If you’re growing software program that can ship individuals into area, it’s good to make it possible for it really works as anticipated. In safety-critical methods like these, the method of unbiased verification and validation (IV&V) is meant to make sure that a product meets its necessities and capabilities as supposed. Whereas most IV&V strategies have been related to the waterfall mannequin of venture administration, an adoption of an Agile mindset and ideas permits IV&V groups to be extra aligned with modern software program improvement processes and produce higher outcomes. On this put up, I talk about how Agile ideas can work with IV&V processes, examples of how we put Agile IV&V into apply at NASA, and recommendation for transitioning to Agile.
IV&V
IV&V is a typical apply in the private and non-private sectors as a type of danger mitigation or as a part of compliance necessities. Usually, the means of verification asks, Are we constructing the product proper? In different phrases, Is the implementation of the product in keeping with the specification? Validation asks, Are we constructing the appropriate product? In different phrases, Does the product as specified align with the precise mission want?
Crucially, the unbiased a part of IV&V signifies that verification and validation are carried out by analysts who usually are not a part of the event staff. These processes had been developed to function a second set of eyes that might present better assurance of mission success. IEEE 1012, the business customary for verification and validation, units forth three parameters for independence: technical, managerial, and monetary. If a staff achieves these areas of independence, there may be much less probability of outdoor affect over the evaluation and findings, eradicating potential organizational conflicts of curiosity and permitting the staff to deal with the work at hand.
In apply, this strategy may cause pressure. The necessary nature of IV&V in lots of authorities initiatives can create an us versus them mentality. Furthermore, IV&V practices had been developed at a time when waterfall venture administration methodologies had been customary. In waterfall fashions, software program is developed sequentially, with necessities gathered first. Builders then create the design, implement it, and take a look at the software program. IV&V could be undertaken all through that course of with particular assessment gates serving as milestones for evaluation to be full. With extra software program groups transferring to Agile processes, nevertheless, IV&V analysts might discover themselves out of step with the event course of. In consequence, groups might discover that they aren’t receiving suggestions at mandatory factors within the improvement processes, leading to wasted work and emotions of frustration.
Agile Rules and Frameworks
Agile processes, in contrast, emphasize iterative and incremental improvement cycles. Initially proposed by a gaggle of software program builders in 2001, the Manifesto for Agile Software program Growth contains 4 values and 12 ideas that undergird Agile considering. These ideas emphasize buyer satisfaction, transparency, and adaptability—vital values for creating sturdy, collaborative working relationships between IV&V and improvement groups and a big a part of why Agile approaches have a lot to supply IV&V processes.
Many variations on Agile frameworks have emerged since 2001. Most embrace the idea of a backlog: a prioritized listing of labor that have to be accomplished by the staff. Groups seek advice from the backlog to plan out work and allocate assets. In contrast to waterfall approaches, improvement groups utilizing Agile don’t must plan out their work from the begin to end. By engaged on smaller timescales, they’ll modify extra rapidly to issues uncovered alongside the way in which. This contains challenges recognized within the IV&V course of. Under are examples of some widespread Agile frameworks and components which were useful in incorporating Agile strategies into IV&V.
Scrum
Scrum is a typical Agile framework utilized in a wide range of industries. The framework emphasizes groups working briefly sprints, sometimes for 2 to 4 weeks in length. These sprints are accompanied by various planning and check-in rituals to make sure steady communication and collaboration inside the staff. These rituals embrace an preliminary planning assembly the place the staff defines the objective of the upcoming dash and identifies any backlog gadgets that may be included. Moreover, many teams will maintain common (normally day by day) stand-up conferences the place staff members share progress and determine obstacles. After a dash is full, groups maintain retrospectives to evaluate the work accomplished and discover areas for enchancment.
Scrum additionally emphasizes self-managed groups. These groups have a excessive degree of autonomy to develop their very own plans and approaches to finishing work. The objective of a self-managed staff is to present members a way of possession and collective accountability for outcomes, with out work plans being imposed from the surface.
Scaled Agile Framework (SAFe)
SAFe is a set of processes that goals to facilitate Agile practices in bigger groups. There are a lot of challenges that bigger organizations face when implementing Agile workflows, and SAFe addresses extra complicated improvement processes, similar to the necessity to plan for an extended timescale with a planning interval (PI). The PI is a timeboxed sequence of improvement sprints adopted by a planning iteration. PIs are sometimes someplace between two to a few months in size, although they might be barely longer in authorities contexts. It’s our expertise that, within the extra common case of Agile at scale, structure performs an important position in success.
Agile for IV&V
With this background in Agile frameworks in thoughts, what does Agile appear to be within the IV&V context?
The primary a number of priorities within the Agile Manifesto are to “fulfill the client by early and steady supply” and to “ship working software program incessantly, from a few weeks to a few months, with a choice to the shorter timescale.” If we consider the deliverable in IV&V as assurance (quite than software program or a product), we are able to perceive the worth of Agile IV&V: quick, dependable assurance that works on the cadence that builders do. That is analogous to the continual authorization to function (ATO) that’s used throughout the Division of Protection (DoD), enhancing the safety posture of our DoD methods.
These ideas, nevertheless, usually require a tradition and mindset shift in IV&V. Analysts might want to transfer away from wanting on the entirety of the software program to working by smaller items, maybe on the degree of a person functionality or algorithm. Working in these smaller batches is a change from waterfall approaches, nevertheless it additionally permits groups to determine errors and incorporate fixes a lot quicker.
Past the sensible transition from waterfall venture administration kinds, Agile IV&V additionally requires transparency and elevated communication. Scrum rituals will be useful in constructing this tradition. For instance, dash planning and retrospectives give the entire staff perception into progress and permit staff members to talk about what’s (and isn’t) going nicely. Standup conferences that embrace dialogue of IV&V actions enhance transparency into day-to-day work and supply alternatives for fast suggestions and alignment.
Agile IV&V at NASA
Once I labored in venture administration at NASA’s Katherine Johnson IV&V Facility, I started implementing Agile IV&V. On the time, NASA was growing Orion, a multi-purpose crew car designed for the Artemis missions that can finally return astronauts to the moon. Orion’s software program is complicated, and the software program builders had moved to a SAFe mannequin, with main releases each three months. The IV&V analysts assigned to Orion had been used to extra conventional improvement fashions and had problem maintaining with the tempo of improvement, resulting in V&V findings being delivered to the software program developer typically months out of part.
Our staff acknowledged that we would have liked to take a distinct strategy. The SEI’s Will Hayes helped us perceive Agile ideas and the way they could possibly be used within the IV&V context. Will helped us outline our aims and incorporate Agile strategies into our assurance work. We adopted a number of practices, together with making use of a backlog, day by day stand-ups, and retrospectives.
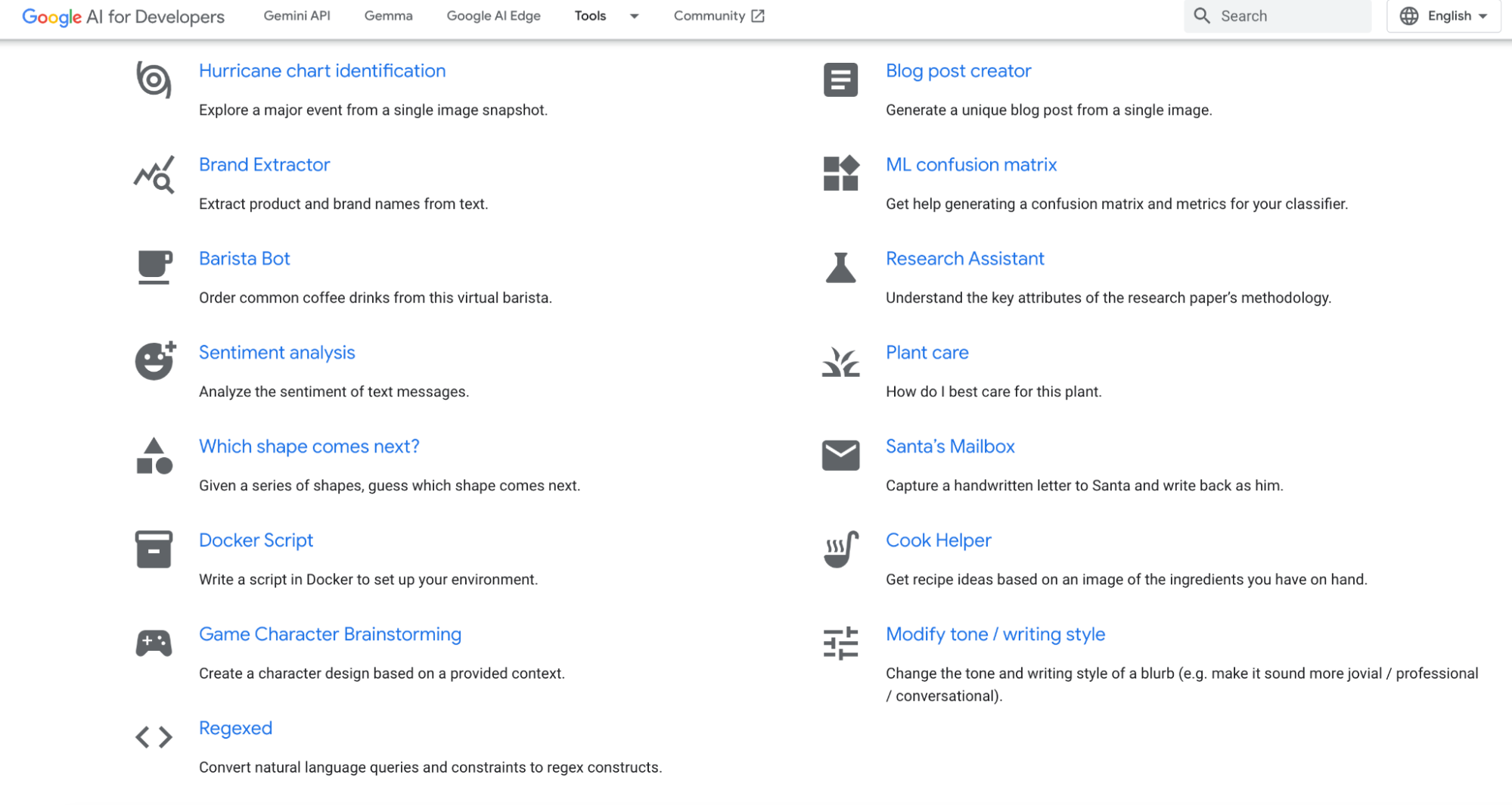
We would have liked to signify our work to our stakeholders to foster good communication between our groups and assist us plan extra effectively. To visualise our progress, we created a warmth map that confirmed our progress, areas of danger, and the general venture standing.
Every of the warmth map’s hexagons represents a selected functionality our staff was assessing for the Artemis I mission. By breaking apart the work into particular person capabilities, we introduced within the Agile idea of working in small increments, giving us the pliability to reprioritize and iterate as wanted. The analysts began by figuring out the important thing, top-level capabilities that had been mandatory for mission success. From there they independently recognized the capabilities that will be mandatory to ensure these top-level capabilities had been profitable. These capabilities had been then scored for danger utilizing a device developed by NASA’s IV&V program. The colours on the warmth map are these danger scores on a conventional danger scale: pink signifies {that a} functionality is on the highest degree of danger, yellow means that there’s some danger, and inexperienced signifies that the aptitude has the bottom degree of danger.
We used this warmth map and danger scores to assist us prioritize and handle our backlog throughout our PI classes, held thrice per yr. In these classes, we deliberate work for the next 4 months, specializing in the very best danger capabilities first.
As soon as we put these Agile ideas into motion, we noticed outstanding outcomes that every one stakeholders might simply perceive. Breaking apart the work into capabilities like we did, we might communicate to all ranges of this system in approach that made extra sense than simply talking when it comes to points discovered. From a technical perspective, the IV&V staff was capable of focus our work on essentially the most high-impact issues and riskiest areas quite than trivial defects. We had been additionally capable of lower our supply cadence from months to weeks, a time-frame far more according to the builders’ work. Merely put, we had been capable of produce higher, extra helpful work quicker than ever.
Higher Tradition, Higher Outcomes
At NASA, Agile IV&V gave analysts a deeper understanding of the methods they had been engaged on, in addition to higher communication with this system and improvement staff. Now as an Agile transformation chief working on the SEI with Will Hayes, I’m persevering with this work with our DoD prospects to assist transition IV&V practices.
Transferring to an Agile mindset is a tradition change. It requires belief, psychological security, and a willingness from the staff to strive one thing new. The excellent news is that Agile practices may also help foster these shifts and make adjustments alongside the way in which if one thing isn’t working. These ideas can work for small groups or giant groups as nicely. From an IV&V perspective, the important thing factor for our staff was the backlog of capabilities that we independently constructed. One other large piece for anybody transferring into Agile are a few of the rituals highlighted. These rituals may also help construct belief between improvement groups and analysts. As belief will increase, groups can be extra prone to talk tough points. When groups can discuss issues candidly and with out concern of reprisal, they’re extra prone to take calculated dangers, which may discover deeply hidden points and result in improvements in the way in which work is completed.