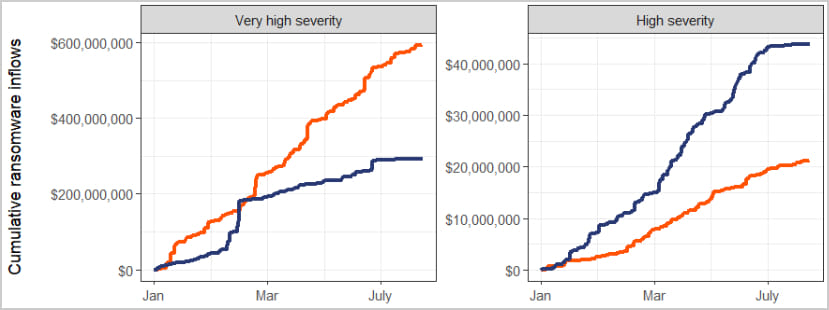
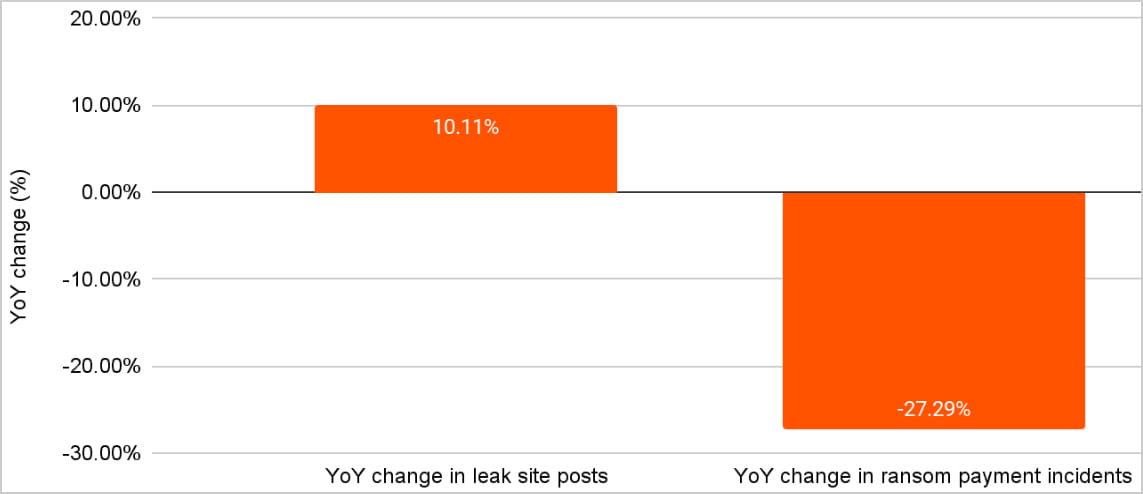
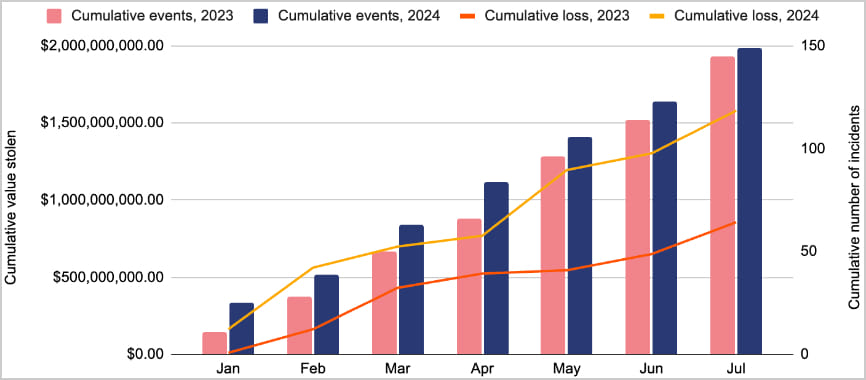
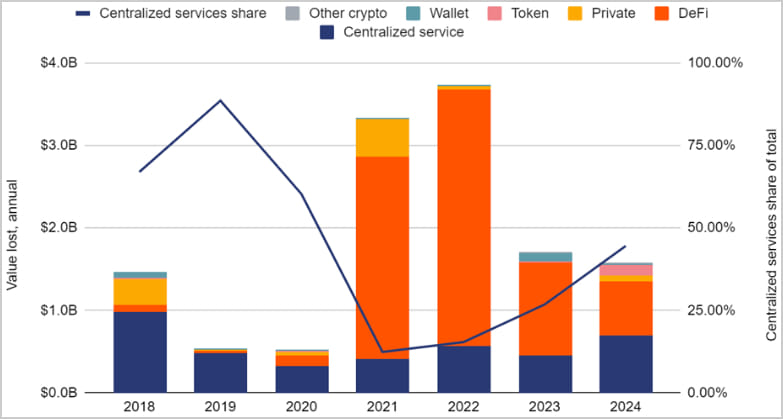
Within the ever-evolving world of software program improvement and testing, having the suitable instruments at your disposal is essential. One such software that has turn out to be indispensable for builders is the proxy. Proxies enable builders to check their purposes throughout varied areas, keep away from IP blocks, and scrape knowledge with out revealing their precise IP addresses. On this article, we’ll discover the highest 5 proxy suppliers which are good for tester builders, with Proxys.io taking the highest spot. Whether or not you’re a seasoned developer or simply beginning, this information will make it easier to select the most effective proxy supplier to fulfill your wants.
What Is a Proxy and Why Do Software program Builders and Testers Want It?
A proxy is an middleman server that sits between a consumer’s gadget and the web. It permits the consumer to make requests to net servers by way of the proxy server, which then processes the requests and returns the info to the consumer. This course of masks the consumer’s precise IP tackle, offering anonymity and safety.
Function of Proxies in Growth and Testing
Proxies play an important position in improvement and testing by enabling builders to simulate requests from totally different areas, check geo-targeted content material, and scrape knowledge from web sites with out getting blocked. They’re particularly helpful for automating duties like knowledge scraping, accessing region-restricted content material, and conducting load assessments.

Widespread Use Instances for Proxies in Growth and Testing
- Internet Scraping: Gathering knowledge from web sites with out being blocked.
- Testing Geo-targeted Content material: Making certain that content material is displayed accurately throughout totally different areas.
- Load Testing: Simulating excessive visitors to check the efficiency of purposes.
- Safety Testing: Analyzing how an utility responds to totally different safety threats.
Standards for Selecting the Finest Proxy Suppliers
When choosing a proxy supplier, there are a number of key elements to contemplate:
Velocity and Reliability
The pace of a proxy can considerably influence the efficiency of your testing and improvement. Dependable proxies guarantee constant uptime and fast knowledge retrieval, which is crucial for large-scale initiatives.
Safety and Anonymity
Safety is paramount when working with proxies. A very good proxy supplier ought to supply sturdy encryption, IP rotation, and excessive ranges of anonymity to guard your knowledge and identification.
Pricing and Scalability
Whether or not you’re engaged on a small challenge or want proxies for enterprise-level duties, pricing and scalability are crucial. Search for suppliers that provide versatile pricing plans and the power to scale up as your wants develop.
Buyer Help
Good buyer assist could make a world of distinction, particularly once you encounter technical points. Select suppliers that provide responsive and educated assist.
#1 Proxy Supplier: Proxys.io
Proxys.io is a top-tier proxy supplier identified for its reliability, pace, and intensive community of IP addresses. It gives a variety of proxies, together with residential, knowledge middle, and cell proxies, making it supreme for builders with numerous wants.
Key Options
- In depth Proxy Pool: Entry to tens of millions of IPs worldwide.
- Excessive Velocity: Optimized servers for fast knowledge retrieval.
- Sturdy Safety: Superior encryption and IP rotation.
- Consumer-Pleasant Dashboard: Simple to handle and configure proxies.
Pricing Plans
Proxys.io gives varied pricing tiers to cater to totally different customers, from small builders to giant enterprises. Plans begin at a aggressive fee, with choices for pay-as-you-go and month-to-month subscriptions.
Execs and Cons
Execs:
- Excessive pace and reliability
- Wonderful buyer assist
- Broad number of proxy varieties
Cons:
- Barely increased pricing in comparison with some opponents
Why It’s the Finest for Sofware Testers and Builders
Proxys.io stands out for its mixture of pace, reliability, and complete options. It’s significantly well-suited for tester builders who want sturdy proxies for large-scale testing and knowledge scraping.
Web site: https://proxys.io/en.
#2 Proxy Supplier: Smartproxy
Smartproxy is a widely known supplier providing an unlimited pool of residential proxies. It’s favored by builders for its user-friendly interface and excessive success fee in net scraping duties.
Key Options
- Residential Proxies: Actual IPs from ISPs throughout the globe.
- Rotating Proxies: Computerized IP rotation to keep away from bans.
- Superior Dashboard: Simple to make use of with detailed analytics.
Pricing Plans
Smartproxy’s pricing is aggressive, with versatile choices based mostly on bandwidth utilization. It gives month-to-month subscriptions with no long-term commitments.
Execs and Cons
Execs:
- Simple to make use of
- Excessive success fee in scraping
- Inexpensive pricing
Cons:
- Restricted to residential proxies
#3 Proxy Supplier: Vivid Knowledge
Vivid Knowledge, previously generally known as Luminati, is among the largest proxy networks globally. It gives a variety of proxy choices, together with residential, cell, and knowledge middle proxies.
Key Options
- International Protection: Entry to IPs in virtually each nation.
- Versatile Proxy Sorts: Residential, cell, and knowledge middle choices.
- Excessive Customization: Tailor proxies to particular wants.
Pricing Plans
Vivid Knowledge’s pricing is on the upper finish, reflecting its intensive community and premium options. It gives pay-as-you-go and subscription fashions.
Execs and Cons
Execs:
- In depth proxy community
- Excessive customization choices
- Wonderful security measures
Cons:
- Costly for small-scale builders
#4 Proxy Supplier: Oxylabs
Oxylabs is a premium proxy supplier identified for its enterprise-level companies. It gives an unlimited vary of proxies with a give attention to excessive efficiency and scalability.
Key Options
- Excessive Scalability: Appropriate for large-scale initiatives.
- Knowledge Heart and Residential Proxies: Big selection of choices.
- 24/7 Buyer Help: Round the clock help.
Pricing Plans
Oxylabs’ pricing is geared in direction of companies and huge groups, with versatile plans that may be personalized in accordance with particular wants.
Execs and Cons
Execs:
- Wonderful scalability
- Excessive-quality proxies
- Sturdy buyer assist
Cons:
- Not supreme for small builders because of price
#5 Proxy Supplier: Shifter
Overview of Shifter
Shifter gives dependable rotating proxies with a give attention to affordability. It’s an amazing possibility for builders who want constant efficiency with out breaking the financial institution.
Key Options
- Rotating Proxies: Computerized rotation to maintain your actions nameless.
- Inexpensive Plans: Aggressive pricing for small to medium initiatives.
- Simple Integration: Easy API for seamless integration.
Pricing Plans
Shifter’s pricing is budget-friendly, with a number of plans to select from, making it accessible for builders at totally different ranges.
Execs and Cons
Execs:
- Inexpensive
- Dependable rotating proxies
- Simple to make use of
Cons:
- Restricted options in comparison with premium suppliers
Comparability Desk of Prime 5 Proxy Suppliers
| Supplier |
Key Options |
Pricing |
Execs |
Cons |
| Proxys.io |
In depth proxy pool, excessive pace |
Average to excessive |
Velocity, reliability, buyer assist |
Larger pricing |
| Smartproxy |
Residential proxies, rotating IPs |
Inexpensive |
Consumer-friendly, excessive success fee |
Restricted to residential proxies |
| Vivid Knowledge |
International protection, excessive customization |
Premium pricing |
In depth community, customization |
Costly |
| Oxylabs |
Excessive scalability, 24/7 assist |
Enterprise-level |
Scalability, high quality, assist |
Expensive for small builders |
| Shifter |
Rotating proxies, affordability |
Funds-friendly |
Price-effective, straightforward integration |
Fewer options |
How one can Combine a Proxy Supplier into Your Growth Workflow
Integrating a proxy supplier into your improvement workflow is an easy course of. Right here’s a step-by-step information:
- Select Your Supplier: Primarily based in your wants, choose the most effective proxy supplier from the checklist above.
- Set Up an Account: Join and select the suitable plan.
- Configure the Proxies: Use the supplier’s dashboard to configure the proxy settings, together with IP rotation and area choice.
- Combine with Your Instruments: Join the proxies along with your improvement instruments utilizing the API or built-in integrations.
- Check the Setup: Run a number of assessments to make sure the proxies are working as anticipated.
- Monitor Efficiency: Keep watch over proxy efficiency and modify settings as wanted.
Widespread Challenges and Options When Utilizing Proxies
Connectivity Points
Generally proxies can face connectivity points because of server downtimes or community issues. The answer is to decide on a supplier with a excessive uptime assure and to have backup proxies in place.
IP Blocking and Rotation
Web sites might block sure IPs in the event that they detect suspicious exercise. Utilizing rotating proxies will help mitigate this problem by altering IP addresses regularly.
Dealing with Giant-Scale Requests
When coping with large-scale requests, efficiency can turn out to be a problem. Go for a supplier that provides excessive bandwidth and pace, and think about using a number of suppliers to distribute the load.
Why Utilizing A number of Proxy Suppliers Can Be Helpful
Utilizing a number of proxy suppliers can improve your testing and improvement efforts by diversifying your IP sources, lowering the chance of being blocked, and enhancing general reliability. It additionally means that you can leverage the strengths of various suppliers for varied duties.
Future Developments in Proxy Expertise for Builders
The way forward for proxy know-how is prone to see extra automation and AI-driven options, making proxy administration simpler and extra environment friendly. Enhanced security measures and the enlargement of proxy markets into rising areas can even be traits to look at.
Conclusion
Selecting the best proxy supplier is crucial for tester builders seeking to optimize their workflow and make sure the success of their initiatives. Proxys.io leads the pack with its glorious pace, reliability, and complete options. Nevertheless, relying in your particular wants, any of the highest 5 suppliers talked about on this article could possibly be the proper match. Take the time to judge your necessities and select the supplier that greatest aligns along with your improvement targets.
FAQs
What’s the distinction between a knowledge middle and residential proxy? Knowledge middle proxies are hosted in knowledge facilities and share IP addresses, making them sooner however much less nameless. Residential proxies are tied to actual gadgets and ISPs, providing increased anonymity.
How usually ought to I rotate my proxies? It’s really helpful to rotate proxies regularly, particularly throughout knowledge scraping or when accessing delicate websites, to keep away from detection and blocking.
Can I exploit free proxies for improvement? Free proxies can be utilized, however they usually lack reliability, pace, and safety. For severe improvement work, it’s higher to spend money on a good supplier.
What are the authorized concerns when utilizing proxies? Be certain that using proxies complies with native legal guidelines and the phrases of service of the web sites you’re accessing. Unlawful actions utilizing proxies can result in severe penalties.
How can I check the pace of my proxies? You should utilize instruments like pace assessments supplied by proxy suppliers or third-party companies to test the latency and pace of your proxies.