As two privacy-focused VPNs, each NordVPN and Proton VPN provide robust options that might make it onerous to decide on one answer over the opposite.
NordVPN offers an throughout service with an in depth server community and reliably quick VPN efficiency. Alternatively, Proton VPN operates in privacy-friendly Switzerland and gives a beneficiant free VPN, which might entice budget-oriented customers.
On this article, we check out which VPN is greatest for you and your group.
- NordVPN: Greatest for many companies that need a feature-packed VPN that provides a geographically various server suite and quick VPN speeds.
- Proton VPN: Greatest for particular person customers who need a privacy-centric VPN with a devoted free model that might be used long-term.
NordVPN vs Proton VPN: Comparability
Each VPNs embody the identical quantity of simultaneous machine connections and beginning worth. They do differ of their respective server suite and free trial entry.
| Our score | ||
| Safety protocols | ||
| No. of servers | ||
| VPN server areas | ||
| Simultaneous machine areas | ||
| Supported platforms | ||
| Free trial | ||
| Beginning worth | ||
|
|
NordVPN vs Proton VPN: Pricing
NordVPN pricing
NordVPN’s paid plans have three tiers, with every tier having a month-to-month, an annual and a two-year plan possibility. The tiers are NordVPN Fundamental, Plus and Final — with Final having essentially the most options out of the bunch.
SEE: Tips on how to Run a Cybersecurity Threat Evaluation in 5 Steps (TechRepublic Premium)
Beneath is an outline of pricing and have variations with every tier:
| Fundamental | Plus | Final | |
|---|---|---|---|
| Month-to-month | $12.99 per 30 days | $13.99 per 30 days | $15.99 per 30 days |
| 1 12 months | $4.99 per 30 days | $5.99 per 30 days | $7.99 per 30 days |
| 2 years | $3.99 per 30 days | $4.99 per 30 days | $6.99 per 30 days |
| Options | Contains fundamental VPN | All Fundamental options plus anti-malware and shopping safety, advert and tracker blocker and information breach scanner | All Plus options plus 1TB encrypted cloud storage, cyber extortion safety and id theft restoration profit |
Personally, I feel the NordVPN Plus plan for one 12 months at $5.99 per 30 days is the most effective package deal among the many three plans. It gives you extra safety features on high of the VPN whereas nonetheless not going overboard when it comes to the month-to-month charge.
Whereas I’m glad NordVPN has a seven-day free trial, I discover it unlucky that it’s solely obtainable by way of its Android cell app. This makes it tough for iOS and iPhone customers who’re presumably excited by test-driving NordVPN. Hopefully, NordVPN makes its trial obtainable for each iOS and Android customers, opening it as much as extra customers, no matter their smartphone preferences.
Fortunately, customers can attempt NordVPN on desktop after accessing the free trial on Android — which is how I examined NordVPN’s premium subscription.
If you wish to be taught extra, learn our full NordVPN evaluation.
Proton VPN pricing
As compared, Proton VPN has two tiers for its paid service and a devoted free model. Its paid plans are known as Proton VPN Plus and Limitless, each with month-to-month, annual and two-year contract choices.
| Proton VPN Free | Proton VPN Plus | Proton Limitless | |
|---|---|---|---|
| Month-to-month | Free | $9.99 per 30 days | $12.99 per 30 days |
| Annual | Free | $4.99 per 30 days | $9.99 per 30 days |
| 2 years | Free | $4.49 per 30 days | $7.99 per 30 days |
| Options |
|
|
|
Whereas Proton VPN doesn’t have a free trial of its paid tiers, I like the way it offers a full free model of its VPN service. This allows customers to get a glimpse of its VPN with none preliminary fee or subscription.
The free model itself is restricted in that it solely provides you entry to 5 nations and slower speeds. Nonetheless, it’s beneficiant given the way it offers limitless bandwidth and information — one thing that isn’t widespread on different free VPNs. As compared, NordVPN doesn’t presently provide any kind of free model.
When it comes to its paid plans, I discover the Plus subscription for one 12 months to be the most effective worth. Whereas not essentially the most reasonably priced, it’s nonetheless on par with NordVPN’s equal beginning subscription at $4.99 per 30 days. You get Proton’s VPN service, together with the complete server fleet, with out the opposite Proton companies within the Limitless tier that will or is probably not of use to you.
If you wish to be taught extra, learn our full Proton VPN evaluation and see this information on learn how to use Proton VPN.
NordVPN vs Proton VPN: Characteristic comparability
Safety protocols and encryption
Winner: Tie
Each NordVPN and Proton VPN have VPN protocols that present a very good combine between velocity and safety. NordVPN gives the OpenVPN protocol and its proprietary NordLynx protocol based mostly on WireGuard. Alternatively, Proton VPN carries OpenVPN, WireGuard and its personal Stealth protocol constructed to disguise VPN use.
To me, a contemporary VPN ought to at the least have the security-focused OpenVPN protocol and the speed-oriented WireGuard protocol. Fortuitously, we get variations of each with NordVPN and Proton VPN.
SEE: NordVPN vs ExpressVPN: Which VPN Is Greatest? (TechRepublic)
Each VPNs additionally include top-grade encryption algorithms, equipping their software program with AES-256 encryption. AES-256 is taken into account the usual for safeguarding consumer information, utilized by authorities companies, banks and army establishments to maintain delicate data safe in opposition to malicious actors.
VPN server community and areas
Winner: NordVPN
For servers, NordVPN has the sting over Proton VPN. As of July 2024, NordVPN presently has 6,400+ servers throughout 111 nations. In distinction, Proton VPN gives entry to six,300+ servers in 100 nations.
Whereas the distinction in server rely is negligible, I discover extra worth in NordVPN having an extra 11 extra nations over Proton VPN. That is vital as a result of one of many fundamental makes use of of a VPN is to unblock geo-restricted content material.
With the upper nation rely, customers and companies may have extra location choices to select from in the case of unblocking.
Third-party audits and observe file
Winner: Proton VPN
So far as total observe file and third-party audits go, I’m giving the win to Proton VPN. Whereas each VPN suppliers have undergone intensive and up to date impartial audits, I really feel Proton VPN offers extra transparency to the general public in the case of audit outcomes.
As of July 2024, Proton VPN has completed its third consecutive impartial audit, confirming its no-logs coverage. On the flipside, NordVPN has undergone 4 impartial safety audits confirming the identical.
The distinction lies in how they share their respective audit outcomes. In its most up-to-date audit, NordVPN opted to not share the complete outcomes to make sure the findings weren’t “taken out of context or misunderstood” — offering full entry to the report solely to these with a NordVPN account.
SEE: 4 Greatest Free VPNs for 2024 (TechRepublic)
Alternatively, Proton VPN offers a full hyperlink to its 2024 Securitum safety audit. The audit outcomes are accessible to each the general public and official Proton VPN customers.
I actually commend Proton VPN right here, showcasing its robust dedication to maintaining customers knowledgeable about its service’s efficiency, good or unhealthy. Whereas NordVPN’s suite of audits is strong in its personal proper, I’ve to present this spherical to Proton VPN for its transparency.
Standout options
Winner: NordVPN
For standout options, NordVPN wins over Proton VPN. Except for its fundamental VPN service, NordVPN features a ton of safety and privacy-focused options that make it a compelling safety instrument for companies.
For instance, it has its Meshnet characteristic that lets customers create their very own non-public encrypted community, permitting them to share recordsdata or entry different gadgets extra securely.
I personally like this double VPN characteristic that routes the consumer’s connection to 2 totally different VPN server areas, offering an extra layer of safety alongside the encrypted VPN connection.
Different options embody a built-in malware, internet tracker and advert blocker, in addition to a darkish internet monitor to maintain observe of compromised credentials, amongst different safety capabilities.
SEE: Does a VPN Gradual Down Your Web Pace? (TechRepublic)
That isn’t to say Proton VPN doesn’t have its personal standout inclusions. A spotlight for me is its Swiss-based privateness. Whereas not a software program characteristic per se, Proton VPN’s operations are based mostly in Switzerland, a rustic with among the strongest privateness legal guidelines on this planet. Because of this Proton customers received’t have to fret about their information being illegally accessed.
It additionally has a singular Stealth VPN protocol that makes use of obfuscation expertise to masks your VPN site visitors, making it appear to be you aren’t linked by way of a VPN. This may be essential for customers in restrictive areas that don’t essentially enable VPNs.
Total, whereas Proton VPN contains helpful privacy-focused options, I give the benefit to NordVPN for its intensive suite of extra performance on high of its fundamental VPN capabilities.
Efficiency and velocity
Winner: NordVPN
In the case of velocity, I’ve to present NordVPN the benefit. Throughout my testing, I linked to each VPNs and did my normal workflow as a author. This concerned having a number of tabs open for analysis, attending on-line video conferences, utilizing Google Workspace apps like Docs and Drive and streaming the occasional 1080p YouTube video.
Per my expertise, I had extra steady speeds with NordVPN in comparison with Proton VPN. Whereas I anticipated a lower in velocity whereas linked to a NordVPN server in comparison with my web service supplier, I truthfully felt zero to little distinction in velocity.
SEE: How A lot Does a VPN Value? + Financial savings Ideas (TechRepublic)
As compared, Proton VPN additionally supplied decently quick speeds. Nonetheless, I did really feel NordVPN had that slight edge when it comes to consistency and total reliability with its connection.
In case your precedence is having the most effective speeds, I discover NordVPN to be the higher alternative out of the 2.
Ease of use and design
Winner: NordVPN
For consumer expertise, ease of use and design, NordVPN is my winner. NordVPN makes use of a minimalist, light-themed consumer interface that’s straightforward on the eyes and intuitive to navigate.
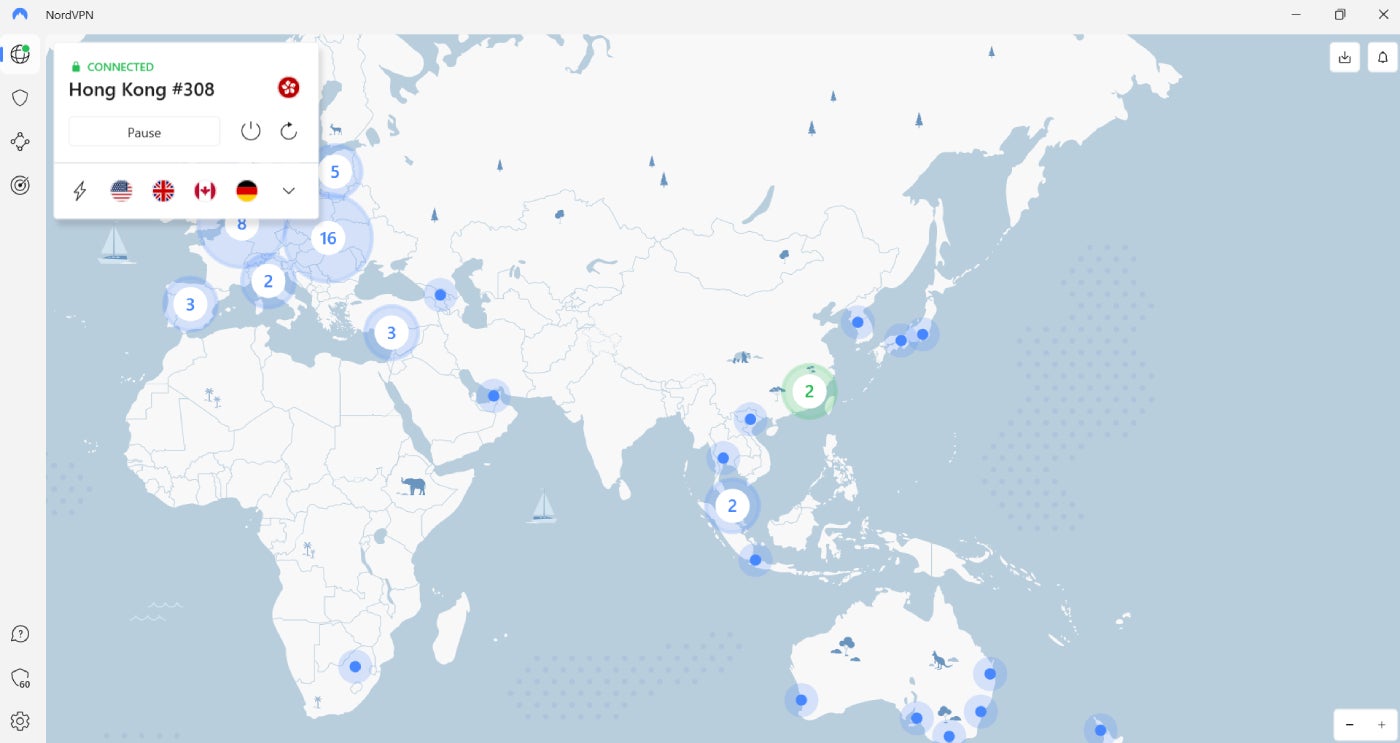
It has a sidebar on the left that neatly organizes all its vital options and helps present a clear interface that doesn’t really feel cluttered, regardless of the variety of options it homes.
In the meantime, Proton VPN adopts a darker themed desktop utility that I discover a bit much less organized in comparison with NordVPN. Whereas the app itself performs properly, I feel there’s a bit an excessive amount of occurring with its desktop app that might confuse customers.
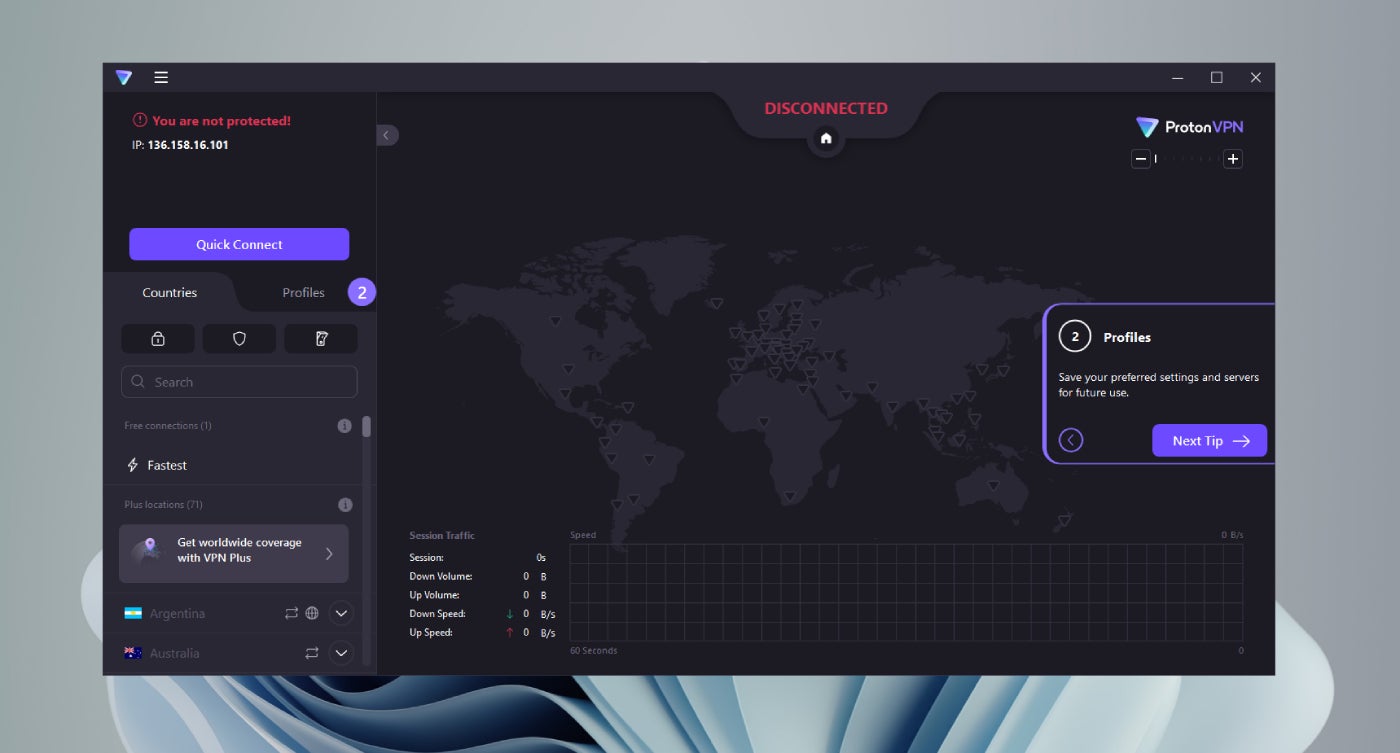
I personally assume it might do a greater job of organizing its options into separate menus as an alternative of its present iteration the place it has a number of buttons on a single web page. For instance, if we take a look at Proton VPN’s sidebar, we get a International locations and Profiles tab, three characteristic buttons, a search menu and the server checklist multi function place.
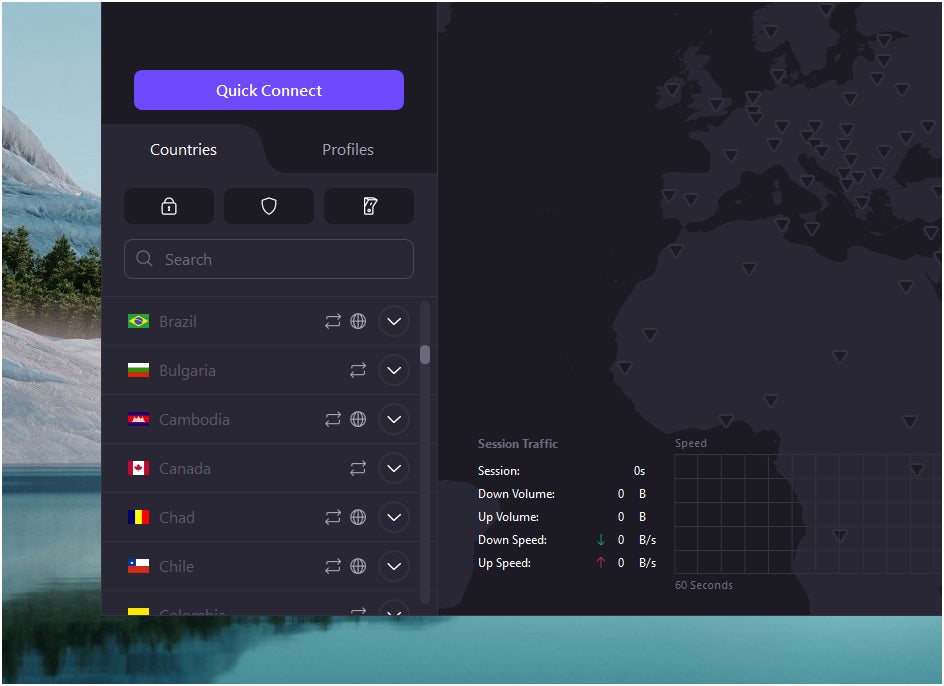
Personally, I feel having all these options in a single part makes Proton VPN really feel a bit cluttered and disorganized. In distinction, NordVPN has a devoted tab for every of its options, together with its server checklist, Meshnet instrument and different options.
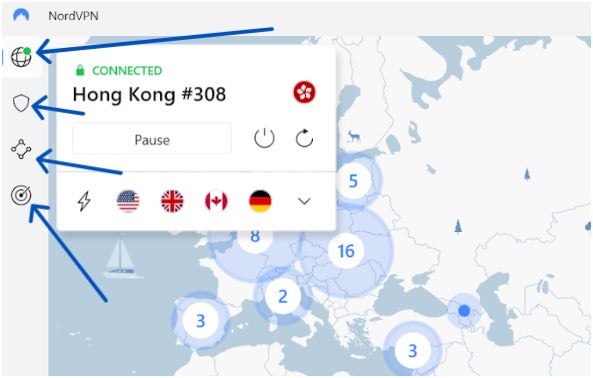
With this, I really feel it helps make NordVPN the simpler VPN to make use of out of the field. That is particularly vital for freshmen who is probably not accustomed to how VPNs work.
Simultaneous machine connections
Winner: Tie
Trying into simultaneous machine connections, NordVPN and Proton VPN are tied. Each VPNs enable for as much as 10 gadgets to be concurrently linked to their VPN servers.
Whereas I might have most well-liked being able to attach a vast variety of gadgets, like Personal Web Entry VPN or Surfshark VPN, I feel 10 gadgets remains to be a ok quantity for many companies and customers. This can enable most organizations to have a handful of smartphones, laptops and different gadgets linked to a VPN server all on the identical time.
NordVPN professionals and cons
Execs
- Servers in 111 nations, with 6,400+ servers.
- Nicely-designed and intuitive desktop utility.
- Contains a wide range of security-focused extra options.
Cons
- Full audit outcomes require a NordVPN account.
- Free trial solely accessible by way of Android.
- No free model.
Proton VPN professionals and cons
Execs
- Based mostly in privacy-friendly Switzerland.
- Extra clear audit outcomes.
- Has a free model with limitless information.
Cons
- Desktop app might be streamlined.
- Fewer nation areas in comparison with NordVPN.
Ought to your group use NordVPN or Proton VPN?
For many companies, I like to recommend going with NordVPN. It has a extra intensive 111-country server community, a bevy of extra privacy-focused options and an easy-to-use and well-designed VPN utility.
I additionally actually like NordVPN for its total quick and constant VPN speeds, which offered nearly zero real-world drop in efficiency in comparison with my ISP.
This isn’t to dismiss Proton VPN. I really feel Proton VPN is an efficient alternative for freshmen who wish to attempt a free VPN with none information or bandwidth restrictions.
Proton VPN can be an important possibility for customers who’re notably anxious about authorities surveillance. As a Switzerland-based firm, it operates in a privacy-friendly nation that may provide peace of thoughts to companies and customers with privateness considerations.
Methodology
My head-to-head match-up of NordVPN and Proton VPN concerned an in-depth evaluation of each VPN’s options, real-world efficiency and worth.
To judge every VPN, each companies had been scored on every part from their server networks to their pricing. Specifically, I took under consideration 5 fundamental pillars, every having corresponding weights:
- Pricing (20%).
- Core VPN options (30%).
- Ease of use (15%).
- Buyer assist (30%).
- Skilled evaluation (5%).
I additionally appeared into actual consumer suggestions and respected opinions to spherical out my closing suggestions for each NordVPN and Proton VPN.
For velocity and efficiency, I examined each VPNs on my private Home windows pc and ran them by means of Ookla’s public Speedtest. Lastly, I additionally thought of which kinds of companies or particular person customers would greatest profit from both NordVPN or Proton VPN.


_Tero_Vesalainen_Alamy.jpg?disable=upscale&width=1200&height=630&fit=crop&w=768&resize=768,0&ssl=1)





