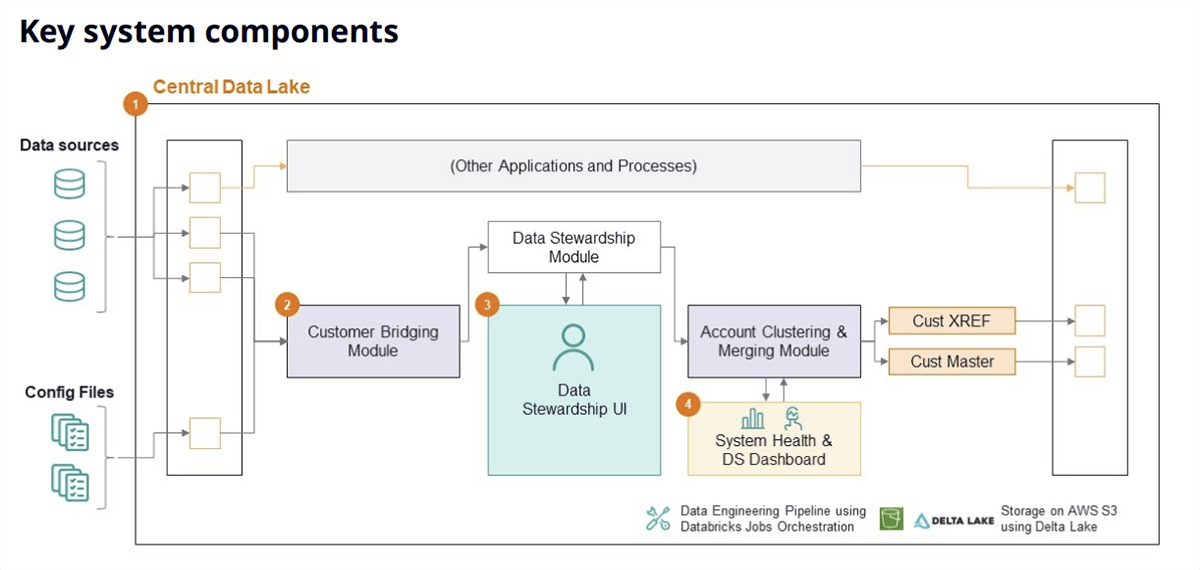
When you concentrate on all of the software program you utilize in your each day work and even in your personal life, you’ll quickly understand how advanced a system it really is. This complexity inevitably brings in potential safety points and vulnerabilities, and whereas there’s by no means just one weak hyperlink within the chain, it’s typically the job of the software program engineering staff to ensure that each the software program and {hardware} used stays protected.
On this article, I take a more in-depth take a look at how software program growth impacts the safety of organizational sources in at the moment’s panorama. Fashionable approaches have modified the methods we take into consideration our safety posture, as issues such because the elevated reputation of distant work have moved the goalposts from securing property inside a bodily location to securing information and property globally with the potential of them being accessed from anyplace at any time.
Whereas previously organizations approached their community safety with the mentality of “if it is in, it is safe,” this has confirmed to be a defective notion. Whereas making use of issues like community entry controls can positively assist mitigate potential points on-premises, this regardless raises one query: why inherently belief something within the first place? That is the place the idea of zero belief is available in.
With zero belief, we deal with each entity, person, and gadget alike as probably untrusted till we are able to confirm the entity and grant them any scope of entry. This strategy is very useful when contemplating the fashionable method of working, the place accessing sources remotely is gaining additional momentum daily. The potential assault vectors opened by permitting distant customers and distant gadgets to entry organizations’ networks should be mitigated to the perfect of our skills, and nil belief is an crucial constructing block of such a paradigm.
Nonetheless, zero belief is not only a matter of community safety; it blends in with software program engineering as effectively, as organizations must ensure that their software program helps zero belief approaches from the get-go. In lots of instances, this could require a complete mindset shift in addition to a reconfiguration or perhaps a rebuild of the methods used throughout the group, ensuring that safe by design is a core worth of the entire growth course of.
These days, we not anticipate any piece of software program to be a self-contained, easy software however reasonably part of a far more advanced suite of software program. With the growing demand for entry and functions to enterprise exterior of a singular pc and person house, we have to take excellent care to ensure that all methods keep as safe as attainable.
Contemplate a note-taking software from ages in the past: you had a little bit textual content field you wrote issues into after which saved the textual content file. At the moment, we would like to have the ability to share these recordsdata with our colleagues utilizing cloud companies like Google Drive or Microsoft OneDrive; we would like to have the ability to entry our notes on cell gadgets; and we would like elevated storage redundancy through the use of community file shares. All these required options demand that the software program engineers focus not solely on the precise characteristic set but additionally on making it tamper-proof with related entry administration controls.
Id and Entry Administration (IAM) handles entry to sources similar to gadgets, functions, and community recordsdata. This supervision takes place on a person person degree. Privileged Entry Administration (PAM) grants privileged customers the flexibility to make adjustments to those networks, gadgets, or functions. These are nice instruments for verifying, limiting, and limiting entry, however they have to be constructed into software program for us to take advantage of their capabilities.
Whereas chaos engineering, or deliberately injected failure testing for system resilience, is commonly checked out extra with the eyes of website reliability, it’s good to notice that each one of those points come right down to software program growth. When the failure is injected into the system, be it on a {hardware} or software program degree, the onus is on the software program to ensure the proper failure administration procedures are adopted.
Conventional testing, be it in direction of performance or safety, is, in fact, obligatory throughout software program growth. Nonetheless, it’s chaos engineering that’s used to throw the proverbial wrench into the system to actually confirm that every little thing does not break down when one thing surprising occurs. The principle purpose of this type of testing is to search out gaps within the failure course of, which could result in undesired outcomes. A bit of software program or a system crashing or locking up won’t in and of itself trigger a significant downside, however the potential for fallout in a posh chain of methods might find yourself doing that.
Components like useful resource exhaustion, information leakage, and defective error dealing with attributable to part of the system failing are issues that have to be addressed by the software program engineering staff, ensuring that when the surprising occurs, it is not going to trigger a breach throughout the community or gadgets linked to it. This all ties along with the resilience of the system, however on the finish of the day, it’s the software program engineering staff that has the accountability to make all of it work effectively collectively.
Organizational safety is not only the duty of 1 single division however reasonably a collaborative effort between everybody. Software program growth is one thing that touches all points of the system, from desktop functions to even hardware-level implementations, so adopting a safety mindset all through the software program growth life cycle is crucial for sustaining a powerful safety posture of the group.
Safety is a really advanced and nuanced matter, and there’s no common resolution to attain an honest degree of it. The elements outlined above play a vital function in fashionable software program engineering from a safety perspective, and may shed some mild on the ever-increasing complexity of the software program and {hardware} methods inside our organizations, together with highlighting the significance of a well-planned strategy to ensure that the group, its property, and customers keep protected for the long term.