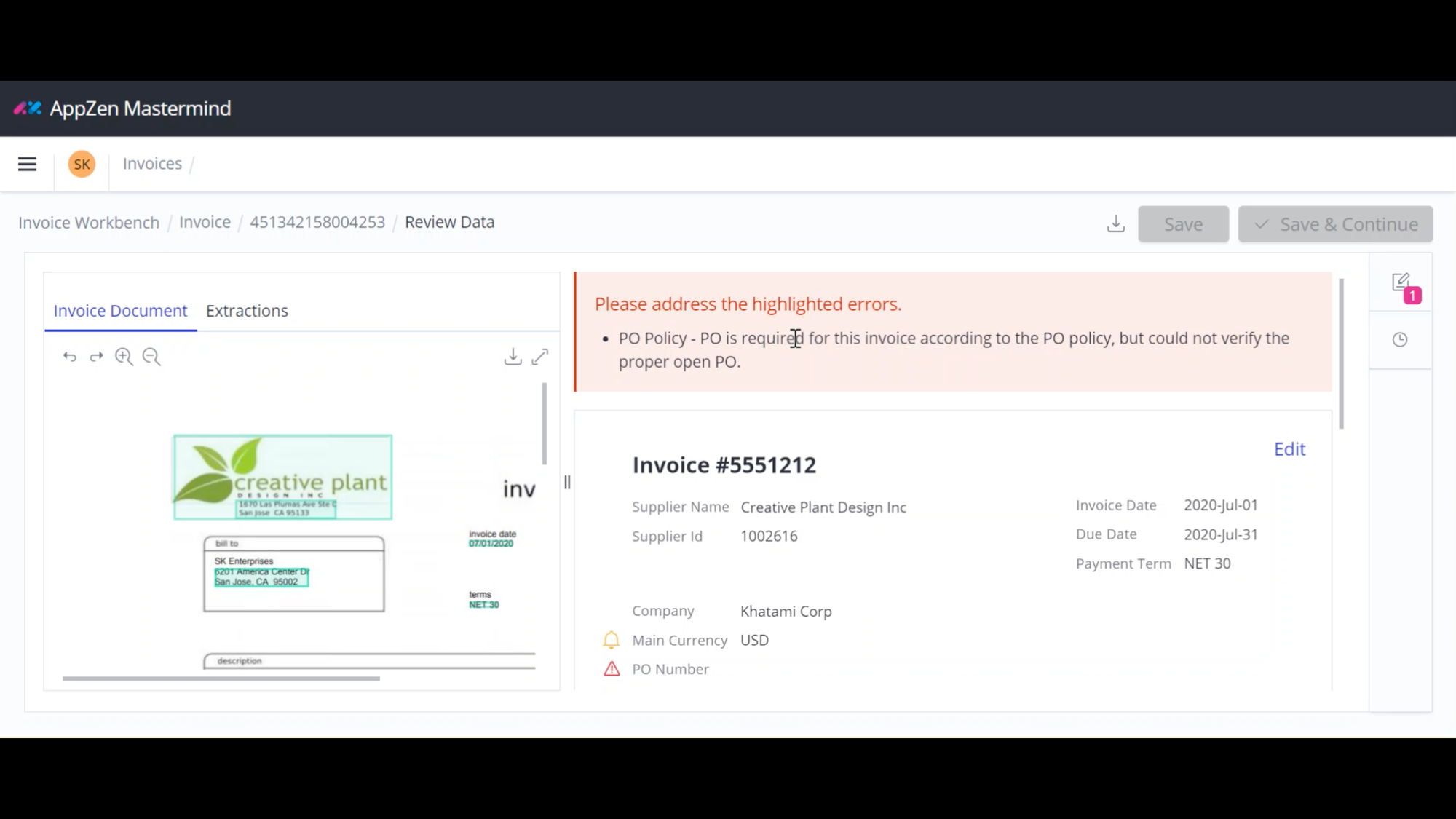
ESET researchers found two beforehand unknown backdoors – which we named LunarWeb and LunarMail – compromising a European ministry of international affairs (MFA) and its diplomatic missions overseas. We consider that the Lunar toolset has been used since no less than 2020 and, given the similarities between the instruments’ ways, strategies, and procedures (TTPs) and previous actions, we attribute these compromises to the notorious Russia-aligned cyberespionage group Turla, with medium confidence. We lately offered our insights from this analysis at this yr’s ESET World convention and supply extra particulars about our findings on this blogpost.
Key factors of the blogpost:
- ESET Analysis found two beforehand unknown backdoors – LunarWeb and LunarMail – used within the compromise of a European MFA and its diplomatic missions.
- LunarWeb, deployed on servers, makes use of HTTP(S) for its C&C communications and mimics reputable requests, whereas LunarMail, deployed on workstations, is continued as an Outlook add-in and makes use of e-mail messages for its C&C communications.
- Each backdoors make use of the strategy of steganography, hiding instructions in photos to keep away from detection.
- Each backdoors make the most of a loader that makes use of the DNS area identify for decryption of the payload, share parts of their codebases, and have the weird functionality of having the ability to execute Lua scripts.
- The loader can have varied types, together with trojanized open-source software program, demonstrating the superior strategies utilized by the attackers.
Turla, also called Snake, has been energetic since no less than 2004, presumably even courting again to the late Nineties. Believed to be a part of the Russian FSB, Turla primarily targets high-profile entities akin to governments and diplomatic organizations in Europe, Central Asia, and the Center East. The group is infamous for breaching main organizations, together with the US Division of Protection in 2008 and the Swiss protection firm RUAG in 2014. Over the previous few years, we have documented a massive half of Turla’s arsenal on WeLiveSecurity.
Our present investigation started with the detection of a loader decrypting and working a payload, from an exterior file, on an unidentified server. This led us to the invention of a beforehand unknown backdoor, which we named LunarWeb. Subsequently, we detected the same chain with LunarWeb deployed at a diplomatic establishment of a European MFA. Notably, the attacker additionally included a second backdoor – which we named LunarMail – that makes use of a unique technique for command and management (C&C) communications.
Throughout one other assault, we noticed simultaneous deployments of a series with LunarWeb at three diplomatic establishments of this MFA within the Center East, occurring inside minutes of one another. The attacker in all probability had prior entry to the area controller of the MFA and utilized it for lateral motion to machines of associated establishments in the identical community.
Additional examination uncovered extra items of the puzzle, together with parts utilized within the preliminary stage of the compromise and a restricted variety of instructions issued by the attacker. The timestamps within the oldest samples and the variations of the libraries used counsel that this toolset has been operational since no less than 2020, presumably earlier. Our technical evaluation focuses on the strategies these backdoors make use of, akin to steganography, and communication strategies.
Victimology
In accordance with ESET telemetry, the compromised machines that we managed to determine belong to a European MFA and are primarily associated to its diplomatic missions within the Center East.
Technical evaluation
Preliminary entry
We don’t know precisely how preliminary entry was gained in any of the compromises. Nonetheless, recovered installation-related parts and attacker exercise counsel potential spearphishing and abuse of misconfigured community and software monitoring software program Zabbix. Potential Zabbix abuse is usually recommended by a LunarWeb set up element imitating Zabbix logs, and a recovered backdoor command used to get the Zabbix agent configuration. Moreover, proof of spearphishing features a Phrase doc putting in a LunarMail backdoor through a malicious macro.
Beneath, we offer particulars of the installation-related parts and preliminary attacker exercise.
Stage 0 – LunarWeb preliminary server compromise
Whereas we don’t have the complete image of the preliminary compromise, we discovered an installation-related element in one of many server compromises – a compiled model of an ASP.NET internet web page originating from following supply information:
aspnet_clientsystem_web.aspx aspnet_clientsystem_web.cs
The system_web.aspx filename is a identified IoC of Hafnium, a China-aligned APT identified for exploiting vulnerabilities in Microsoft Change Server software program. Nonetheless, we consider that is both a coincidence or a false flag.
When the system_web.aspx web page is requested, it responds with a benign-looking Zabbix agent log. Nonetheless, the web page covertly expects a password in a cookie named SMSKey. If offered, the password (mixed with the salt Microsoft.SCCM.Replace.Supervisor) is used to derive an AES-256 key and IV for decrypting two embedded blobs, that are then dropped to 2 short-term information in a listing excluded from scanning.
Whereas we don’t know the password, the file sizes match additional phases within the compromise chain – the Stage 1 loader and Stage 2 blob – containing the LunarWeb backdoor. Lastly, both the attacker or an unknown element renames and strikes the 2 short-term information to their remaining locations, and units up persistence.
Throughout our investigation, we discovered that the attacker already had community entry, used stolen credentials for lateral motion, and took cautious steps to compromise the server with out elevating suspicion. The attacker’s steps included copying two log information over the community; these information had been intentionally named to imitate Zabbix agent logs. The attacker moved them to the IIS internet listing because the system_web web page, and despatched a HEAD request to the web page with a password, which resulted within the creation of two information with .tmp filename extensions. The system_web web page information had been then deleted, and the dropped .tmp information containing Phases 1 and a couple of had been moved to the next areas:
- C:WindowsSystem32en-USwinnet.dll.mui
- C:WindowsSystem32DynamicAuth.bin
Lastly, to take care of entry and execute their code, the attacker arrange a Group Coverage extension within the registry utilizing the Distant Registry service.
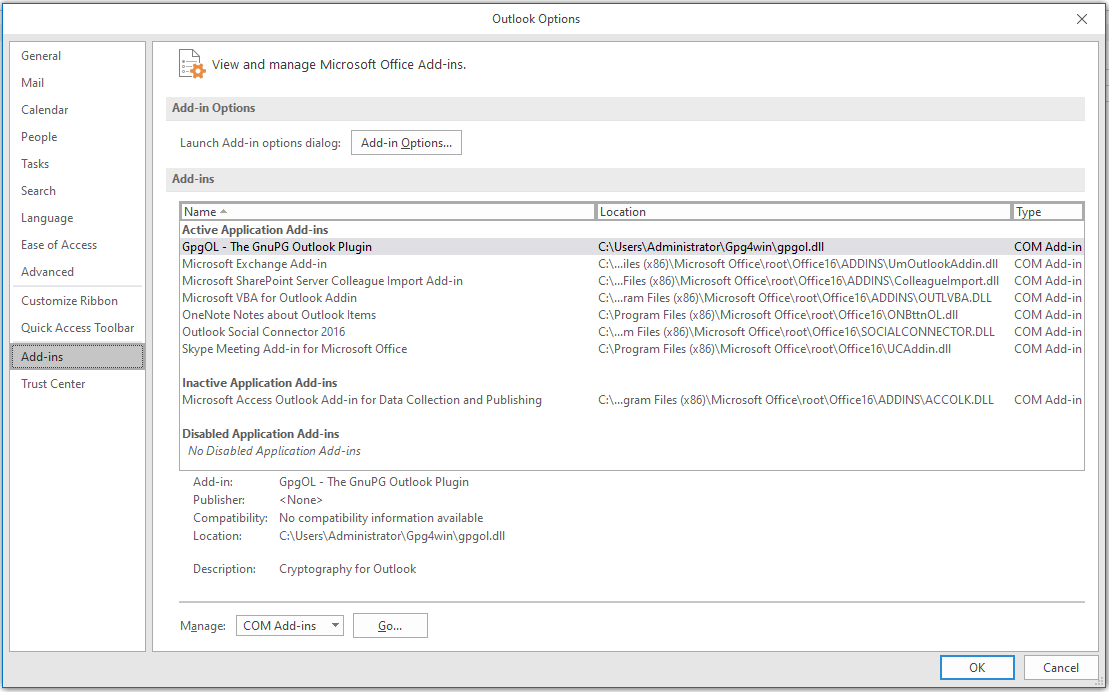
Stage 0 – LunarMail preliminary consumer compromise
In one other compromise, we discovered an older malicious Phrase doc, possible from a spearphishing e-mail. Regardless of being a DOC file, it’s really in DOCX format, which is a ZIP archive that may maintain additional content material. This doc has uncommon parts: 32- and 64-bit variations of a Stage 1 loader, and a Stage 2 blob containing the LunarMail backdoor.
They’re put in utilizing a VBA macro, executed on doc opening, that does the next:
- Calculates a sufferer ID from the pc identify and informs its C&C server by pinging a particular URL with the ID in its subdomain.
- Creates the listing %USERPROFILEpercentGpg4win and extracts the suitable information from the additional content material within the ZIP/DOCX – Stage 1 loader to gpgol.dll and Stage 2 blob to tempkeys.dat.
- Units up persistence through Outlook add-in registry settings and pings one other URL containing the ID.
We didn’t get hold of the entire doc, nevertheless it in all probability incorporates a lure that’s engaging sufficient, since it might probably’t be accessed in any other case, to persuade the sufferer to allow macros.
The paths and names used mimic Gpg4win’s Outlook add-in, GpgOL. As soon as deployed, the Stage 1 loader seems in Outlook Add-Ins, as proven in Determine 1.
Lunar toolset
Following our evaluation of the installers launched within the earlier part, we look at the loaders and end with evaluation of their payloads – two beforehand unknown backdoors. Determine 2 outlines the parts within the two noticed compromise chains.
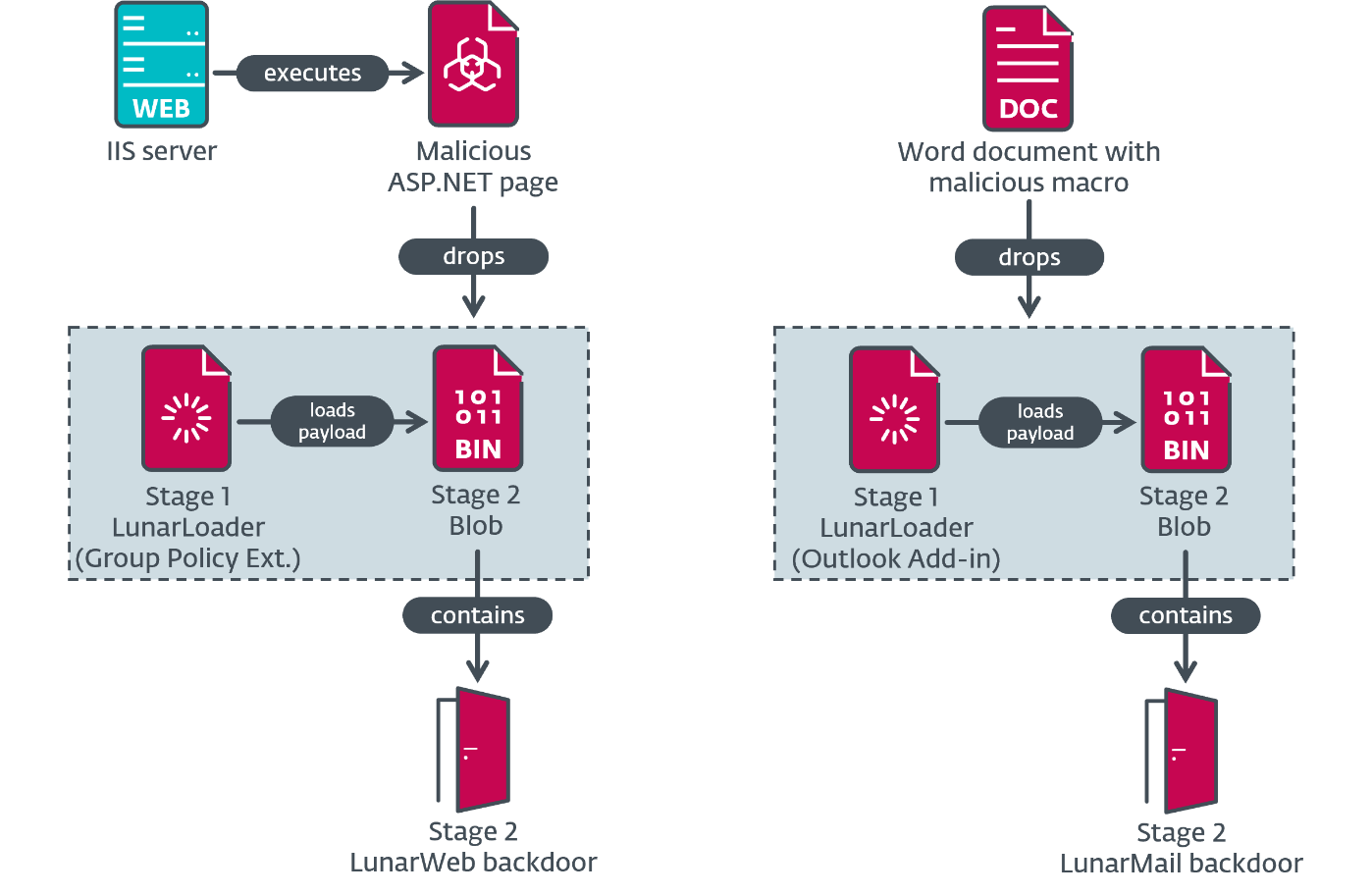
Stage 1 – LunarLoader
The execution chain begins with a loader that we’ve got named LunarLoader. It makes use of RC4, a symmetric key cipher, to decrypt the trail to the Stage 2 blob and reads an encrypted payload from it. To make sure that just one loader occasion is energetic, it makes an attempt to open after which create a mailslot with a novel identify, as an alternative of a typical synchronization object akin to mutex or occasion. It additionally creates a decryption key, derived from the MD5 hash of the pc’s DNS area identify, which it verifies. The payload is then decrypted utilizing AES-256, leading to a PE file. LunarLoader allocates reminiscence for the PE picture and decrypts the identify of an exported perform within the PE file, which is then run in a brand new thread. This perform incorporates a reflective loader.
Utilizing the DNS area identify for payload decryption serves as an execution guardrail. The loader appropriately executes solely within the focused group, which can hinder evaluation if the area identify isn’t identified.
LunarLoader can have a standalone type or be part of trojanized open-source software program. We noticed one case of the latter, with a trojanized AdmPwd, which is part of Home windows Native Administrator Password Answer (LAPS).
We noticed that LunarLoader makes use of three completely different persistence strategies and a number of other file paths, as proven in Desk 1.
Desk 1. Variants of LunarLoader
|
Persistence technique |
Loader path(s) |
Host course of |
Observe |
|
Group coverage extension |
C:WindowsSystem32en-USwinnet.dll.mui C:Program FilesLAPSCSEAdmPwd.dll* |
svchost.exe -k GPSvcGroup |
The AdmPwd dll is a identified reputable file path of Microsoft LAPS. |
|
System DLL substitute |
C:WindowsSystem32tapiperf.dll |
wmiprvse.exe |
Changing a reputable |
|
Outlook add‑in |
%USERPROFILEpercentGpg4wingpgol.dll |
outlook.exe |
N/A |
Stage 2 blob – payload container
The blob utilized in Stage 2 consists of 4 entries – together with two unused strings, the place the worth of 1 is the base64-encoded model of the string freedom or demise or freedom or demise (yeah,we’re alive), as proven in Determine 3, and 32-bit and 64-bit variations of the payload.

Whereas the aim of the freedom or demise string within the given context isn’t explicitly defined, it’s widespread for malware authors to incorporate such strings for a wide range of potential causes, akin to monitoring completely different variations of their malware, to function a distraction or false lead for analysts, or just as a type of signature or calling card. In some circumstances, we discovered strings as an alternative of a 32-bit payload – such because the string shit occurs.
We noticed two completely different backdoors used as payloads. The backdoors appear to make use of the next DLL names within the export listing, with these suspected meanings:
- mswt[e].dll – web transport (LunarWeb)
- msmt[e].dll – mail transport (LunarMail)
The e suffix is used for the 64-bit variations. The noticed file paths for the blob are listed within the IoCs part.
Stage 2 payload #1 – LunarWeb backdoor
LunarWeb, the primary payload we found, is a backdoor that communicates with its C&C server utilizing HTTP(S) and executes instructions it receives. We noticed that LunarWeb was deployed solely on servers, not consumer workstations.
Throughout its initialization, LunarWeb makes an attempt to find or create its state file, which incorporates entries associated to its execution. Then it decrypts strings, largely associated to communication, utilizing RC4 with the static key C1 82 A7 04 21 B6 40 C8 9A C3 79 AD F5 5F 72 86. It additionally collects sufferer identification knowledge and makes use of it to calculate a sufferer ID, which is utilized in communications with the C&C server.
After conducting security checks, the backdoor waits for just a few hours earlier than coming into its communication loop. This delay is skipped on the backdoor’s first run. The safety checks embrace a restrict of preliminary contact makes an attempt with the C&C server, assessing the backdoor’s lifespan, and checking C&C server accessibility. If any of the protection circumstances fail, LunarWeb self-removes, deleting its information, together with the Stage 1 loader and Stage 2 blob. Nonetheless, the persistence technique for the Stage 1 loader is left, doubtlessly leaving detectable traces.
Configuration and state
LunarWeb’s configuration is hardcoded into the binary, possible from handbook supply code adjustments. The configuration varies between samples, together with the C&C servers, their unreachability threshold, the communication format, and the backdoor lifespan.
The backdoor maintains a 512-byte state construction, up to date throughout execution and saved in a file. This file incorporates three state slots, accessed by index 0, 1, or 2 as proven in Determine 4. The primary two slots are modifiable, however unused by this backdoor; solely the third slot is used. State slots are encrypted utilizing RC4 with key 99 53 EA 6A AB 29 44 EF BE 36 12 9E F2 3B 5E C9.
The noticed areas of the state information are listed within the IoCs part.
Info assortment
LunarWeb collects the next details about its host laptop:
- distinctive sufferer identification obtained through WMI queries:
- working system model with serial quantity,
- BIOS model with serial quantity, and
- area identify.
- additional system info obtained through shell instructions:
- laptop and working system info (output of systeminfo.exe),
- atmosphere variables,
- community adapters,
- checklist of working processes,
- checklist of providers, and
- checklist of put in safety merchandise.
The data is shipped to the C&C server on first contact.
Communication
After initialization, LunarWeb communicates with its C&C server utilizing HTTP(S), beneath which is a customized binary protocol with encrypted content material.
LunarWeb employs three URLs (containing IP addresses as an alternative of domains) for various functions. One URL is used for first contact, importing details about the host laptop as described within the earlier part. The 2 remaining URLs are used for getting instructions, every being on a unique server. We refer to those URLs beneath as command URLs.
To cover its C&C communications, LunarWeb impersonates legitimate-looking site visitors, spoofing HTTP headers with real domains and generally used attributes. It may well additionally obtain instructions hidden in photos. Impersonated attributes from every noticed LunarWeb pattern are proven in Desk 2.
Desk 2. Impersonated attributes
|
Host |
Consumer-Agent |
Request-URI / Filename |
|
win8.ipv6.microsoft.com |
Mozilla/5.0 (Home windows NT 10.0; Win64; x64; rv:80.0) Gecko/20100101 Firefox/80.0 |
(Non-impersonating URIs) |
|
i1.c1.eset.com |
Host: EES Replace (Home windows; U; 64bit; BPC 9.0.2047.0; OS: 10.0.16299 SP 0.0 NT; TDB 57524; TPCAT 0; CL 1.0.0; x64c; APP ees; ASP 0.0; FW 32.0; PX 1; CD 1; RA 1; UBR 2166; HVCI 0; SHA256 1; WU 3; HWF: DA7506AC-AB57-4C28-BC32-E6D90B48B66F; PLOC en_us; PCODE 111.0.0; PAR 0; ATH -1; DC 0; PLID 375-GTM-VO6; SEAT 62f587f1; RET 5004) [sic] |
replace.ver.signed livegrid |
|
Mozilla/5.0 (Home windows NT 10.0; Win64; x64; rv:73.0) Gecko/20100101 Firefox/73.0 |
(Non-impersonating URIs) |
|
|
ctldl.windowsupdate.com |
Microsoft-CryptoAPI/6.1 |
/msdownload/replace/v3/static/trustedr/en/authrootstl.cab /msdownload/replace/v3/static/trustedr/en/disallowedcertstl.cab /msupload/replace/v3/static/trustedr/stats |
|
ctldl.windowsupdate.com |
Microsoft-CryptoAPI/6.1 |
/msdownload/replace/v3/static/trustedr/en/authrootstl.cab /msdownload/replace/v3/static/trustedr/stats |
Notable examples of impersonation embrace Home windows providers (Teredo, Home windows Replace) and updates of ESET merchandise. In circumstances of ESET impersonation, the attackers copied the Consumer-Agent (the place they slipped in a Host header) and different headers utilized by updates of our product. Surprisingly, they spoofed a nonexistent area within the Host header.
Sufferer identification is included in HTTP requests, both in a cookie or a URL question parameter. The primary technique makes use of randomly generated cookies with a 16-byte identifier (presumably a marketing campaign ID) and a sufferer ID. The second technique appends the sufferer ID twice to the URL. The suspected marketing campaign ID is current in samples utilizing the second technique however isn’t used. LunarWeb also can use an HTTP proxy server for C&C communications, if wanted.
Receiving instructions
LunarWeb collects instructions from the C&C server through a GET request to the command URL. The request and response format differ throughout 5 supported codecs, with a hardcoded worth figuring out which to make use of. Desk 3 offers an outline of those codecs. We noticed utilization of codecs 2, 3, and 4.
Desk 3. Communication codecs for getting instructions
|
Format |
Command request filename instance |
Response, extraction, decoding |
Response decryption, decompression |
Observe |
|
0 |
N/A |
Base64 |
RSA |
Brief instructions solely (RSA-4096 512‑byte restrict). |
|
1 |
N/A |
None |
RSA |
Brief instructions solely (RSA-4096 512‑byte restrict). |
|
2 |
replace.ver.signed disallowedcertstl.cab (impersonation particular) |
Base64 or none |
RSA, AES, zlib |
Decoding is skipped in situations the place this format is definitely used. |
|
3 |
|
JPG |
RSA, AES, zlib |
The info is inside a JPG remark. |
|
4 |
|
GIF |
RSA, AES, zlib |
The info is inside GIF knowledge blocks. |
Relying on the communication format, the info obtained from the C&C server would possibly want decoding utilizing the base64 algorithm or extraction from a picture. JPGs are scanned for the remark marker FF FE, whereas GIFs are parsed utilizing the giflib library. In each circumstances, the fascinating knowledge is embedded within the buildings of the picture format and never hidden in particular person pixels of a picture, as in LSB steganography for instance.
Communication codecs 0 and 1, although not noticed, merely decrypt ensuing knowledge utilizing RSA-4096. Codecs 2, 3, and 4 are extra advanced. The ensuing knowledge begins with an encrypted AES seed, decrypted with RSA-4096 and used to derive a session key. This session secret’s then used to decrypt the remainder of the info utilizing AES-256, adopted by zlib decompression.
After decryption and, if wanted, decompression, the obtained knowledge leads to a command package deal. This package deal, possessing a novel ID, is in comparison with the final processed ID, saved within the backdoor’s state. If they’re completely different, the backdoor processes the package deal and updates the final ID. The package deal might maintain a number of instructions. Every command is executed, and its output despatched to the C&C server in a single format, with no steganography, as described within the ensuing Exfiltrating knowledge part.
To carry out cryptographic operations, LunarWeb makes use of a statically linked Mbed TLS library. It has two embedded RSA-4096 keys: one for decrypting incoming knowledge and one for encrypting outgoing knowledge. Each use commonplace parameters and are outlined in our GitHub repository.
Exfiltrating knowledge
First, knowledge is zlib-compressed and encrypted utilizing AES-256, with a session key and IV derived from the info’s measurement, additionally producing a hash-based message authentication code (HMAC).
For AES encryption, a random 32-byte AES seed is generated and encrypted utilizing RSA-4096. The seed is used to derive a session key in a PBKDF-like method, SHA-256 hashing the seed and an IV 8,192 occasions. The identical key derivation occurs when decrypting obtained knowledge. The derivation algorithm and encryption code was copied from an older Mbed TLS pattern program that was faraway from the library in 2021.
Lastly, the encrypted knowledge, together with decryption and integrity metadata, is shipped. If output knowledge exceeds 1.33 MB after compression, it’s break up into a number of components of random measurement (384–512 KB).
POST requests to the C&C server embrace impersonation headers and sufferer identification, and their sending is delayed by a sleep of 34 to 40 seconds. Apparently, every command package deal obtained incorporates an output URL, which is the place to ship the end result. This may very well be a unique URI on the identical C&C server, or a totally completely different server. Within the restricted variety of command packages that we noticed, the output URL was the identical because the command URL.
Instructions
LunarWeb helps widespread backdoor capabilities, together with file and course of operations, and working shell instructions, together with ones through PowerShell. One of many instructions stands out, with the relatively unusual functionality of having the ability to run Lua code.
The total checklist of supported instructions, with extra particulars, is proven in Desk 4.
Desk 4. Overview of LunarWeb instructions
|
Kind |
Command |
Particulars |
|
0 |
Run shell instructions through a BAT file and get output |
Runs specified shell instructions through a short lived BAT file %TEMP%<random_9_alnum_chars>.bat. The output is retrieved through a pipe (additionally applies to the subsequent 4 instructions). |
|
1 |
Run shell instructions and get Unicode output |
Runs the shell instructions on the command line through cmd.exe /c and /U possibility for Unicode output. |
|
2 |
Run shell instructions and get output |
Runs the shell instructions on the command line through cmd.exe /c. |
|
3 |
Run PowerShell instructions through a PS1 file and get output |
Runs specified PowerShell instructions through a short lived script file %TEMP% |
|
4 |
Run PowerShell instructions and get output |
Runs specified PowerShell instructions through powershell.exe -command. |
|
5 |
Run Lua code |
Lua code is executed utilizing the statically linked LuaCOM library and the Lua library, model 5.1.5. These libraries, together with the command, weren’t current within the single 32-bit model of the LunarWeb backdoor that we noticed. |
|
6 |
Write file |
Specifies the file path and content material to put in writing. |
|
7 |
Learn file |
Makes use of file mapping to entry content material as an alternative of the common ReadFile API. |
|
8 |
Get sufferer identification through WMI |
Obtains sufferer identification info utilizing WMI queries, the identical info as described within the Info assortment part. |
|
9 |
No operation |
N/A |
|
10 |
Replace state entry in third slot |
Updates an entry within the state utilized by the backdoor (index 2), adjusting break length earlier than communication loop and after C&C contact failure.. |
|
11 |
Set state content material in first slot |
Units the content material of the state within the first slot (index 0), however its objective is unknown. |
|
12 |
Set state content material in second slot |
Units the content material of the state within the second slot (index 1), however its objective is unknown. |
|
13 |
Create course of and get output |
Creates an arbitrary course of with a specified command line and retrieves its output through a pipe. |
|
14 |
Zip specified path(s) |
Creates a ZIP archive with specified information and directories, through the statically linked Zipper library. |
Among the instructions can output an error message referring to the instructions as duties – Format of the duty is inaccurate.
We had been capable of get better a command package deal that contained a number of shell instructions used for reconnaissance executed through command 1, amassing the next: system and OS Info, consumer info, community configuration and connections, atmosphere variables, scheduled duties, put in packages and safety merchandise, firewall settings, listing listings, Kerberos tickets and classes, shared sources, Group Coverage, and native group memberships. Moreover, a learn file command (7) was used to retrieve Zabbix configuration from a specified file path.
Stage 2 payload #2 – LunarMail backdoor
The second backdoor, which we name LunarMail, shares many similarities with LunarWeb. The principle distinction is the communication technique – LunarMail makes use of e-mail for communication with its C&C server.
This backdoor is designed to be deployed on consumer workstations, not servers – as a result of it’s continued and supposed to run as an Outlook add-in. A high-level overview of how LunarMail operates is proven in Determine 5.
LunarMail shares concepts of its operation with LightNeuron, one other Turla backdoor that makes use of e-mail messages for C&C functions. Though each use the same exfiltration technique, we didn’t discover any code similarities between the 2 backdoors. Different Turla backdoors with comparable operation embrace Outlook backdoor.
Initialization
Throughout its initialization, the backdoor decrypts a string used to initialize a regex object that’s used as a filter to seek for the e-mail profile to make use of for C&C functions, which we describe later. The regex expression, and different strings within the backdoor, are encrypted utilizing RC4 with the static key E3 7C 9E B0 DF D1 46 48 B4 AE 8A 5F 2A A1 78 7B.
To work together with Outlook, the backdoor dynamically resolves the mandatory Outlook Messaging API (MAPI) features.
On every run, the backdoor creates a listing within the path %TEMP%{
Configuration and state
Much like LunarWeb, LunarMail’s configuration entries are hardcoded within the binary. It additionally maintains a state file, with a single state (in contrast to LunarWeb, which has a number of state slots).
The configuration possible consists of circumstances to seek out an Outlook profile for C&C communications, default exfiltration configuration, and the backdoor’s lifespan restrict.
The state is continued within the file %LOCALAPPDATApercentMicrosoftOutlookoutlk.share with a 668-byte construction, up to date throughout execution. It shops, amongst others, a timestamp of the final executed command and present staging listing. On subsequent runs, the earlier staging listing is deleted and changed with a brand new one.
Info assortment
On first run, the LunarMail backdoor collects the next info:
- atmosphere variables, and
- recipients of all despatched e-mail messages (e-mail addresses).
Moreover, a batch file with shell instructions to acquire additional system info is decrypted however by no means executed.
In sure error circumstances, akin to failure to gather the aforementioned info, the e-mail addresses of accessible Outlook profiles are collected.
Communication and instructions
Operating inside Outlook, the LunarMail backdoor communicates with its C&C server – receiving instructions and exfiltrating knowledge – utilizing e-mail messages, through the Outlook Messaging API (MAPI).
Profile search
To speak, LunarMail first searches for appropriate Outlook profiles offered by Microsoft Change. The profile circumstances embrace having solely 4 default folders (Inbox, Despatched, Deleted, and Outbox), containing the area of the focused establishment within the e-mail handle, and never matching a regex sample for varied reputable institutional emails.
The primary matching profile sends preliminary info. For additional communication, the inboxes of profile candidates are looked for command-containing emails. This method avoids hardcoding profiles and makes identification more durable. Moreover, instructions can set a particular profile to make use of, which is continued within the backdoor’s state.
Receiving instructions
LunarMail identifies a profile with instructions by looking out e-mail messages and trying to parse their attachments. The attachment have to be a single PNG picture with the .png extension, with the scale of lower than or equal to 10 MB. It then makes an attempt to parse IDAT chunks of the PNG file, on the lookout for an AES seed, an exfiltration configuration, and instructions chunks. All these parts are zlib-compressed and encrypted, the primary utilizing RSA-4096 and the latter two utilizing AES.
Apparently, the chunks should adhere to the PNG format with verified CRCs, leading to a sound, however noisy-looking picture as a consequence of encrypted, compressed content material.
LunarMail makes use of the identical cryptography as LunarWeb, together with the Mbed TLS library, two RSA-4096 keys (listed in our GitHub repository), and utilization of AES-256 with the identical key derivation algorithm. The decompressed chunk with AES-encrypted content material has the same construction to that seen in LunarWeb.
The decrypted, decompressed exfiltration configuration has a particular construction together with configuration ID, e-mail handle, topic, physique, and attachment identify and extension.
The exfiltration configuration construction mirrors LunarWeb’s command package deal metadata, specifying the command outputs’ vacation spot and an ID to keep away from duplicate instructions, saved in state. As soon as decrypted and decompressed, LunarMail instructions have a construction equivalent to LunarWeb’s. Every parsed command is executed, storing output within the staging listing for exfiltration.
Notably, e-mail messages that fail parsing for instructions have their IDs cached to keep away from repeated parsing, though the cache isn’t continued and it’s recreated on every backdoor execution. Emails efficiently parsed for instructions are deleted after processing.
Instructions
By way of command capabilities, LunarMail is easier and includes a subset of the instructions present in LunarWeb. It may well write a file, create a brand new course of, and uniquely, take a screenshot and modify the C&C communication e-mail handle. Whereas LunarMail lacks separate instructions for working shell or PowerShell instructions, it does assist Lua scripts. When executed, instructions write their output to information within the staging listing.
The total checklist of supported instructions is proven in Desk 5.
Desk 5. Overview of LunarMail instructions
|
Kind |
Command |
Particulars |
|
0 |
No operation |
N/A |
|
1 |
Write file |
Specifies the file path and content material to put in writing. |
|
2 |
Set the e-mail handle used for C&C communications |
Units a particular Outlook profile to make use of for C&C communications. The profile is specified by an e-mail handle, which is then continued within the backdoor’s state. |
|
3 |
Create course of and get output |
Creates an arbitrary course of with a specified command line, redirecting its output to the staging listing. |
|
4 |
Take a screenshot |
Makes use of GDI+ API to seize the complete display screen and produce a JPG file. |
|
5 |
Run Lua code |
Simply as in LunarWeb, Lua code is executed utilizing the statically linked libraries LuaCOM and Lua. |
Exfiltrating knowledge – preparation
LunarMail searches its staging listing for output information produced by the backdoor, getting ready them for exfiltration by embedding them in a PNG picture or PDF doc (relying on the attachment extension within the exfiltration configuration). Each PNG and PDF information are created utilizing a sound content material template.
For PNG information, a template matching the compromised establishment’s brand is used, indicating prior information and preparation of the backdoor. To create a PNG that incorporates output information, LunarMail first generates a random 32-byte AES seed, used for encryption. Then it creates IDAT chunks with knowledge and appends them to the PNG template. The chunks are just like obtained instructions, containing the next:
- Chunk with AES seed – RSA-4096 encrypted, zlib compressed.
- Chunk(s) with filename and content material – AES-256 encrypted, zlib compressed.
Earlier than compression and encryption, the output file identify and content material are wrapped right into a construction that additionally incorporates a magic string 001035 that may very well be the backdoor model. Similar to in obtained command PNGs, the created chunks comply with the PNG specification and have their CRC checksum calculated, making certain a sound picture. To finalize the picture, the IEND footer chunk is appended.
The second technique, producing a PDF file, makes use of an encrypted template from the file %TEMPpercentl4_mgrT.tmp. Now we have not noticed this knowledge file and the template’s content material is unknown, however in all probability it’s a benign, unsuspicious doc.
The output information with metadata are inserted on the finish of the final stream within the PDF template, earlier than the terminating endstream key phrase. They’re inserted within the following format and order:
- Output information – variable sized, zlib compressed, AES-256 encrypted.
- Metadata – mounted measurement (512 bytes), RSA-4096 encrypted.
The output filename and content material are wrapped into the identical construction as with the PNG, together with the magic string, which is then compressed and encrypted.
The metadata incorporates info crucial for parsing and decrypting the buildings of output information, together with AES seed and output file positions within the PDF file.
After processing and embedding within the PNG or PDF file, information staged for exfiltration are deleted. The created file briefly resides within the staging listing till exfiltration.
Exfiltrating knowledge – transmission
Ready PNG photos or PDF paperwork containing output information are transmitted as attachments in emails to an attacker-controlled inbox, as per the exfiltration configuration. The default LunarMail setup features a particular recipient e-mail, topic header, message physique, and attachment filename. The e-mail content material, though within the language of the compromised European MFA, seems machine translated as a consequence of its unnatural phrasing.
An exfiltration configuration from a obtained command overrides the default one. Now we have not recovered any instructions so don’t know if completely different e-mail recipients, topics, our bodies, or attachment identify or varieties are used throughout a number of instructions.
If supported, the e-mail physique makes use of HTML format. The PNG is embedded as a picture within the physique, in contrast to the PDF. Determine 6 exhibits an illustration of an exfiltration e-mail primarily based on the default configuration. The e-mail was translated, redacted, and the emblem was modified by ESET Analysis, to not reveal the compromised establishment.
Exfiltration e-mail messages are despatched with the PR_DELETE_AFTER_SUBMIT flag. As well as, any despatched messages to the exfiltration handle are deleted.
Conclusion
Now we have described two beforehand unknown backdoors utilized in compromises of a European authorities’s establishments, which we attribute with medium confidence to the Russia-aligned APT group Turla.
The backdoors share a loader, bear code overlaps, and assist comparable instructions, however they undertake completely different C&C communication strategies. The primary backdoor – LunarWeb – makes use of HTTP(S) and makes an attempt to mix in by mimicking the site visitors of reputable providers akin to Home windows Replace. The second backdoor – LunarMail – piggybacks on Outlook and communicates through e-mail messages, utilizing both PNG photos or PDF paperwork to exfiltrate knowledge.
We noticed various levels of sophistication within the compromises; for instance, the cautious set up on the compromised server to keep away from scanning by safety software program contrasted with coding errors and completely different coding types (which aren’t the scope of this blogpost) within the backdoors. This means a number of people had been possible concerned within the growth and operation of those instruments.
Though the described compromises are newer, our findings present that these backdoors evaded detection for a extra prolonged interval and have been in use since no less than 2020, primarily based on artifacts discovered within the Lunar toolset.
IoCs
A complete checklist of IoCs and samples might be present in our GitHub repository.
Information
|
SHA-1 |
Filename |
Detection |
Description |
|
DE83C2C3FE68CB1BF961 |
App_Web_0bm4blbr.dll |
MSIL/Agent.ERT |
Compiled model of ASP.NET internet web page that installs LunarWeb. |
|
9CEC3972FA35C88DE87B |
N/A |
VBA/TrojanDownloader. |
Malicious Phrase macro that installs LunarMail. |
|
2ED792E39F7D56DE52BD |
gpgol.dll |
Win64/LunarLoader.B |
LunarLoader (x64) used to load LunarMail. |
|
F09E36553E48EBD42E60 |
gpgol.dll |
Win32/LunarLoader.A |
LunarLoader (x86) used to load LunarMail. |
|
94A4CE9C75BC847E7BE5 |
tapiperf.dll |
Win64/LunarLoader.C |
LunarLoader (x64) used to load LunarWeb. |
|
00006B30806F91591134 |
admpwd.dll |
Win64/LunarLoader.A |
LunarLoader (x64); a trojanized AdmPwd, used to load LunarWeb. |
|
19D86CF2ED82EAE23E01 |
AdmPwd.dll |
Win64/LunarLoader.A |
LunarLoader (x64); a trojanized AdmPwd, used to load LunarWeb. |
|
795C4127D42FE8DFAF45 |
winnet.dll.mui |
Win64/LunarLoader.B |
LunarLoader (x64) used to load LunarWeb. |
|
754FB657156643FD09A6 |
N/A |
Win32/LunarWeb.A |
LunarWeb backdoor (x86). |
|
FCAE66F6D95C78DC8296 |
N/A |
Win64/LunarMail.A |
LunarMail backdoor (x64). |
|
67C6AEC8D129E610378E |
N/A |
Win32/LunarMail.A |
LunarMail backdoor (x86). |
|
4C84110F1B10DF5FDD61 |
N/A |
Win64/LunarWeb.A |
LunarWeb backdoor (x64). |
|
5D3975E57BDCB630A00F |
N/A |
Win64/LunarWeb.A |
LunarWeb backdoor (x64). |
|
5EF771AFC96C24371D36 |
N/A |
Win64/LunarWeb.A |
LunarWeb backdoor (x64). |
|
512E4FA7D6119270FF44 |
N/A |
Win64/LunarWeb.A |
LunarWeb backdoor (x64). |
File paths
Stage 2 blob
C:WindowsSystem32DynamicAuth.bin
C:Program FilesLAPSCSEadmpwd.cache
C:ProgramDataMicrosoftWinThumbadcache.clb
C:WindowsSystem32perfcache.dat
%USERPROFILEpercentGpg4wintempkeys.dat
LunarWeb state file
C:ProgramDataMicrosoftWindowsTemplatescontent.tpl
C:ProgramDataMicrosoftWinThumbthumb.clb
C:ProgramDataMicrosoftWinThumbcfcache.clb
C:WindowsSystem32perfconfm.dat
LunarMail state file
%LOCALAPPDATApercentMicrosoftOutlookoutlk.share
Community
|
IP |
Area |
Internet hosting supplier |
First seen |
Particulars |
|
N/A |
thedarktower.av. |
N/A |
2020‑02‑01 |
Area (Free DNS) pinged by malicious Phrase macro. |
|
45.33.24[.]145 |
N/A |
Akamai Linked Cloud |
2020‑05‑20 |
C&C server of LunarWeb (compromised VPS). |
|
45.79.93[.]87 |
N/A |
Akamai Linked Cloud |
2020‑05‑20 |
C&C server of LunarWeb (compromised VPS). |
|
65.109.179[.]67 |
N/A |
Hetzner On-line GmbH |
2023‑10‑29 |
C&C server of LunarWeb (compromised VPS). |
|
74.50.80[.]35 |
N/A |
Host Division NJ, LLC |
2023‑10‑29 |
C&C server of LunarWeb. |
|
82.165.158[.]86 |
N/A |
IONOS SE |
2022‑08‑03 |
C&C server of LunarWeb (compromised VPS). |
|
82.223.55[.]220 |
N/A |
IONOS SE |
2022‑08‑03 |
C&C server of LunarWeb (compromised VPS). |
|
139.162.23[.]113 |
N/A |
Akamai Linked Cloud |
2023‑06‑15 |
C&C server of LunarWeb (compromised VPS). |
|
158.220.102[.]80 |
N/A |
Contabo GmbH |
2023‑10‑29 |
C&C server of LunarWeb. |
|
161.97.74[.]237 |
N/A |
Contabo GmbH |
2023‑06‑15 |
C&C server of LunarWeb. |
|
176.57.150[.]252 |
N/A |
Contabo GmbH |
2023‑06‑15 |
C&C server of LunarWeb. |
|
212.57.35[.]174 |
N/A |
Webglobe, a.s. |
2023‑06‑02 |
C&C server of LunarWeb (compromised VPS). |
|
212.57.35[.]176 |
N/A |
Webglobe, a.s. |
2023‑06‑02 |
C&C server of LunarWeb (compromised VPS). |
Registry keys
HKCUSOFTWAREClassesCLSID{3115036B-547E-4673-8479-EE54CD001B9D}
MITRE ATT&CK strategies
This desk was constructed utilizing model 15 of the MITRE ATT&CK framework.
|
Tactic |
ID |
Title |
Description |
|
Reconnaissance |
Collect Sufferer Org Info |
LunarMail’s communication technique signifies prior information about compromised establishments. |
|
|
Useful resource Improvement |
Purchase Infrastructure: DNS Server |
Stage 0 macro pings a site from free DNS internet hosting offered by ClouDNS. |
|
|
Purchase Infrastructure: Digital Personal Server |
Turla has used VPS internet hosting suppliers for C&C servers. |
||
|
Compromise Infrastructure: Digital Personal Server |
Turla has used compromised VPSes for C&C functions. |
||
|
Compromise Accounts: E-mail Accounts |
Turla has used possible compromised e-mail accounts for communication with the LunarMail backdoor. |
||
|
Develop Capabilities: Malware |
Turla has developed customized malware, together with loaders and backdoors. |
||
|
Execution |
Home windows Administration Instrumentation |
LunarWeb obtains system info by utilizing WMI queries. |
|
|
Command and Scripting Interpreter |
LunarWeb and LunarMail can execute Lua scripts. |
||
|
Command and Scripting Interpreter: PowerShell |
LunarWeb can execute PowerShell instructions. |
||
|
Command and Scripting Interpreter: Home windows Command Shell |
LunarWeb can execute shell instructions through cmd.exe. |
||
|
Command and Scripting Interpreter: Visible Primary |
Stage 0 Phrase doc incorporates a VBA macro. |
||
|
Native API |
LunarWeb and LunarMail use varied Home windows APIs. |
||
|
Consumer Execution: Malicious File |
Stage 0 Phrase doc with malicious macro have to be opened by sufferer. |
||
|
Persistence |
Workplace Software Startup: Add-ins |
LunarMail loader is continued as an Outlook add-in. |
|
|
Boot or Logon Autostart Execution |
A LunarWeb loader is continued as a Group Coverage extension. |
||
|
Hijack Execution Movement |
A LunarWeb loader is continued by changing the system DLL tapiperf.dll. |
||
|
Protection Evasion |
Obfuscated Information or Info |
LunarWeb and LunarMail are AES-256 encrypted on disk. |
|
|
Obfuscated Information or Info: Steganography |
LunarMail phases exfiltration knowledge right into a PNG picture or PDF doc. |
||
|
Obfuscated Information or Info: Dynamic API Decision |
LunarMail dynamically resolves MAPI features. |
||
|
Obfuscated Information or Info: Embedded Payloads |
LunarMail installer has payloads embedded in a DOCX format doc. |
||
|
Masquerading: Match Professional Title or Location |
Filenames utilized by LunarWeb and LunarMail loading chains mimic reputable information. |
||
|
Indicator Elimination: File Deletion |
LunarWeb and LunarMail can uninstall themselves by deleting their loading chain. |
||
|
Indicator Elimination: Clear Mailbox Information |
LunarMail deletes e-mail messages used for C&C communications. |
||
|
Deobfuscate/Decode Information or Info |
LunarWeb and LunarMail decrypt their strings utilizing RC4. |
||
|
Execution Guardrails: Environmental Keying |
LunarLoader decrypts its payload utilizing a key derived from the DNS area identify. |
||
|
Reflective Code Loading |
LunarWeb and LunarMail are executed utilizing a reflective loader. |
||
|
Discovery |
System Service Discovery |
LunarWeb retrieves a listing of providers. |
|
|
System Community Configuration Discovery |
LunarWeb retrieves community adapter info. |
||
|
Course of Discovery |
LunarWeb retrieves a listing of working processes. |
||
|
System Info Discovery |
LunarWeb retrieves system info akin to OS model, BIOS model, area identify, and atmosphere variables. LunarMail retrieves atmosphere variables. |
||
|
Software program Discovery: Safety Software program Discovery |
LunarWeb discovers put in safety options through the WMI question wmic /Namespace:rootSecurityCenter2 Path AntiVirusProduct Get *. |
||
|
Assortment |
Information from Native System |
LunarWeb and LunarMail can add information from the compromised machine. |
|
|
Information Staged: Native Information Staging |
LunarMail phases knowledge in a listing in %TEMP%. |
||
|
Display screen Seize |
LunarMail can seize screenshots. |
||
|
E-mail Assortment: Native E-mail Assortment |
LunarMail collects recipients of despatched e-mail messages and may acquire e-mail addresses of Outlook profiles. |
||
|
Archive Collected Information: Archive through Library |
LunarWeb and LunarMail use a statically linked zlib library for compression of collected knowledge. |
||
|
Command and Management |
Information Obfuscation: Steganography |
LunarWeb can obtain instructions hidden in JPG or GIF photos. LunarMail receives instructions hidden in PNG photos and exfiltrates knowledge hidden in PNG photos or PDF paperwork. |
|
|
Information Obfuscation: Protocol Impersonation |
LunarWeb impersonates reputable domains in C&C communications by utilizing a pretend Host header and identified URIs. |
||
|
Software Layer Protocol: Net Protocols |
LunarWeb makes use of HTTP for C&C communications. |
||
|
Software Layer Protocol: Mail Protocols |
LunarMail makes use of e-mail messages for C&C communications. |
||
|
Proxy: Inside Proxy |
LunarWeb can use an HTTP proxy for C&C communications. |
||
|
Non-Software Layer Protocol |
Stage 0 macro pings the C&C server, using ICMP protocol. |
||
|
Information Encoding: Customary Encoding |
LunarWeb might obtain base64-encoded knowledge from the C&C server. |
||
|
Encrypted Channel: Symmetric Cryptography |
LunarWeb and LunarMail encrypt C&C communications utilizing AES-256. |
||
|
Encrypted Channel: Uneven Cryptography |
LunarWeb and LunarMail encrypt the AES key utilized in C&C communications utilizing RSA-4096. |
||
|
Exfiltration |
Automated Exfiltration |
LunarWeb and LunarMail mechanically exfiltrate collected knowledge to the C&C server. |
|
|
Information Switch Dimension Limits |
LunarWeb splits exfiltrated knowledge above 1.33 MB into a number of smaller chunks. LunarMail limits the scale of e-mail attachments containing exfiltrated knowledge. |
||
|
Exfiltration Over C2 Channel |
LunarWeb and LunarMail exfiltrate knowledge over the C&C channel. |