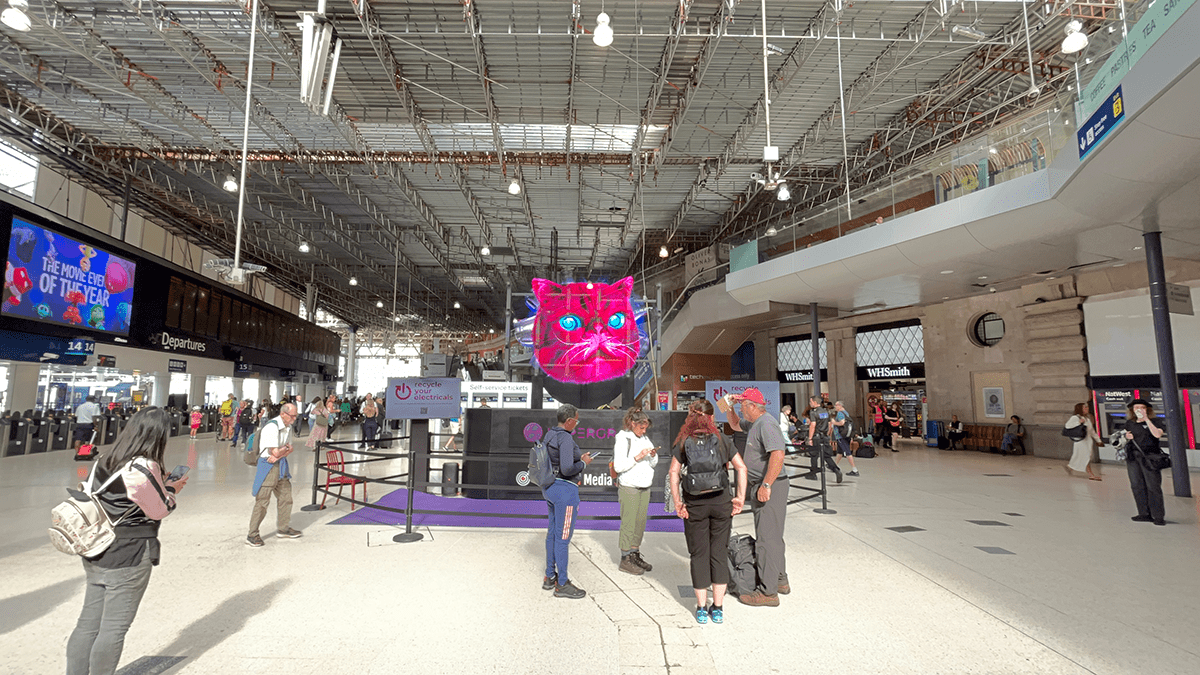
An enormous pink cat hologram might be stunning commuters at London Waterloo from Tuesday twentieth August. The hologram is seemingly an effigy of HypnoCat, Recycle Your Electricals’ pink, fluffy mascot, which might be playfully leaping out at commuters, tail a-twitching and eyes a-swirling.
The large, 3-metre-tall pink HypnoCat might be seen pouncing on commuters and mesmerising them as electrical gadgets spiral round him, seemingly highlighting the tech gadgets that he needs everybody to recycle. The state-of-the-art know-how, offered by HyperGram, makes use of the newest holographic know-how, with out the necessity for a display or glasses. 3-D objects float mid-air, making certain that HypnoCat and his message are unimaginable to disregard. He’ll make recycling electricals unmissable for commuters, vacation goers and customers.
The HypnoCat hologram is being launched within the run-up to Worldwide E-Waste Day (October 14th), to encourage individuals throughout the UK to take part in The Nice Cable Problem. This nationwide marketing campaign goals to handle the hundreds of thousands of unused cables mendacity idle throughout houses by urging households, native authorities, retailers, faculties and neighborhood initiatives to collectively recycle 1 million cables. Cables comprise at the least 20% copper and this treasured materials is misplaced perpetually when cables and different electricals are thrown away. Copper is a necessary a part of on a regular basis gadgets we take with no consideration, together with our sensible tech, transport, medical gear and our inexperienced vitality future.
Scott Butler, Govt Director of Materials Focus mentioned, “HypnoCat is out and about and bigger than ever earlier than! Utilizing unbelievable hologram know-how on this distinctive visible approach, we hope he’ll pawsuade many extra individuals to take motion and be a part of us in our recycling efforts within the run as much as Worldwide E-Waste Day.
“Virtually all of us have these previous, forgotten cables stashed away at residence – I’ve a field underneath my mattress of cables I’ve been holding onto ‘simply in case’ however haven’t really utilized in months or are damaged. However by recycling them or donating those who nonetheless work, we are able to repurpose or reclaim that helpful copper at the moment going to waste. The Nice Cable Problem is an easy approach for everybody to make an enormous, collective distinction – by recycling at the least one cable. Most individuals might be stunned at simply how simple it’s to do.”
As a nation of cat lovers, everyone knows that “cats rule” and this cat isn’t any exception – he’ll be distracting commuters, and even a number of canine! Together with his tail twitching impatiently, and his voice booming, he’ll compete with important practice info. Commuters at Waterloo on twentieth – twenty fourth August will discover HypnoCat in 3D beneath the massive practice time info board.
Bailey Younger, Director at DMG mentioned, “Disturbed Media Group, an progressive company on the forefront of immersive experiences, is proud to announce the showcase of its newest undertaking within the UK, HyperGram. Leveraging state-of-the-art 3D holographic know-how developed by our esteemed tech companion, Hypervsn, HyperGram transforms conventional visible storytelling by creating animations that seem to drift in mid-air.
It’s been a pleasure bringing to life Hypnocat which appeared extremely becoming to what we have been attempting to realize this yr. We hope shoppers round London have a extremely pleasing expertise and we look ahead to the outcomes of the marketing campaign!”
How are you going to get entangled in Worldwide E-Waste Day?
Anybody can take part in The Nice Cable Problem and take one small motion to make an enormous distinction. Merely bag up your cables – and another previous, undesirable electricals you discover in your ‘drawer of doom’ – and go to Recycle Your Electricals’ postcode locator to search out your native donation or recycling level.
Materials Focus has created a marketing campaign toolkit to allow native authorities, retailers, faculties and neighborhood initiatives throughout the UK to participate within the problem and assist encourage individuals to recycle their previous cables and different small electricals. If you need extra info then please electronic mail hey@materialfocus.org.uk.
Companions can both:
- Arrange pop-up cable collections in workplaces, universities, faculties and neighborhood halls, to make it as simple as attainable for workers, college students or residents to recycle their family electricals and cables. The toolkit features a step-by-step information for organising your personal pop-up assortment level (for family electricals solely, not enterprise waste).
- Assist promote the marketing campaign utilizing Materials Focus’ communication supplies, and lift consciousness {of electrical} waste and encourage people, and native communities, to take motion.