SwiftIO is an digital circuit board that runs Swift on the naked steel. It could possibly management sensors, shows, lights, motors and extra.
The SwiftIO board
MadMachine’s SwiftIO board is an Arduino-like system, however it could run Swift code natively on the {hardware}. Swift is a good programming language for training functions, it’s a fashionable language with a JavaScript-like syntax that’s simple to study and perceive. Swift is protected and environment friendly, this mix makes it an ideal candidate for embedded techniques. The SwiftIO board allows us common Swift / iOS builders to construct IoT initiatives utilizing our favourite programming language.
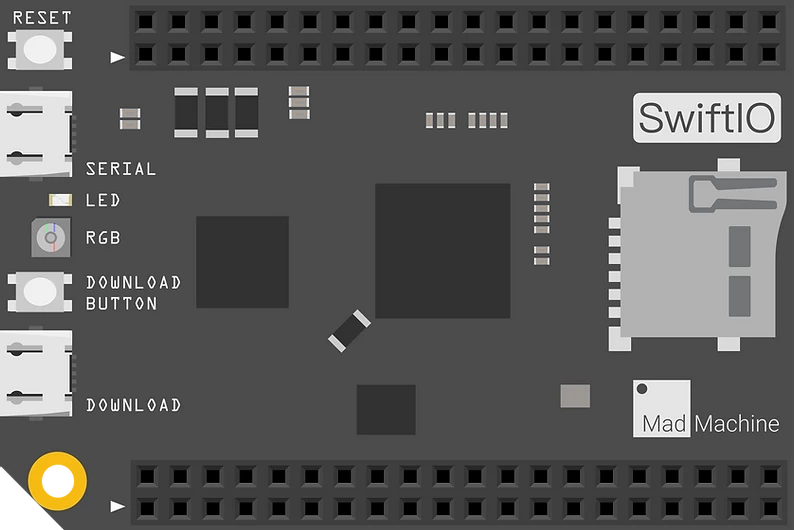
The board itself has a small footprint, it’s nearly 1,57” x 2,36” (4cm x 6cm) massive.
It’s fairly a strong microcontroller. It’s undoubtedly essentially the most inexpensive Swift language studying system. It may be best for STEM training functions for college students who need to see construct digital circuits and get some fundamental Swift programming expertise on the identical time.
The Maker Equipment field incorporates each a 7 section and an LCD show, a servo and a DC motor with drivers, a humiture (temperature & humidity) sensor, a buzzer module a potentiometer and a light-weight sensor and lots of extra different issues (breadboard, resistors, LEDs, buttons and cables, and many others.) that you need to use to construct the starter initiatives. You should have just about every thing within the field that you just want as a newcomer to get began and have some enjoyable time utilizing SwiftIO.
Sadly you received’t discover a working GPS, WiFi or Bluetooth module for the SwiftIO board but, however hopefully these type of equipment are just some months away. There’s a new defend and a model new display screen module within the works. Oh by the way in which a defend is one thing that you could plug into your board and join exterior equipment utilizing “particular” colourful cables.
Shields are boards that may be plugged on prime of the Arduino PCB extending its capabilities. The completely different shields comply with the identical philosophy as the unique toolkit: they’re simple to mount, and low cost to supply. – ArduinoShields
The board initially went on sale in July, 2020 and many individuals introduced it from all around the globe. New plug-ins, extensions and modules are nonetheless being developed by the makers, however you will need to emphasize that the SwiftIO board {hardware} is in a secure state.
Technical specs:
- i.MX RT1052 Crossover Processor with Arm® Cortex®-M7 core @600MHz
- Micro SD card slot, supporting customary and excessive capability SD playing cards
- Micro USB connector for energy
- On-board USB to UART for serial communication
- 46 GPIO on left and proper edges
- On-board GRB LED
- 12x 12-bit analog to digital (ADC) converters
- 4 UART, 2 CAN, 2 IIC, and a pair of SPI
- 14 PWM pins
- Many extra superior options to satisfy the wants of superior customers
Ports, communication, structure
You may join the SwiftIO board to your laptop through a USB connector, the 2 gadgets can talk by way of a serial port. The USB cable will present the required energy help, however alternatively you need to use an adapter or an exterior battery by way of a defend.
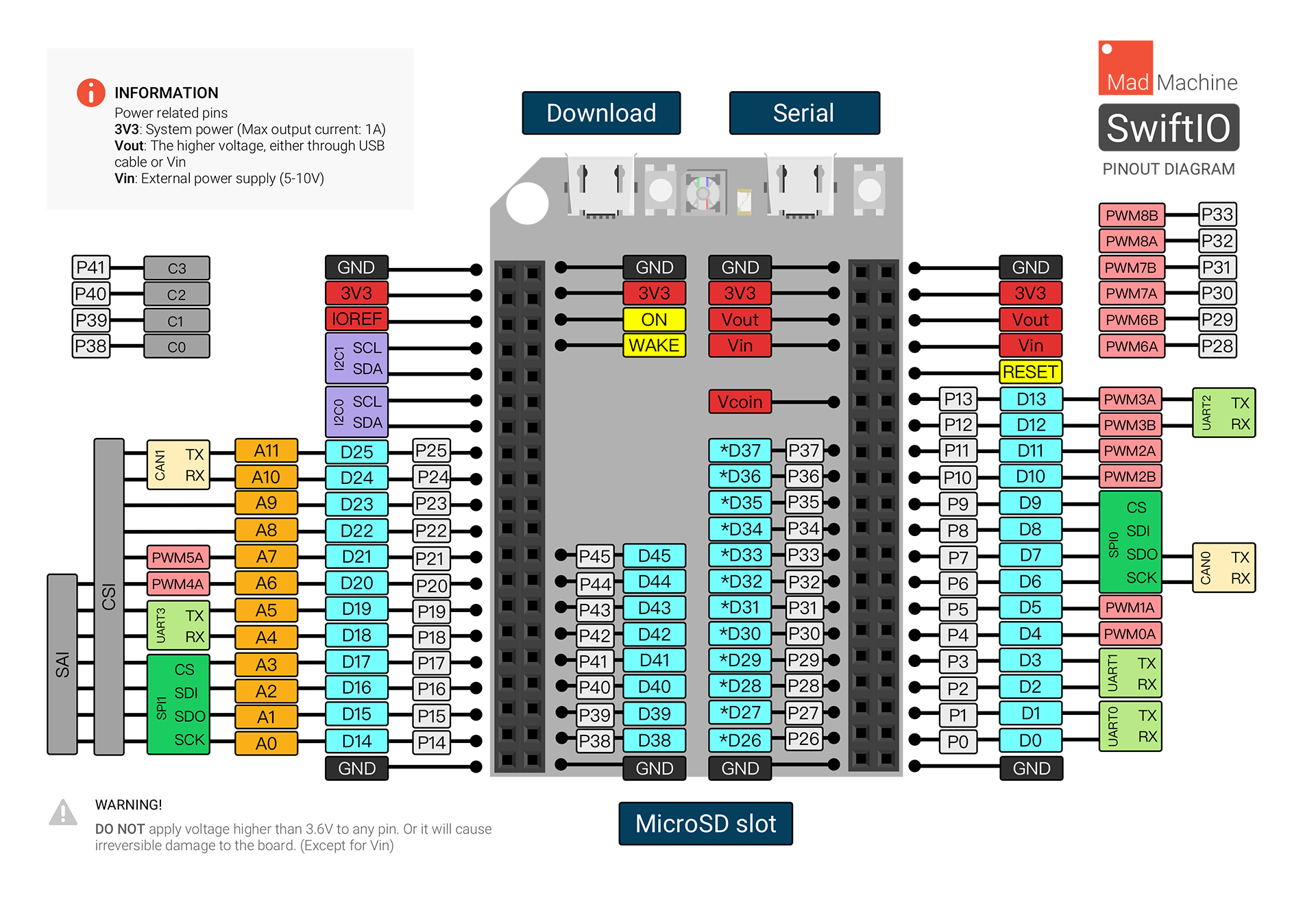
You may wire up extra elements utilizing the Common Goal Enter/Output pins (GPIO). You may see the precise specification on the image above, however truthfully I barely perceive this diagram.
Confession time: I don’t know shit about electronics (but).
The board can be utilized with a defend and happily the MakersKit arrives with a helpful instruction handbook for absolute freshmen. I felt fortunate, as a result of I used to be in a position to method this little gadget with my programmer mindset and I may focus extra on Swift as an alternative of constructing working circuits.
So what’s really underneath the hood? How can I construct & run functions for SwiftIO?
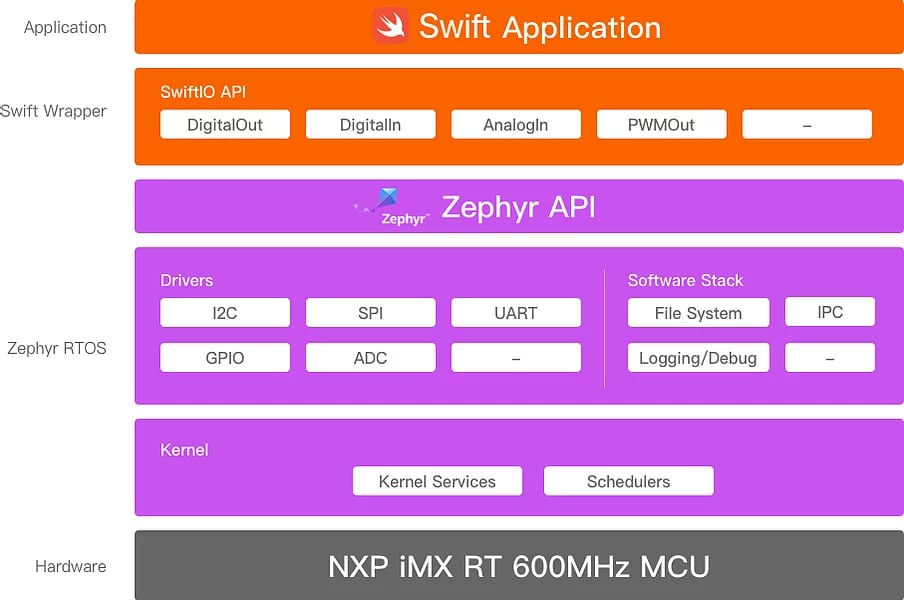
The grey space is the {hardware} itself, on prime of that within the pink-ish/purple packing containers there’s this Zephyr layer which I’ve by no means heard earlier than. I’m simply scratching the floor right here, however that’s positive, since as a Swift developer we solely care concerning the orange stuff. Lengthy story quick, there’s a customized constructed Swift toolchain for this system that permits us to construct and run Swift functions on the board.
If there’s a toolchain, then we will run Swift binaries, however how can we talk with the ports and stuff like that? Happily the SwiftIO framework is right here for us. It gives an easy accessibility to speak with exterior {hardware} equipment. You may learn or write digital and analog alerts utilizing the communication protocol. Are you prepared for some Swift code?
The SwiftIO atmosphere
Though the {hardware} is secure, the software program is just not completed but. There are two choices accessible, however if you’re on a Home windows machine, it is best to seize the official MadMachine IDE and use that. The reason being that the Swift Package deal Supervisor is just not prepared for that platform but, so that you received’t have the ability to work with the instruments that I’ll present you subsequent. Sorry Home windows, no offense.
So possibility A, is to go along with the IDE, it’s very easy to make use of and gives an awesome DX. Possibility B, study a bit extra concerning the underlying toolkit and comply with my information, it’s a bit extra sophisticated, however you’ll know extra concerning the technical infrastructure in the event you select this path.
Putting in the MadMachine SDK & CLI
As a macOS or Linux person it is best to know that you could set up the unofficial MadMachine SDK alongside a command line instrument referred to as mm. As you may see this MadMachine SDK is written in Swift, however it is best to know that I ported a python script from the unique mm-sdk undertaking with the assistance of Marcus Kida. First, he made an Xcode template by invoking the unique script contained in the official MadMachine IDE, then I assumed, it could be cool to eliminate the IDE for good, and now, right here we go, we’ve got a standalone Swift model of the required construct instruments. You may set up it like this:
git clone https://github.com/EmbeddedSwift/MadMachine.git
cd MadMachine
make set up
Now try to be prepared to make use of the mm cli app, you may verify the accessible instructions contained in the README file on GitHub. I’ve not examined this on Linux but, so in the event you discover any points, please don’t hesitate to report or submit a PR. That is an experimental undertaking, so preserve this in thoughts.
The MadMachine toolchain
With a purpose to use the MadMachine SDK you will want a working toolchain put in in your laptop. You may seize the most recent one by working the next command:
mm toolchain --upgrade
This may seize the most recent launch from the unofficial MadMachine toolchain repository, and place it underneath your own home folder contained in the .MadMachine listing. There’s one extra factor that now you need to do earlier than you could possibly begin constructing SwiftIO apps. At the moment there’s one further python script that was not ported but, as a result of it is going to be fully eradicated sooner or later. For now you continue to should obtain the official MadMachine SDK from the GitHub releases web page and place your entire contents of the mm-sdk/tools_[platform]/scripts/dist/gen_isr_tables folder into the ~/.MadMachine/legacy listing. You may need to create a legacy folder.
The SwiftIO framework
The SwiftIO framework goes to be linked with the applying binary, we’ve got to put in it (with the assistance of the mm-cli instrument) as a system library first. There’s an unofficial repo with a makefile for this:
git clone https://github.com/EmbeddedSwift/SwiftIO
cd SwiftIO
make set up
You could find the library reference for the SwiftIO framework, however we’ll see you can also make it work, in just some moments. Earlier than we go additional it is best to notice that the customized MadMachine toolchain is a modified model of the Swift 5.1 toolchain. This implies that you could’t use Swift 5.3 on the board but, however hopefully the creators of SwiftIO will launch new software program elements actual quickly.
Utilizing Xcode
The SwiftIO framework may be compiled in your native machine with the native Swift toolchain (utilizing Xcode), so it’s attainable to construct functions with out focusing on the board, and in a while you may re-compile the supply information with the mm-cli command, signal the ultimate binary and deploy it to the SwiftIO board after you’ve pressed the obtain button. That is the present workflow in a nutshell.
There’s an current Xcode template created by @kidmar that you need to use as a place to begin.
Utilizing SPM
These days I desire to create a Swift package deal for nearly every thing. You should utilize SPM with a Makefile and your favourite editor to create SwiftIO apps. You simply should initialize a brand new executable package deal with the required dependencies, for instance:
// swift-tools-version:5.3
import PackageDescription
let package deal = Package deal(
title: "myProject",
merchandise: [
.executable(name: "myProject", targets: ["myProject"]),
],
dependencies: [
.package(url: "https://github.com/EmbeddedSwift/SwiftIO", .branch("main")),
.package(url: "https://github.com/EmbeddedSwift/SHT3x", .branch("main")),
.package(url: "https://github.com/EmbeddedSwift/LCD1602", .branch("main")),
],
targets: [
.target(name: "myProject", dependencies: [
.product(name: "SwiftIO", package: "SwiftIO"),
.product(name: "SHT3x", package: "SHT3x"),
.product(name: "LCD1602", package: "LCD1602"),
]),
]
)
Contained in the most important.swift file now you may write a easy Humiture sensor app that shows the present humidity & temperature on a 16×2 LCD show like this:
import SwiftIO
import SHT3x
import LCD1602
// Get a quantity with one decimal place.
extension Float {
func format(_ f: Int) -> Float {
guard f > 0 else {return self}
var mul = 10
for _ in 1..Now in the event you open the Package deal.swift file utilizing Xcode you may even construct the undertaking domestically utilizing the CMD+B shortcut, however don’t attempt to run it, since your Mac is just not a SwiftIO board…
If you wish to construct and run this undertaking you need to goal the SwiftIO board. The mm-cli can’t resolve package deal dependencies (but) so you need to set up the required dependencies (SHT3x, LCD1602) the identical manner as we did with the SwiftIO library. You must clone each repositories and use the makefile to put in them as native MadMachine system libraries. This may transfer the required information underneath the ~/.MadMachine/libraries folder, all of the accessible libraries “stay” there.
After you’ve put in the libraries, you need to use the next Makefile for the precise binary builds:
construct:
mm construct --name myProject --binary-type executable --input . --output ./myProject
run: construct
mm board --run ./myProject/swiftio.bin
clear:
rm -r ./myProject
The mm construct command invokes the swiftc compiler from the SwiftIO toolchain with the precise search paths and library search paths. The mm board --run [binary] command will merely copy the required information to the MadMachine board whether it is in obtain mode. You must press the obtain button on the board earlier than you run this command. Urgent the obtain button will mount the SD card so we will deploy the signed binary to the system, then eject the storage, which can restart the board and the brand new utility might be loaded & executed immediately.
The MadMachine IDE
If you happen to don’t wish to play with command line utilities, you may at all times use the MadMachine IDE to construct and ship your initiatives. It makes use of a mmp file to explain dependencies, so it could resolve them on the fly, however I don’t like the truth that I’ve to make use of a brand new package deal supervisor and editor to work with Swift. I’m in a love and hate relationship with Xcode (plus I’m an old-school Chic Textual content fan).
Anyway, you will discover actually nice examples with a devoted GitHub repository and lots of video tutorials on the official YouTube channel. You may entry all of the MakerKit pattern codes, they’re each on GitHub and you’ll clone a template with a click on utilizing the MadMachine IDE.
Conclusion
For me, the SwiftIO board was a nice shock. I at all times needed to play with embedded techniques, know a bit extra about {hardware} and low degree stuff, however the Raspberry PI and the Arduino felt like alien planet. As soon as I’ve tried to construct an app for a Raspberry PI at a hackaton, nevertheless it was an entire catastrophe, I used to be upset, as a result of the instruments and the developer expertise was actually dangerous.
The promise of MadMachine is that you could simply use Swift on such a tool and I consider that Andy Liu created one thing that may have a vivid future on the long run. I felt in love with SwiftIO proper after I’ve assembled my first circuit and deployed my very first Swift supply. It was a seamless (ache free) expertise and I consider that’s a very vital issue for builders who by no means used such gadgets earlier than. This may be the start and the way forward for Swift on embedded techniques.
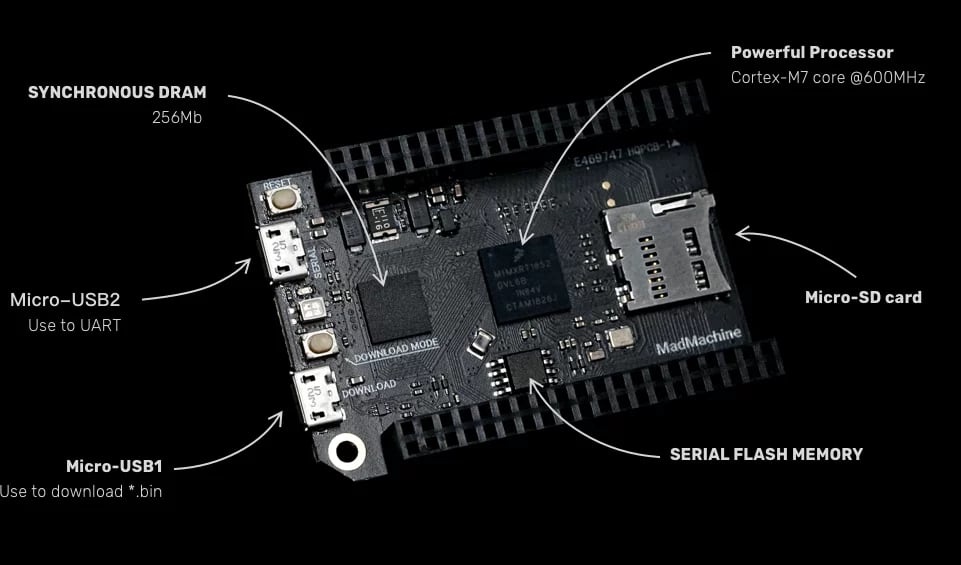
You may construct some actually enjoyable stuff with SwiftIO, it’s an ideal instrument for studying how electrical circuits work. I can’t wait to see increasingly sensors and libraries accessible for MadMachine. If in case you have an concept or a query be happy to hitch the official Discord server.






















