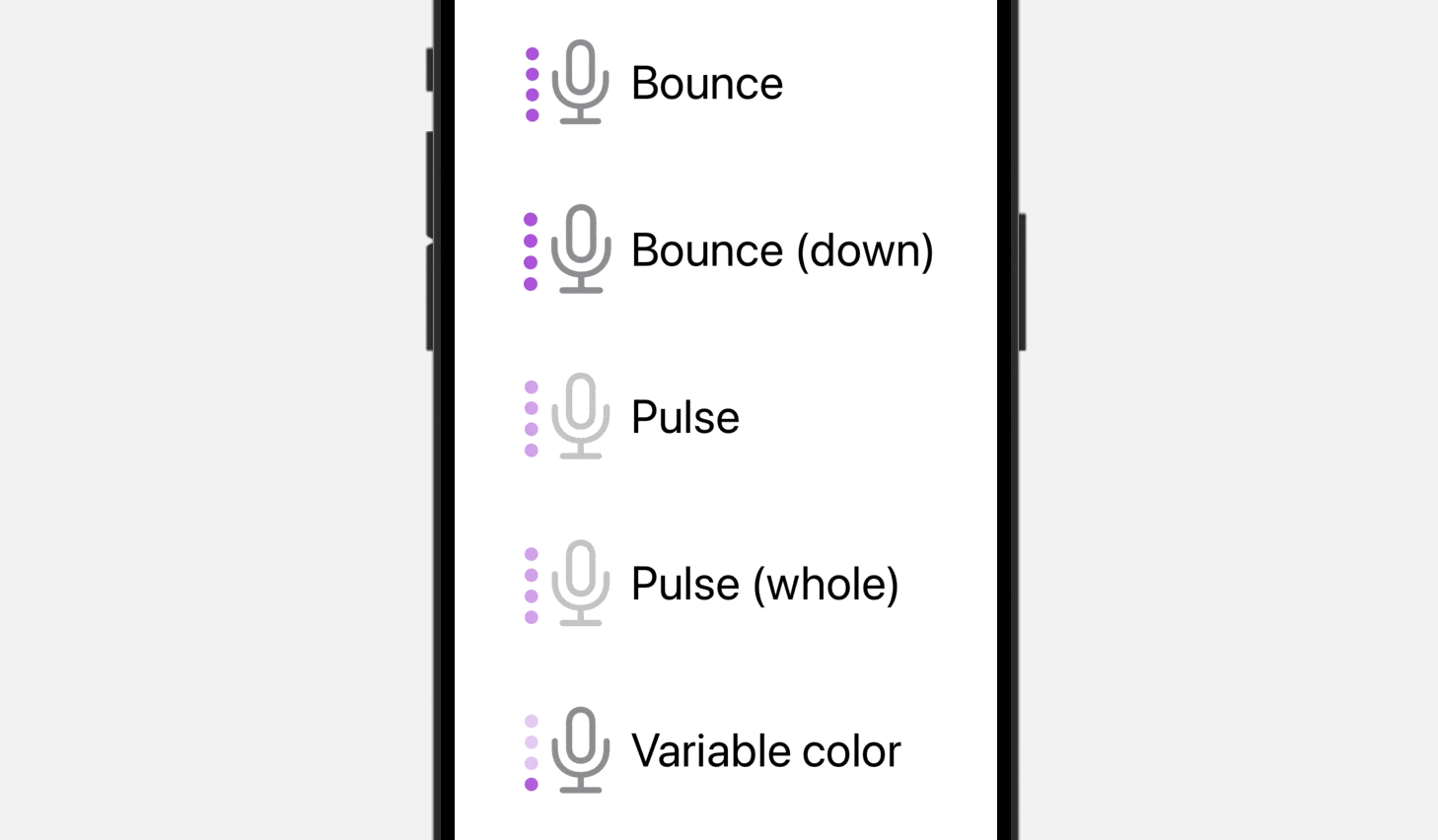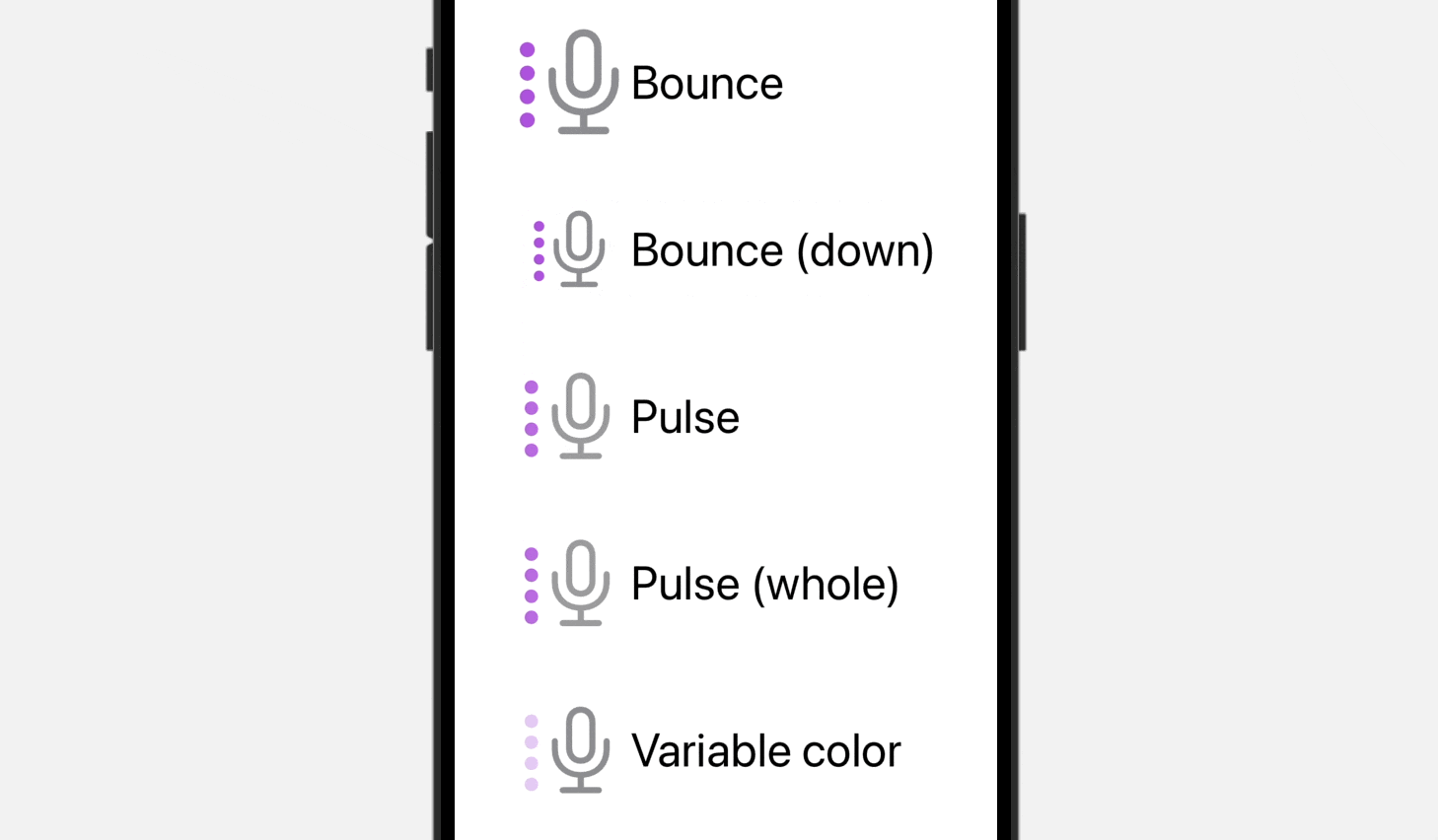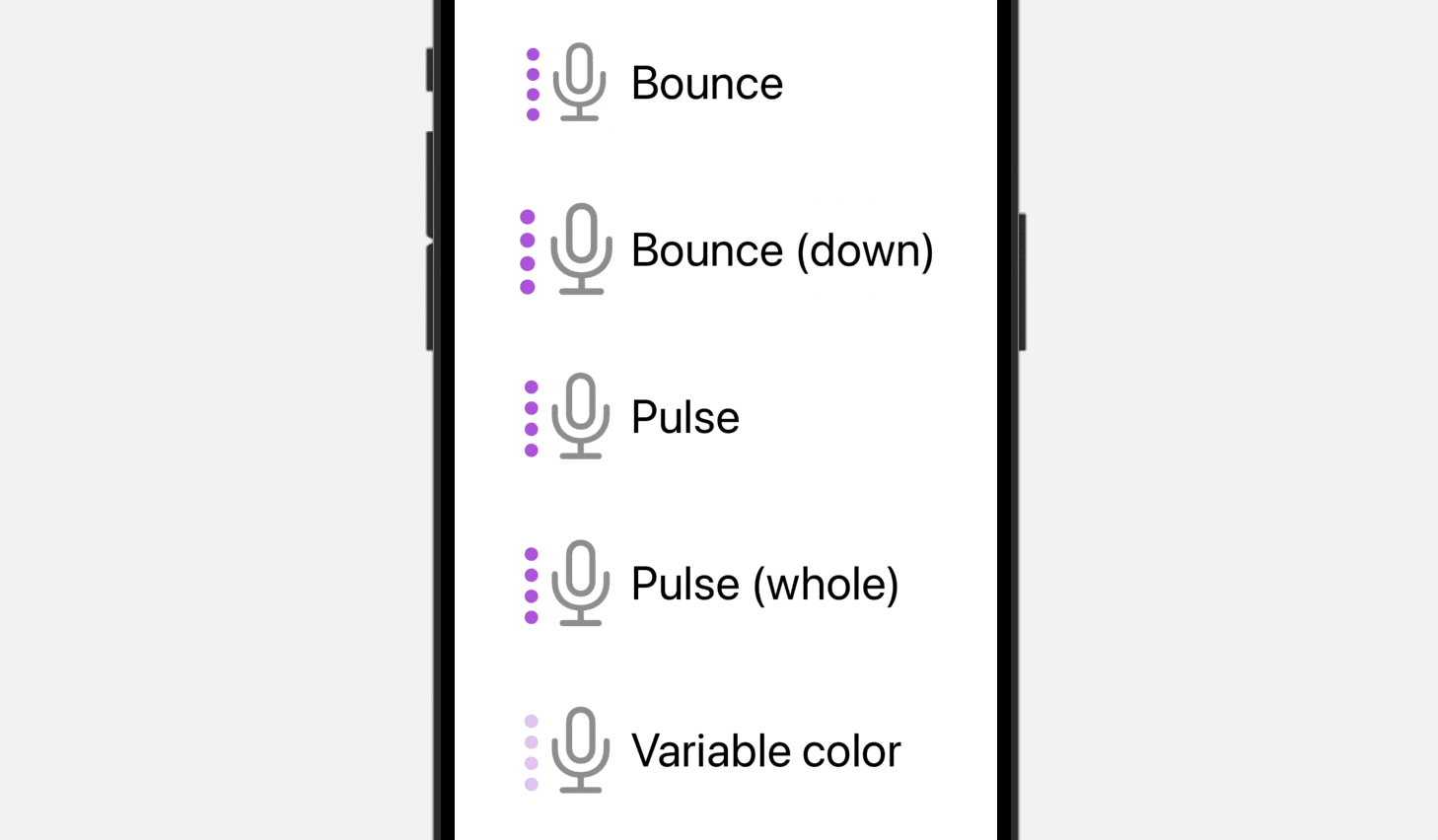
Even for the Bounce animation, you possibly can specify .bounce.down to bounce the image downward.
.symbolEffect(.bounce.down, choices: .repeating, worth: animate)For added flexibility, it’s attainable to use a number of symbolEffect modifiers to a view, permitting you to attain a customized impact by combining completely different animations.
Picture(systemName: "ellipsis.message")
.font(.system(measurement: 100))
.symbolRenderingMode(.palette)
.foregroundStyle(.purple, .grey)
.symbolEffect(.bounce, choices: .pace(1.5), worth: animate)
.symbolEffect(.pulse, choices: .repeating, worth: animate)
.onTapGesture {
animate.toggle()
}Content material Transition and Change Animation

In sure eventualities, there could also be a have to transition between completely different symbols inside a picture. As an example, when a person faucets the Contact ID image, it transforms right into a checkmark image. To make sure a seamless and visually pleasing transition, you possibly can make the most of the contentTransition modifier along side the Change animation, as demonstrated under:
Picture(systemName: animate ? "checkmark.circle" : "touchid")
.font(.system(measurement: 100))
.symbolRenderingMode(.palette)
.symbolEffect(.bounce, worth: animate)
.contentTransition(.symbolEffect(.exchange))
.foregroundStyle(.purple, .grey)
.onTapGesture {
animate.toggle()
}Abstract
SF Symbols and symbolEffect present builders with highly effective instruments to reinforce person interactions and create visually participating interfaces in iOS and macOS purposes.
This tutorial demonstrates the essential utilization of symbolEffect, making animations repeatable, controlling animation pace, and exploring completely different animation varieties. It additionally covers content material transition and exchange animation.
If in case you have discovered this tutorial pleasing and wish to discover SwiftUI additional, we extremely suggest trying out our complete e book, “Mastering SwiftUI.“











