A fantastic many readers this month reported receiving alerts that their Social Safety Quantity, title, tackle and different private data have been uncovered in a breach at a little-known however aptly-named client knowledge dealer known as NationalPublicData.com. This submit examines what we find out about a breach that has uncovered tons of of thousands and thousands of client data. We’ll additionally take a better take a look at the information dealer that bought hacked — a background examine firm based by an actor and retired sheriff’s deputy from Florida.
On July 21, 2024, denizens of the cybercrime group Breachforums launched greater than 4 terabytes of knowledge they claimed was stolen from nationalpublicdata.com, a Florida-based firm that collects knowledge on shoppers and processes background checks.
The breach monitoring service HaveIBeenPwned.com and the cybercrime-focused Twitter account vx-underground each concluded the leak is identical data first put up on the market in April 2024 by a prolific cybercriminal who goes by the title “USDoD.”
On April 7, USDoD posted a gross sales thread on Breachforums for 4 terabytes of knowledge — 2.9 billion rows of data — they claimed was taken from nationalpublicdata.com. The snippets of stolen knowledge that USDoD provided as teasers confirmed rows of names, addresses, telephone numbers, and Social Safety Numbers (SSNs). Their asking value? $3.5 million.
Many media retailers mistakenly reported that the Nationwide Public knowledge breach impacts 2.9 billion individuals (that determine really refers back to the variety of rows within the leaked knowledge units). HaveIBeenPwned.com’s Troy Hunt analyzed the leaked knowledge and located it’s a considerably disparate assortment of client and enterprise data, together with the true names, addresses, telephone numbers and SSNs of thousands and thousands of People (each dwelling and deceased), and 70 million rows from a database of U.S. legal data.
Hunt stated he discovered 137 million distinctive electronic mail addresses within the leaked knowledge, however pressured that there have been no electronic mail addresses within the information containing SSN data.
“If you end up on this knowledge breach through HaveIBeenPwned.com, there’s no proof your SSN was leaked, and if you happen to’re in the identical boat as me, the information subsequent to your file might not even be right.”
Nationalpublicdata.com publicly acknowledged a breach in an announcement on Aug. 12, saying “there seems to have been an information safety incident which will have concerned a few of your private data. The incident seems to have concerned a third-party unhealthy actor that was attempting to hack into knowledge in late December 2023, with potential leaks of sure knowledge in April 2024 and summer season 2024.”
The corporate stated the data “suspected of being breached” contained title, electronic mail tackle, telephone quantity, social safety quantity, and mailing tackle(es).
“We cooperated with legislation enforcement and governmental investigators and carried out a assessment of the doubtless affected data and can attempt to notify you if there are additional vital developments relevant to you,” the assertion continues. “We have now additionally carried out extra safety measures in efforts to stop the reoccurrence of such a breach and to guard our methods.”
Hunt’s evaluation didn’t say what number of distinctive SSNs have been included within the leaked knowledge. However in accordance with researchers at Atlas Information Privateness Corp., there are 272 million distinctive SSNs in all the data set.
Atlas discovered most data have a reputation, SSN, and residential tackle, and that roughly 26 % of these data included a telephone quantity. Atlas stated they verified 5,000 addresses and telephone numbers, and located the data pertain to individuals born earlier than Jan. 1, 2002 (with only a few exceptions).
If there’s a tiny silver lining to the breach it’s this: Atlas found that most of the data associated to people who find themselves now virtually actually deceased. They discovered the common age of the patron in these data is 70, and totally two million data are associated to individuals whose date of start would make them greater than 120 years previous at present.
TWISTED HISTORY
The place did Nationwide Public Information get its client knowledge? The corporate’s web site doesn’t say, however it’s operated by an entity in Coral Springs, Fla. known as Jerico Photos Inc. The web site for Jerico Photos just isn’t presently responding. Nonetheless, cached variations of it at archive.org present it’s a movie studio with workplaces in Los Angeles and South Florida.
The Florida Secretary of State says Jerico Photos is owned by Salvatore (Sal) Verini Jr., a retired deputy with the Broward County Sheriff’s workplace. The Secretary of State additionally says Mr. Verini is or was a founding father of a number of different Florida corporations, together with Nationwide Legal Information LLC, Twisted Historical past LLC, Shadowglade LLC and Trinity Leisure Inc., amongst others.
Mr. Verini didn’t reply to a number of requests for remark. Cached copies of Mr. Verini’s self-importance area salvatoreverini.com recount his expertise in appearing (e.g. a job in a Eighties detective drama with Burt Reynolds) and extra not too long ago producing dramas and documentaries for a number of streaming channels.
Sal Verini’s profile web page at imdb.com.
Pivoting on the e-mail tackle used to register that self-importance area, DomainTools.com finds a number of different domains whose historical past presents a clearer image of the varieties of knowledge sources relied upon by Nationwide Public Information.
A kind of domains is recordscheck.web (previously recordscheck.data), which advertises “immediate background checks, SSN traces, workers screening and extra.” One other now-defunct enterprise tied to Mr. Verini’s electronic mail — publicrecordsunlimited.com — stated it obtained client knowledge from a wide range of sources, together with: start, marriage and dying data; voting data; skilled licenses; state and federal legal data.
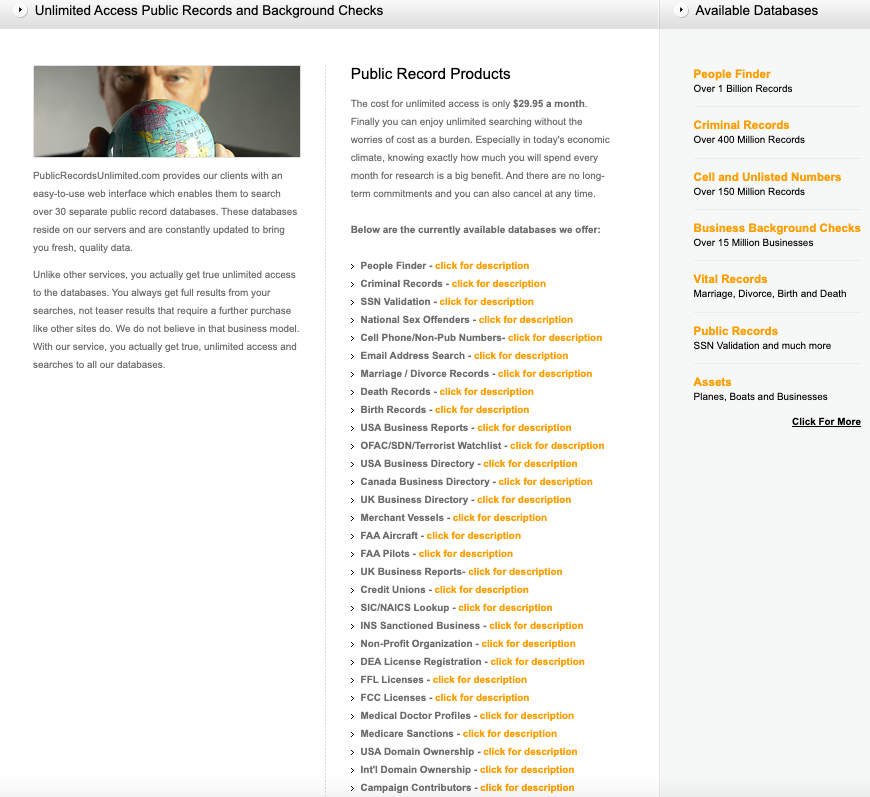
The homepage for publicrecordsunlimited.com, per archive.org circa 2017.
It stays unclear how thieves initially obtained these data from Nationwide Public Information. KrebsOnSecurity sought remark from USDoD, who is probably finest identified for hacking into Infragard, an FBI program that facilitates data sharing about cyber and bodily threats with vetted individuals within the non-public sector.
USDoD stated they certainly offered the identical knowledge set that was leaked on Breachforums this previous month, however that the one who leaked the information didn’t receive it from them. USDoD stated the information stolen from Nationwide Public Information had traded palms a number of occasions because it was initially stolen in December 2023.
“The database has been floating round for some time,” USDoD stated. “I used to be not the primary one to get it.”
USDoD stated the one who initially stole the information from NPD was a hacker who goes by the deal with SXUL. That consumer seems to have deleted their Telegram account a number of days in the past, presumably in response to intense media protection of the breach.
ANALYSIS
Information brokers like Nationwide Public Information sometimes get their data by scouring federal, state and native authorities data. These authorities information embrace voting registries, property filings, marriage certificates, motorized vehicle data, legal data, court docket paperwork, dying data, skilled licenses, chapter filings, and extra.
People might consider they’ve the appropriate to choose out of getting these data collected and offered to anybody. However specialists say these underlying sources of data — the above-mentioned “public” data — are carved out from each single state client privateness legislation. This consists of California’s privateness regime, which is usually held up because the nationwide chief in state privateness rules.
You see, right here in America, nearly anybody can change into a client knowledge dealer. And with few exceptions, there aren’t any particular necessities for brokers to indicate that they really care about defending the information they gather, retailer, repackage and promote so freely.
In February 2023, PeopleConnect, the homeowners of the background search providers TruthFinder and Prompt Checkmate, acknowledged a breach affecting 20 million prospects who paid the information brokers to run background checks. The info uncovered included electronic mail addresses, hashed passwords, first and final names, and telephone numbers.
In 2019, malicious hackers stole knowledge on greater than 1.5 billion individuals from Individuals Information Labs, a San Francisco knowledge dealer whose people-search providers linked tons of of thousands and thousands of electronic mail addresses, LinkedIn and Fb profiles and greater than 200 million legitimate mobile phone numbers.
These knowledge brokers are the digital equal of large oil tankers wandering the coast with out GPS or an anchor, as a result of once they get hacked, the impact may be very a lot akin to the ecological and financial fallout from a large oil spill.
It’s an apt analogy as a result of the dissemination of a lot private knowledge suddenly has ripple results for months and years to return, as this data invariably feeds into an enormous underground ocean of scammers who’re already geared up and staffed to commit id theft and account takeovers at scale.
It’s additionally apt as a result of very similar to with real-life oil spills, the cleanup prices and energy from knowledge spills — even simply huge collections of technically “public” paperwork just like the NPD corpus — may be huge, and many of the prices related to that fall to shoppers, immediately or not directly.
WHAT SHOULD YOU DO?
Do you have to fear that your SSN and different private knowledge is likely to be uncovered on this breach? That isn’t mandatory for individuals who’ve been following the recommendation right here for years, which is to freeze one’s credit score file at every of the main client reporting bureaus. Having a freeze in your information makes it a lot more durable for id thieves to create new accounts in your title, and it limits who can view your credit score data.
The principle motive I like to recommend the freeze is that the entire data ID thieves must assume your id is now broadly accessible from a number of sources, because of the multiplicity of knowledge breaches we’ve seen involving SSN knowledge and different key static knowledge factors about individuals.
However past that, there are quite a few cybercriminal providers that supply detailed background checks on shoppers, together with full SSNs. These providers are powered by compromised accounts at knowledge brokers that cater to personal investigators and legislation enforcement officers, and a few at the moment are totally automated through Telegram immediate message bots. That means, if you happen to’re an American who hasn’t frozen their credit score information and also you haven’t but skilled some type of new account fraud, the ID thieves most likely simply haven’t gotten round to you but.
All People are additionally entitled to acquire a free copy of their credit score report weekly from every of the three main credit score bureaus. It was once that buyers have been allowed one free report from every of the bureaus yearly, however in October 2023 the Federal Commerce Fee introduced the bureaus had completely prolonged a program that allows you to examine your credit score report as soon as every week without cost.
For those who haven’t performed this shortly, now can be a superb time to order your information. To put a freeze, it’s essential to create an account at every of the three main reporting bureaus, Equifax, Experian and TransUnion. When you’ve established an account, you need to be capable of then view and freeze your credit score file. Dispute any inaccuracies chances are you’ll discover. For those who spot errors, resembling random addresses and telephone numbers you don’t acknowledge, don’t ignore them: Id theft and new account fraud should not issues that get simpler to resolve by letting them fester.
Mr. Verini most likely didn’t reply to requests for remark as a result of his firm is now the topic of a class-action lawsuit (NB: the lawsuit additionally erroneously claims 3 billion individuals have been affected). These lawsuits are virtually inevitable now after a significant breach, however additionally they have the unlucky tendency to let regulators and lawmakers off the hook.
Virtually each time there’s a significant breach of SSN knowledge, People are provided credit score monitoring providers. More often than not, these providers come from one of many three main client credit score bureaus, the identical corporations that revenue by compiling and promoting extremely detailed dossiers on shoppers’ monetary lives. The identical corporations that use darkish patterns to trick individuals into paying for “credit score lock” providers that obtain an analogous outcome as a freeze however nonetheless let the bureaus promote your knowledge to their companions.
However class-actions alone won’t drive us towards a nationwide dialog about what wants to vary. People presently have only a few rights to choose out of the private and monetary surveillance, knowledge assortment and sale that’s pervasive in at present’s tech-based financial system.
The breach at Nationwide Public Information might not be the worst knowledge breach ever. Nevertheless it does current one more alternative for this nation’s leaders to acknowledge that the SSN has fully failed as a measure of authentication or authorization. It was by no means a good suggestion to make use of as an authenticator to start with, and it’s actually now not appropriate for this objective.
The reality is that these knowledge brokers will proceed to proliferate and thrive (and get hacked and relieved of their knowledge) till Congress begins to comprehend it’s time for some client privateness and knowledge safety legal guidelines which can be related to life within the twenty first century.
Replace, Aug. 16, 8:00 a.m. ET: Corrected the story to notice that buyers can now receive a free credit score report from every of the three client reporting bureaus weekly, as an alternative of simply yearly.















