 Menace actors are abusing a method known as “URL rewriting” to cover their phishing hyperlinks from safety filters, based on researchers at Notion Level.
Menace actors are abusing a method known as “URL rewriting” to cover their phishing hyperlinks from safety filters, based on researchers at Notion Level.
 Menace actors are abusing a method known as “URL rewriting” to cover their phishing hyperlinks from safety filters, based on researchers at Notion Level.
Menace actors are abusing a method known as “URL rewriting” to cover their phishing hyperlinks from safety filters, based on researchers at Notion Level.
In a nutshell: An upcoming public firmware replace from Apple will seemingly point out a bug involving particular character combos in its changelog. Though the difficulty seems largely innocent for now, comparable exploits up to now have been used to crash gadgets and create new vulnerabilities.
Apple system customers not too long ago found a minor bug that causes the Settings display screen and residential display screen to crash. Whereas no critical points have been reported thus far, a repair in a future firmware replace wouldn’t be stunning.
Swiping proper on the iOS house display screen till the app library seems, after which typing the characters “::” into the search bar, causes Springboard – the software program that handles the primary menu – to crash. A black display screen with a loading icon briefly seems earlier than the system returns to the lock display screen.
Moreover, coming into the identical characters into the search bar on the high of the Settings menu crashes the app, instantly sending customers again to the house display screen. Nonetheless, the bug may be triggered by variations of this character mixture as properly.

Safety researchers have discovered that almost any mixture involving two citation marks, one colon, and some other character can set off the identical impact. For instance, typing “X”:X additionally causes the difficulty. TechSpot confirmed that the bug happens on iPhones and iPads operating firmware model 17.6.1, however Macs stay unaffected.
Researchers advised TechCrunch that the difficulty does not pose a safety menace. Nonetheless, the bug might increase some issues as a result of it resembles extra critical incidents from the previous.
In 2015, a selected string of textual content brought about stress when customers found it might lock them out of the Messages app and even reboot the iPhone. In 2017, customers discovered they may remotely crash an iPhone or iPad by sending a selected mixture of emojis over iMessage, iCloud, and the Notes app. One other crash triggered by a textual content string showing in notifications emerged in 2020.
Comparable distant exploits have allowed hackers to transmit spy ware by zero-click assaults. Packages like Pegasus pressured Apple to implement safety measures to guard delicate targets, similar to journalists and diplomats.
Google Pixel telephones additionally not too long ago encountered a harmful firmware-level flaw the place a hidden app accessed insecure servers, making gadgets weak to man-in-the-middle assaults.
Thankfully, the current iOS bug can solely be triggered by somebody bodily utilizing the system, so the potential danger stays restricted.
Yesterday marked the fifth anniversary of the Apple Card, which noticed an official launch on August 20, 2019. The Apple Card is Apple’s first and solely Apple-branded bank card, made out there in partnership with Goldman Sachs.

At launch, the Apple Card was solely out there in america, and at present, 5 years later, it’s nonetheless restricted to america and has not expanded to further international locations. Only a month after the Apple Card’s debut, Apple CEO Tim Prepare dinner stated that Apple was considering increasing the Apple Card to a number of international locations, however that it will take time resulting from varied laws all over the world.
There have been rumors of Apple Card talks in Europe, and Apple trademarked Apple Card in Europe, Hong Kong, and Canada, however no offers have emerged. Apple Card increasing to further international locations is much more up within the air with Apple’s upcoming decoupling from Goldman Sachs.
Apple is planning to finish its partnership with Goldman Sachs in 2025, and it might want to discover a new Apple Card supplier in america. Apple and Goldman Sachs bumped into bother with customer support points for disputed Apple Card transactions, in addition to complaints with wait instances for Apple Financial savings account withdrawals.
Goldman Sachs even ended up being investigated by the U.S. Shopper Monetary Safety Bureau due to buyer complaints, which led to a souring of the financial institution’s relationship with Apple. Goldman Sachs now plans to get out of client banking fully.
The Apple Card is a no-fee bank card with no annual charges, no worldwide charges, no charges for making a late fee, and no charges for exceeding a credit score restrict. There aren’t client protections like one may get with an American Categorical card, however there may be deep integration with the Pockets app for monitoring spending.
Apple gives 1 p.c Day by day Money again on all purchases, 2 p.c for Apple Pay purchases, and three p.c for Apple Pay purchases from the Apple Retailer. Day by day Money is distributed to clients every day, therefore the title.
Apple has not commented on the potential for increasing Apple Card to further international locations in a while, and there’s no phrase on whether or not that is nonetheless the plan.
Greater than 1,000,000 domains — together with many registered by Fortune 100 companies and model safety corporations — are weak to takeover by cybercriminals because of authentication weaknesses at quite a lot of massive webhosting suppliers and area registrars, new analysis finds.
Picture: Shutterstock.
Your Internet browser is aware of the best way to discover a website like instance.com because of the worldwide Area Title System (DNS), which serves as a sort of telephone e-book for the Web by translating human-friendly web site names (instance.com) into numeric Web addresses.
When somebody registers a site title, the registrar will usually present two units of DNS data that the client then must assign to their area. These data are essential as a result of they permit Internet browsers to search out the Web handle of the internet hosting supplier that’s serving that area.
However potential issues can come up when a site’s DNS data are “lame,” which means the authoritative title server doesn’t have sufficient details about the area and might’t resolve queries to search out it. A site can grow to be lame in quite a lot of methods, equivalent to when it isn’t assigned an Web handle, or as a result of the title servers within the area’s authoritative document are misconfigured or lacking.
The rationale lame domains are problematic is that quite a lot of Website hosting and DNS suppliers permit customers to assert management over a site with out accessing the true proprietor’s account at their DNS supplier or registrar.
If this risk sounds acquainted, that’s as a result of it’s hardly new. Again in 2019, KrebsOnSecurity wrote about thieves using this technique to grab management over hundreds of domains registered at GoDaddy, and utilizing these to ship bomb threats and sextortion emails (GoDaddy says they fastened that weak spot of their methods not lengthy after that 2019 story).
Within the 2019 marketing campaign, the spammers created accounts on GoDaddy and had been capable of take over weak domains just by registering a free account at GoDaddy and being assigned the identical DNS servers because the hijacked area.
Three years earlier than that, the identical pervasive weak spot was described in a weblog put up by safety researcher Matthew Bryant, who confirmed how one might commandeer no less than 120,000 domains by way of DNS weaknesses at a few of the world’s largest internet hosting suppliers.
Extremely, new analysis collectively launched at present by safety consultants at Infoblox and Eclypsium finds this identical authentication weak spot continues to be current at quite a lot of massive internet hosting and DNS suppliers.
“It’s straightforward to use, very onerous to detect, and it’s totally preventable,” stated Dave Mitchell, principal risk researcher at Infoblox. “Free providers make it simpler [to exploit] at scale. And the majority of those are at a handful of DNS suppliers.”
Infoblox’s report discovered there are a number of cybercriminal teams abusing these stolen domains as a globally dispersed “visitors distribution system,” which can be utilized to masks the true supply or vacation spot of internet visitors and to funnel Internet customers to malicious or phishous web sites.
Commandeering domains this fashion can also permit thieves to impersonate trusted manufacturers and abuse their constructive or no less than impartial status when sending e mail from these domains, as we noticed in 2019 with the GoDaddy assaults.
“Hijacked domains have been used immediately in phishing assaults and scams, in addition to massive spam methods,” reads the Infoblox report, which refers to lame domains as “Sitting Geese.” “There’s proof that some domains had been used for Cobalt Strike and different malware command and management (C2). Different assaults have used hijacked domains in focused phishing assaults by creating lookalike subdomains. A number of actors have stockpiled hijacked domains for an unknown function.”
Eclypsium researchers estimate there are presently about a million Sitting Duck domains, and that no less than 30,000 of them have been hijacked for malicious use since 2019.
“As of the time of writing, quite a few DNS suppliers allow this by weak or nonexistent verification of area possession for a given account,” Eclypsium wrote.
The safety companies stated they discovered quite a lot of compromised Sitting Duck domains had been initially registered by model safety corporations specializing in defensive area registrations (reserving look-alike domains for high manufacturers earlier than these names may be grabbed by scammers) and combating trademark infringement.
For instance, Infoblox discovered cybercriminal teams utilizing a Sitting Duck area known as clickermediacorp[.]com, which was a CBS Interactive Inc. area initially registered in 2009 at GoDaddy. Nevertheless, in 2010 the DNS was up to date to DNSMadeEasy.com servers, and in 2012 the area was transferred to MarkMonitor.
One other hijacked Sitting Duck area — anti-phishing[.]org — was registered in 2003 by the Anti-Phishing Working Group (APWG), a cybersecurity not-for-profit group that intently tracks phishing assaults.
In lots of circumstances, the researchers found Sitting Duck domains that seem to have been configured to auto-renew on the registrar, however the authoritative DNS or internet hosting providers weren’t renewed.
The researchers say Sitting Duck domains all possess three attributes that makes them weak to takeover:
1) the area makes use of or delegates authoritative DNS providers to a distinct supplier than the area registrar;
2) the authoritative title server(s) for the area doesn’t have details about the Web handle the area ought to level to;
3) the authoritative DNS supplier is “exploitable,” i.e. an attacker can declare the area on the supplier and arrange DNS data with out entry to the legitimate area proprietor’s account on the area registrar.
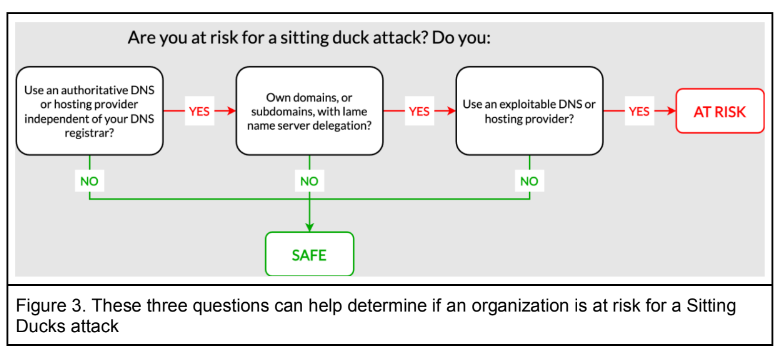
Picture: Infoblox.
How does one know whether or not a DNS supplier is exploitable? There’s a often up to date record printed on GitHub known as “Can I take over DNS,” which has been documenting exploitability by DNS supplier over the previous a number of years. The record contains examples for every of the named DNS suppliers.
Within the case of the aforementioned Sitting Duck area clickermediacorp[.]com, the area seems to have been hijacked by scammers by claiming it on the webhosting agency DNSMadeEasy, which is owned by Digicert, one of many trade’s largest issuers of digital certificates (SSL/TLS certificates).
In an interview with KrebsOnSecurity, DNSMadeEasy founder and senior vice chairman Steve Job stated the issue isn’t actually his firm’s to resolve, noting that DNS suppliers who’re additionally not area registrars haven’t any possible way of validating whether or not a given buyer legitimately owns the area being claimed.
“We do shut down abusive accounts once we discover them,” Job stated. “But it surely’s my perception that the onus must be on the [domain registrants] themselves. In the event you’re going to purchase one thing and level it someplace you don’t have any management over, we will’t stop that.”
Infoblox, Eclypsium, and the DNS wiki itemizing at Github all say that webhosting big Digital Ocean is among the many weak internet hosting companies. In response to questions, Digital Ocean stated it was exploring choices for mitigating such exercise.
“The DigitalOcean DNS service will not be authoritative, and we’re not a site registrar,” Digital Ocean wrote in an emailed response. “The place a site proprietor has delegated authority to our DNS infrastructure with their registrar, they usually have allowed their possession of that DNS document in our infrastructure to lapse, that turns into a ‘lame delegation’ below this hijack mannequin. We imagine the basis trigger, in the end, is poor administration of area title configuration by the proprietor, akin to leaving your keys in your unlocked automobile, however we acknowledge the chance to regulate our non-authoritative DNS service guardrails in an effort to assist decrease the influence of a lapse in hygiene on the authoritative DNS stage. We’re related with the analysis groups to discover further mitigation choices.”
In a press release supplied to KrebsOnSecurity, the internet hosting supplier and registrar Hostinger stated they had been working to implement an answer to stop lame duck assaults within the “upcoming weeks.”
“We’re engaged on implementing an SOA-based area verification system,” Hostinger wrote. “Customized nameservers with a Begin of Authority (SOA) document can be used to confirm whether or not the area actually belongs to the client. We intention to launch this user-friendly resolution by the top of August. The ultimate step is to deprecate preview domains, a performance generally utilized by clients with malicious intents. Preview domains can be deprecated by the top of September. Legit customers will have the ability to use randomly generated short-term subdomains as a substitute.”
What did DNS suppliers which have struggled with this subject up to now do to deal with these authentication challenges? The safety companies stated that to assert a site title, the most effective observe suppliers gave the account holder random title servers that required a change on the registrar earlier than the domains might go stay. Additionally they discovered the most effective observe suppliers used numerous mechanisms to make sure that the newly assigned title server hosts didn’t match earlier title server assignments.
[Side note: Infoblox observed that many of the hijacked domains were being hosted at Stark Industries Solutions, a sprawling hosting provider that appeared two weeks before Russia invaded Ukraine and has become the epicenter of countless cyberattacks against enemies of Russia].
Each Infoblox and Eclypsium stated that with out extra cooperation and fewer finger-pointing by all stakeholders within the world DNS, assaults on sitting duck domains will proceed to rise, with area registrants and common Web customers caught within the center.
“Authorities organizations, regulators, and requirements our bodies ought to take into account long-term options to vulnerabilities within the DNS administration assault floor,” the Infoblox report concludes.
At present, Confluent introduced the overall availability of its serverless Apache Flink service. Flink is among the hottest stream processing applied sciences, ranked as a high 5 Apache challenge and backed by a various committer group together with Alibaba and Apple. It powers steam processing at many corporations together with Uber, Netflix, and Linkedin.
Rockset clients utilizing Flink typically share how difficult it’s to self-manage Flink for streaming transformations. That’s why we’re thrilled that Confluent Cloud is making it simpler to make use of Flink, offering environment friendly and performant stream processing whereas saving engineers from advanced infrastructure administration.
Whereas it is well-known that Flink excels at filtering, becoming a member of and enriching streaming knowledge from Apache Kafka® or Confluent Cloud, what’s much less recognized is that it’s more and more turning into ingrained within the end-to-end stack for AI-powered purposes. That’s as a result of efficiently deploying an AI utility requires retrieval augmented era or “RAG” pipelines, processing real-time knowledge streams, chunking knowledge, producing embeddings, storing embeddings and operating vector search.
On this weblog, we’ll talk about how RAG suits into the paradigm of real-time knowledge processing and present an instance product advice utility utilizing each Kafka and Flink on Confluent Cloud along with Rockset.
LLMs like ChatGPT are educated on huge quantities of textual content knowledge accessible as much as a cutoff date. As an example, GPT-4’s cutoff date was April 2023, so it could not pay attention to any occasions or developments occurring past that time of time. Moreover, whereas LLMs are educated on a big corpus of textual content knowledge, they aren’t educated to the specifics of a site, use case or possess inner firm information. This data is what offers many purposes their relevance, producing extra correct responses.
LLMs are additionally susceptible to hallucinations, or making up inaccurate responses. By grounding responses in retrieval data, LLMs can draw on dependable knowledge for his or her response as an alternative of solely counting on their pre-existing information base.
Constructing a real-time, contextual and reliable information base for AI purposes revolves round RAG pipelines. These pipelines take contextual knowledge and feed it into an LLM to enhance the relevancy of a response. Let’s check out every step in a RAG pipeline within the context of constructing a product advice engine:
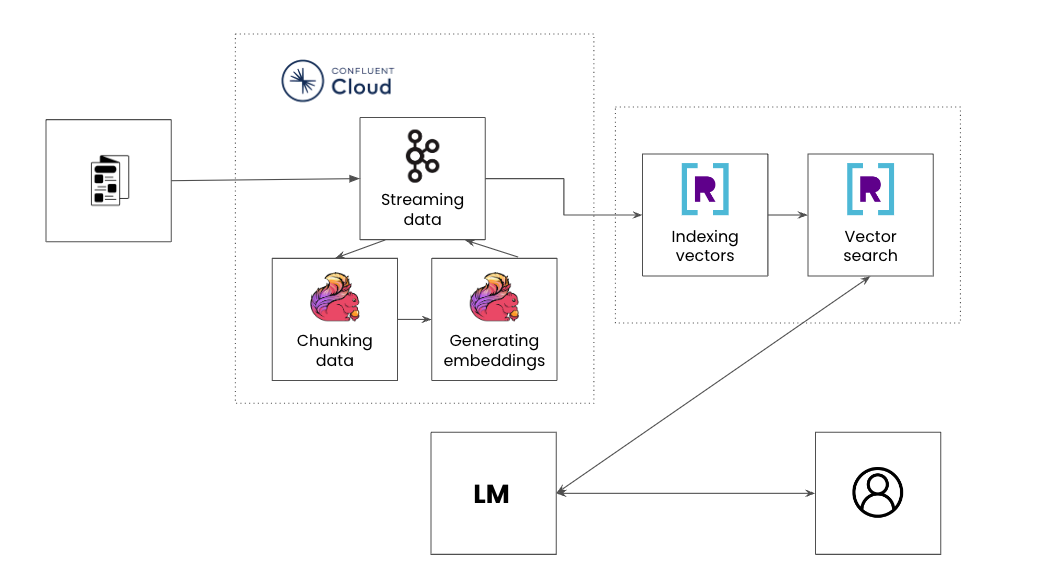
Whereas a RAG pipeline captures the precise steps to construct AI purposes, these steps resemble a conventional stream processing pipeline the place knowledge is streamed from a number of sources, enriched and served to downstream purposes. AI-powered purposes even have the identical set of necessities as every other user-facing utility, its backend companies must be dependable, performant and scalable.
Streaming-first architectures are a obligatory basis for the AI period. A product suggestions utility is way more related if it could actually incorporate alerts about what merchandise are in inventory or will be shipped inside 48 hours. If you find yourself constructing purposes for constant, real-time efficiency at scale it would be best to use a streaming-first structure.
There are a number of challenges that emerge when constructing real-time RAG pipelines:
Within the following sections, we’ll talk about these challenges broadly and delve into how they apply extra particularly to vector search and vector databases.
Quick suggestions on contemporary knowledge require the RAG pipeline to be designed for streaming knowledge. In addition they must be designed for real-time updates. For a product catalog, the most recent objects have to have embeddings generated and added to the index.
Indexing algorithms for vectors don’t natively assist updates properly. That’s as a result of the indexing algorithms are fastidiously organized for quick lookups and makes an attempt to incrementally replace them with new vectors quickly deteriorate the quick lookup properties. There are a lot of potential approaches {that a} vector database can use to assist with incremental updates- naive updating of vectors, periodic reindexing, and many others. Every technique has ramifications for the way rapidly new vectors can seem in search outcomes.
Streaming knowledge on merchandise in a catalog is used to generate vector embeddings in addition to present extra contextual data. For instance, a product advice engine might wish to present related merchandise to the final product a person searched (vector search) which can be extremely rated (structured search) and accessible for transport with Prime (structured search). These extra inputs are known as metadata filtering.
Indexing algorithms are designed to be massive, static and monolithic making it troublesome to run queries that be a part of vectors and metadata effectively. The optimum strategy is single-stage metadata filtering that merges filtering with vector lookups. Doing this successfully requires each the metadata and the vectors to be in the identical database, leveraging question optimizations to drive quick response instances. Virtually all AI purposes will wish to embody metadata, particularly real-time metadata. How helpful would your product advice engine be if the merchandise beneficial was out of inventory?
AI purposes can get very costly in a short time. Producing vector embeddings and operating vector indexing are each compute-intensive processes. The power of the underlying structure to assist streaming knowledge for predictable efficiency, in addition to scale up and down on demand, will assist engineers proceed to leverage AI.
In lots of vector databases, indexing of vectors and search occur on the identical compute clusters for quicker knowledge entry. The draw back of this tightly coupled structure, typically seen in programs like Elasticsearch, is that it can lead to compute rivalry and provisioning of assets for peak capability. Ideally, vector search and indexing occur in isolation whereas nonetheless accessing the identical real-time dataset.
Confluent Cloud for Apache Flink and Rockset, the search and analytics database constructed for the cloud, are designed to assist high-velocity knowledge, real-time processing and disaggregation for scalability and resilience to failures.
Listed here are the advantages of utilizing Confluent Cloud for Apache Flink and Rockset for RAG pipelines:
Let’s now take a look at how we will leverage Kafka and Flink on Confluent Cloud with Rockset to construct a real-time RAG pipeline for an AI-powered suggestions engine.
For this instance AI-powered advice utility, we’ll use a publicly accessible Amazon product critiques dataset that features product critiques and related metadata together with product names, options, costs, classes and descriptions.
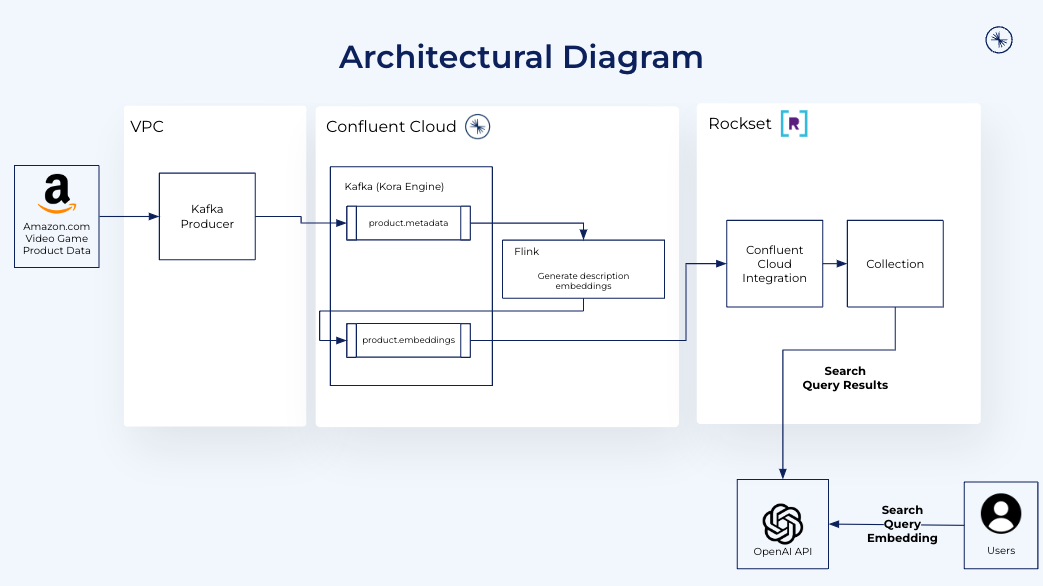
We’ll discover essentially the most related video video games to Starfield which can be suitable with the Ps console. Starfield is a well-liked online game on Xbox and players utilizing Ps might wish to discover related video games that work with their setup. We’ll use Kafka to stream product critiques, Flink to generate product embeddings and Rockset to index the embeddings and metadata for vector search.
Confluent Cloud is a fully-managed knowledge streaming platform that may stream vectors and metadata from wherever the supply knowledge resides, offering easy-to-use native connectors. Its managed service from the creators of Apache Kafka affords elastic scalability, assured resiliency with a 99.99% uptime SLA and predictable low latency.
We setup a Kafka producer to publish occasions to a Kafka cluster. The producer ingests Amazon.com product catalog knowledge in actual time and sends it to Confluent Cloud. It runs java utilizing docker compose to create the Kafka producer and Apache Flink.
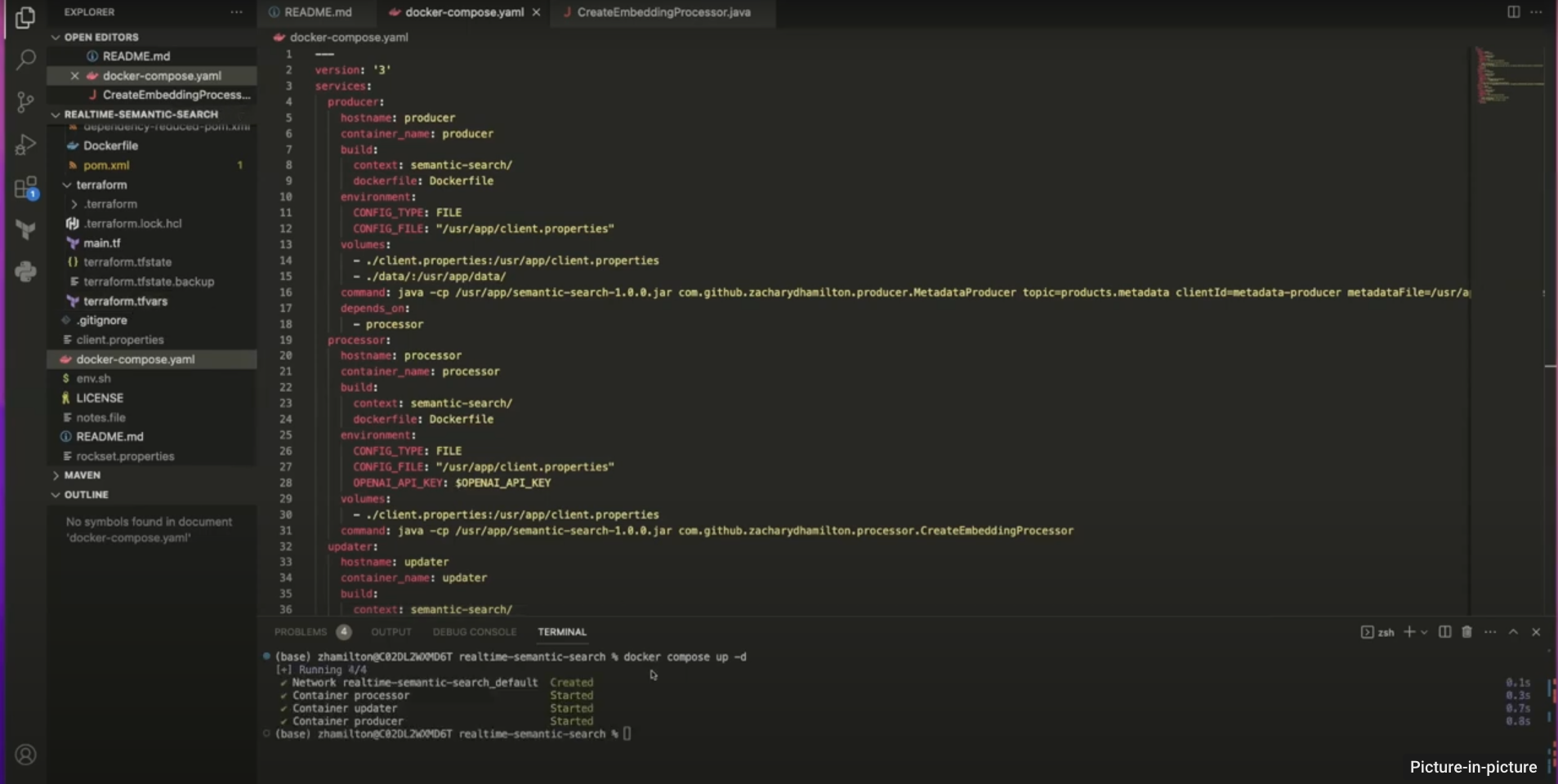
In Confluent Cloud, we create a cluster for the AI-powered product suggestions with the subject of product.metadata.
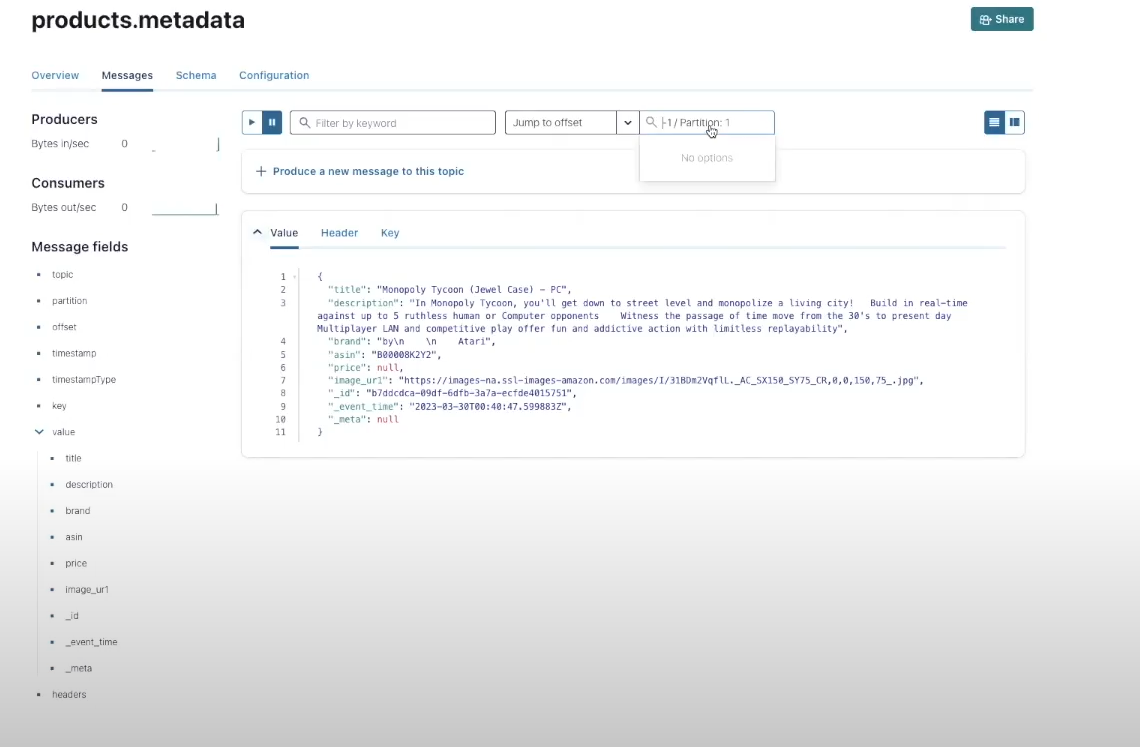
Simply filter, be a part of and enrich the Confluent knowledge stream with Flink, the de facto customary for stream processing, now accessible as a serverless, fully-managed answer on Confluent Cloud. Expertise Kafka and Flink collectively as a unified platform, with absolutely built-in monitoring, safety and governance.
To course of the merchandise.metadata and generate vector embeddings on the fly we use Flink on Confluent Cloud. Throughout stream processing, every product evaluate is consumed one-by-one, evaluate textual content is extracted and despatched to OpenAI to generate vector embeddings and vector embeddings are hooked up as occasions to a newly created merchandise.embeddings subject. As we don’t have an embedding algorithm in-house for this instance, we’ve to create a user-defined perform to name out to OpenAI and generate the embeddings utilizing self-managed Flink.
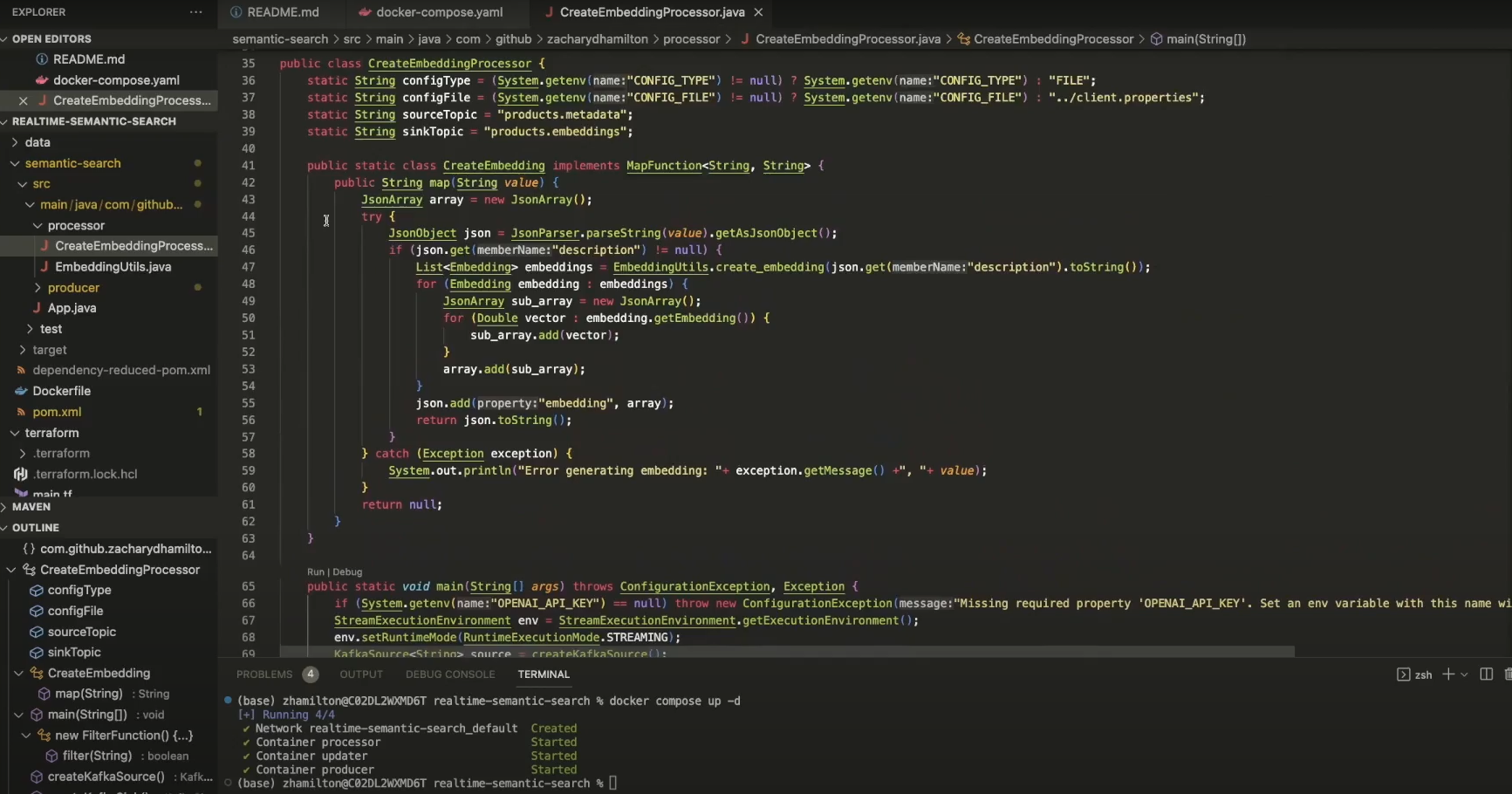
We are able to return to the Confluent console and discover the merchandise.embeddings subject created utilizing Flink and OpenAI.
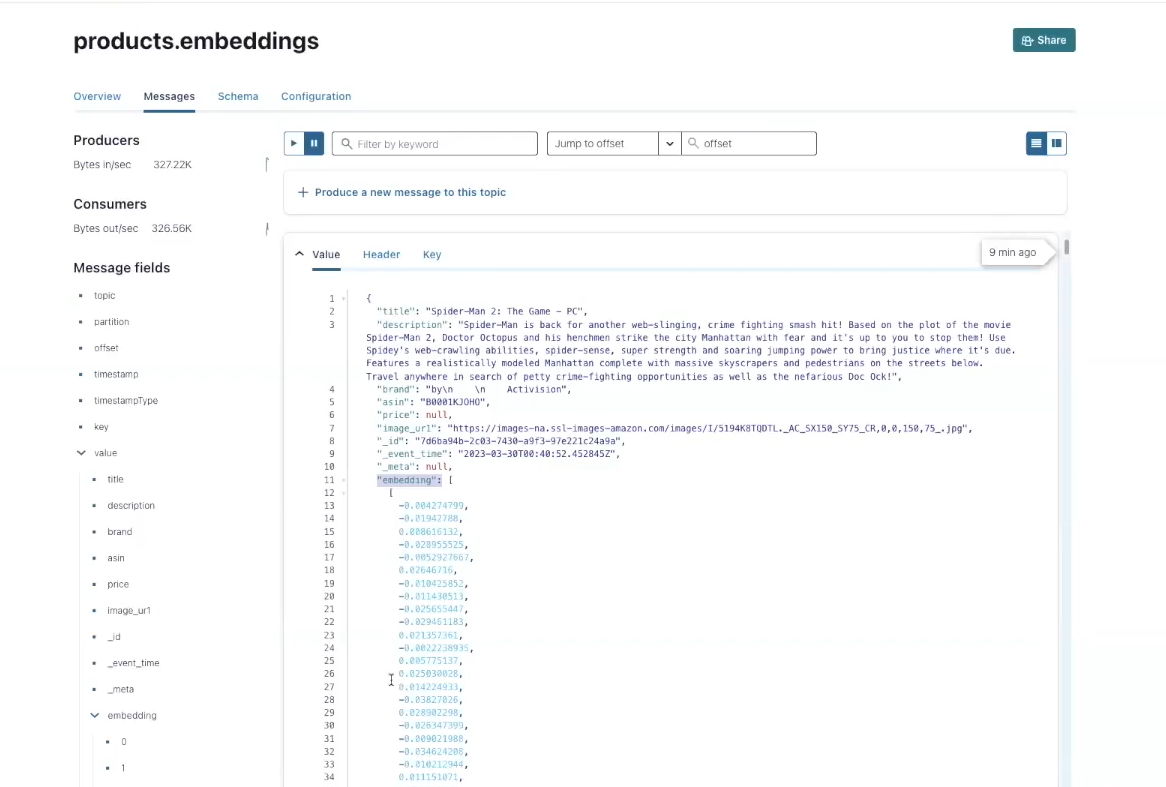
Rockset is the search and analytics database constructed for the cloud with a local integration to Kafka for Confluent Cloud. With Rockset’s cloud-native structure, indexing and vector search happen in isolation for environment friendly, predictable efficiency. Rockset is constructed on RocksDB and helps incremental updating of vector indexes effectively. Its indexing algorithms are primarily based on the FAISS library, a library that’s well-known for its assist of updates.
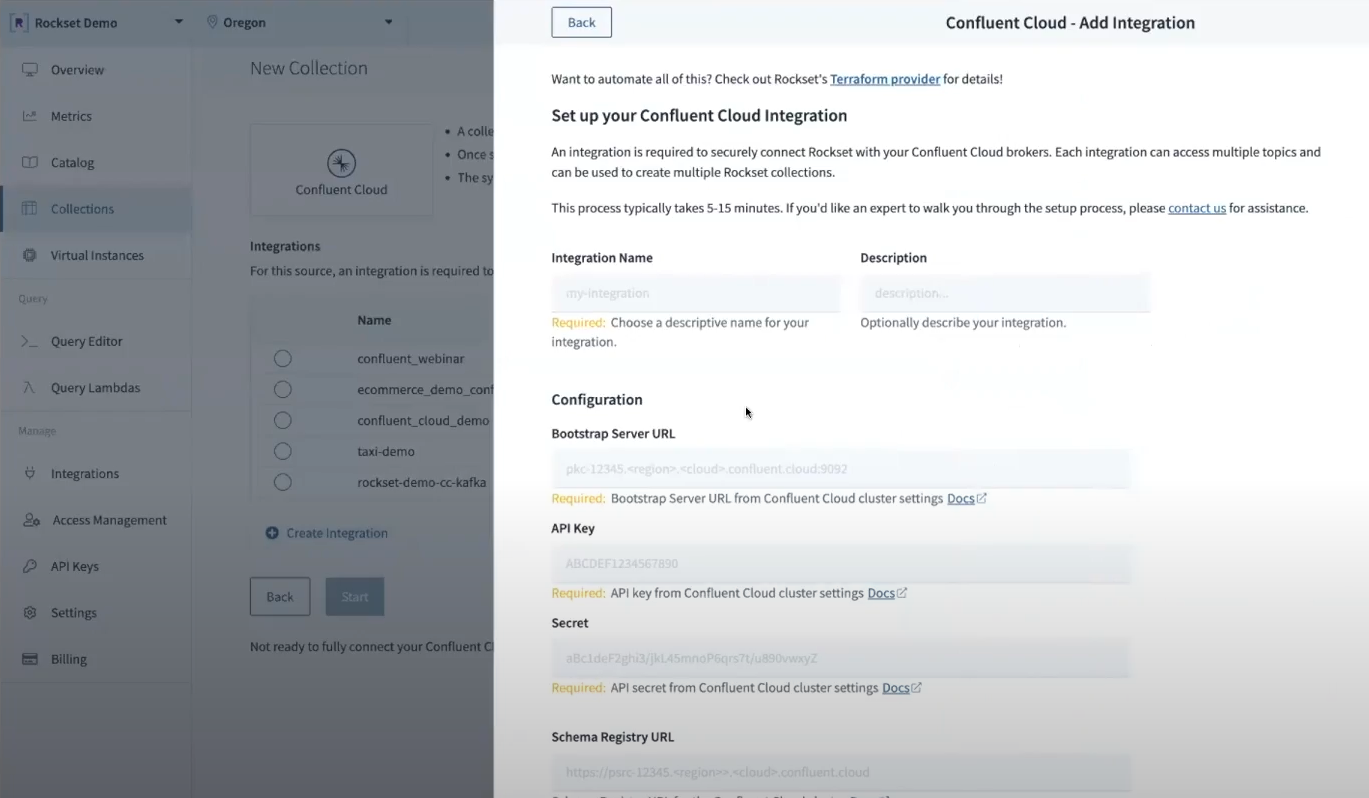
Rockset acts as a sink for Confluent Cloud, choosing up streaming knowledge from the product.embeddings subject and indexing it for vector search.
On the time a search question is made, ie “discover me all the same embeddings to time period “house wars” which can be suitable with Ps and beneath $50,” the appliance makes a name to OpenAI to show the search time period “house wars” right into a vector embedding after which finds essentially the most related merchandise within the Amazon catalog utilizing Rockset as a vector database. Rockset makes use of SQL as its question language, making metadata filtering as simple as a SQL WHERE clause.
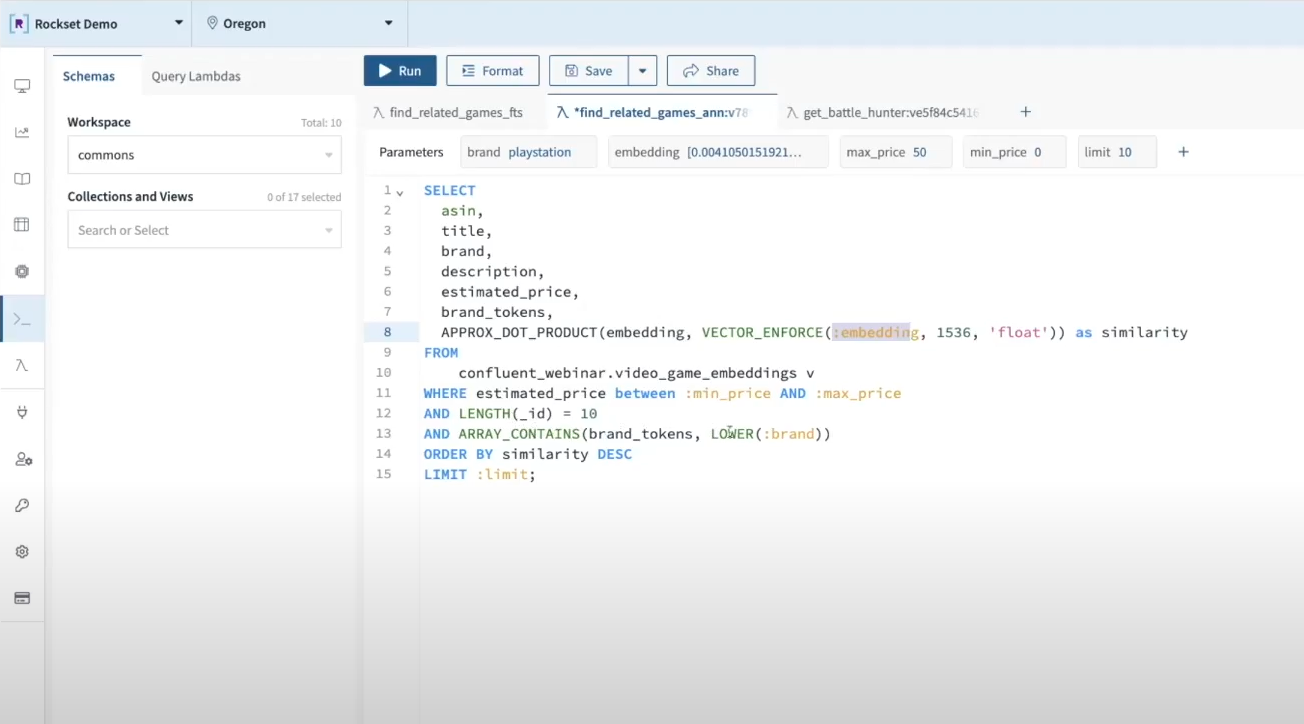
Confluent’s serverless Flink providing completes the end-to-end cloud stack for AI-powered purposes. Engineering groups can now deal with constructing subsequent era AI purposes quite than managing infrastructure. The underlying cloud companies scale up and down on demand, guaranteeing predictable efficiency with out the pricey overprovisioning of assets.
As we walked by way of on this weblog, RAG pipelines profit from real-time streaming architectures, seeing enhancements within the relevance and trustworthiness of AI purposes. When designing for real-time RAG pipelines the underlying stack ought to assist streaming knowledge, updates and metadata filtering as first-class residents.
Constructing AI-applications on streaming knowledge has by no means been simpler. We walked by way of the fundamentals of constructing an AI-powered product advice engine on this weblog. You may reproduce these steps utilizing the code discovered on this GitHub repository. Get began constructing your individual utility as we speak with free trials of Confluent Cloud and [Rockset].
Embedded content material: https://youtu.be/mvkQjTIlc-c?si=qPGuMtCOzq9rUJHx
Observe: The Amazon Evaluation dataset was taken from: Justifying suggestions utilizing distantly-labeled critiques and fine-grained features Jianmo Ni, Jiacheng Li, Julian McAuley Empirical Strategies in Pure Language Processing (EMNLP), 2019. It incorporates precise merchandise however they’re just a few years previous